Insider threat definition
The definition of an insider threat in cybersecurity is any risk posed by individuals who have legitimate access to critical organizational data, such as employees, contractors, or business partners. This can involve theft of sensitive information, sabotage of systems, or unintentional exposure of vulnerabilities. Insider threats can manifest as intentional insider threats, where the insider acts maliciously, or unintentional actions, such as negligence or accidental mishandling of data.
Types of insider threats
Not all insider threats are caused by users with a malicious intent. Sometimes, a lack of awareness and negligence of insiders can result in compromised security. Depending on the user's intention, insider threats can be classified into the following types:
1. Malicious insider threats
These threats are caused by insiders who seek to harm their organization or exploit confidential data for their personal gain. Their insider knowledge often makes it easier to carry out damaging attacks without raising suspicion. For example:
- An employee is stealing trade secrets.
- A disgruntled worker planting malware to disrupt operations.
2. Unintentional insider threats
These threats are accidental and often caused due to inadequate training and lack of security protocol awareness. They can include actions like mishandling sensitive data and falling for phishing emails. For example:
- Sending sensitive files to the wrong recipient.
- Using weak passwords that are easily hacked.
3. Negligent insider threats
Negligent insiders may not have a malicious intent, but their careless actions cause significant harm. This could involve failing to follow security policies, misconfigured systems, or using weak passwords. Careless users can be of two kinds:
i. Pawns: These are the users who are tricked into malicious acts through social engineering practices. For example, a user who has been manipulated by an imposter to disclose sensitive data.
ii. Goofs: These are users who don't adhere to security procedures. For example, a user who stores sensitive client data on their personal device, knowing that it is against security principles.
4. Compromised insiders
These threats occur when an external attacker gains access to an insider's credentials, effectively impersonating them.
A typical insider attack flow
The steps in an insider attack can be outlined as follows:
- Defining the goal of the attack and identifying target systems that align with the motives.
- Leveraging the legitimate access to breach the system.
- Escalating privileges and using the knowledge about the organization's infrastructure to exploit vulnerabilities that grant higher access.
- Identifying and collecting the targeted data.
- Obscuring traces by deleting logs and altering timestamps to avoid detection.
- Exfiltrating the stolen data from the organizaton's network and exiting the system.
Risks caused by insider threats in cybersecurity
Why are insider threats so dangerous?
According to Security Intelligences’ recent 2024 Insider Threat Report, 83% of organizations reported at least one insider attack in the last year. Here's why they are dangerous:
- They exploit trust: Insiders already have privileged access to sensitive data and systems, allowing them to bypass traditional security measures designed to stop unauthorized users.
- They have deep security knowledge: Employees or contractors familiar with an organization’s security architecture understand how to evade detection, disable monitoring systems, or manipulate logs to cover their tracks.
- They evolve tactics rapidly: Since insider threats are not constrained by the same barriers as external attackers, their attack methods change and adapt much faster, making it challenging for security teams to keep up.
- They are harder to detect: With legitimate credentials, insiders can carry out malicious actions such as unauthorized data exfiltration or privilege escalation without triggering immediate red flags. Their actions often mimic normal business operations, making it difficult to differentiate between routine and malicious activities.
Common risks posed by insider threats:
- Data breaches: Exposure of confidential information to unauthorized parties.
- Operational disruption: Downtime or sabotage of critical systems.
- Financial loss: Costs related to recovery, legal fines, and lost revenue.
- Reputation damage: Loss of customer trust and market standing.
Detecting insider threats
Detecting insider threats can be an exhaustive job as it demands a constant vigilance for any anomalous user behavior.
Some of the indicators and behaviors to detect insider threats are:
- Unusual access patterns, such as employees trying to log in to systems or files outside of their assigned duties or working hours.
- User behavior that suddenly changes, such as accessing an abnormally large amount of data or copying private material to portable storage devices. Any unauthorized use or efforts to escalate privileges should set off alarms.
- Major changes in an employee's behavior at work, attitude, or unexpected financial difficulty may point to possible insider threat motivations.
- Indicators of unauthorized activity can also include a spike in failed login attempts, odd login locations, or recurrent access to prohibited regions.
Mitigating insider threats
A multi-layered defense plan is necessary to deal with insider threats. Security tools with features like user and entity behavior analytics (UEBA) and threat intelligence can be crucial aspects of this strategy. By creating baselines of typical user and entity behavior, ML-based UEBA can detect deviations that can be indicative of malicious behavior. This, combined with real-time network monitoring, allows for the prompt detection of abnormal activity, giving security personnel the chance to take action before any serious harm is caused.
A SIEM solution that can integrate UEBA with threat intelligence and incident response will help your organization deal with insider threats.
Furthermore, the danger of unauthorized access can be decreased by adopting stringent access restrictions, the least privilege principle, and continuous surveillance of privileged accounts.
Beyond security monitoring, IAM plays a crucial role in mitigating insider threats by enforcing strict authentication and authorization policies. Implementing a Zero Trust model eliminates implicit trust within the network, requiring continuous verification for every access request. Additionally, enforcing MFA adds an extra layer of protection, making it significantly harder for attackers, whether internal or external—to misuse credentials.
Detect and mitigate insider threats using ManageEngine Log360
ManageEngine Log360 is a unified SIEM solution for detecting, prioritizing, analyzing, and mitigating security threats for enterprises across all industries.
Learn how you can utilize powerful features of Log360, including UEBA, correlation rules, and incident workflow, and customize them to detect and remediate insider threats.
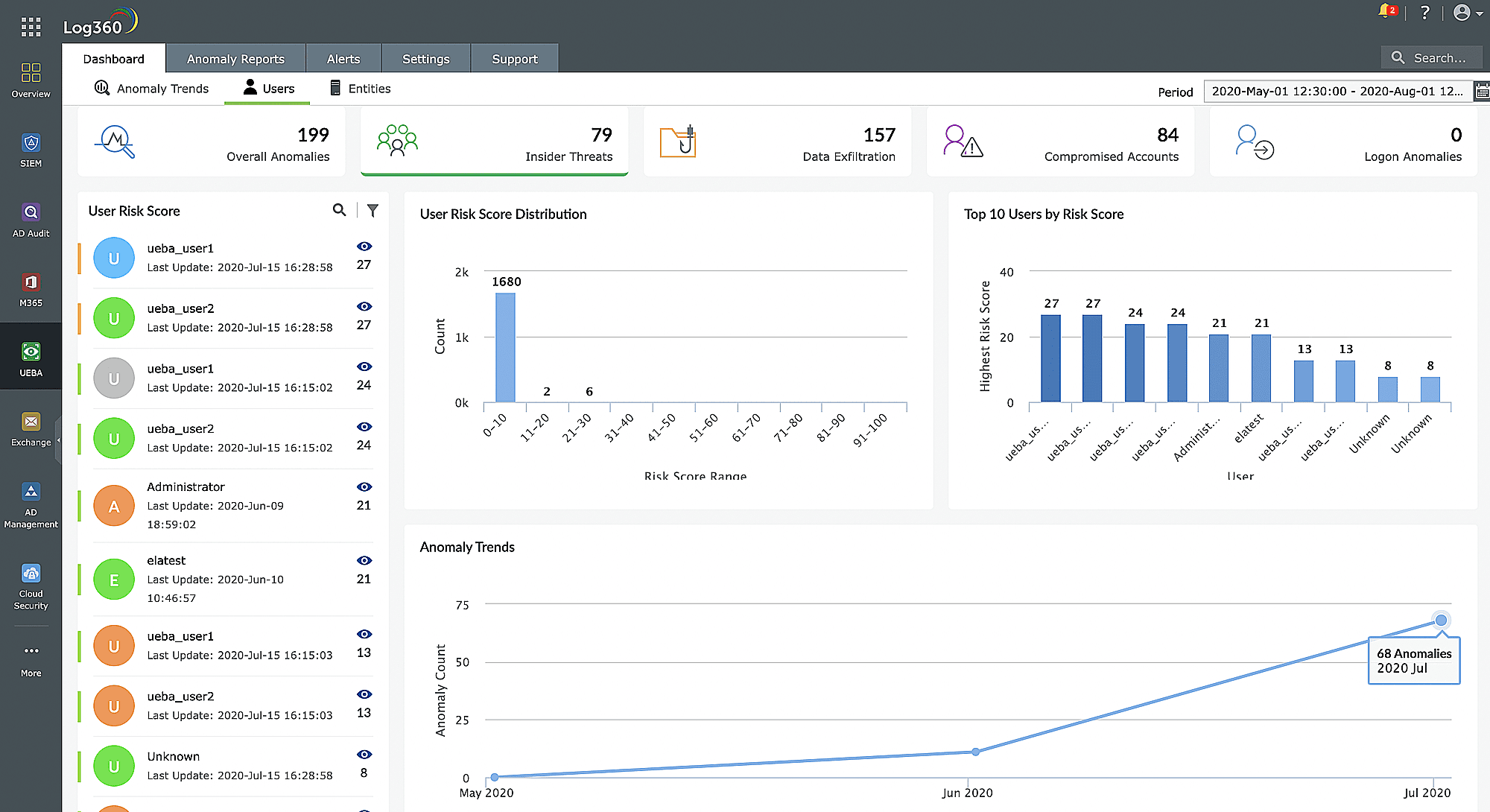
Detection insider threats through UEBA
With the help of advanced analytics, Log360's UEBA develops a baseline of typical behavior patterns in order to spot anomalies like erratic login times. Contextual analysis reduces false positives by considering elements like resource types and user roles. Prioritization is achieved via risk scoring, and by correlating diverse data sources, you can get a full picture of your network security. Generate alerts and reports for suspicious activities, aiding the swift investigation of potential insider threats. Continuous ML refines the system's understanding of evolving threats in your network.
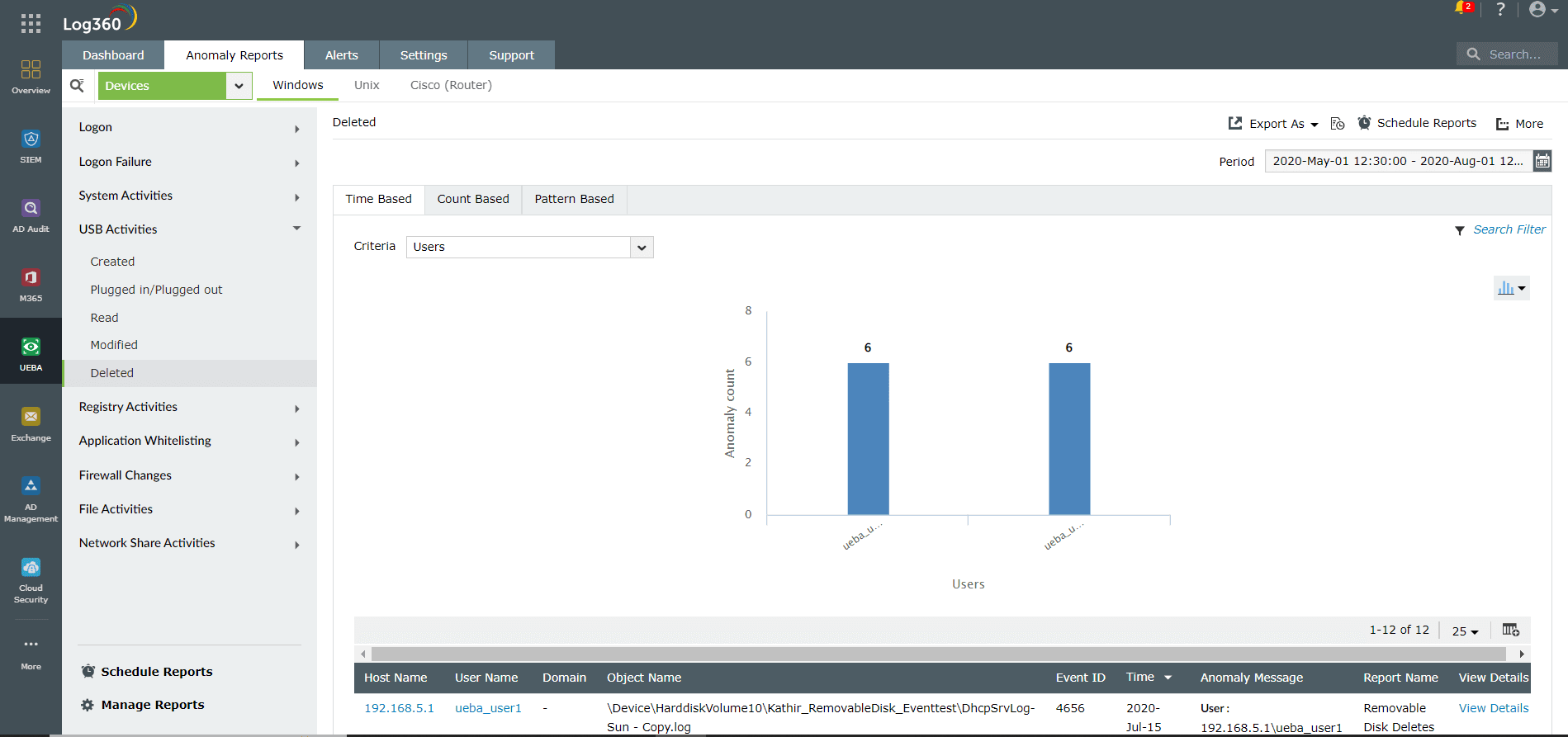
Detecting insider threats through correlation
Insiders can carry out attacks in multiple steps that are not obviously related to each other using multiple devices. Log360's powerful correlation engine can track activities across various devices and connect these not-so-related events seamlessly into a coherent pattern, which can indicate an insider attack.
Event ID 4624 indicates a successful logon attempt from a local computer.
Event ID 4663 monitors the access attempts to critical file system objects, which have their own system access control list.
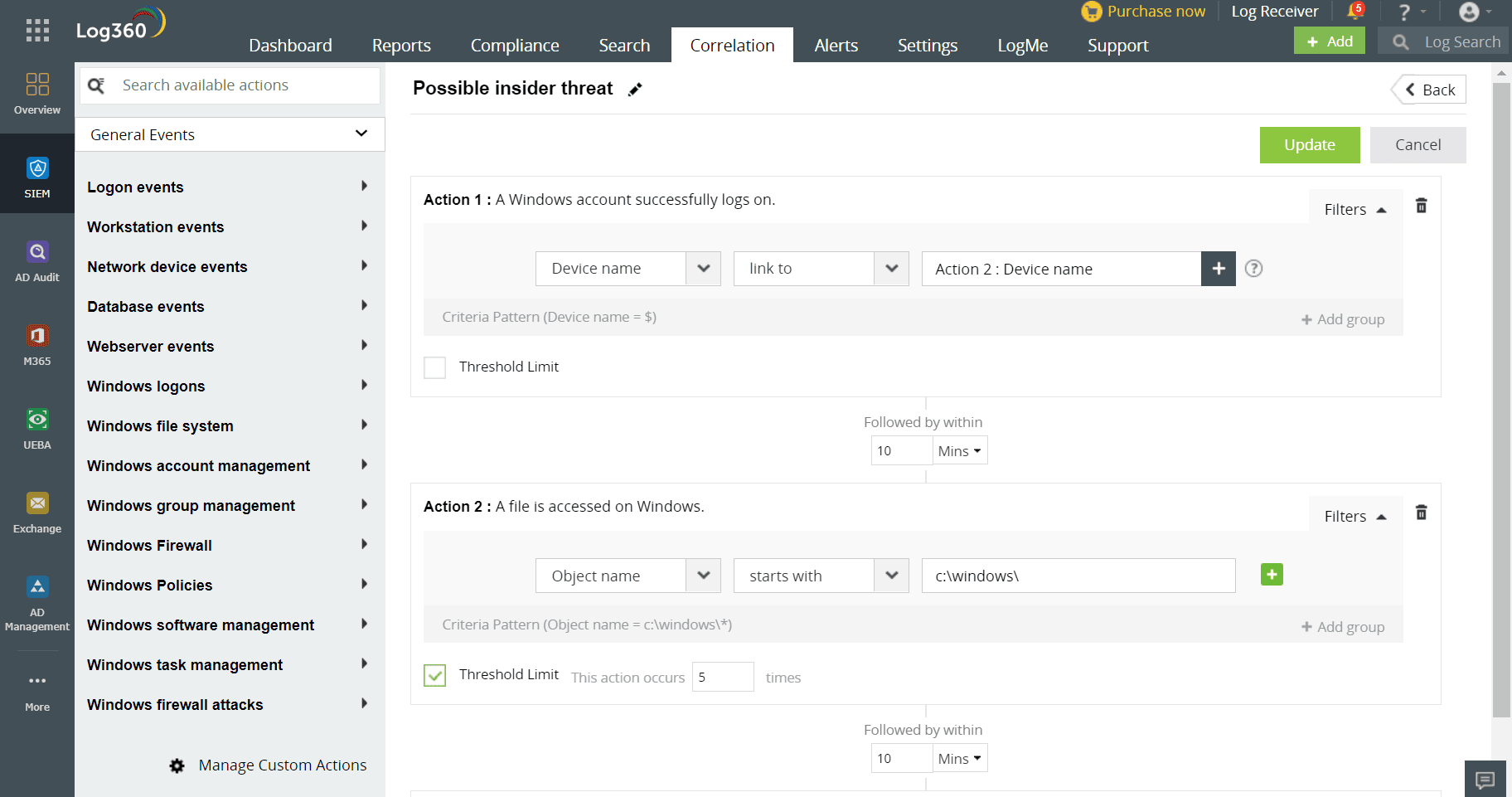
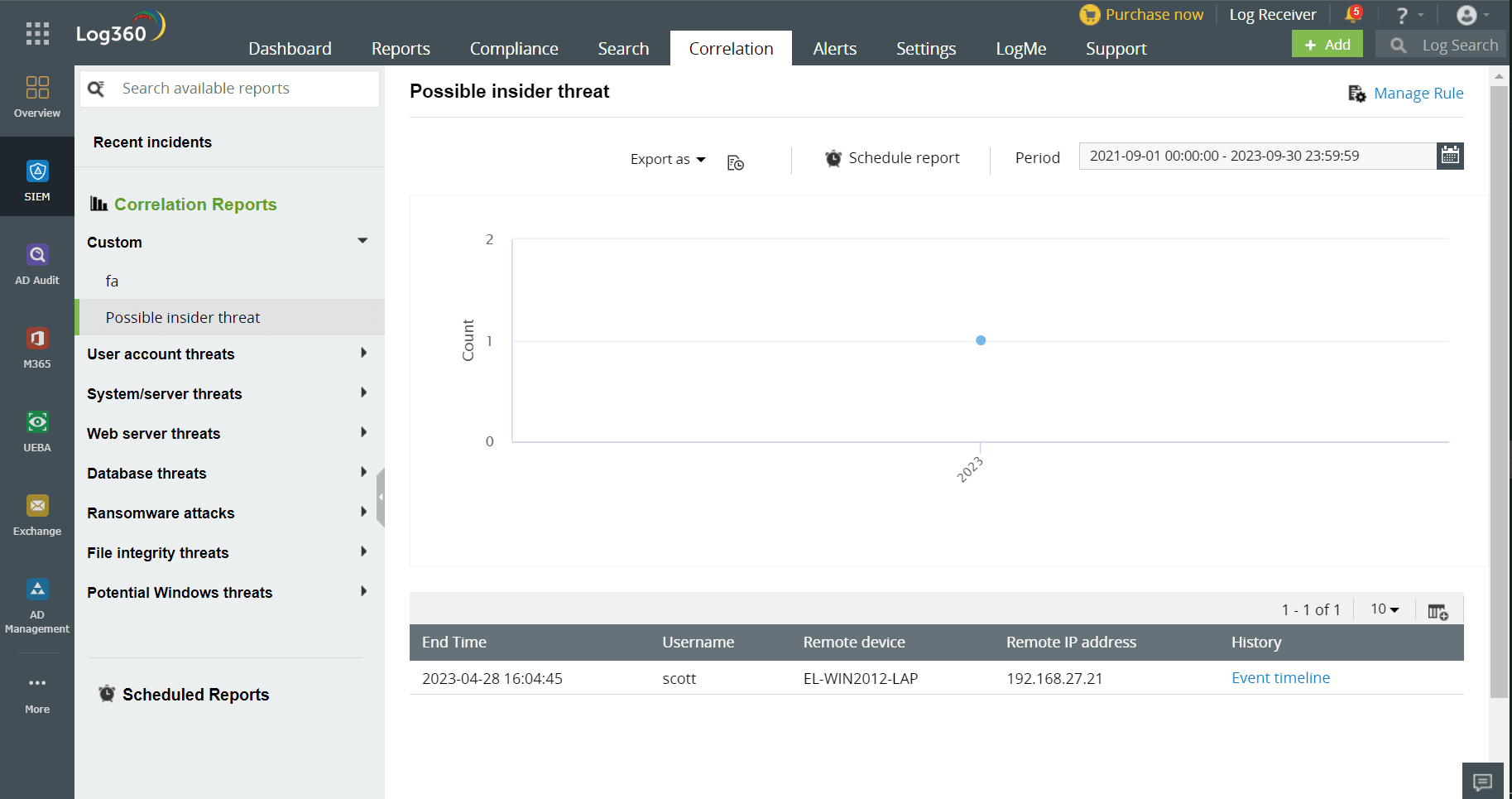
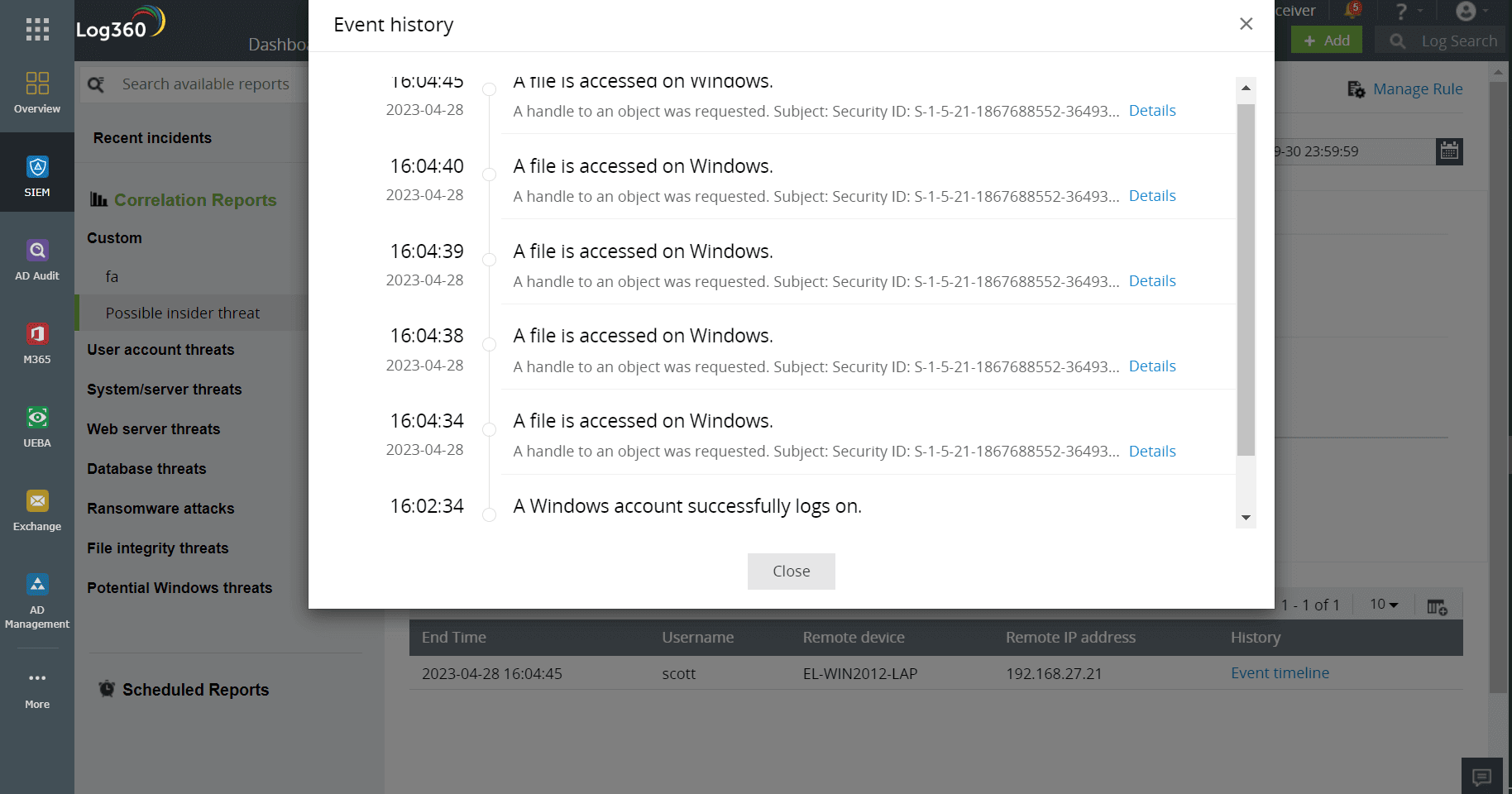
Real-time alerts
Log360 can quickly identify anomalies that might indicate an insider's malicious intent by continuously monitoring user and entity behavior and setting correlation rules. Real-time alerts are triggered based on predefined rules, such as unusual data access, unauthorized system changes, or abnormal login patterns. Once an alert is raised, predefined workflows can be implemented, and security teams can promptly investigate and take appropriate actions to mitigate risks before they escalate into security events.
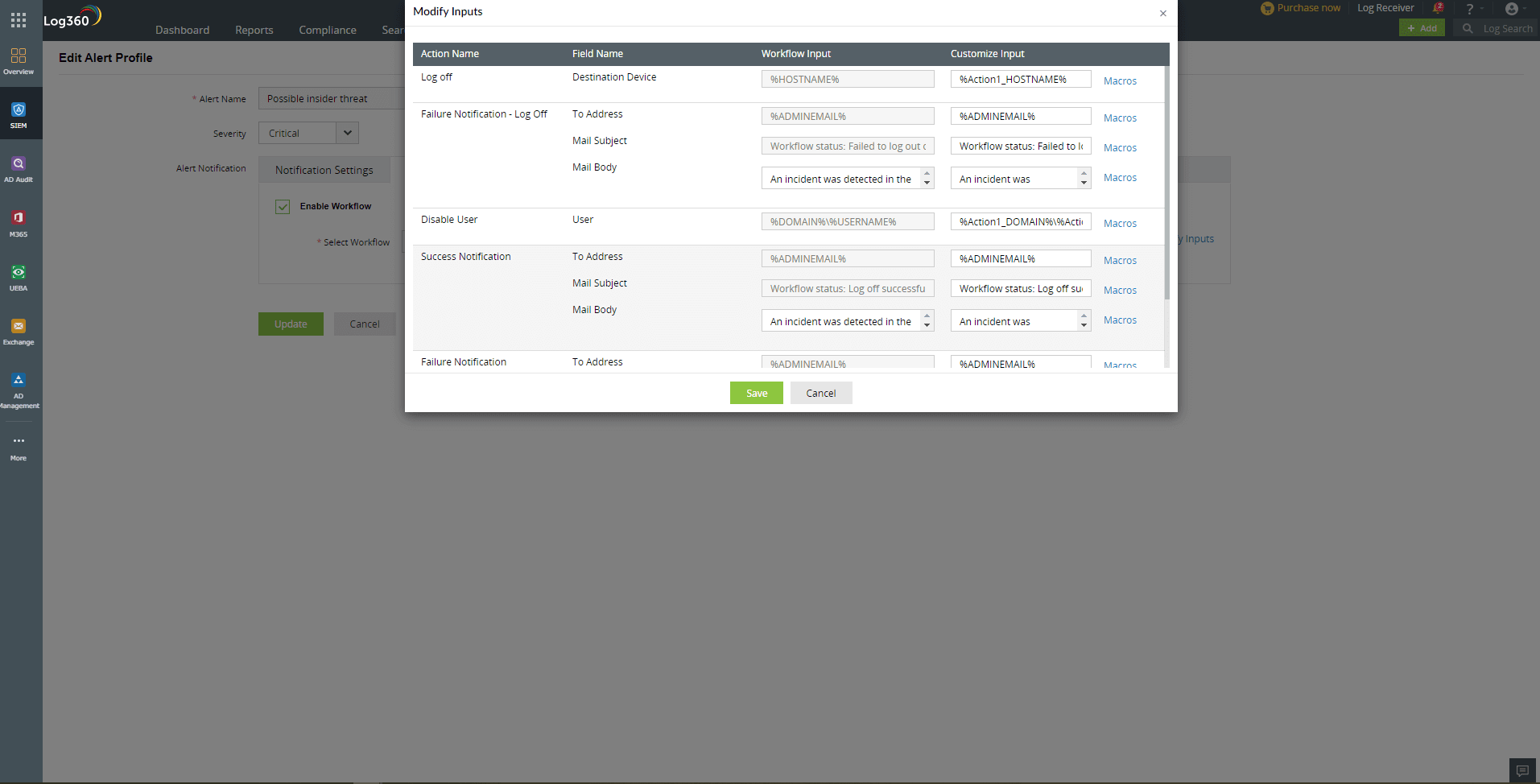
Insider threat mitigation - Sample playbooks
- Containment: Disable user or device; suspend the suspected user account and system temporarily.
- Network safeguarding: Block the suspected system's inbound and outbound traffic to mitigate data transfer attempts.
- Notification and alerting: Notify the suspected user that their activities are being monitored and alert the security team to take immediate action.
- System analysis: Review the running processes on the suspected system and run cleanup scripts if any unauthorized malware is detected. Restart the system to ensure that the malicious process is terminated.
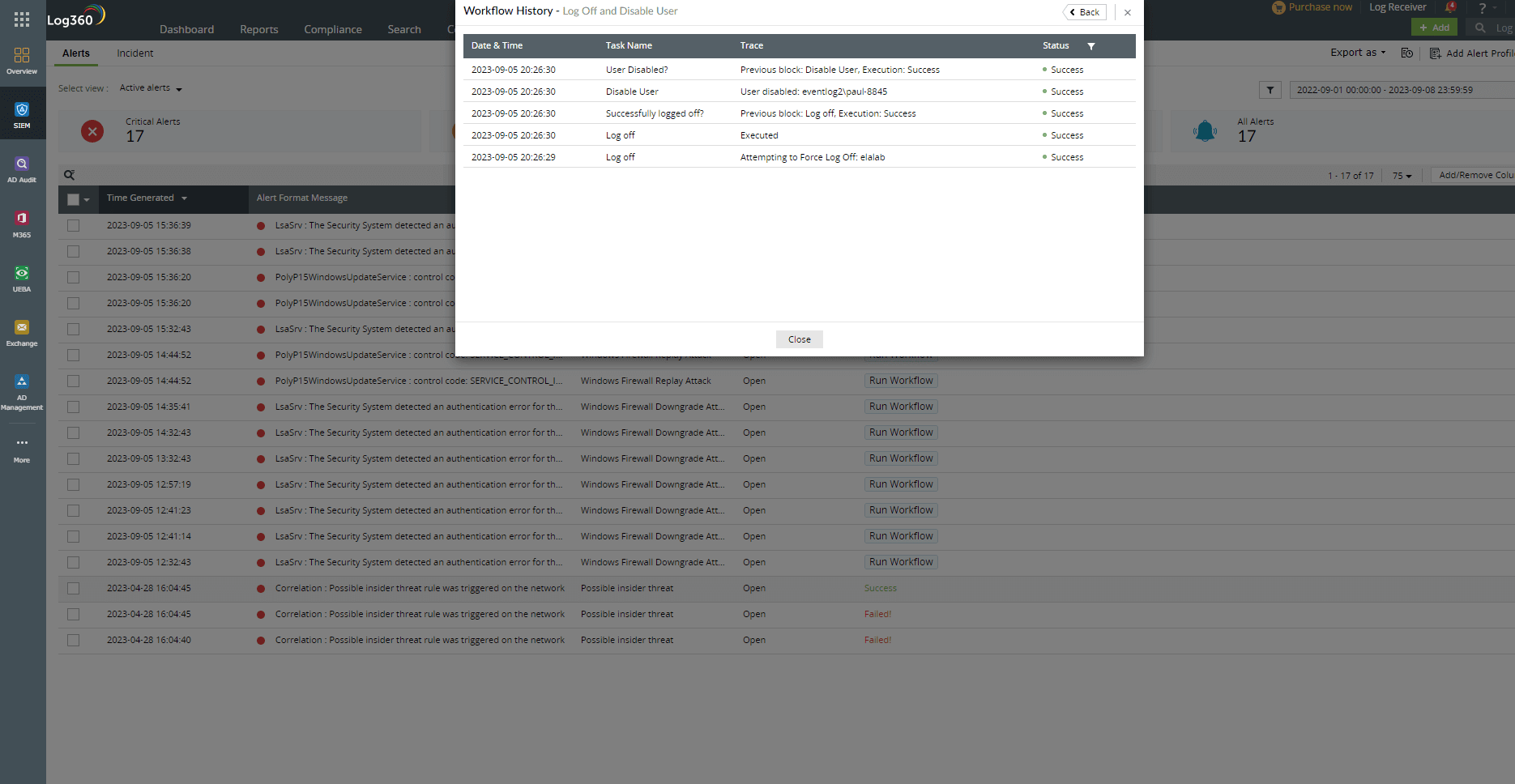
Investigation through reports
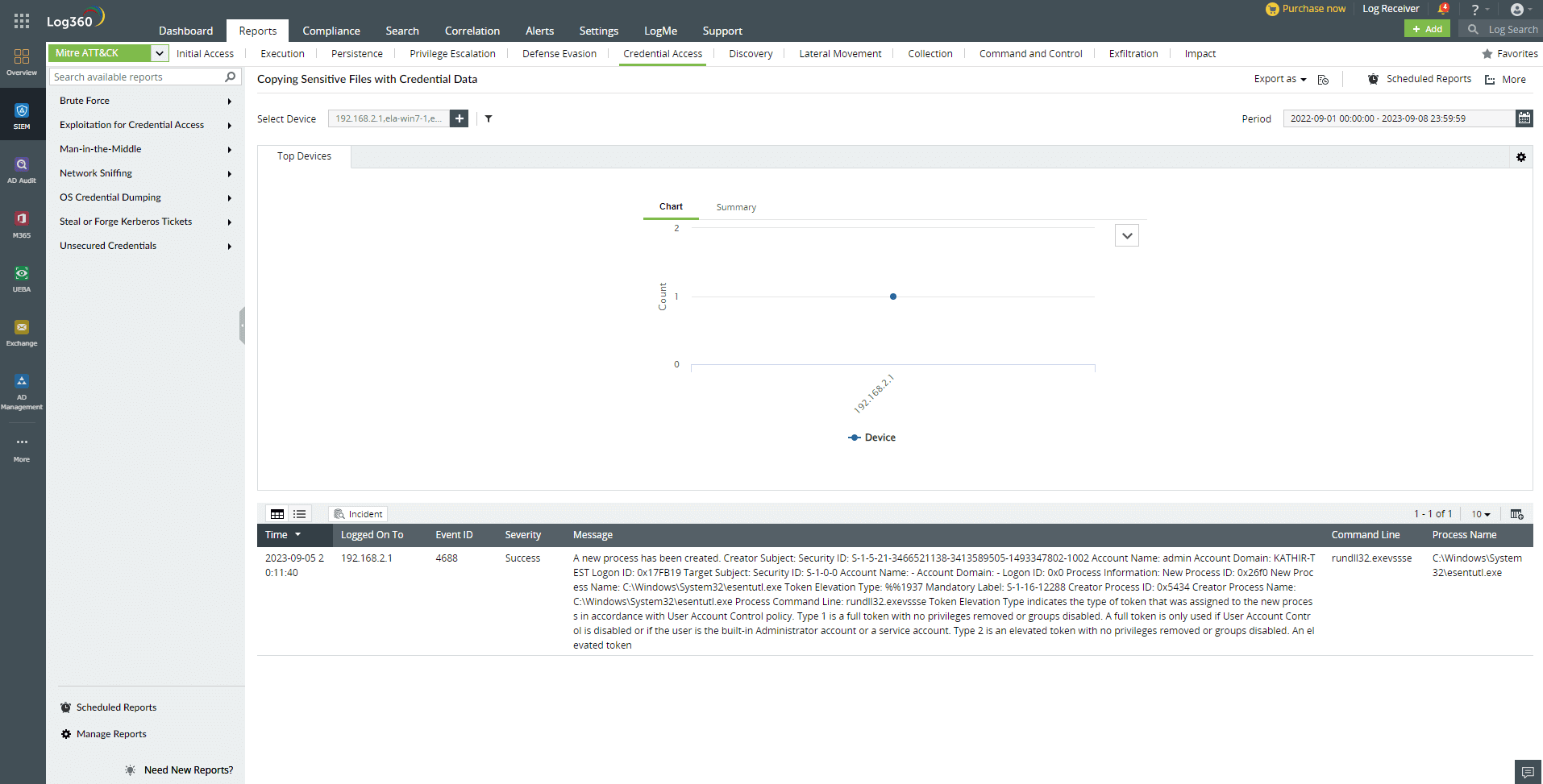
Log360 offers a thorough overview of user behavior by collecting and visualizing data from numerous sources over time. This helps security teams find trends, anomalies, and correlations that can point to risky behavior. Analysts can delve into certain events and circumstances with the help of filtering capabilities for a thorough investigation. Analytical widgets and dashboards of Log360 concerning user audit trails and activity trends make it easier to spot odd access patterns, data transfers, or system interactions, assisting organizations in efficiently identifying insider threats in advance.
Ready to secure your network from privilege escalation attacks? Leverage Log360’s advanced security features to implement robust defensive strategies and incident response measures.
- Insider threat definition
- Types of insider threats
- A typical insider attack flow
- Risks caused by insider threats in cybersecurity
- Detecting insider threats
- Mitigating insider threats
- Detect and mitigate insider threats using ManageEngine Log360
- Insider threat mitigation - Sample playbooks