For many years, cybersecurity was an afterthought. "Core" business functions took center stage and security was not considered one of them. In fact, security was sometimes seen as an impediment to business, with security managers always cautioning against the use of new technology. However, times have changed.
If you're an Australian organization, you're probably in the process of implementing the Essential Eight: The cybersecurity framework created by the Australian Cyber Security Centre (ACSC). The Essential Eight requires you to determine your risk exposure level and gives you a maturity model to adhere to. Called the Essential Eight Maturity Model, which provides four levels of security maturity, starting from zero to three.
This two-part blog series explores the assessment procedure used to check if an organization has effectively implemented the Essential Eight mitigation strategies. It delves into how an organization can achieve their target maturity level.
[We recommend you glance through the first part of the blog series before reading this one. Click here to get a brief introduction to the topics mentioned above.]
This blog will explore the following topics:
Let us start with assessing whether you are indeed at level zero.
Any organization that does not meet the security requirements of Maturity Level One, falls under Maturity Level Zero.
You likely belong to Maturity Level Zero if:
While this may not paint a pretty picture of your cybersecurity posture, it is best to assess where you stand, so you can recognize and tackle these risks head on. The ACSC's Essential Eight Maturity Model prescribes some basic measures you can adopt to ensure your organization takes the first step towards reaching Maturity Level One across all eight mitigation strategies.
Let's see how you can reach your nearest target maturity level and get accredited as such.
We recommend that you read our blog or download our free e-book on the Essential Eight before we explore the security controls that need to be implemented for each mitigation strategy. The table below briefly illustrates some of the security requirements to pass the assessment procedure for each control under the first mitigation strategy: Application Control.
Reaching your target maturity level: Level One
| Mitigation Strategy | Security control | Security requirements for the assessment procedure | How a SIEM can help you implement this |
| Application Control | The execution of:
is prevented on workstations from standard user profiles and temporary folders used by the operating system, web browsers, and email clients. |
There are three ways assessors can test whether the control has been effectively implemented, according to the system owner's security policies and the kind of assessment tools that can be used.
|
SIEM solutions come with built-in security reporting modules which give analysts all the required information at one glance. Several vendors offer custom reports for compliance management. For example, Log360, ManageEngine's SIEM solution offers users the option of creating a customized compliance report. Also, out-of-the-box reports, such as the ones listed below, can help you look out for and identify changes that can prevent the listed executions, detect file modifications, permission, and policy changes. These include:
A more detailed explanation of each report and how it can help effectively implement the security control is given below. |
Here's how the reporting feature of a comprehensive SIEM solution can help you comply with the security requirements of Essential Eight's first maturity level:
About the report: The file activity monitoring reports in a SIEM solution give analysts a comprehensive audit of all the files shared on the network. They provide information about the modifications, creations, and deletions of files. There are also reports on renamed files, any permission changes made and top file operations that have been carried out, segregated based on users, devices, and files for easier reference. These reports provide granular information about the type of change that has occurred, who has instigated it, the name of the file or folder that has been modified, and the time and date the change occurred.
How it helps implement the control: This report can help keep track of changes occurring in any temporary folders, unusual permission changes, or any other suspicious activity that could signal the execution of a malicious script.
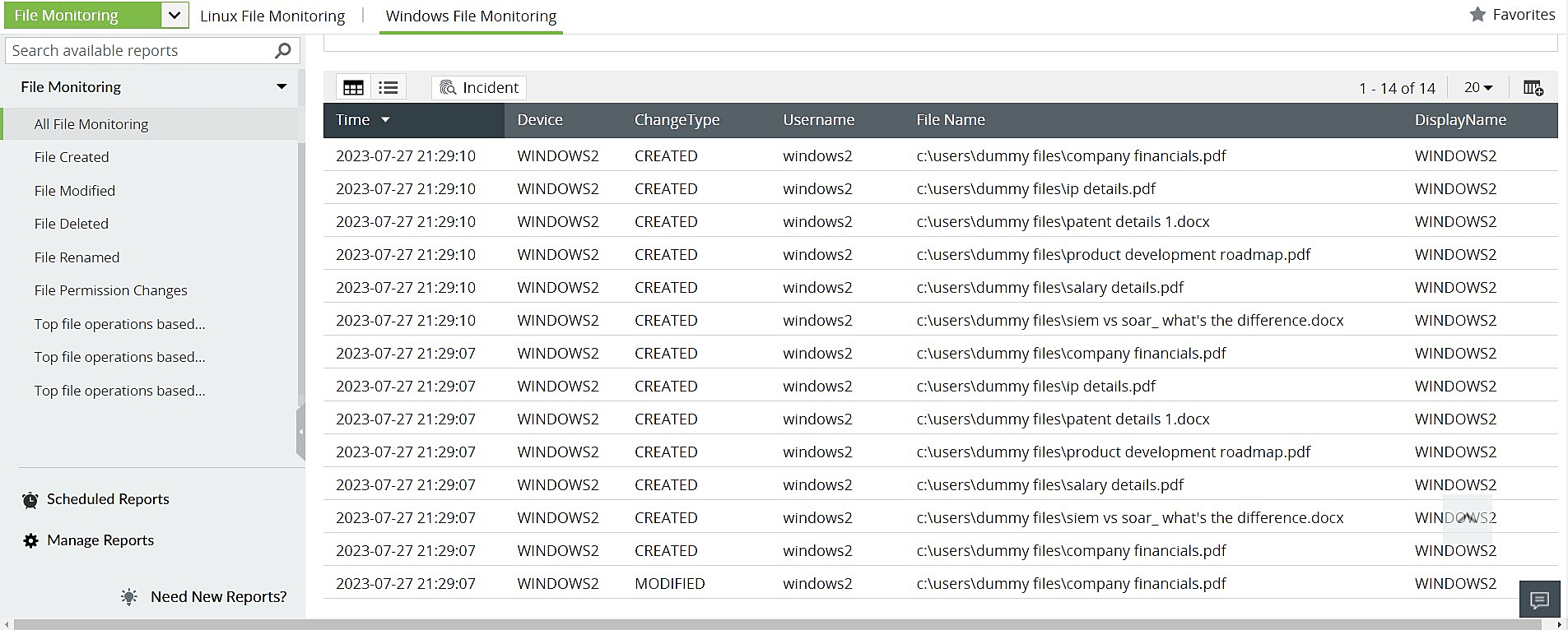 Figure 1: File Monitoring reports in Log360, ManageEngine's comprehensive SIEM solution
Figure 1: File Monitoring reports in Log360, ManageEngine's comprehensive SIEM solution
About the report: A SIEM solution integrates with the MITRE ATT&CK framework to help security personnel spot adversaries, classify attacks, and single out attack tactics and techniques. The reports are classified according to the different tactics, techniques, and sub-techniques. There are separate reports to address threats classified under different sub-techniques, with each report looking out for IoCs specific to that threat.
How it helps implement the control: The MITRE ATT&CK framework extensively covers the techniques used by cybercriminals to carry out malicious executions, along with the activities that need to be tracked by security teams to detect them. A SIEM solution, like Log360, is integrated with the framework and produces specific reports for each of these techniques. Log360 offers security administrators a categorized and ready to be analyzed view of all executions that could lead to malicious activity. This feature will go a long way in spotting executions, scripts, installers, HTML applications, or control panel applets that are uncalled for and identify the user profile and workstation they were carried out from.
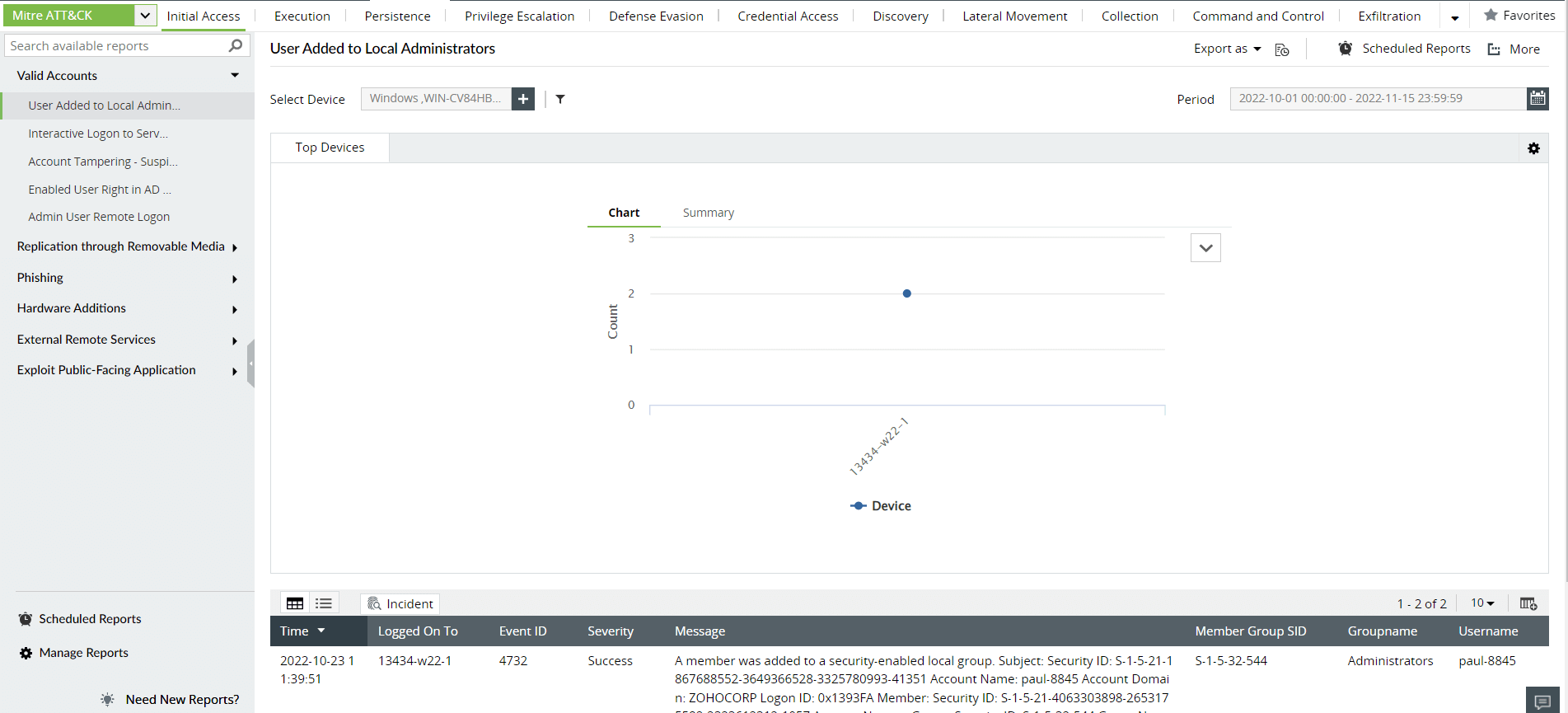 Figure 2: MITRE ATT&CK reports in Log360, ManageEngine's comprehensive SIEM solution
Figure 2: MITRE ATT&CK reports in Log360, ManageEngine's comprehensive SIEM solution
About the report: File integrity monitoring (FIM) reports help track any changes made to files or folders in workstations or devices in the network. Security admins and analysts can get detailed information about all file or folder changes including files or folders created, modified, deleted, moved, or renamed. There are specific reports that list out all folder permission changes, audit setting changes, folder owner changes, files or folders copy and pasted, and failed attempts to write or delete files.
How it helps implement the control: FIM reports can help monitor all files and folders for even the smallest of changes. Admins can set up alerts to be notified of any modifications. They can also create and schedule custom reports according to the compliance requirements of the Essential Eight framework for their target maturity level.
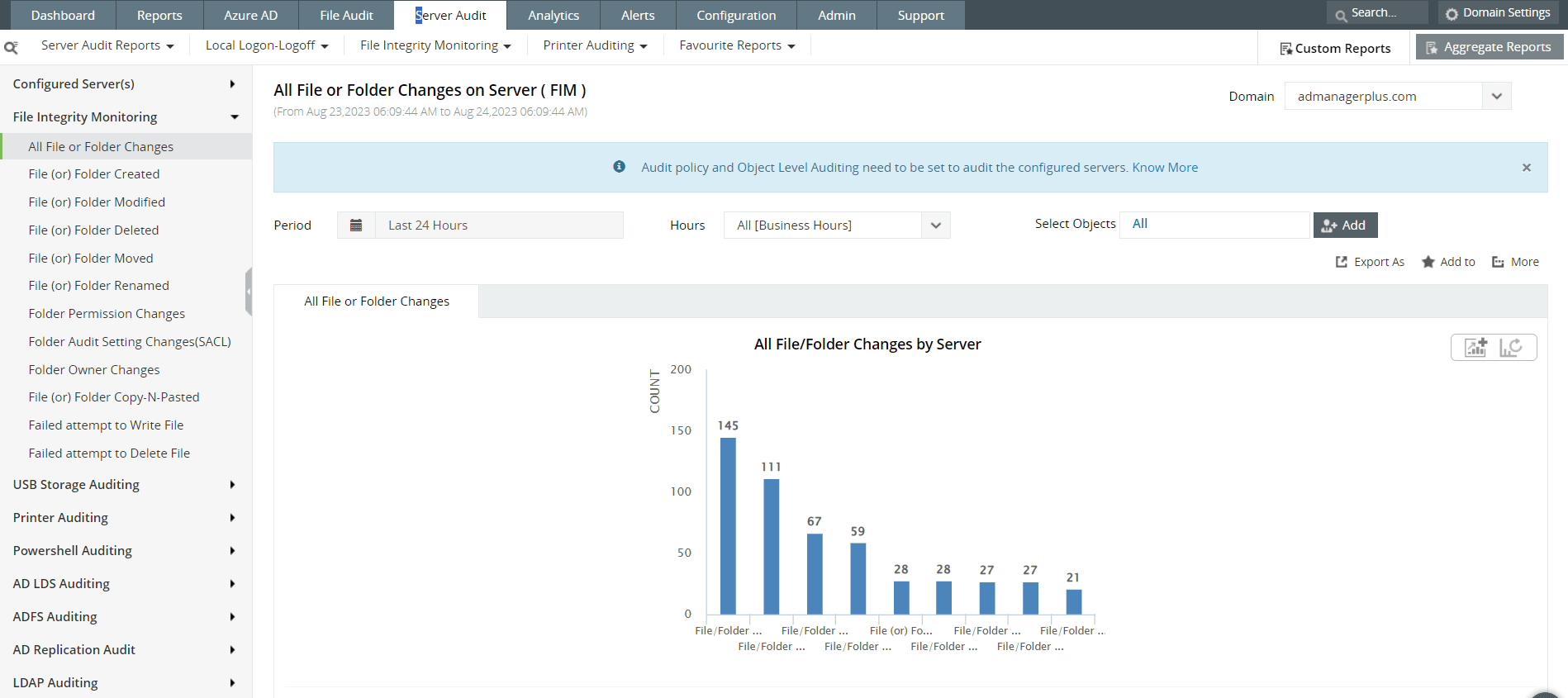 Figure 3: File integrity monitoring reports in Log360, ManageEngine's comprehensive SIEM solution
Figure 3: File integrity monitoring reports in Log360, ManageEngine's comprehensive SIEM solution
About the report: Process tracking reports can help identify malicious executions, suspicious services, tasks, or processes. Each of the reports tracks information from Windows security logs and displays key data about the kind of process that has been executed, who instigated it, and when and where it was executed. There are other specific reports to track:
How it helps implement the control: These reports provide granularity into the kind of processes and services that are happening in the network. Analysts can get the complete picture of who instigated the process, the execution path, and when it took place with these insights. This can help them track the activity and recognize whether it must be examined further or not.
![]() Figure 4: Process tracking reports in Log360, ManageEngine's comprehensive SIEM solution
Figure 4: Process tracking reports in Log360, ManageEngine's comprehensive SIEM solution
Apart from these, a SIEM tool also offers users the ability to:
Administrators can use these features to create reports that match the security requirements of the maturity level they are trying to reach, customize their dashboard so they can spot these at a glance, and schedule them at customized intervals to help with the documentation process for security audits.
To learn more about Log360, ManageEngine's SIEM solution, and how it can help you reach your target maturity levels, sign up for a free personalized demo with our product experts: https://www.manageengine.com/log-management/log360-demo-request-page.html
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.