It is becoming a common adage that security teams are overwhelmed with alerts; while some of these alerts are false positives, others are true positives that they tend to overlook. When alerts start stacking up and don't get dealt with promptly or at all, important issues may go unnoticed and spiral out of control, ultimately resulting in a huge breach. The time it takes to detect and respond to security incidents should be as short as possible to limit the time an attacker has to carry out the attack.
With incident response automation, security teams don't have to take standard, repetitive response measures anymore. There are four steps to automate your incident response processes effectively using a SIEM solution.
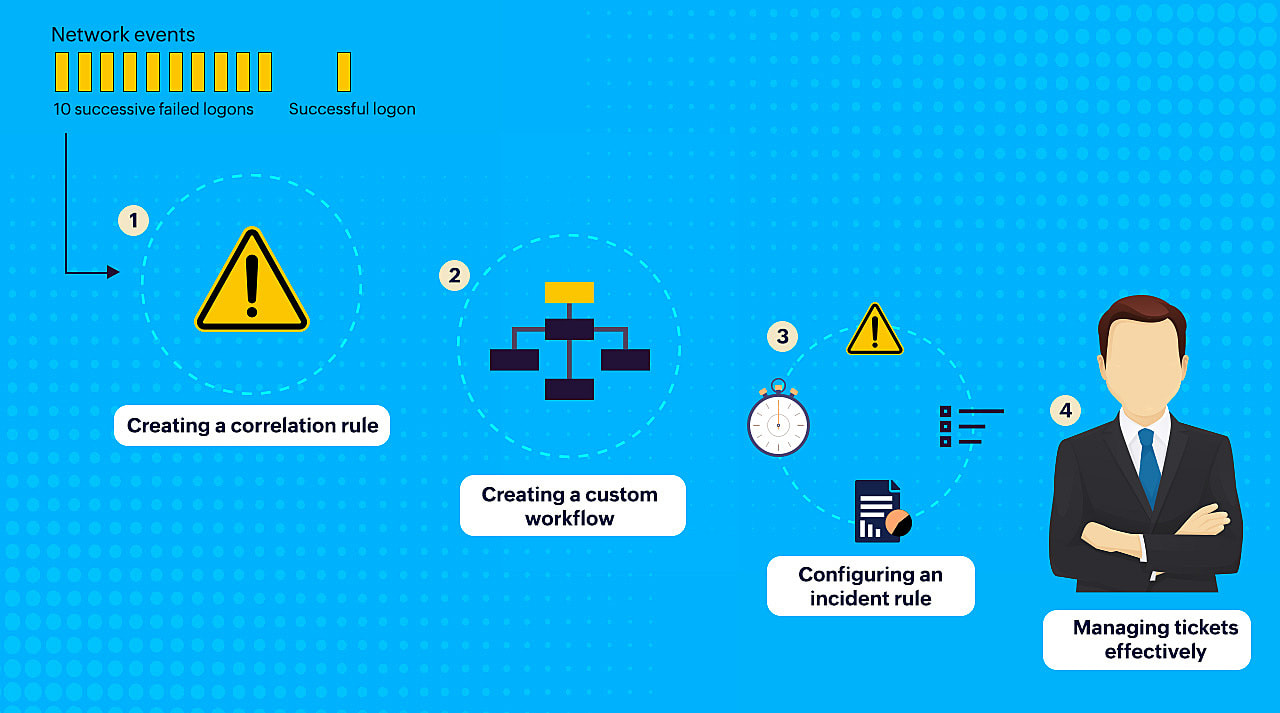
Let's take a closer look at these four steps in a simple brute-force attack scenario.
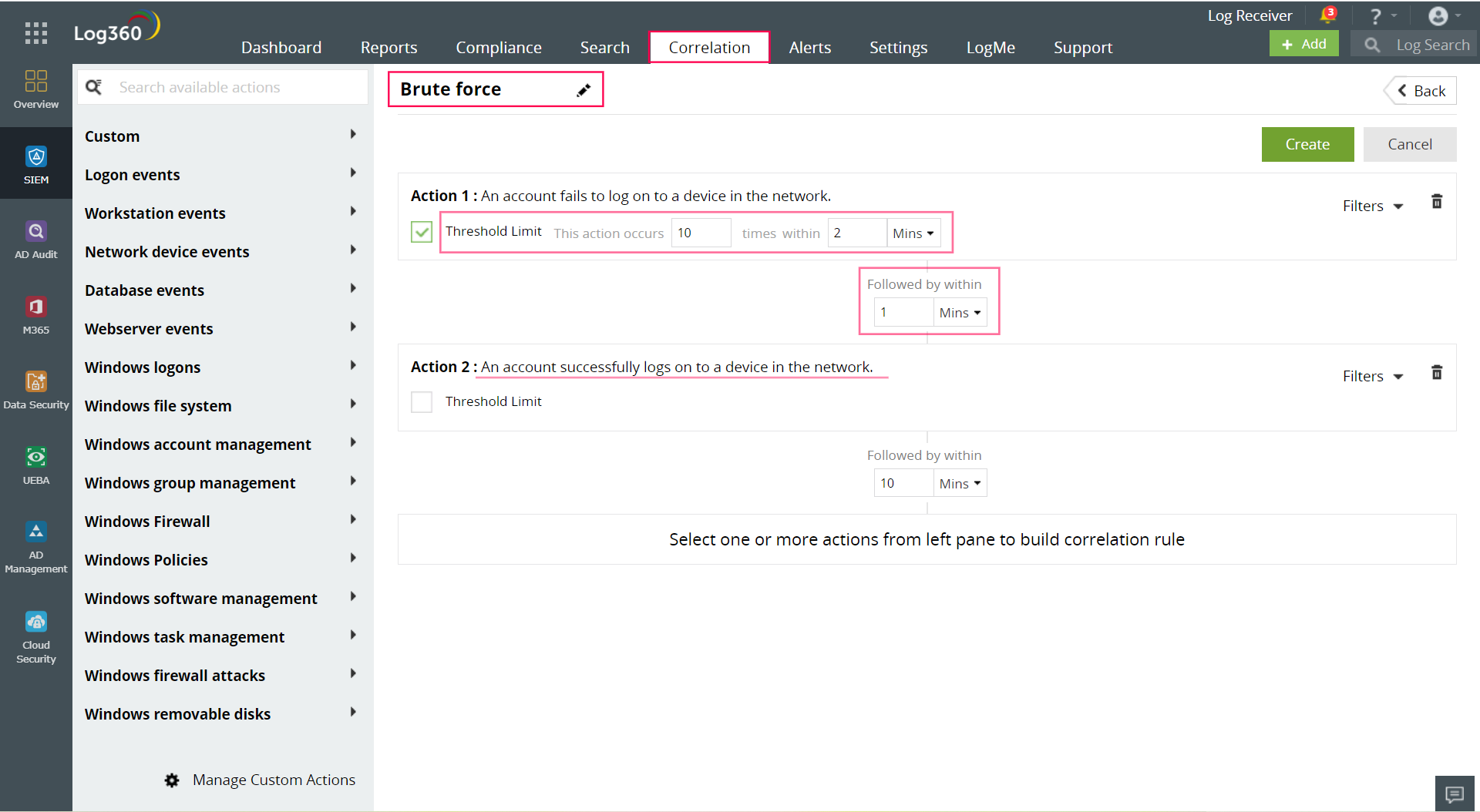
A correlation rule specifies the expected sequence of network events corresponding to a brute-force attack and raises an alert in real time. In the below image, we have set the rule assuming that a brute-force attack pattern to consist of several unsuccessful logon attempts (Action 1) followed by a successful logon (Action 2). The action's duration and frequency are specified by the threshold limit.
A SIEM solution with a correlation engine offers a wide range of preset actions to select from along with custom actions.
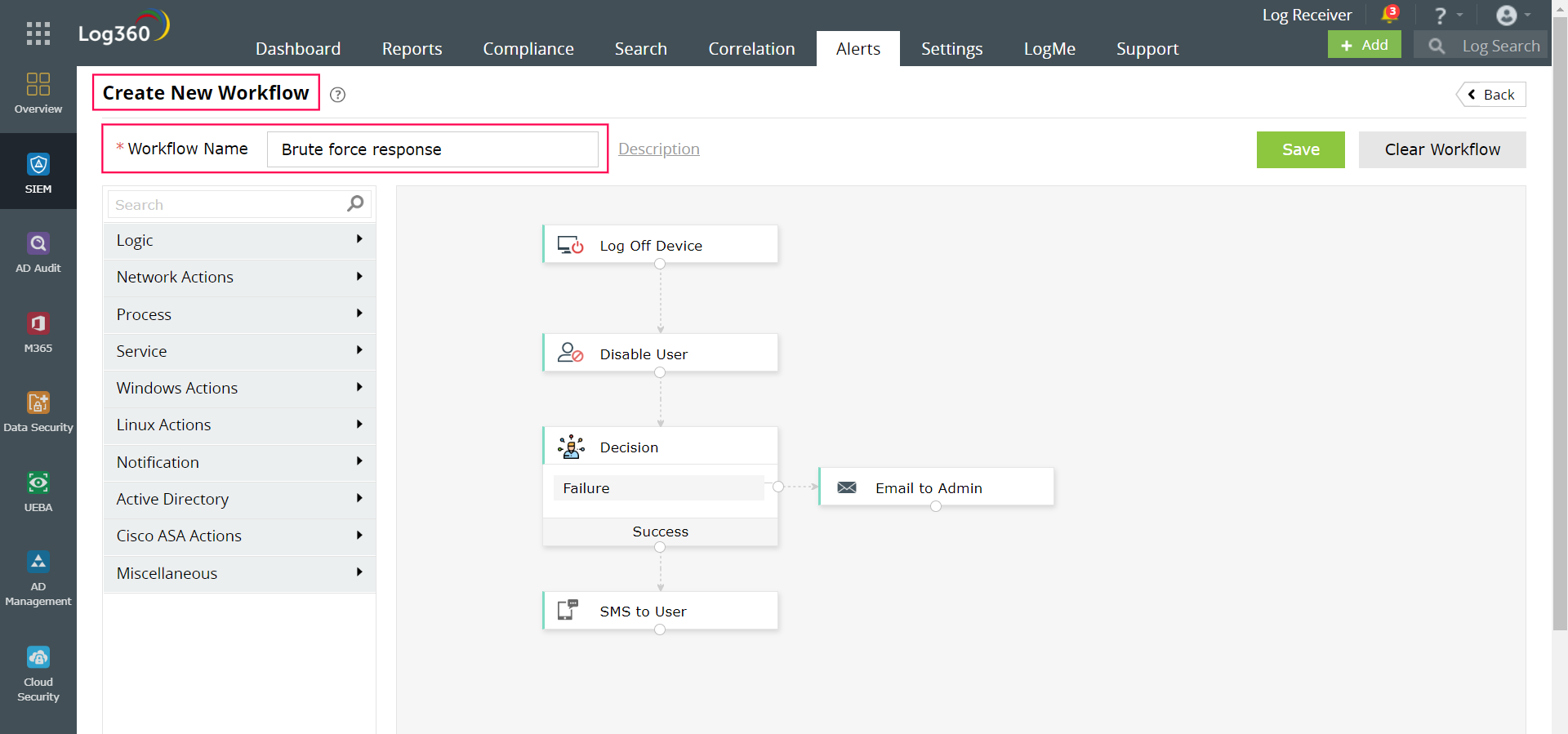
Building workflows initiates a quick response to the brute-force correlation alert. Here, the first step is to log off the device and disable the user next. In case of a failure to disable the user, the admin is notified. If the user is successfully disabled, an SMS is sent out to notify the user.
You can easily create a response action using a drag-and-drop workflow builder like the one seen in the image below.
With incident rules, you can automatically create incidents as soon as an alert is triggered. Now you can more effectively manage alerts by allocating severity to incidents, monitoring their elapsed age and status, and assigning the appropriate person for investigating and closing. It enables you to easily track and handle otherwise clumsy alerts and their resolution better.
In addition to managing incidents within your SIEM, integrating your SIEM with third-party ticketing or help desk applications can automatically create external tickets when alerts are triggered. The alert details are forwarded to the ticketing tool so that the designated technician in your organization can investigate further as needed.
In order to easily understand the process of automated incident response, we looked at a simple use case of a brute-force attack. However, you can use custom correlation rules and workflows to detect and respond to all kinds of attacks, including complex ones.
With automated incident response capabilities, SOCs can automatically correlate suspicious events, prioritize alerts based on severity, trigger the first line of defense with automated response workflows, and manage incidents centrally.
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.