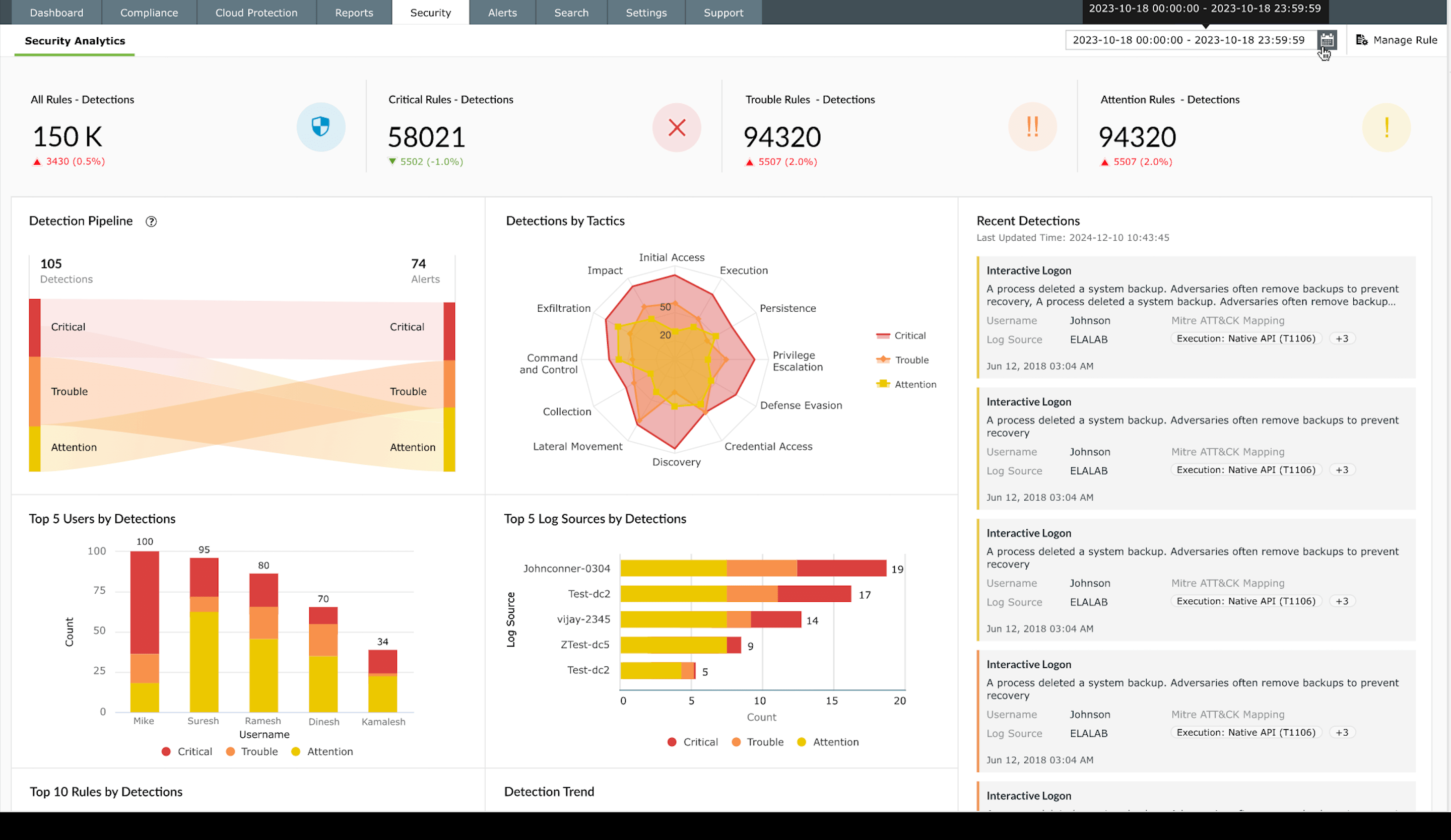
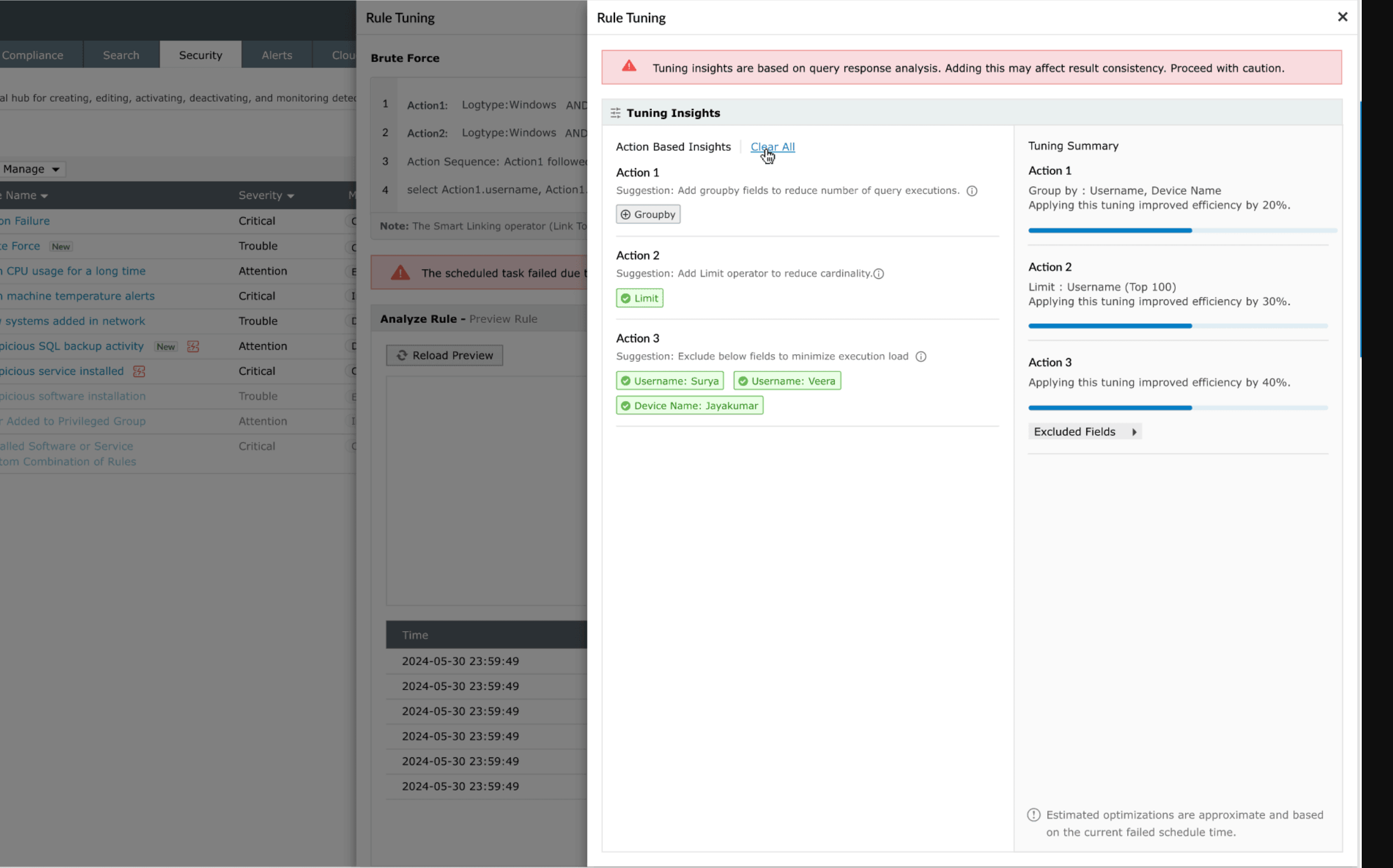
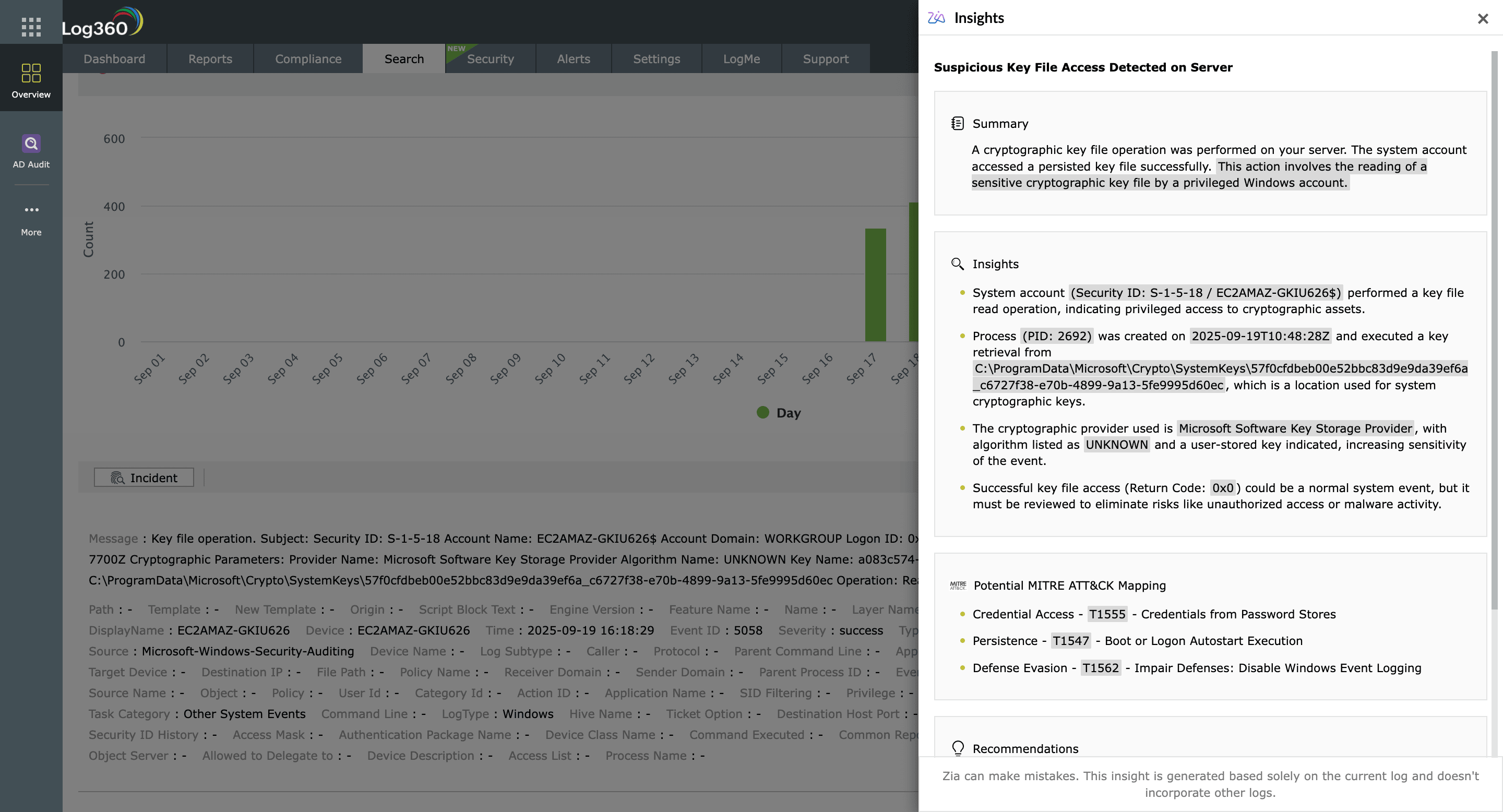
By establishing baselines for normal login patterns such as the time, location, and device, Log360 spots unusual access behavior like off-hours activity, impossible travel, or repeated failed logins. Peer group comparisons and risk scoring help teams separate legitimate travel from brute-force attempts. Log360 flags suspicious password changes across Windows, workstations, and Microsoft SQL Server, including resets on sensitive accounts like the Directory Services Restore Mode admin. It also highlights excessive login failures, account lockouts, and long gaps without a password reset in Microsoft 365.