Almost 90% of businesses employ Active Directory in their IT environments to manage user accounts and control access, according to a report released by Cyber Defense Magazine. It's not surprising that cyberattackers find AD a lucrative target. The same report notes that 95 million AD accounts are targeted everyday.
Exploiting user accounts and leveraging them as an entry point to perform an attack is a tactic actively used by attackers. To combat these malicious actions, organizations should continually monitor their AD.
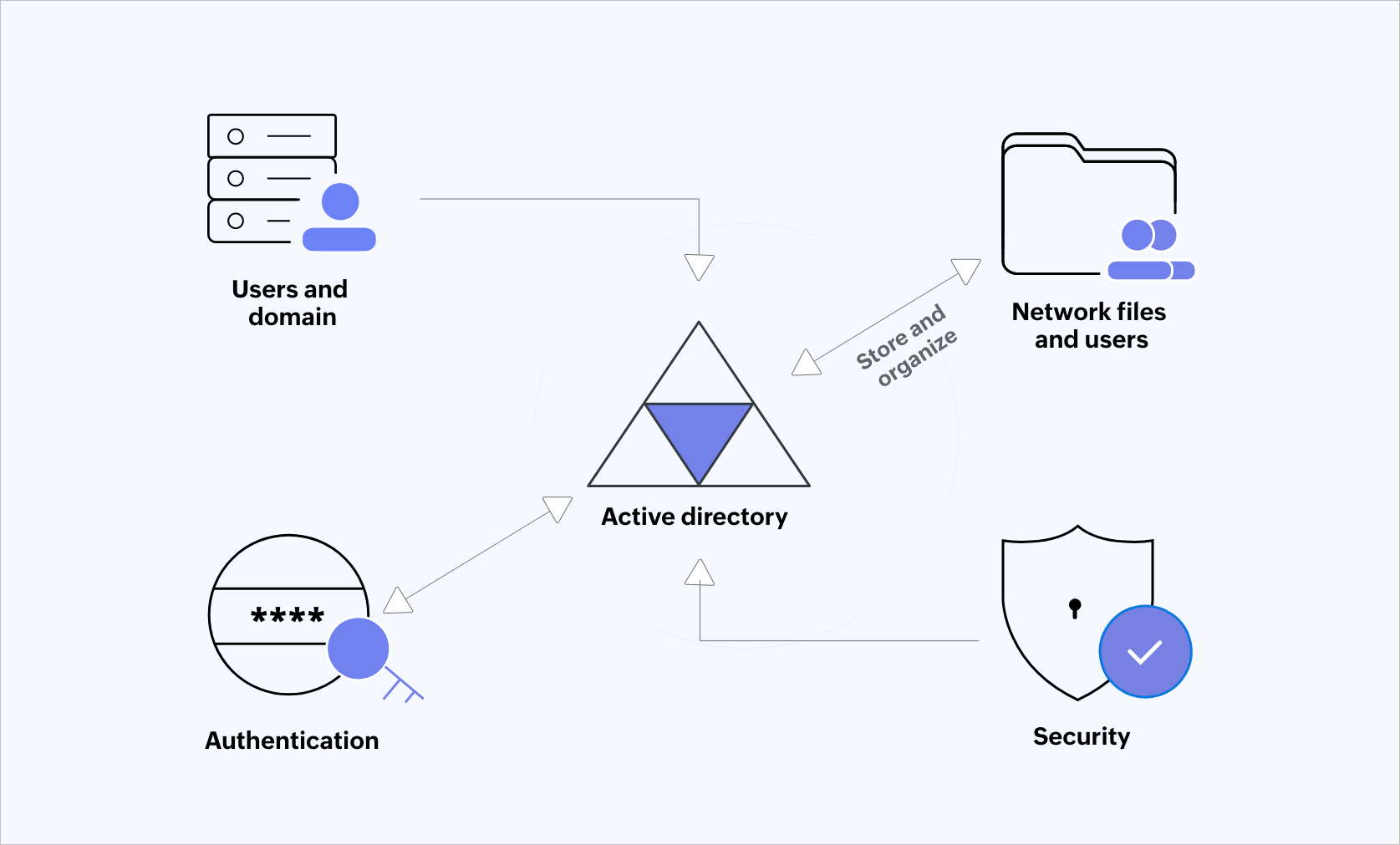 Figure 1: Active Directory.
Figure 1: Active Directory.
Along with addressing the importance of securing AD, this blog provides a 13-point security checklist that helps you protect AD from targeted attacks.
Active Directory is Microsoft's proprietary service that enables admins to manage and access network resources. It helps to store and organize information about various objects such as network resources, shared folders, files, and users. It also handles interaction between users and domains. AD plays a major role in verifying the user's identity.
An attacker who obtains initial access into your AD will try to escalate privileges, move laterally and vertically, and ultimately compromise the domain administrator account. If this happens, the threat actor can go after the domain controller of your AD environment. This is one of the methods the hacker can use to compromise the domain controller. By doing this, the attacker can perform malicious actions such as deletion and modification of sensitive data that is contained within your member servers, workstations, or any other device (refer to Figure 2). Thus, it is important to protect your AD environment.
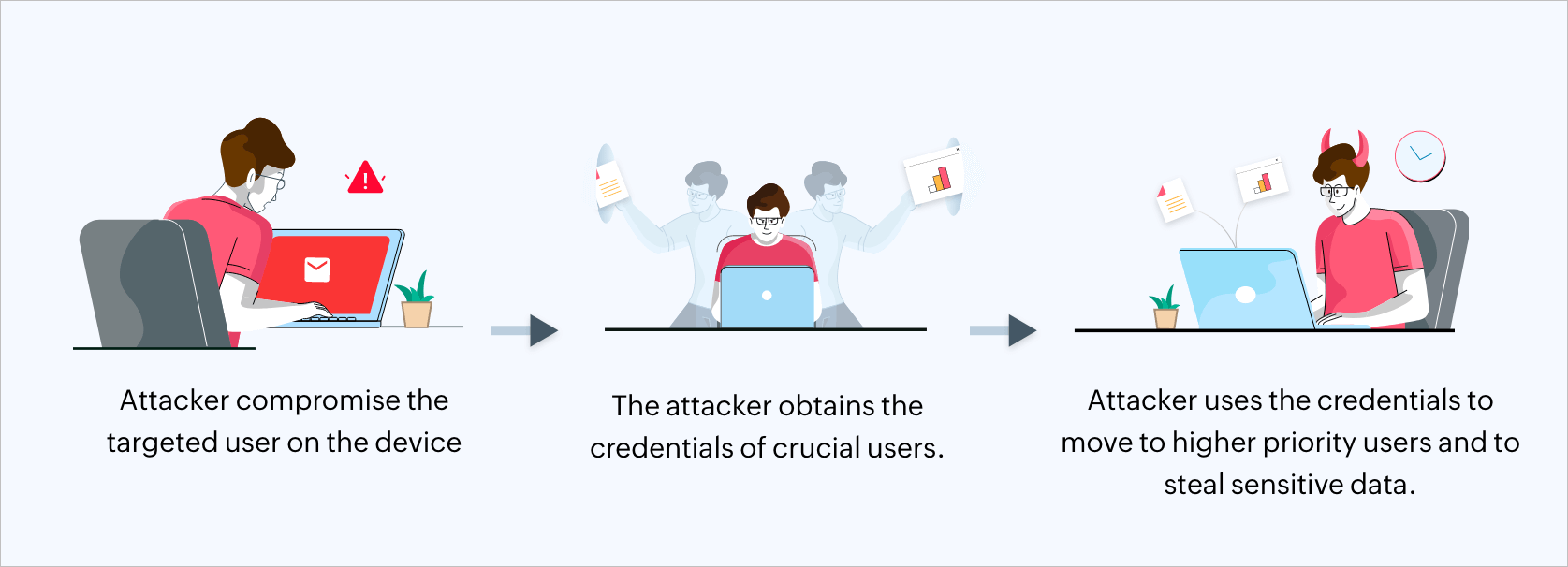 Figure 2: The AD attack process
Figure 2: The AD attack process
Update and patch consistently: The known, unpatched vulnerabilities are the easiest path for attackers to exploit the system. You should deploy vulnerability scanners and patch scanning to detect these vulnerabilities. Ensure that all of your AD servers, operating system, and applications are patched and up-to-date to reduce vulnerabilities.
Secure administrative privileges: A specific administrator is assigned to each of the domains in AD. Administrative privileges should only be granted to those who require them to perform their tasks. Use separate administrative accounts for daily tasks, and administrative activities.
Utilize indestructible password policies: Use only complex passwords that include a combination of uppercase, lowercase, numbers, and special characters. Try using passphrases. Keep changing your passwords regularly and discourage password reuse.
Implement multi-factor authentication: MFA adds an extra layer of security. For example, to verify their identity, ask users to provide supplementary authentication factors such as a code, or their biometric from a mobile app. The attackers would now need a second set of credentials to login successfully. t, Even if their password gets compromised, this prevents the attackers from accessing network resources.
Review and monitor your AD continuously: Monitor your AD environment to track suspicious activities that might end up compromising user accounts. Enable proper auditing policies to track critical events, and generate alerts for potential breaches. Here are some of the functions that should be monitored and regularly reviewed to secure your AD data:
| Platform | Security measures to take |
|---|---|
| AD environment |
|
| Azure AD |
|
| File servers |
|
| Windows server |
|
| Windows workstation |
|
Table 1: Security measures to protect your AD environment
Implement network segmentation: Isolate the critical AD infrastructure from other network resources by using micro segmentation. This limits lateral movement, which helps in minimizing the potential compromises.
Use secure protocols: Use protocols like LDAP and SMB signing to configure your AD environment. Encrypt communication channels between AD servers and the client to protect against eavesdropping and tampering.
Apply strong firewall rules: Restrict external networks from accessing your AD ports and protocols. Ensure that appropriate firewall rules are implemented to allow only the necessary network traffic to and from the AD servers.
Utilize well-organized backups and recovery plan: Perform regular backups of your AD data, and regularly check if the restoration process is happening properly. Create a comprehensive disaster recovery plan to mitigate the impact of potential data breaches and other disasters. Here are a few tactics you can follow to enhance your recovery plan:
Apply security baselines and bench marks: A default Windows operating system installation contains many unsafe features, services, default settings, and valid ports.These default settings should be checked against known security standards. This will reduce the chances of an attack while still maintaining the functionality of the OS. The following resources mentioned below will allow you to analyze and test against Microsoft’s recommended security configuration baselines:
Provide user training to increase security awareness: Developing a security conscious culture within the organization is vital to prevent attacks. Educate the users about common security threats and their preventative strategies.
Delete unnecessary accounts: You need to follow a procedure to identify inactive users. If not, these unused accounts can be used by attackers for their own benefit. Make sure to deactivate or delete dormant accounts as soon as possible.
Standardize group names: AD admins will be able to quickly understand the organizational structure if there are fewer AD groups. By standardizing AD group names, you can avoid confusion. This also helps prevent unwanted access by attackers.
Active Directory is a blessing in disguise for many in IT. It helps IT admins verify user identities, as well as access and manage various facets of network resources. Since AD is a key component of network security, the IT team's focus should be on continually defending it against attacks. Regularly assessing and updating security measures, as well as performing penetration testing, is vital. Staying up-to-date on the latest security trends and best practices is also key to protecting your AD environment.
To dwell deep into the structure and functions of AD, please refer to this series.
With a comprehensive SIEM solution that detects, prioritizes, investigates, and responds to security threats, you can secure your AD environment.
With an effective SIEM solution, you can easily perform these actions:
To learn how you can efficiently secure your organization's AD environment, schedule a free, personalized demo of ManageEngine Log360, a unified SIEM solution.
You can also explore on your own with a free, fully functionally, 30-day trial of Log360.
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.