Uncover insider threats, detect compromised accounts, spot anomalous activities, and distinguish malicious behavior from usual user activity using Log360.
Traditional security solutions protect your endpoints from various known threats. But they cannot detect advanced security threats from users and entities. Log360's user and entity behavior analytics (UEBA) module is powered by machine learning, which enables you to know about anomalous activities that threaten your organization's network security.
The solution creates a standard baseline of behavior for each user and entity in your network and any deviation from this baseline will be marked as an anomaly and assigned a risk score. This will enable security administrators to prioritize threats and mitigate their impact.
With Log360's UEBA console, you can analyze all anomaly trends and get insights on the number of detected anomalies, anomaly report statistics, and risk levels for users and entities in your network. You can also gain information on the top 10 anomalous activities and anomalies that are based on categories.
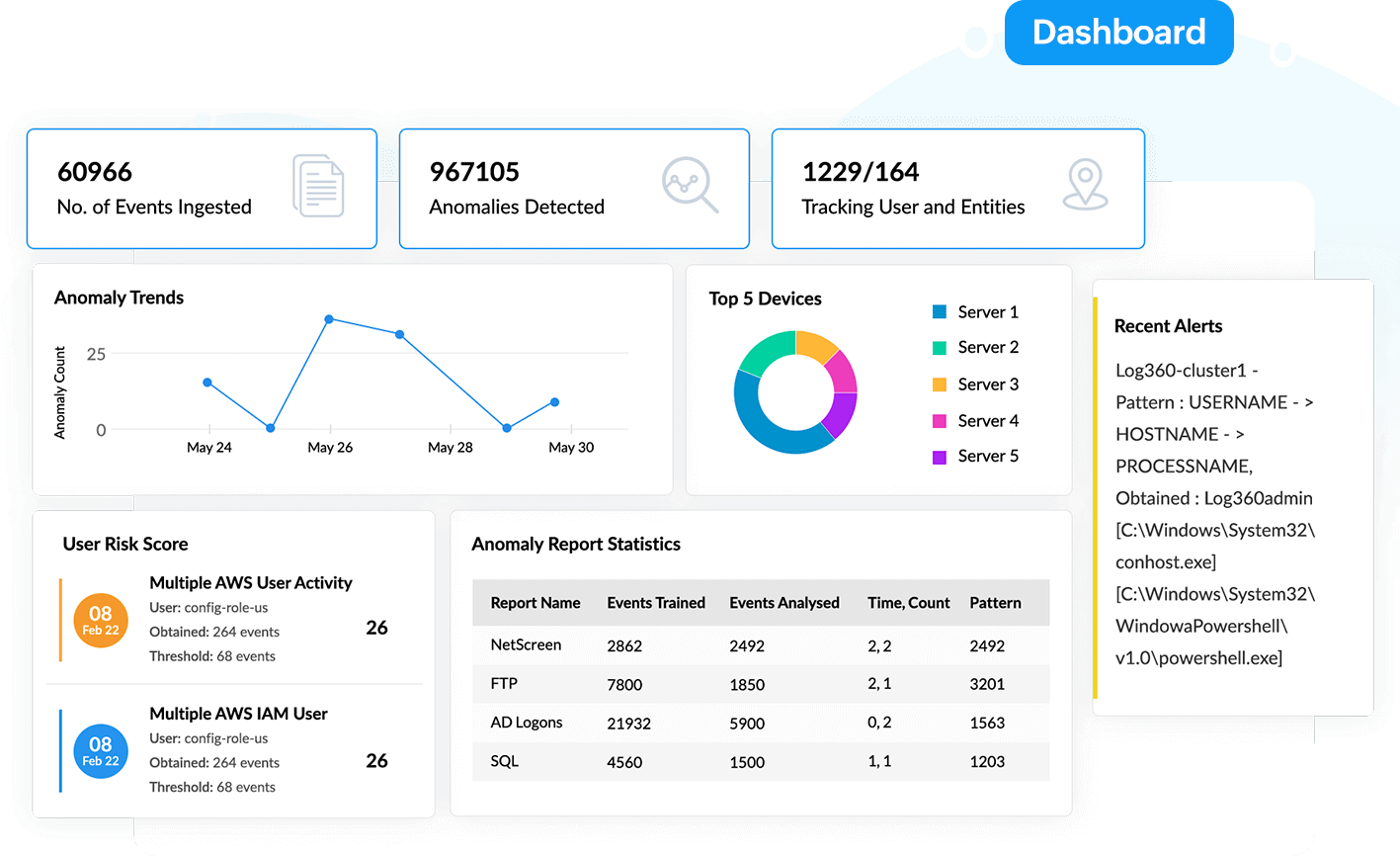
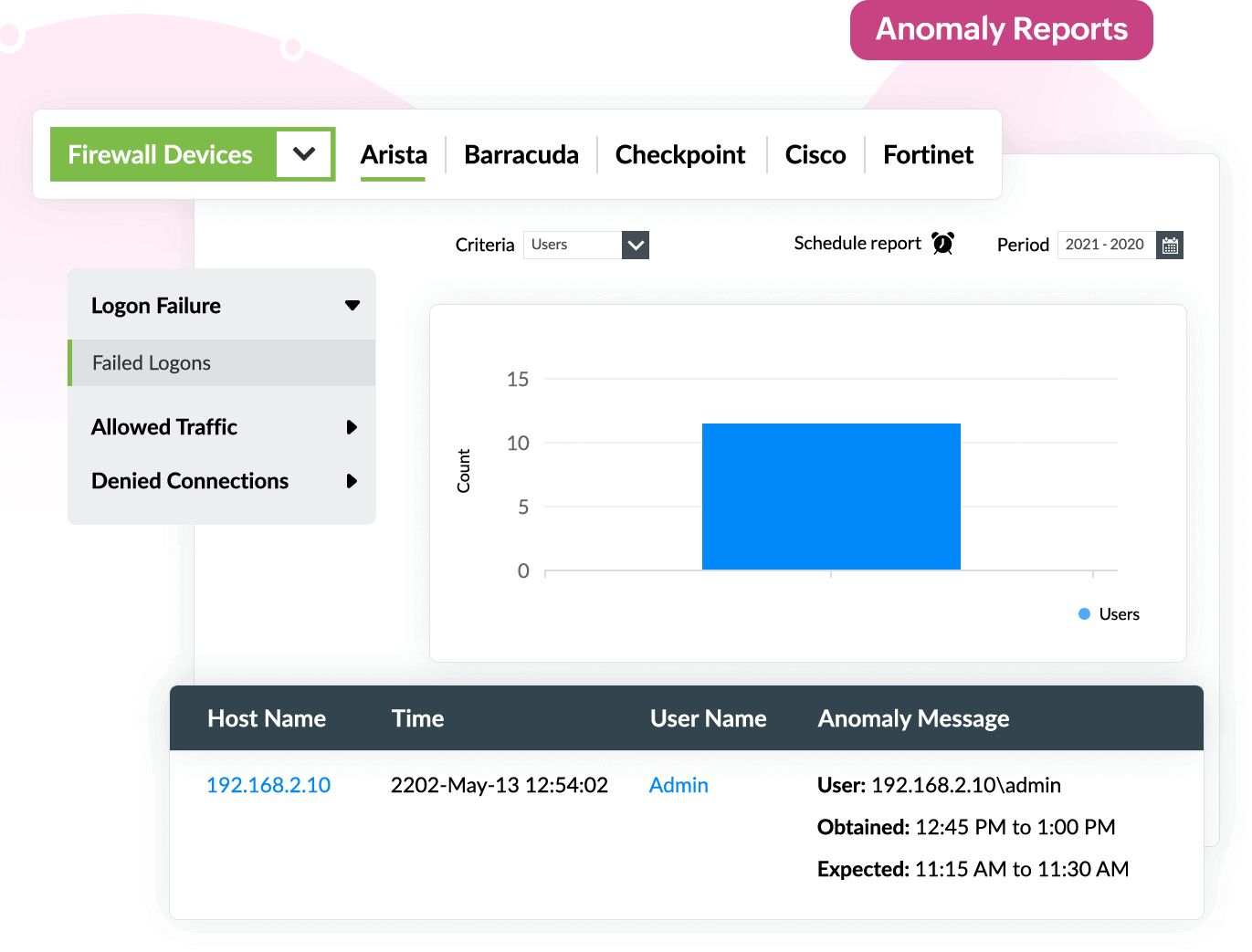
With Log360's security analytics dashboard, you can investigate security events that occur across your network. For example, let's consider an unusual situation for user A, who logs on at 11pm and accesses a few sensitive files and starts downloading them to a removable device. The solution will flag the sequential events as a time, count, and pattern anomaly. Using this information, the IT team can prevent a potential data exfiltration attempt.
With Log360's real-time alert system, you can get alerts about security events, which can improve incident resolution. Get instant notifications on detected suspicious activities across your network devices via SMS and email. You can also create alert profiles based on specific actions, entities, or cyberthreats, including insider threats, logon anomalies, compromised accounts, and more.
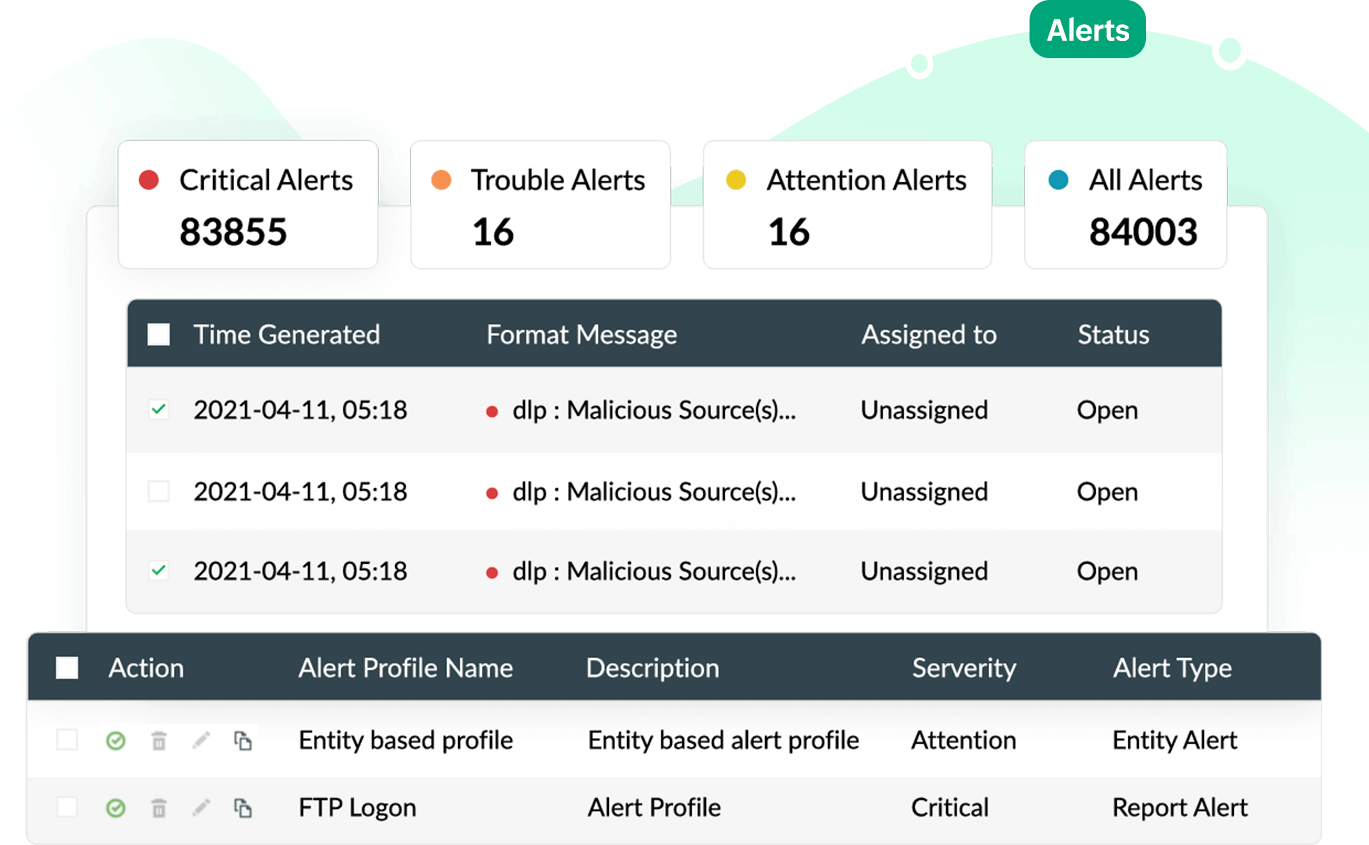
Log360's security capabilities will help you spot anomalous user activities such as logon anomalies, risk scores of users, and watchlisted users.
Log360's attack detection module is integrated with the incident management framework for speedy resolution.
Log360's incident workflows can be automated to mitigate security threats, thereby stopping attackers in their tracks and preventing a potential cyberattack.