With Log360, you can combat security concerns effortlessly and prevent rainy days in your cloud.
Today, multitudes of companies have moved to the cloud with the aim of expanding and modernizing, but in the process have exposed themselves to new and costly risks.
Cloud security is a multi-pronged approach that focuses on protecting data and business content while ensuring your business operations run efficiently. To help you achieve this goal, Log360 offers cloud security features that can ensure the smooth functioning of your business in a secure and protected cloud.
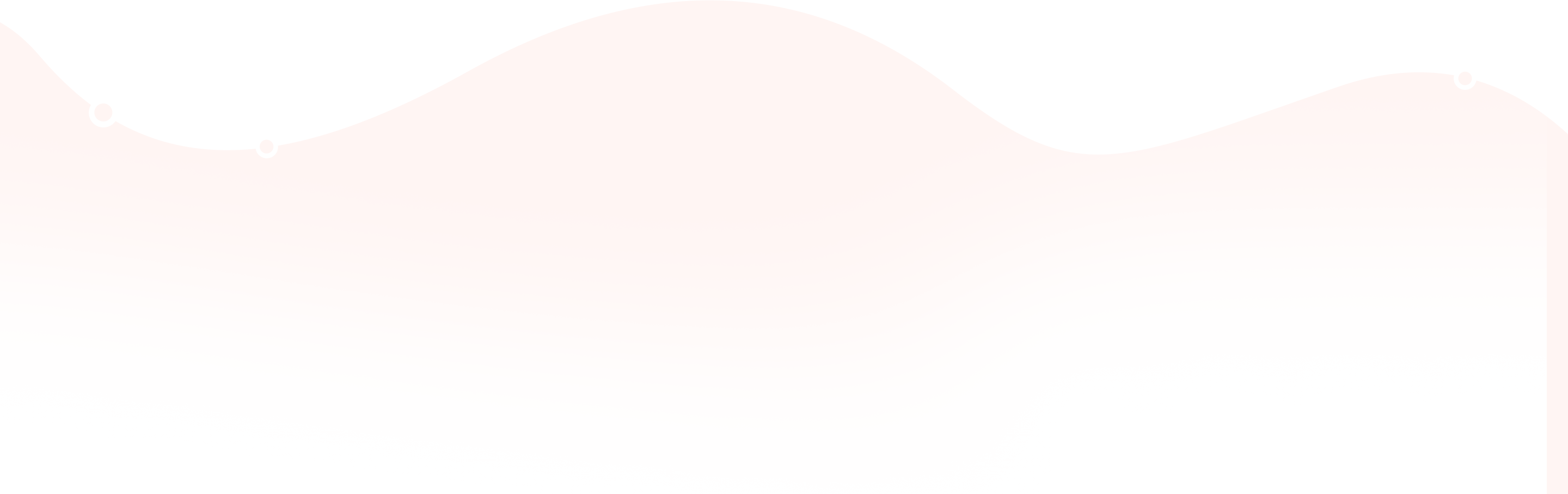
Ensuring your cloud data is accessible only to permitted personnel such as you and your authorized employees is critical to safeguarde your business.
Log360 allows you do just this by giving you actionable insights on user activities including unusual logons, unauthorized distribution of data, and potential data leak incidents. Using this information, any deviation can be instantly acted upon to prevent major data breaches.
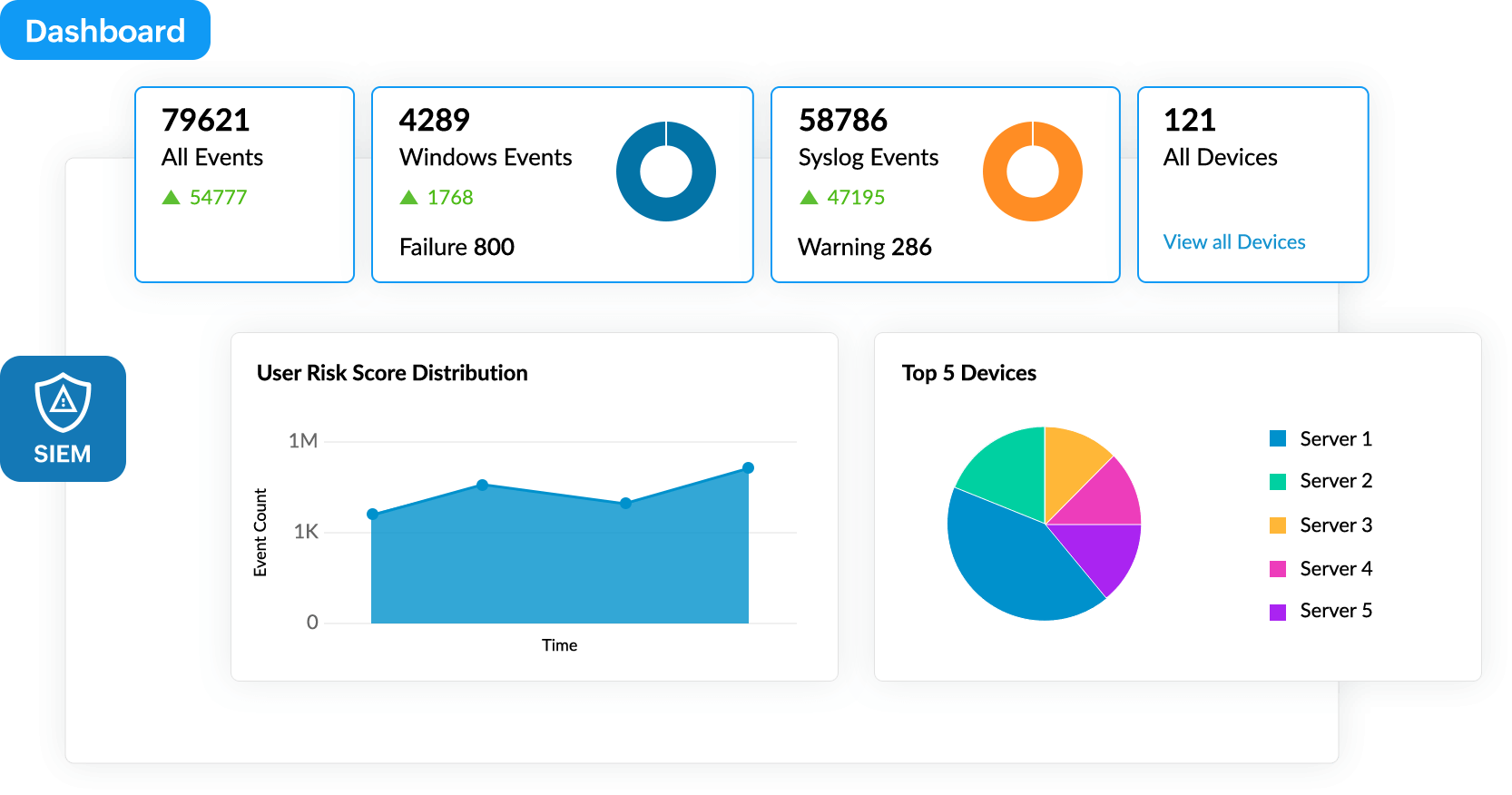
A crucial aspect of cloud security is ensuring the integrity of the data that is held within the cloud infrastructure. Log360 gives you complete visibility into your Amazon Web Service (AWS), Azure, Salesforce, or Google Cloud Platform (GCP) with predefined reports that give you deep insights on user activity, identity and access management, network security, cloud functions, GCP resource management, and more.
These reports enable you to compile all security data from different platforms and different models of cloud services such as IaaS, PaaS, and SaaS in a single console. Expedite threat resolution by automating your response to detected incidents using workflow options.
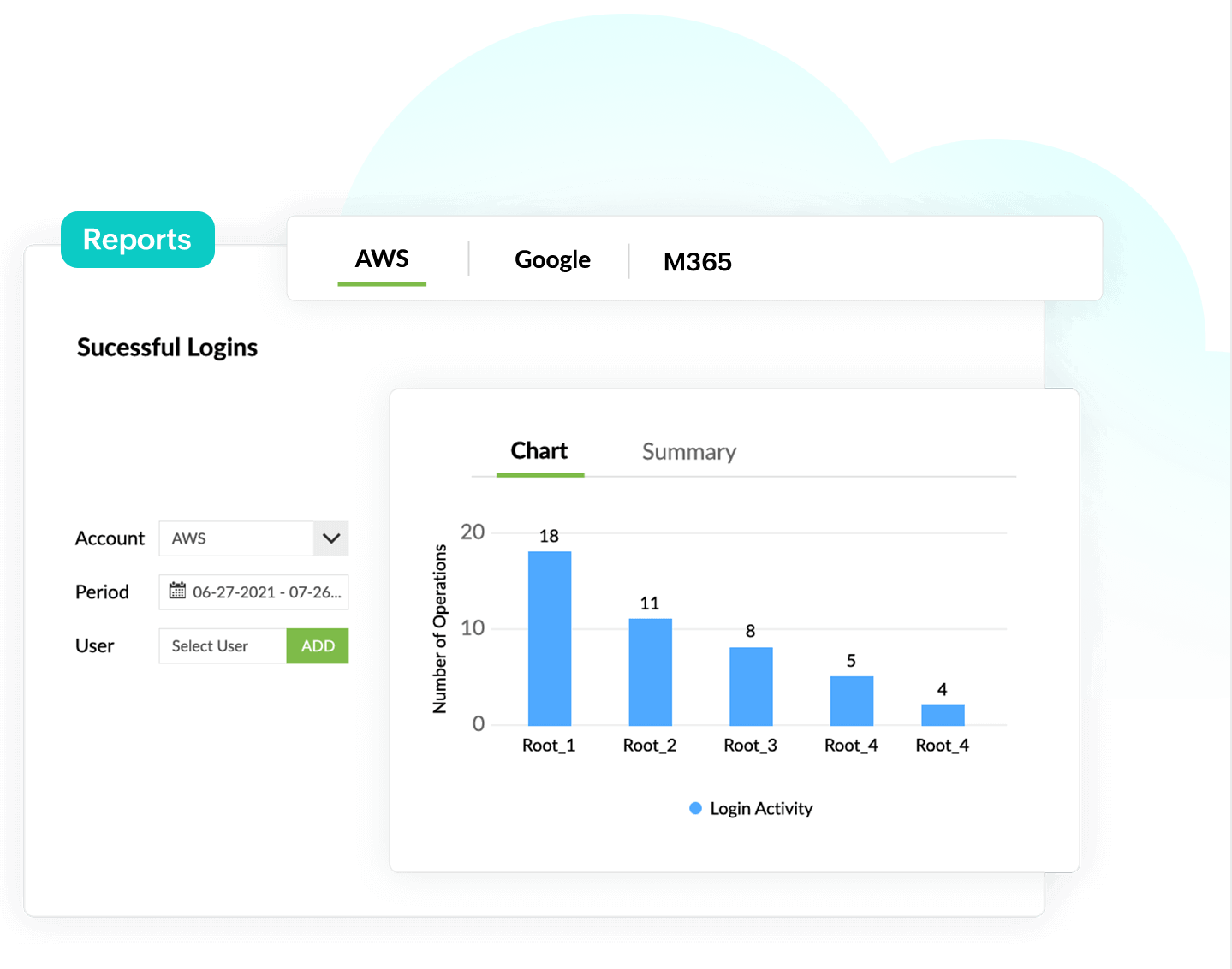
Apart from cyberattacks and security failures, human error is one of the top reasons for data breaches in the cloud. Log360 helps you overcome this obstacle by providing you with detailed reports on your cloud environment.
These reports include insights on changes made to network security groups, virtual networks, DNS zones, virtual machines, databases, and storage accounts. Any misconfiguration can easily be detected and acted upon, preventing costly mishaps.
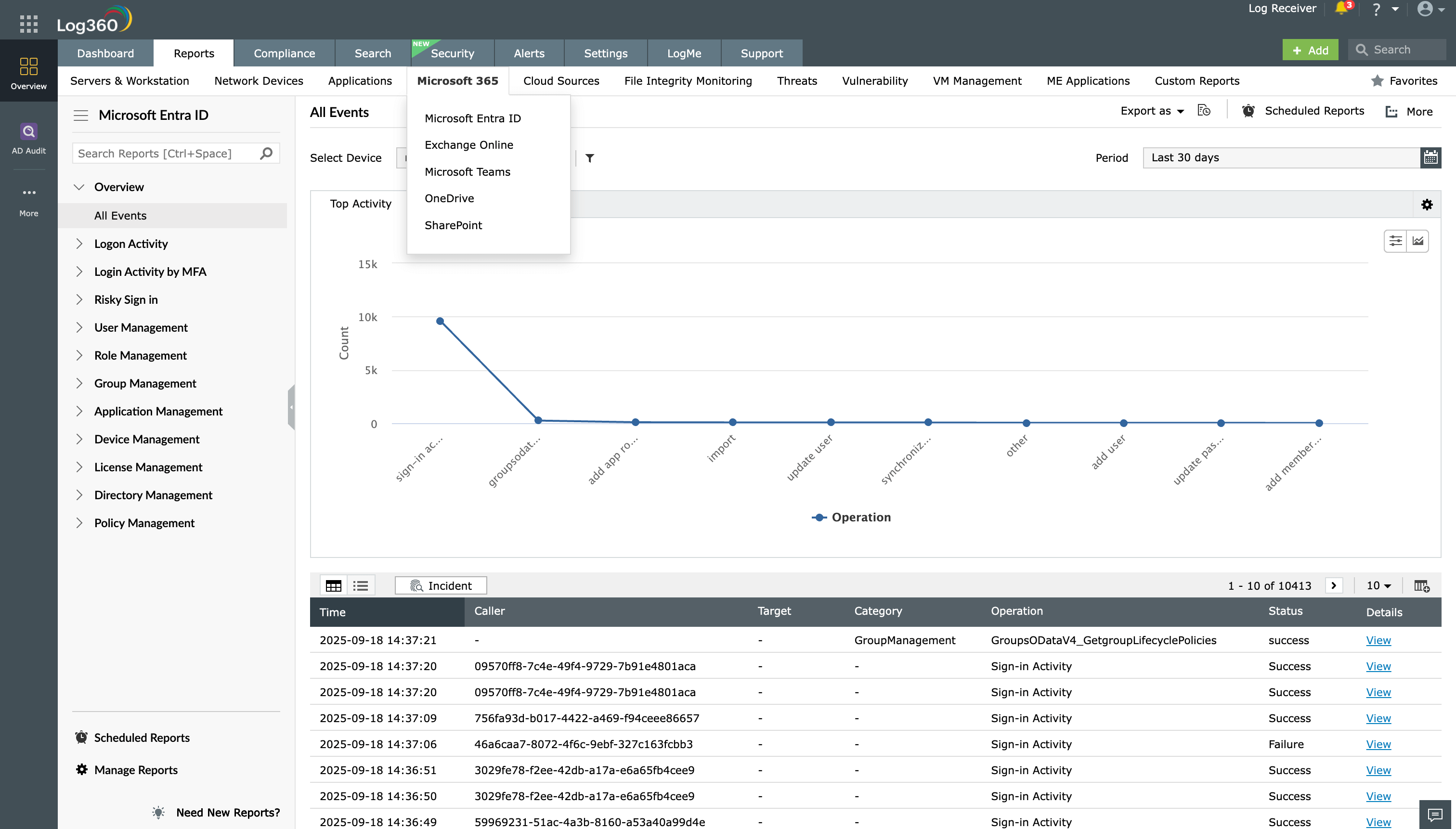
Log360 supports major public cloud platforms, including AWS, GCP, and Microsoft Azure.
A number of predefined reports provide detailed information on events that occur in Amazon EC2, Web Application Firewalls, Relational Database Service, Lambda, Security Token Service, Elastic Block Store, Virtual Private Cloud, Elastic Load Balancer, and Simple Storage Service.
Find what you're looking for with the smart log search engine and advanced search options.
Get notifications via email when unusual activities, web attacks, anomalous trends, and other security threats are detected.
Get detailed reports on network security, VPC activity, network services, hybrid connectivity, cloud functions, and App Engine.
Reports provide insights on user activity and any changes made to network security groups, virtual networks, DNS zones, virtual machines, databases, and storage accounts.
Instant alerts help track potential incidents and unusual access while predefined reports help with rapid investigation of user activity by tracking who did what, when, and from where.