What is a cyberattack?
- What is a cyberattack?
- Real-world impact: Notable cyberattacks worldwide
- History: A brief timeline of major cyberthreats
- Types of threats
- Emerging threats: Newer frontiers in cybersecurity
- Why is cybersecurity crucial?
- Cost of data breaches
- The need for a proactive defense strategy
- How SIEM solutions can prevent cyberattacks
What is a cyberattack?
A cyberattack is an attempt by hackers or malicious actors to damage, disrupt, or gain unauthorized access to computer systems, networks, or digital devices, often with the intent of stealing, altering, or destroying data. These attacks can target individuals, organizations, governments, or entire nations.
Real-world impact: Notable cyberattacks worldwide
- 2017 Equifax data breach
One of the largest recorded, this breach exposed the personal information of 147 million people, including Social Security numbers, birth dates, and addresses. The breach cost Equifax over $4 billion in total.
- 2017 WannaCry ransomware attack
This global ransomware attack affected over 200,000 computers across 150 countries, crippling hospitals, businesses, and homes. The damages from this single attack were estimated to be in the billions of dollars.
- 2020 SolarWinds attack
A sophisticated supply chain attack that compromised the systems of thousands of organizations, including multiple United States government agencies. This attack highlighted the vulnerabilities even in the most secure networks.
- 2021 Apache Log4j vulnerability
The "Log4Shell" vulnerability in the Apache Log4j library presented a critical remote code execution risk. Due to its widespread use in systems and applications globally, the flaw led to immediate and extensive exploitation efforts, revealing vulnerabilities in the global software supply chain.
- 2023 MOVEit attack
Hackers exploited a security vulnerability in MOVEit, a file transfer tool used by organizations worldwide, to launch data exfiltration attacks that affected hundreds of organizations.
According to a report by Cybersecurity Ventures, cybercrime damages are expected to reach $8 trillion annually by 2023.
History: A brief timeline of major cyberthreats over the years
- 1971
- 1986
- 1988
- 1990s
- Early 2000s
- Mid-2000s
- 2010s
- Present
1971 - Creeper worm
The Creeper worm is considered one of the earliest instances of self-replicating malware. It spread across ARPANET, displaying the message "I'm the creeper, catch me if you can!"
1986 - Brain virus
The Brain virus was one of the first PC viruses. It infected boot sectors of floppy disks, slowing down systems and displaying a copyright notice.
1988 - Morris worm
Created by Robert Tappan Morris, the Morris worm was one of the first internet worms. It inadvertently caused widespread disruption, slowing down thousands of computers.
1990s - Emergence of malware
The 1990s saw the rise of various types of malware, including viruses, worms, and Trojans. Notable examples include the Michelangelo virus and the Melissa virus.
Early 2000s - Code Red and Nimda
The Code Red worm targeted Microsoft IIS servers, while Nimda spread rapidly through email attachments and network shares
Mid-2000s - Botnets and phishing
Botnets like Storm Worm emerged, capable of launching DDoS attacks. Phishing attacks increased, tricking users into revealing sensitive information.
2010s - Ransomware dominance
Ransomware attacks surged, with notable strains like CryptoLocker and WannaCry. State-sponsored attacks, like Stuxnet, demonstrated the potential for cyber-physical damage.
Present - APTs
Advanced persistent threats (APTs) are highly sophisticated attacks targeting specific organizations or entities. These attacks involve prolonged and stealthy campaigns for data exfiltration or espionage.
Types of cyberthreats
Malware
Malware is a broad term for malicious software that includes viruses, worms, and Trojans. Malware is designed to infiltrate systems, steal data, disrupt operations, or gain unauthorized access.
Ransomware
Ransomware encrypts a victim's data and demands a ransom for decryption. Notable examples include CryptoLocker, Ryuk, and Maze.
Learn morePhishing
Phishing involves tricking individuals into revealing sensitive information through fraudulent emails, websites, or messages. Spear phishing targets specific individuals.
Learn moreSocial engineering
This technique manipulates individuals into divulging confidential information. It often exploits psychological vulnerabilities to gain unauthorized access.
Learn moreA study by the University of Maryland found that, on average, a cyberattack occurs every 39 seconds.
Emerging threats
AI-powered attacks
Malicious actors are using AI and machine learning to enhance the sophistication of attacks. AI-generated phishing emails and deepfake attacks are on the rise.
Learn moreIoT vulnerabilities
The proliferation of Internet of Things (IoT) devices has introduced new security challenges. Vulnerable devices can be exploited to gain access to networks.
Learn moreSupply chain attacks
Attackers target third-party vendors or suppliers to compromise larger organizations. The SolarWinds and Kaseya attacks are recent examples.
Learn moreCyber-physical attacks
Attacks targeting critical infrastructure, such as power grids and transportation systems, pose a threat to physical safety.
Quantum computing threats
The advent of quantum computing could break existing encryption methods, leading to a need for quantum-resistant cryptographic solutions.
Learn moreWhy is cybersecurity crucial for enterprises?
Expansive digital transformation has unlocked levels of efficiency, connectivity, and innovation never known before. But with these advancements comes a host of vulnerabilities. Here's why cybersecurity has become non-negotiable for enterprises:
- Digital dependence: As businesses, governments, and individuals become more dependent on digital systems, the potential impact of cyberattacks grows. A breach can disrupt operations, leak confidential data, and erode trust.
- Economic implications: Cyberattacks can lead to significant financial losses, not just from the immediate fallout of an attack but also from the subsequent loss of consumer trust and potential legal implications.
- Ubiquity of connected devices: The IoT has led to a surge in connected devices. Each device represents a potential entry point for cyberattackers.
- Evolving threat landscape: Cyberthreats are not static. They evolve, adapt, and become more sophisticated. Enterprises must be proactive in their cybersecurity efforts to counteract these evolving threats and protect their assets.
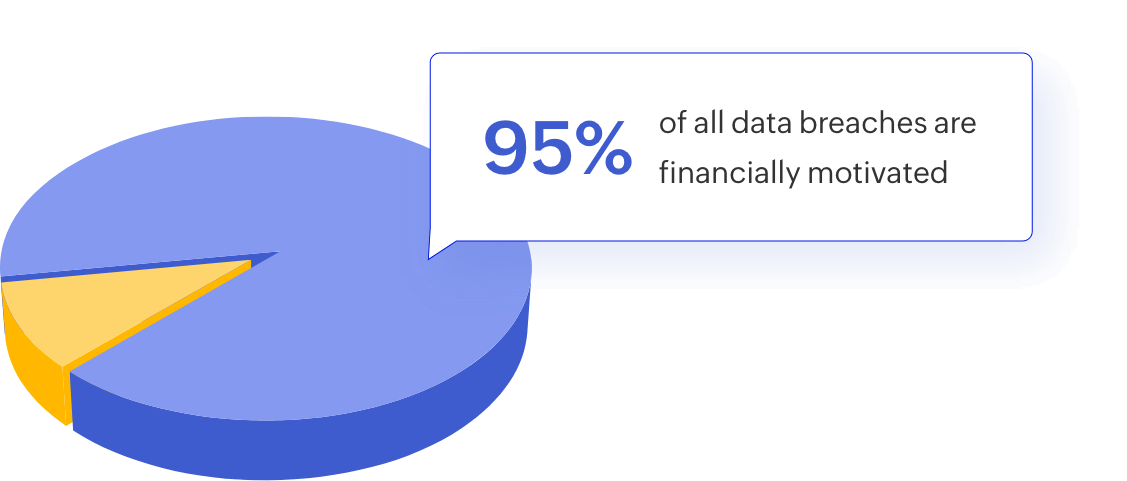
Cost of data breaches: Financial and reputational impacts
-
Financial impact:
Data breaches have substantial financial consequences. Costs include legal fees, fines, forensic investigations, data recovery, and potential legal settlements.
-
Reputational damage:
A data breach can lead to loss of customer trust and loyalty. Organizations may struggle to regain their reputation, which can negatively affect their bottom line in the long term.
-
Legal and regulatory consequences:
Many industries are subject to data protection regulations. Non-compliance with regulations like the PCI DSS, FISMA, the GDPR, or HIPAA can result in severe penalties.
See your savings in real time!
Our ROl calculator reveals how much you can save with Log360
How to prevent a cyberattack
Organizations should have a proactive defense strategy to protect their business against cyberattacks. Proactive cybersecurity involves anticipating and preventing threats before they happen. It involves strategies like threat hunting, continuous monitoring, vulnerability assessments, and implementing security controls to reduce attack surfaces.
Advantages of proactive defenses
- Reduced impact Proactive defense minimizes the impact of potential breaches. By identifying vulnerabilities and addressing them before attackers exploit them, organizations can significantly reduce the risk of data compromise.
- Cost savings While investing in proactive defence requires resources, the cost of mitigating a breach is always far higher. Data breaches can lead to legal fines, loss of customers, reputational damage, and recovery expenses.
- Time savings Responding to a breach is time-consuming and can disrupt business operations. Proactive measures prevent such disruptions, allowing organizations to focus on growth rather than recovery.
- Reputation protection A data breach can erode trust and damage a company's reputation. Proactively protecting data demonstrates commitment to security, fostering customer confidence.
To defend your organization against cyberthreats proactively, tools like log management and security information and event management (SIEM) solutions will be of great help.
Related SIEM resources
- Ebooks
- Whitepapers
- Case Studies
How SIEM helps prevent cyberattacks
Using a SIEM solution like Log360 helps organizations enhance their security posture, respond swiftly to potential threats, maintain regulatory compliance, stay updated on emerging threats, and achieve a cost-effective approach to security management. Here are some of the key features of Log360 that helps you in thwarting cyberattacks:
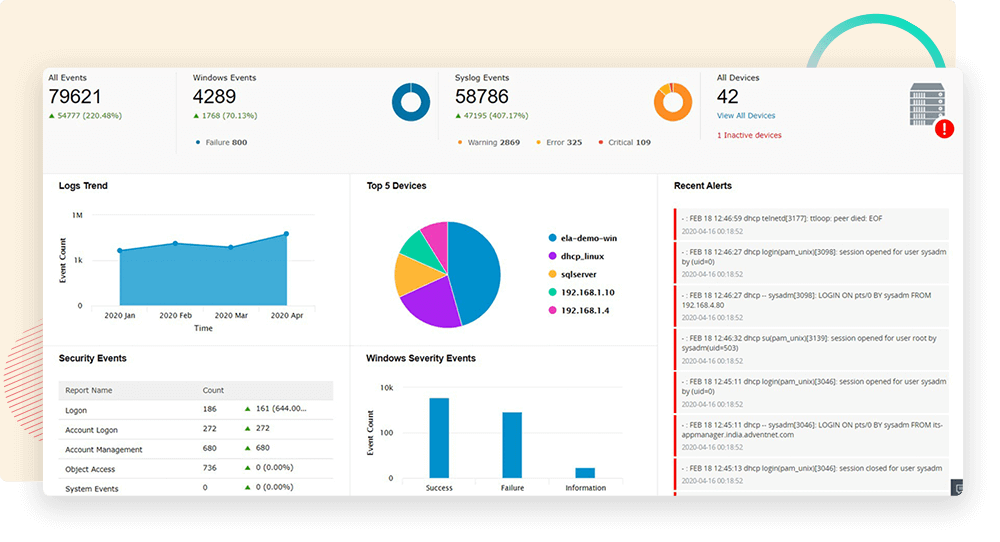
Centralized monitoring
Log360 consolidates logs from various sources like devices, applications, and databases, allowing security professionals to monitor all events from a single interface.
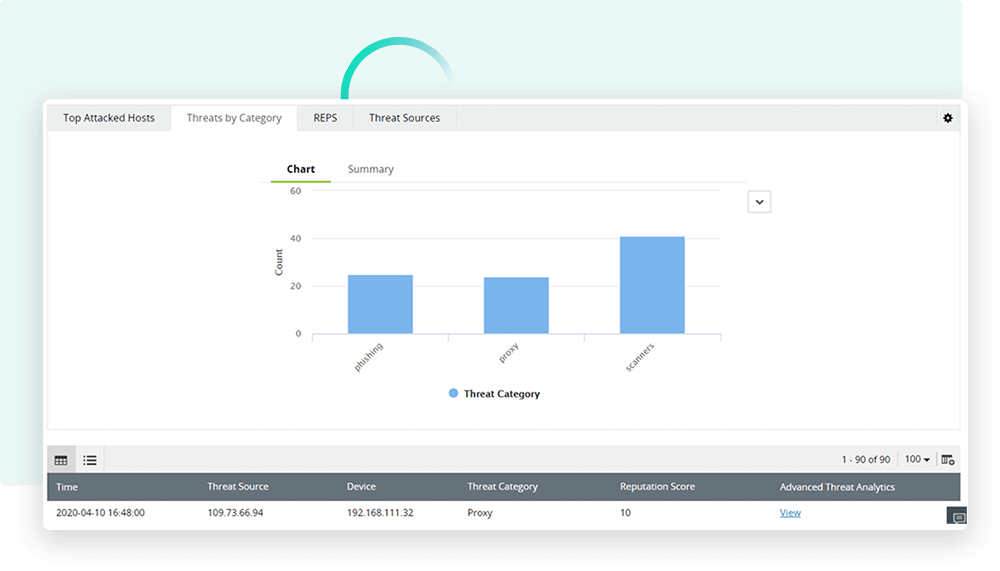
Real-time threat detection
With its advanced correlation engine, Log360 identifies anomalies and suspicious activities as they happen, minimizing the time taken to detect potential threats.
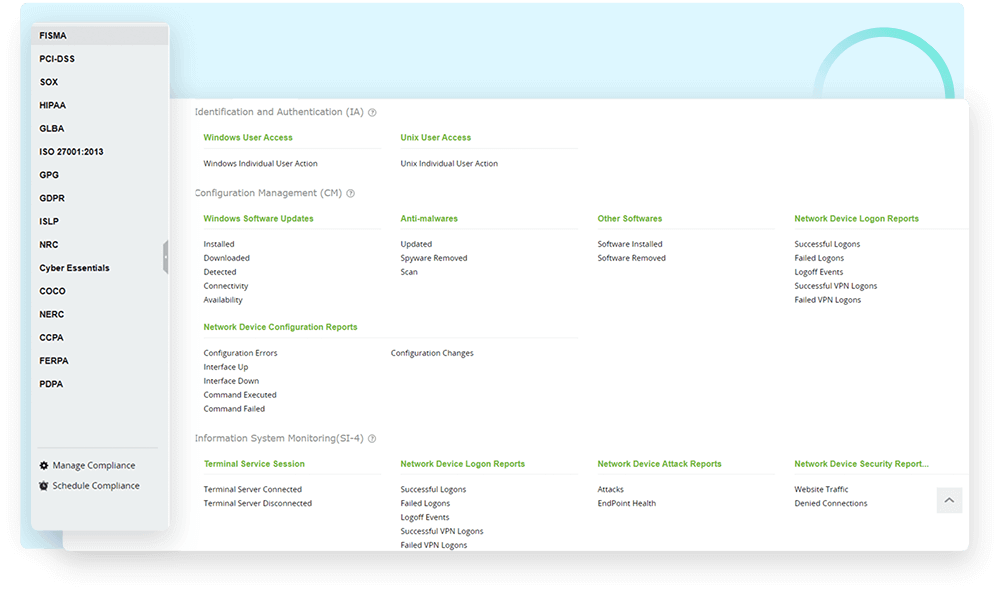
Comprehensive reporting
Log360 comes equipped with out-of-the-box compliance reports for various regulations, ensuring organizations can meet regulatory requirements with ease.
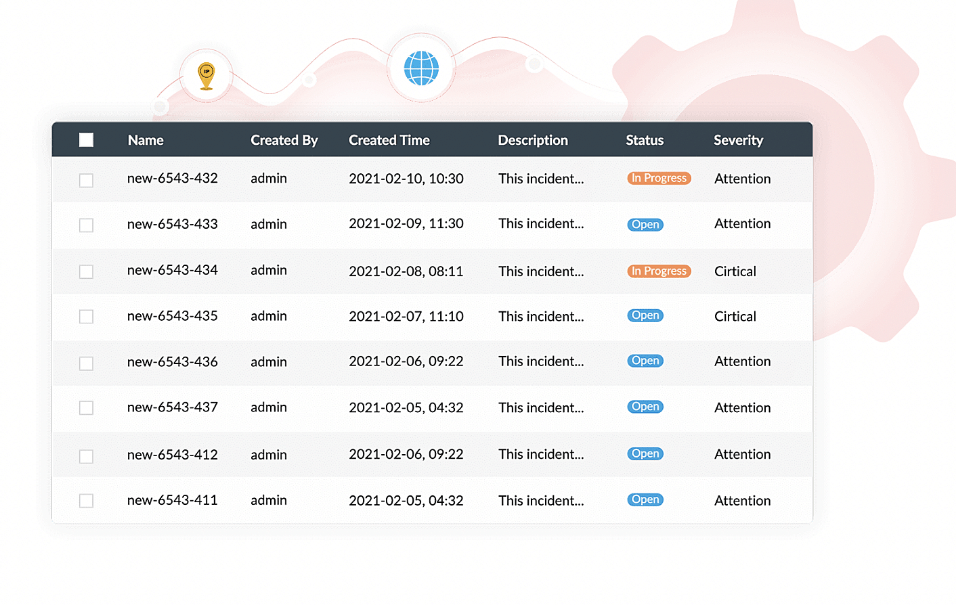
Forensic analysis
If a security incident does occur, the historical data and context provided by Log360 can significantly aid in determining the root cause, assessing damage, and planning the recovery.
User activity monitoring
By tracking user activities across various systems, Log360 helps in identifying insider threats, privilege misuse, and unauthorized access.
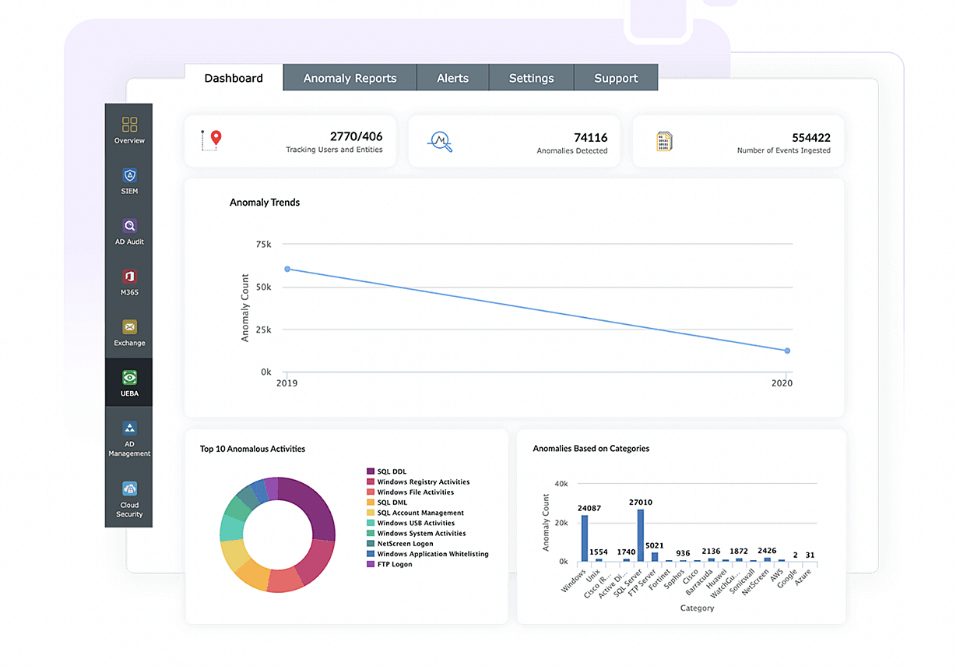
Explore ManageEngine's SIEM solution
ManageEngine Log360, recognized in the Gartner® Magic Quadrant™ for SIEM six consecutive times, is a unified SIEM solution with integrated DLP and CASB capabilities that detects, prioritizes, investigates, and responds to security threats. It combines threat intelligence, machine-learning-based anomaly detection, and rule-based attack detection techniques to detect sophisticated attacks, and offers an incident management console for effectively remediating detected threats. Log360 provides holistic security visibility across on-premises, cloud, and hybrid networks with its intuitive and advanced security analytics and monitoring capabilities. Try out Log360 today by downloading a fully functional, 30-day, free trial of Log360 with no restrictions.


