- Home
- SIEM capabilities
- User behaviour analytics
- Behaviour Analytics
Analyze user behavioral data
to identify patterns, trends,
and anomalies in your network
Reduce attacker dwell time by detecting unknown threats using Log360's behavior analytics module.
Utilizing behavior analytics in cybersecurity
Even though thwarting security breach attempts is the primary goal for a security administrator, the real challenge is closing the gap on spotting different types of indicators of compromise. Traditional threat detection methods can pick up on known threats, but unknown threats might slip through the cracks if there's no readily available information on them.
Therefore, while deciding on a detecting strategy for your organization, it is important to keep in mind both known and unknown threats. With Log360's user and entity behavior analytics module (UEBA), which analyzes user behavior, you can track anomalous activities by suspicious users and entities, assign risk scores, and get alerted about anomalous activities in real time, reducing the dwell time of attackers lurking in your environment.
Assign risk scores to security events
While detecting threats, security administrators need to know which threat to tend to first. This will ensure that the most serious threats are quickly resolved first before they can cause significant damage. By assigning risk scores to different security events, security admins can quickly tend to high-risk threats.
With Log360, you can customize risk scores for different categories, including for anomalies, insider threats, data exfiltration, compromised accounts, and logon anomalies. You can also utilize contextual risk scoring for dynamic measuring of risks.
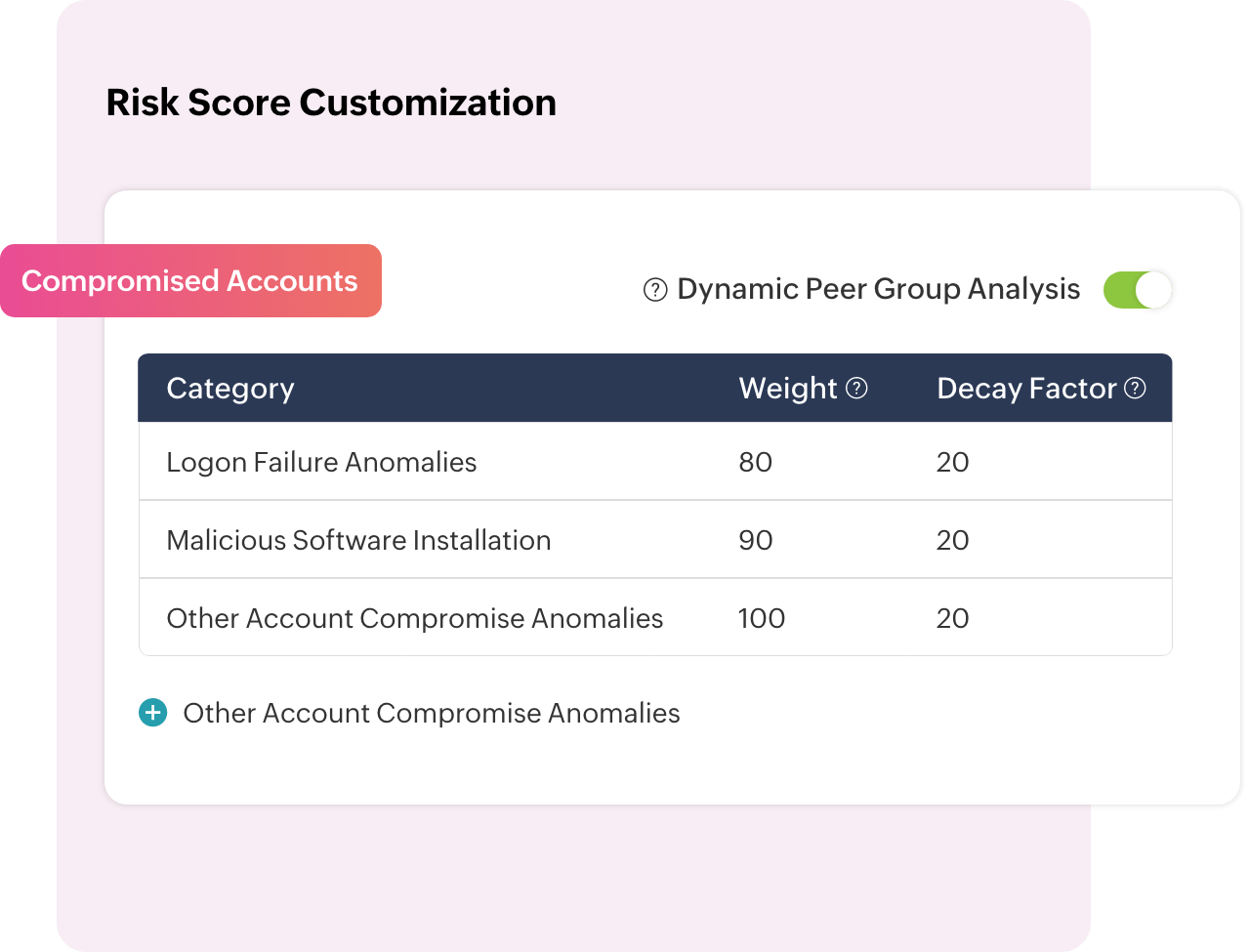
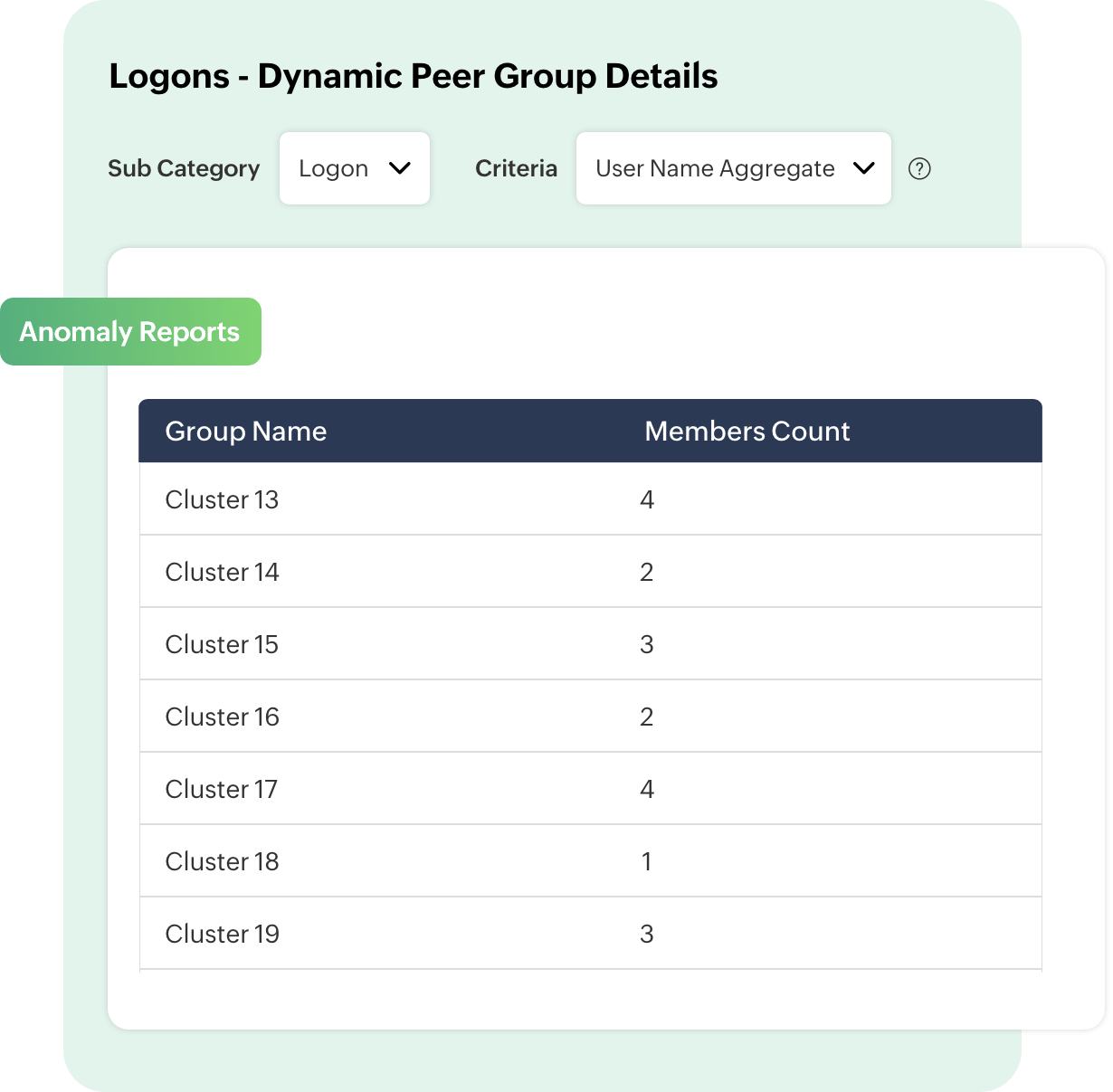
Build dynamic peer groups
By grouping users in a network based on the behaviors they exhibit, Log360's UEBA module establishes a baseline for the group. This baseline is then used as a reference to detect anomalies, and any deviation from this baseline will trigger an alert. This helps in improving accuracy in anomaly detection and reducing the number of false positives.
Streamline user identity mapping
Log360 UEBA uses mapping configurations to connect discrete user accounts to the base user account. This will help you correlate a single user’s anomalous activity across different platforms and devices, and consolidate these activities for effective user risk scoring.
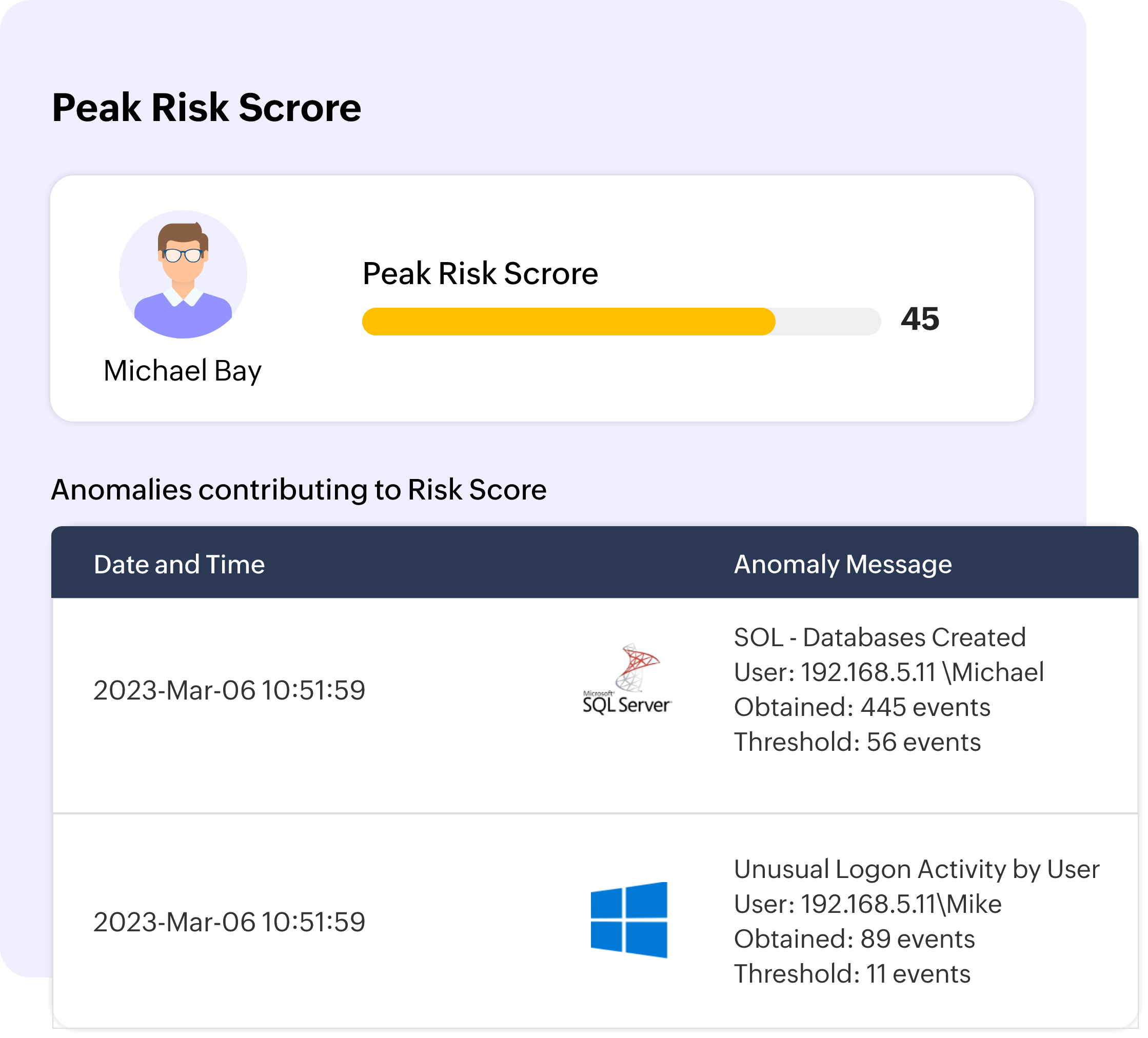
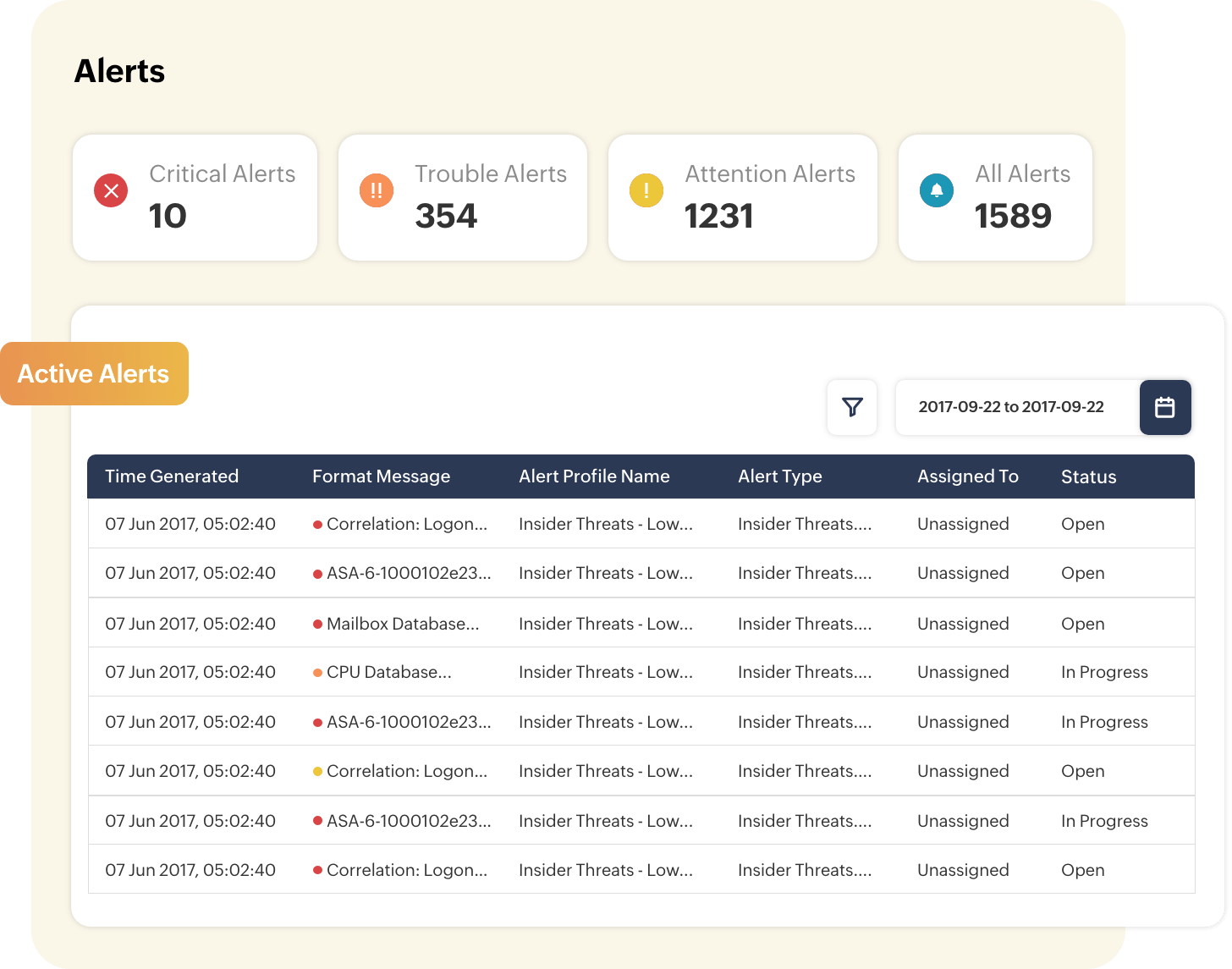
Reduce the dwell time of attackers
Get alerted about behavior-based security events through Log360's real-time alert system. You can get instant notifications via SMS and email, allowing security administrators to quickly tend to detected security threats and respond to them. This can ensure that any presence of external threats actors in your environment can be immediately identified, thereby reducing their dwell time.
Why choose Log360 for behavior analytics?
-
Monitor user and entity activities
Spot suspicious anomalies in your network by constantly monitoring the behavior of users and entities.
-
Protect against unknown threats
Any deviation from usual behavior will trigger an anomaly, thereby alerting you to unusual security threats in the network.
-
Automate your threat response
With Log360's workflow management, you can automate your response to security threats, instantly stopping cyberattacks that involve insider threats, compromised accounts, data exfiltration attempts, and more.


