You might already be aware of the role of a security information and event management (SIEM) solution in monitoring firewalls and making sure they filter out non-legitimate traffic. Or you might be a beginner still finding your way through SIEM and wandering amidst a maze of firewalls. Either way, you've come to the right place. With this blog, you'll be shown how to optimize and manage your firewall rules using the central console of a SIEM solution.
A firewall is essentially a network security device that acts as the first line of defense in protecting your organization from any unauthorized access. Simply put, it protects your organization's internal network from insecure external sources, by acting as a barrier between the two. It's considered the first line of defense because, without a firewall, unauthorized individuals outside your network could make connections with your network. If this were to occur, an attacker could enter your network easily and compromise other devices to escalate privileges or exfiltrate sensitive data.
However, with a firewall in place, any connection request made from outside your network will be monitored and filtered based on the rules you set. Therefore, unsolicited requests will be blocked and only the genuine requests will be passed through, helping you prevent phishing attempts and other more sinister attacks. Once you configure your firewall policy to block requests from any suspicious or malicious source, you'll be able to safeguard your data and privacy, as well as prevent attackers from infecting your network devices with malware and spyware.
A firewall could be hardware-based or software-based. The former is a physical device that allows for centralized network management; the latter is an application that comes packaged with your device's OS and monitors traffic between your applications and the internet. A router with a built-in firewall is an example of a hardware-based firewall, whereas Windows Defender Firewall is an example of a software-based firewall. Both have their perks and pitfalls, so it's always better to have both to secure your network and its devices.
Now that you've familiarized yourself with the basics of firewalls and their importance in securing your organization from cyberattacks, let's take a look at how you can manage your firewall using a SIEM solution. Usually, when an IT security admin wants to change the firewall policy rules, they'll either write a script to enforce the policy change they require, or go to the firewall settings to make changes to the firewall policy. However, with an effective SIEM solution, you can optimize the inbound and outbound rules of your firewall to block malicious threats effectively.
Log360—a unified SIEM with integrated DLP and CASB capabilities—comes packaged with security orchestration, automation, and response (SOAR) capabilities, allowing you to configure automated incident response. This means that you can configure a workflow for an alert which automatically triggers whenever the alert criteria is met. An adequate response will be meted out to deal with the event, depending on the workflow you've set up. In this way, workflows can be used to prevent attacks or stop an ongoing attack in its track. Responses can include actions such as disabling a user, shutting down a device or its network, stopping a process, or managing firewall rules.
A firewall is only effective if its policy has been properly configured, and that's where a SIEM solution comes in. Modern SIEM solutions come packed with SOAR capabilities that can help you create new firewall rules from a central console based on automated response workflows. These workflows can be activated whenever an event occurs that warrants a change in the firewall rules.
While the overall configuration of a SIEM solution is going to differ from vendor to vendor, any good SIEM solution would allow analysts to create their own workflow. For firewalls, the workflow would be based on the "Inbound" and "Outbound" rules. A SIEM solution will give you the option of choosing the interface as global or otherwise, and whether you want the rules to be applied to a particular destination device or to all the devices in the network. This way, your SIEM solution will automatically carry out the desired action as per your configuration. So, if the threat intelligence from your SIEM solution alerts you about a connection request from a malicious source, instead of making the change from your firewall settings to block that IP address, you can have it blocked automatically if you have suitably configured the workflow associated with that alert.
A unified SIEM solution like Log360 can help you create new firewall rules with its drag-and-drop option for building workflows.
Figure 1 will give you an idea of how your inbound rules can be optimized to thwart threats using Log360.
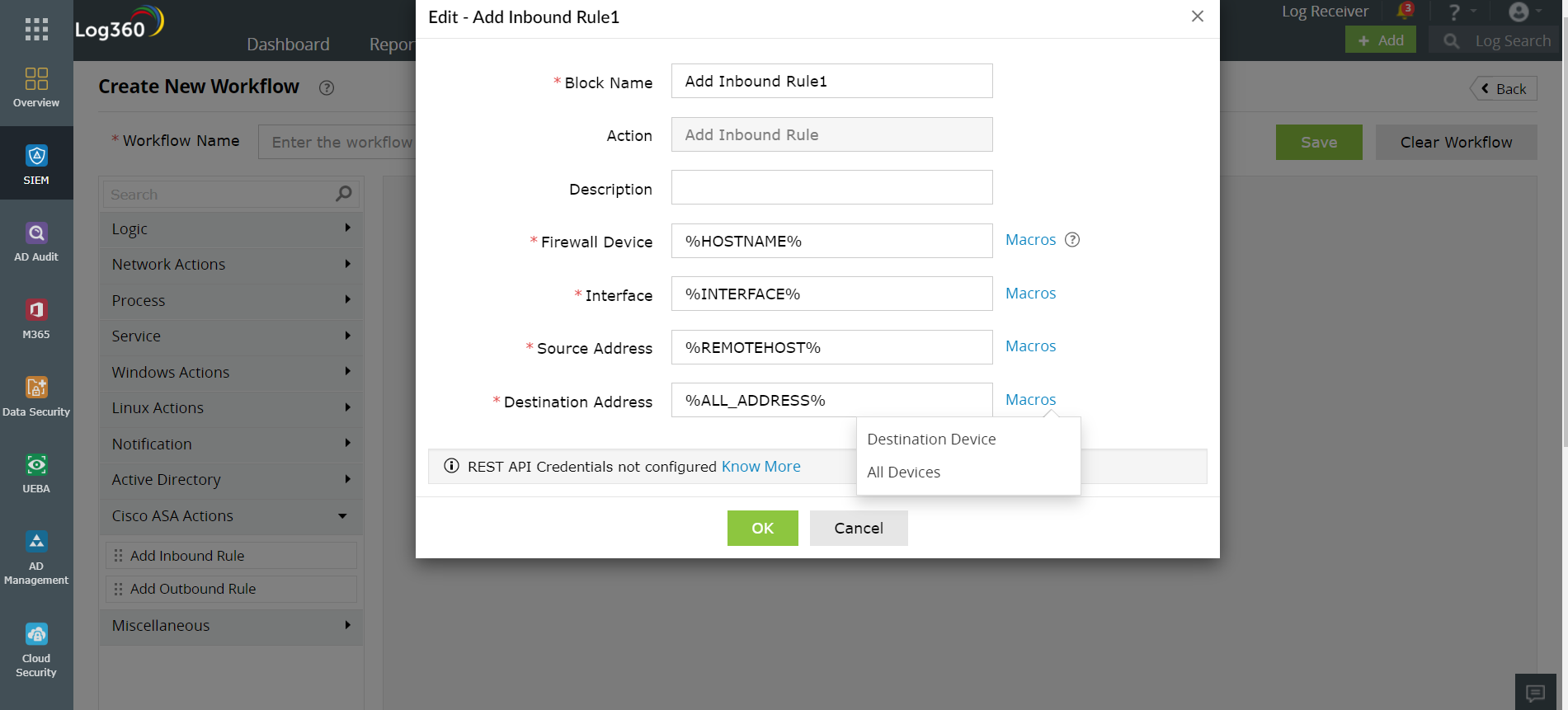
Figure 1: Optimizing inbound rules using Log360
Similarly, you can use Log360's drag-and-drop option to optimize the outbound rules as shown in the figure below.
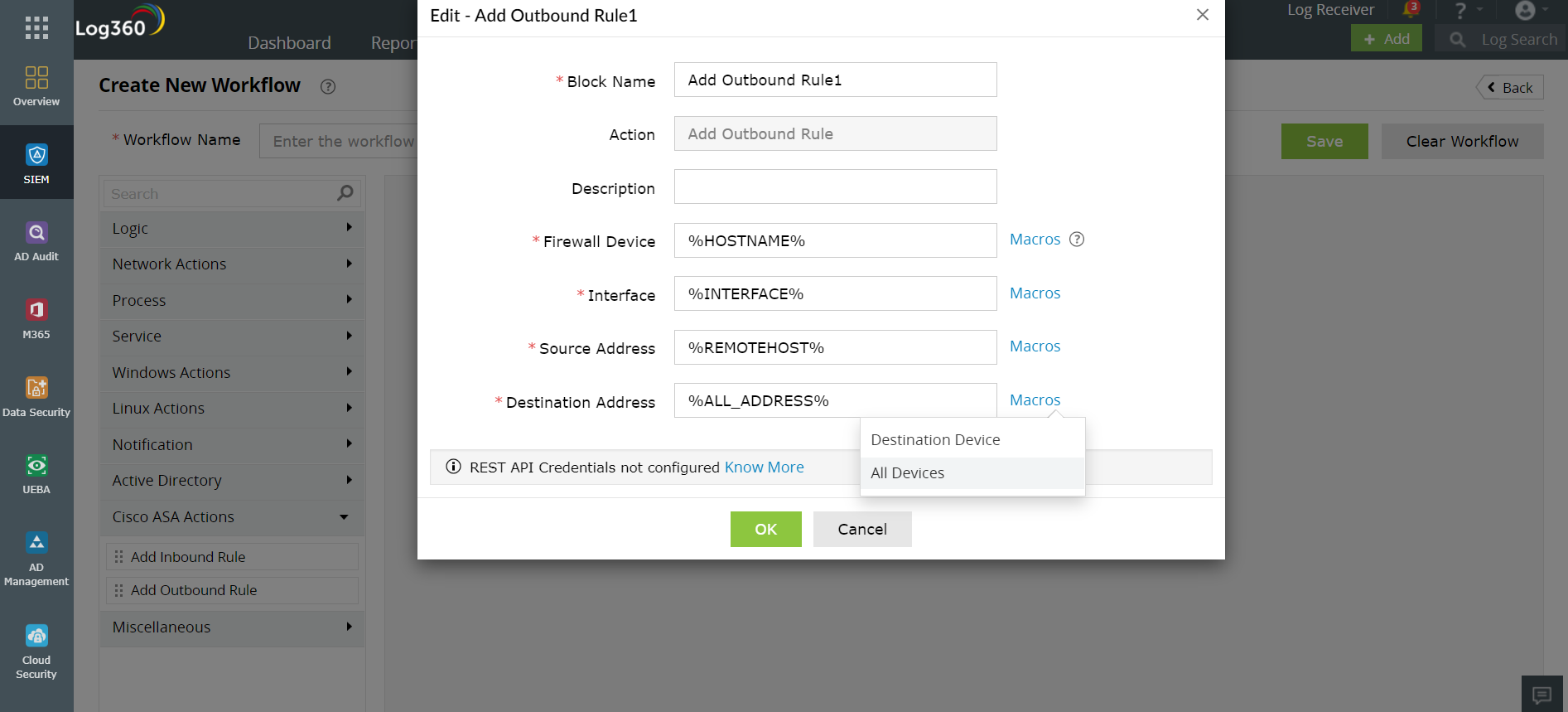
Figure 2: Configuring outbound rules using Log360
See how simple it is to optimize your firewall policies with Log360? Just as you see here for a Cisco router firewall, you'll soon be able to manage the firewall rules of other routers such as Barracuda, Fortinet, Sophos, and Palo Alto.
ManageEngine Log360 can also help you audit your firewall logs and identify various attacks such as firewall flood attack, firewall spoof attack, firewall SYN attack, and more. To fully evaluate how Log360 can help your organization in its battle against cyberattacks, sign up for a personalized demo. Thanks for reading, folks!
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.