Help Center
Quick Start
- Overview
- System requirements
- Minimum privileges required
- Default port configuration
- Installing DataSecurity Plus
- Uninstalling DataSecurity Plus
- Starting DataSecurity Plus
- Launching DataSecurity Plus
- Configuring your solution
- Licensing details
- Applying a license
File Auditing
- About File Auditing
- Domain configuration
- File server configuration
- Failover cluster configuration
- NetApp server configuration
- Nutanix server configuration
- Workgroup configuration
Setting up File Audit
Dashboard
Reports
Alerts
Configuration
Storage Configuration
File Analysis
- About File Analysis
- Domain configuration
- File server configuration
- Workgroup configuration
- SMB File Server Configuration
- On-Demand Reports
Setting up File Analysis
Dashboard
Reports
Alerts
Configuration
Data Risk Assessment
- About Data risk assessment
Setting up Data risk assessment
Dashboard
Reports
Ownership analysis
Configuration
Endpoint DLP
- About Endpoint DLP
Setting up Endpoint DLP
Reports
Alerts
Prevention policies
Configuration
Cloud Protection
- About Cloud Protection
- Gateway Server Installation Steps
- Gateway Configuration in Endpoint
- Gateway Cluster Configuration
- Gateway Server Management
- Certificate Authority Configuration
- Two-way SSL configuration
- Manage Certificate Trust Store
- Threat Analytics Database
- Manage Banned Applications
- Manage Authorized Applications
- Regenerating gateway server access key
- Updating gateway server
- Gateway Server Failover
- Load Balancer Configuration
- Global Insight
- Application Insight
- User Insight
- Shadow Application Insight
- Banned Application Insight
- Cloud App Discovery
- File Upload & Download Reports
- Control Policy reports
- General Reports
- Application Insights
- Shadow Domain Insights
- Banned Domain Insights
Setting up Cloud Protection
Dashboard
Reports
Control Policies
Storage Configuration
Administrative settings
- Technician configuration
- Notification filters
- Manage agent
- Agent settings
- SIEM integration
- Business hours configuration
- Two-factor authentication
- Workgroup configuration
- Security policy
Email configuration
General settings
- Connection
- Personalize
- DataSecurity Plus Server
- Privacy Settings
- Disk utilization
- Schedule Retention Policy
Release notes
2026
2025
2024
2023
2022
2021
2020
2019
2018
2017
2016
2015
Troubleshooting
- HTTP communication failure
- Dormant DataEngine
- Secure Gateway server failure
- RPC communication failure
- Cloud Protection Gateway server failure
- Known issues and limitations
- Known errors and solutions
- Report discrepancy in File Analysis
Guides
- Agent document
- How to Migrate/Move DataSecurity Plus
- How to apply SSL certificate
- How to automate DataSecurity Plus database backup
- How to set alerts in DataSecurity Plus
- How to secure your DataSecurity Plus installation
How to configure alerts in DataSecurity Plus
Configure alerts and responses in DataSecurity Plus by following the module-specific instructions below. For further assistance, please email us at support@datasecurityplus.com.
- Alerts and responses in File Audit
- Alerts and responses in File Analysis
- Alerts and responses in Data Risk Assessment
- Alerts and responses in Data Leak Prevention
Alerts and responses in File Audit
Customize the default alerts or configure new alerts in File Audit by following the steps below:
To define an Alert Profile, navigate to File Audit > Configuration > Settings > Alert Configuration. Alternatively, you can click the New Alert Profile button in the Alerts tab.
| Alert option | Description |
| Alert details |
|
| Alert criteria |
Specify the events that will trigger the new alert by applying filters in the Criteria section. You can define the criteria using the Include or Exclude options. In the Include tab:
Use the + option to add more inclusion criteria. Similarly, you can trigger an alert by defining the exclusion criteria in the Exclude tab. These users, file paths, or other entities configured will be overlooked while monitoring file servers. |
| Alert responses |
When an alert is triggered, you can:
|
Note: If you're defining multiple inclusion criteria, all the conditions must be satisfied for an alert to be triggered.
Exclusion criteria overrides inclusion criteria. For instance, if you specify a particular File Name under the Exclude tab, file access events will be monitored for all other files, leaving out that particular file.
Setting email responses in File Audit Alert Configuration
In the email settings in the Alert Profile, you can customize the following:
| Recipient |
Emails can be sent to:
|
| Priority |
The priority flagged in the email can be set to:
|
| Subject |
The subject of the email can be set to:
|
| Message |
The message can include:
|
| Email limit |
You can restrict the number of alert emails by defining the maximum number of emails for the desired time interval. |
Alerts and responses in File Analysis
Customize the default alerts or configure new alerts in File Analysis by following the steps below:
To define an Alert Profile, navigate to File Analysis > Configuration > Settings > Alert Configuration.
| Alert option | Description |
| Alert details | Define the Alert Name, Alert Description, and Severity. |
| Alert sources |
There are two sources from which alerts can be generated:
|
| Alert criteria |
Specify the events that will trigger the new alert by applying filters in the Criteria section. You can define the criteria using the Include or Exclude options. In the Include tab:
Use the + option to add more inclusion criteria. Similarly, you can trigger an alert by defining the exclusion criteria in the Exclude tab. These file names, file paths, or other entities configured will be overlooked while monitoring file servers. |
| Alert responses |
In the Response tab, configure the follow-up actions that will be initiated immediately after an alert is triggered. Check the boxes to enable the options before configuring them. You can: In the Include tab:
Use the + option to add more inclusion criteria. Similarly, you can trigger an alert by defining the exclusion criteria in the Exclude tab. These file names, file paths, or other entities configured will be overlooked while monitoring file servers. |
Note: If you're defining multiple inclusion criteria, all the conditions must be satisfied for an alert to be triggered.
Exclusion criteria overrides inclusion criteria. For instance, if you specify a particular File Name under the Exclude tab, file access events will be monitored for all other files, leaving out that particular file.
Alerts and responses in Data Risk Assessment
Create alerts based on policies, file owners, and other criteria using the steps below:
To define an Alert Profile, navigate to Risk Analysis > Discovery Policy Configuration > Alert Profile.
| Alert option | Description |
| Alert details |
Define the Alert Name, Alert Source, Description, and Severity. |
| Alert criteria |
Example: Policy, Equals, and GDPR in the respective drop-down filters. |
| Alert responses |
In the Response tab, configure the follow-up actions that will be initiated immediately after an alert is triggered. Check the boxes to enable the options before configuring them. You can:
|
Alerts and responses in Endpoint DLP
Customize the default alerts to track users' endpoint activity by following the steps below.
To customize an Alert Profile, navigate to Endpoint DLP > Configuration > Audit/ Alert Profiles > Alert Configuration.
| Alert option | Description |
| Alert selection |
Click the Alert Profile tabs to view the available alerts. |
| Alert details |
The Alert Name, Alert Source, Description, and Severity are predefined. |
| Alert Profiles |
Alert Profiles in Endpoint DLP vary based on the source of the alerts. Refer to the individual profile details mentioned below. To modify the alerts, click the edit icon next to the individual alert. |
| Alert criteria |
Specify the events that will trigger the new alert by applying filters in the Criteria section. You can define the criteria using the Include or Exclude options. In the Include tab:
Use the + option to add more inclusion criteria. Similarly, you can trigger an alert by defining the exclusion criteria in the Exclude tab. These users, file paths, or other entities configured will be overlooked while monitoring file servers. Follow the steps below to customize various alert sources and responses available in the Endpoint DLP module. |
| File Integrity Monitor |
These alerts can be used to track sensitive file changes, user activity, or indicators of ransomware attacks. Define alert responses as required in the Response section. You can choose to dispatch email notifications and/or execute scripts. Example:
|
| Removable Storage |
These alerts are triggered when file events are initiated in USB drives. Define alert responses as required in the Response section. You can choose to dispatch email notifications, execute scripts, block all USB devices from being used in the source machine, or block the USB device that triggered the alert. Example:
|
|
These alerts monitor print requests. Define alert responses as required in the Response section. You can choose to dispatch email notifications and/or execute scripts. Example:
|
|
| Clipboard |
This alert detects critical file copy and paste events. Define alert responses as required in the Response section. You can choose to dispatch email notifications, execute scripts, or move or delete the files. Example:
|
| Email Client |
These alerts monitor outgoing emails for potential data leaks. Define alert responses as required in the Response section. You can choose the User prompt in Active Responses to warn users about policy violations, and/or choose from the Passive Responses, which include dispatching email notifications and executing scripts. Example:
|
| Web |
This alert is triggered on the potential upload or download of critical files. Define alert responses as required in the Response section. You can choose to dispatch email notifications and/or execute scripts. Example:
|
| File Share |
This alert is triggered when access anomalies are detected in shares. Define alert responses as required in the Response section. You can choose to dispatch email notifications and/or execute scripts. Example:
|
| Alert responses |
In the Response tab of each Alert Profile, configure the follow-up actions that will be initiated immediately after an alert is triggered. Check the boxes to enable the options before configuring them. You can:
|
Note: If you're defining multiple inclusion criteria, all the conditions must be satisfied for an alert to be triggered.
Exclusion criteria overrides inclusion criteria. For instance, if you specify a particular File Name under the Exclude tab, file access events will be monitored for all other files, leaving out that particular file.
How to set default or custom script responses
DataSecurity Plus supports script response actions to be executed immediately when an alert is triggered. Default scripts are available for use in the following location: [installation_directory]\bin\alertScripts.
You can also write custom scripts to suit your requirements. To write a script:
- Mention the application software that will execute the script.
- Include the full path of the script file.
- Choose the parameters to define the script in the Arguments drop-down.
Note: Select the parameters in the Arguments drop-down in the right order to run the script smoothly. For instance, refer to the steps below:
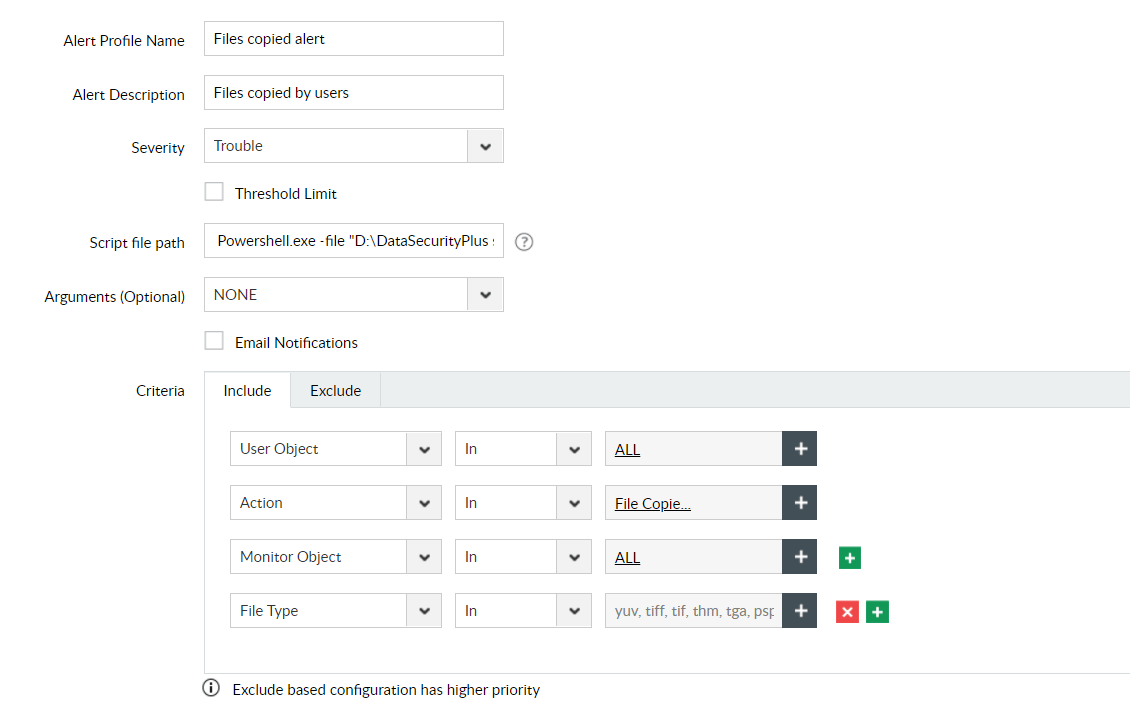
Step 1: Specify script file path.
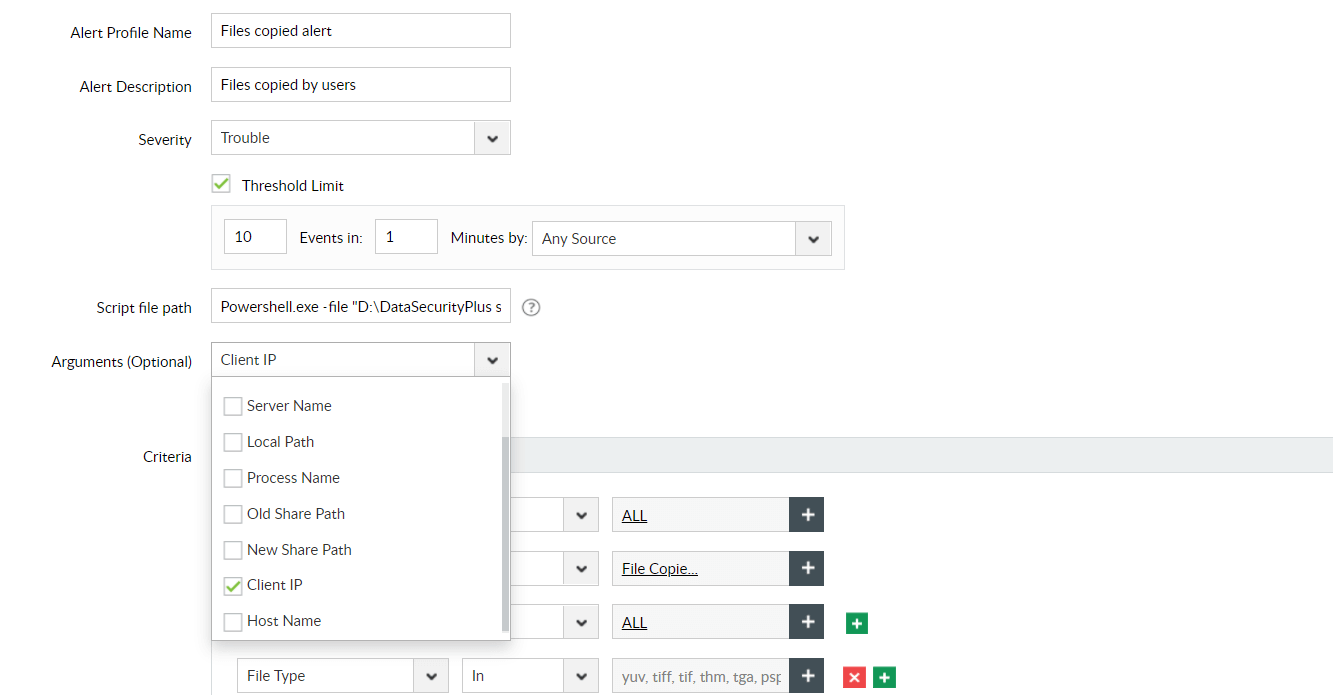
Step 2: Choose the first argument.
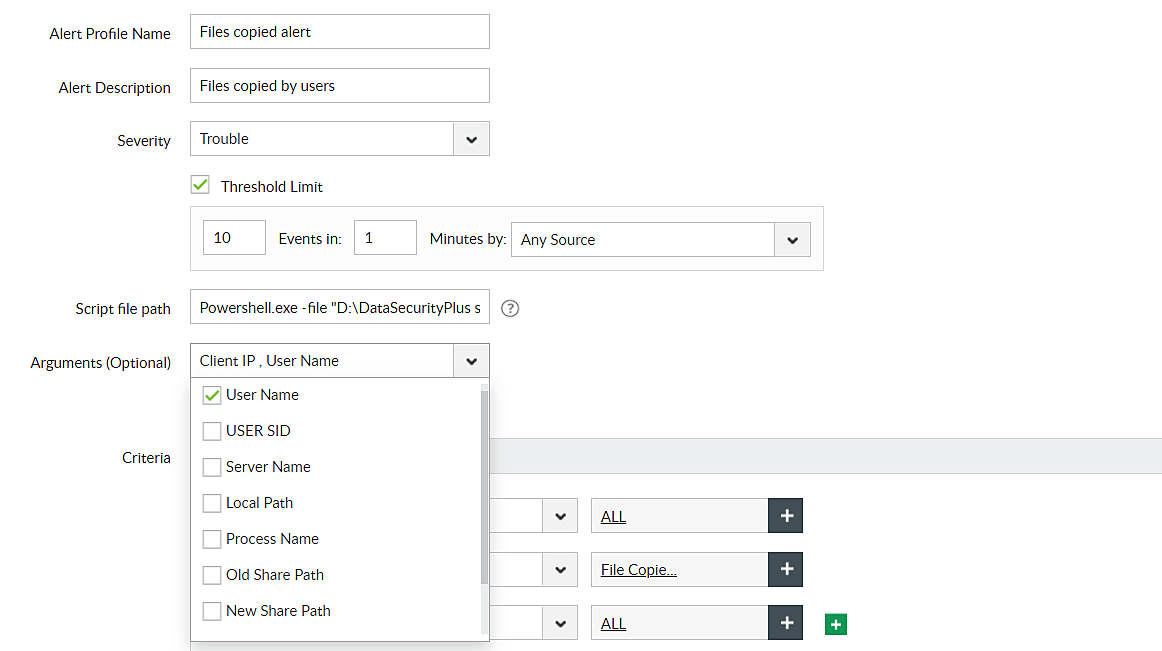
Step 3 - Choose the second argument.
PowerShell script instance
Powershell.exe -file "D:\DataSecurityPlus scripts\trigger-shutdown.ps1"
Argument 1: Client IP
VB script instance
Csscript "D:\DataSecurityPlus scripts\trigger-shutdown.vbs"
Argument 1: Client IP "
Note: If you want to add more arguments while configuring custom scripts, select the arguments consecutively as indicated above.
For further queries and assistance, please contact us at support@datasecurityplus.com.