According to IBM, organizations take an average of 184 days to detect a breach. The more time it takes to detect and resolve a security incident, the more expensive it is for the organization. To minimize the effects of a security incident, it is important for an organization to have an effective incident management process in place. ManageEngine Log360's incident management system can help your organization's security team respond to cyber security threats quickly and efficiently.


Log360's powerful incident manager allows enterprises to optimize their SOC metrics by providing a streamlined incident resolution process. With the help of the actionable incident dashboard, businesses can easily track key metrics such as mean time to detect (MTTD), mean time to respond (MTTR), and more. The dashboard also provides insights into active and unresolved incidents, recent and critical incidents, which can help you understand the workload of security analysts. With this information, enterprises can triage and prioritize incident resolution to ensure optimal functioning of their SOC.
Correlate log data collected from heterogeneous sources to detect attack patterns instantly using Log360's real-time event correlation engine.
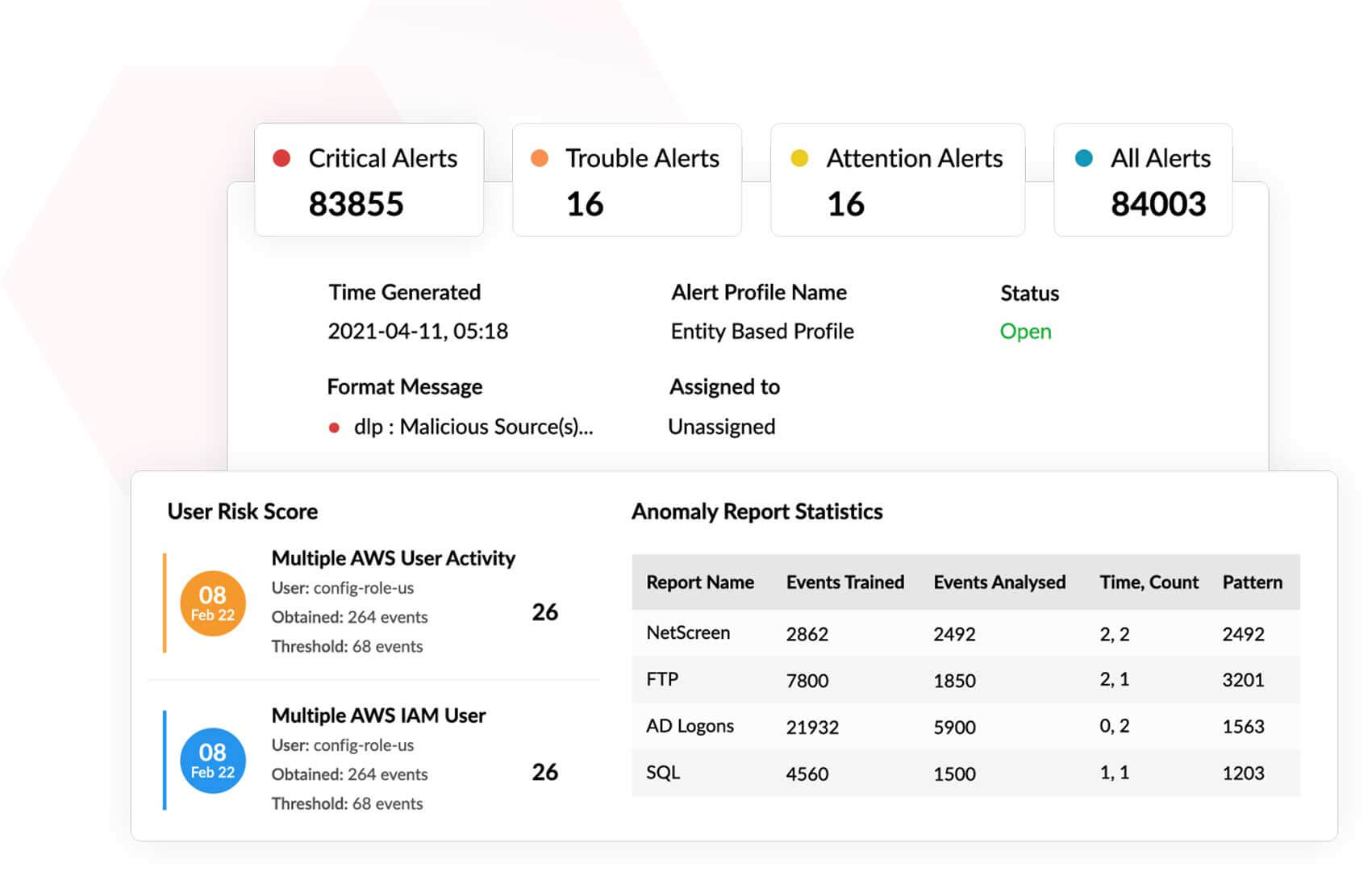
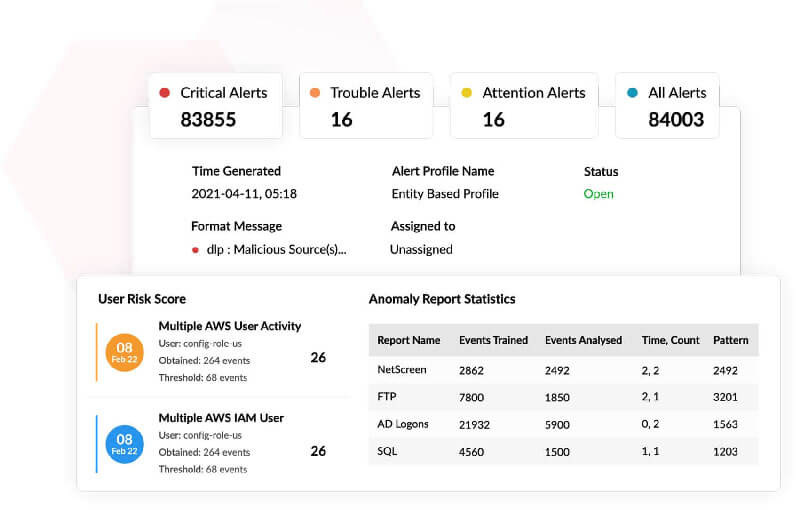
Powered by machine learning algorithms, Log360's UEBA module can detect anomalous activities in your organization's network. By creating a baseline of normal behavior, it analyzes logs coming from various sources for any deviation from expected behavior.
Detect malicious sources interacting with your network by correlating logs with threat data obtained from global threat feeds.
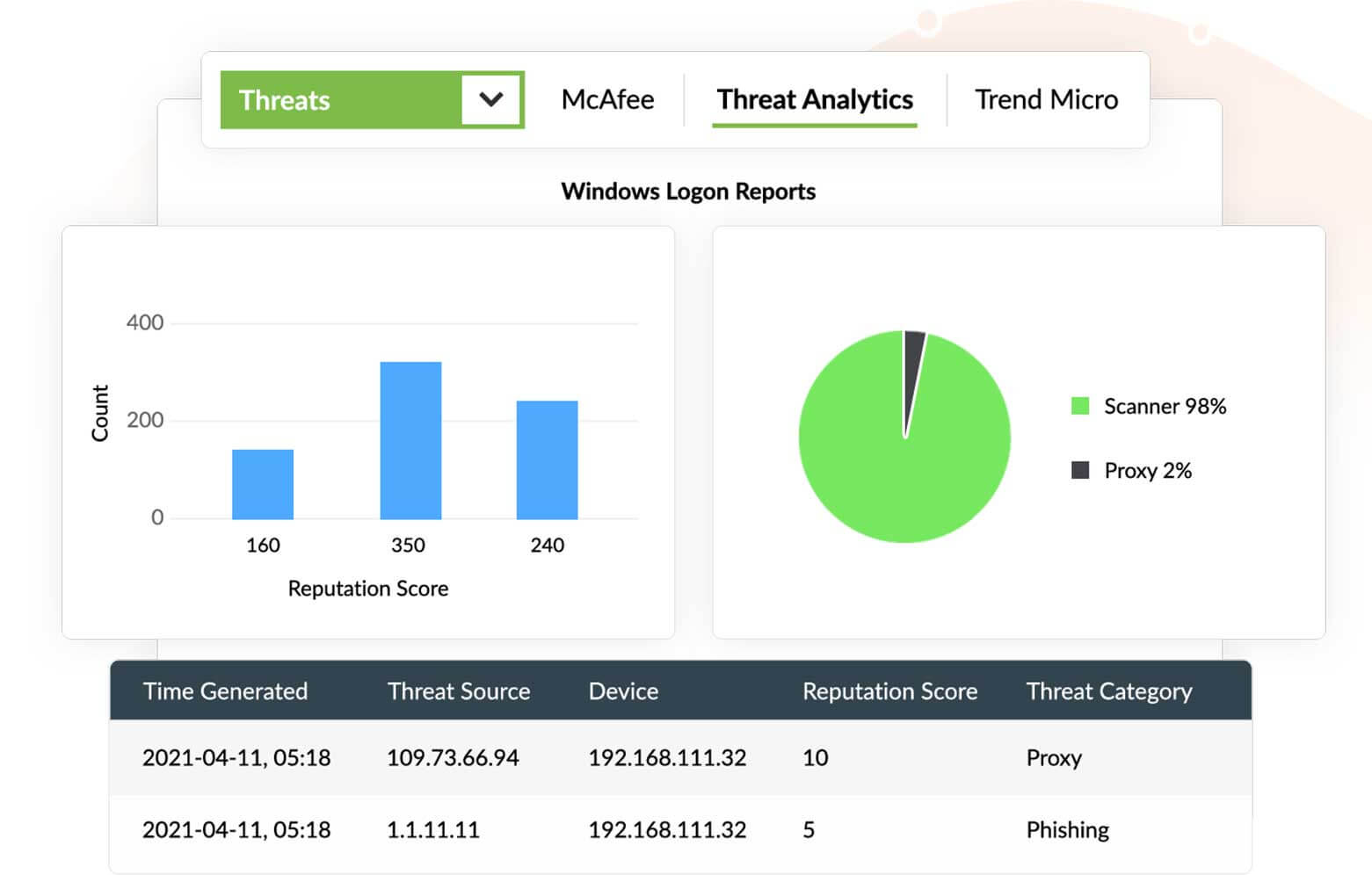
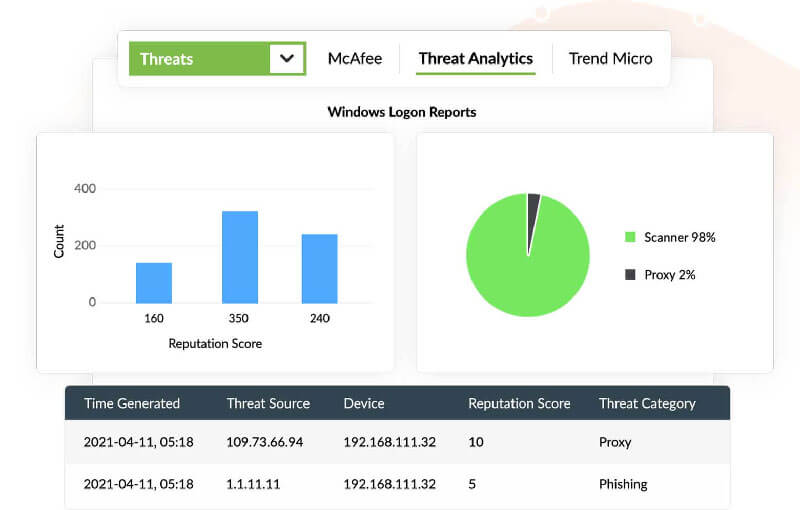
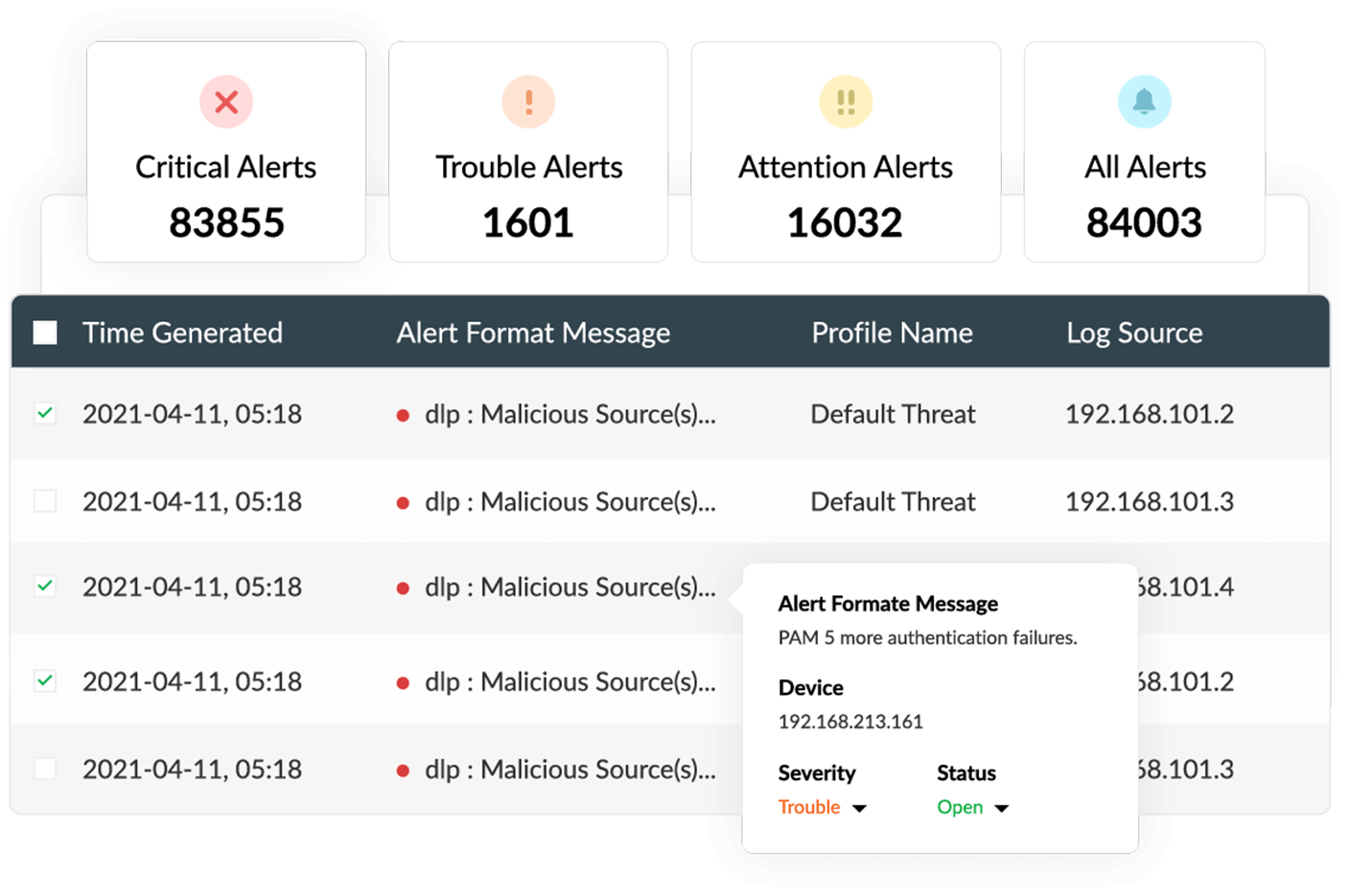
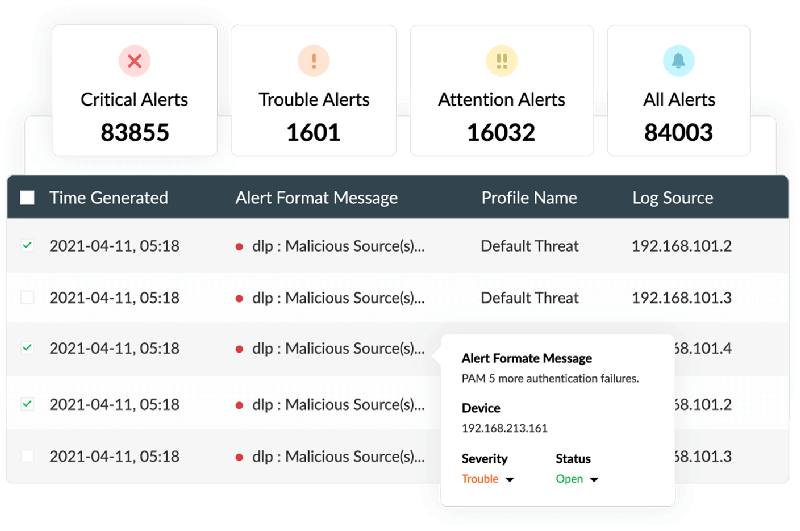
With Log360, get real-time alerts when a security threat is detected in your organization's network.
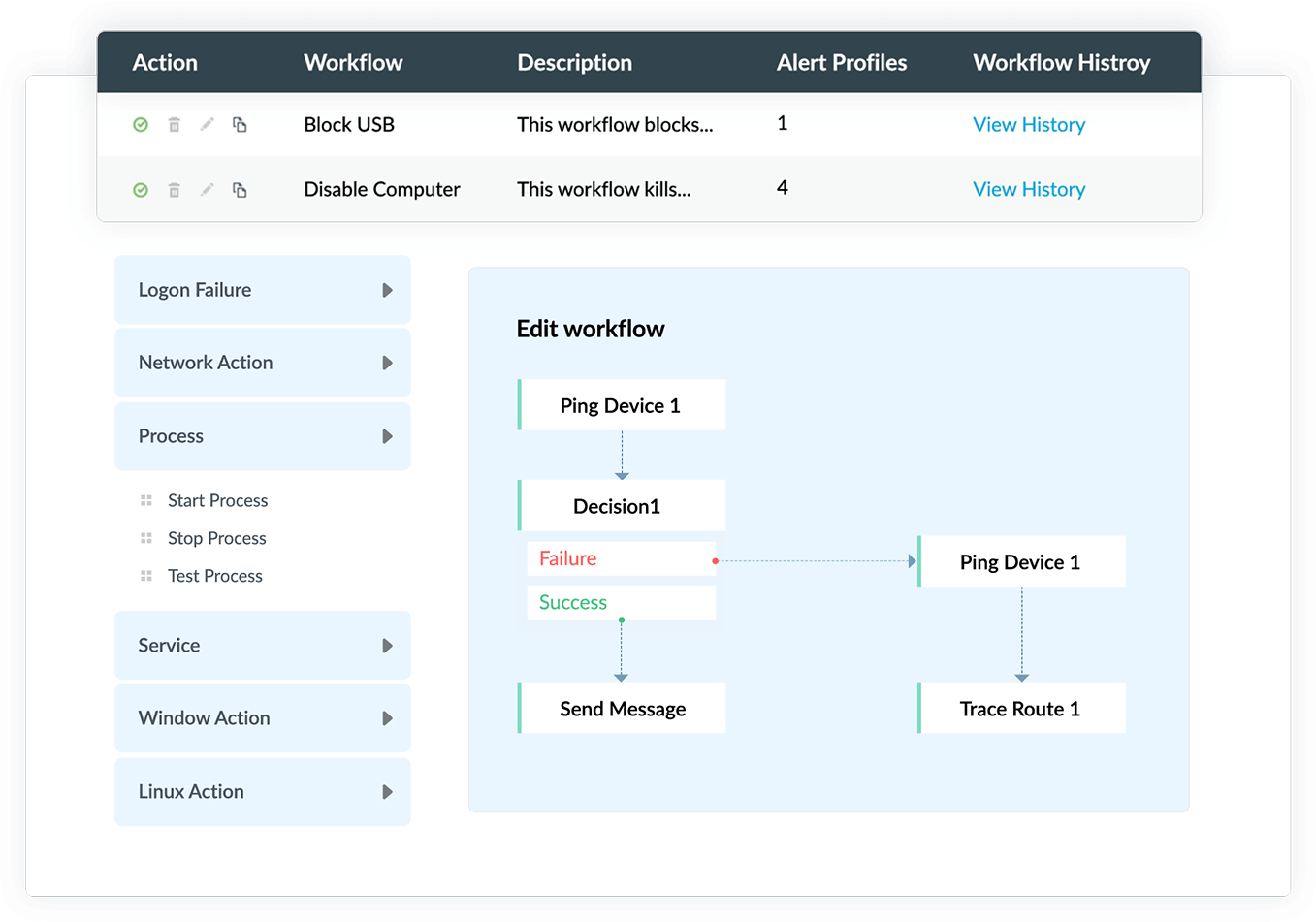
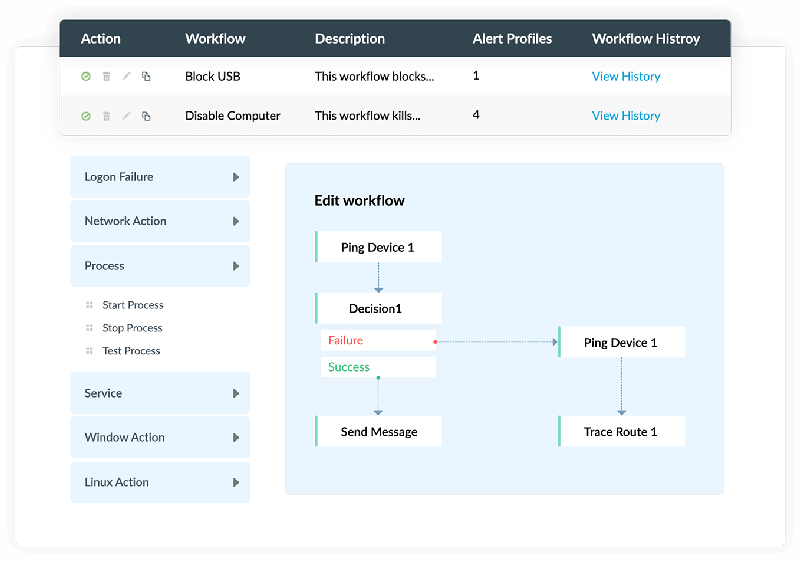
With Log360, you can respond to critical security threats immediately by setting up incident response workflows. They are executed automatically as a responsive action following the occurrence of a security incident.


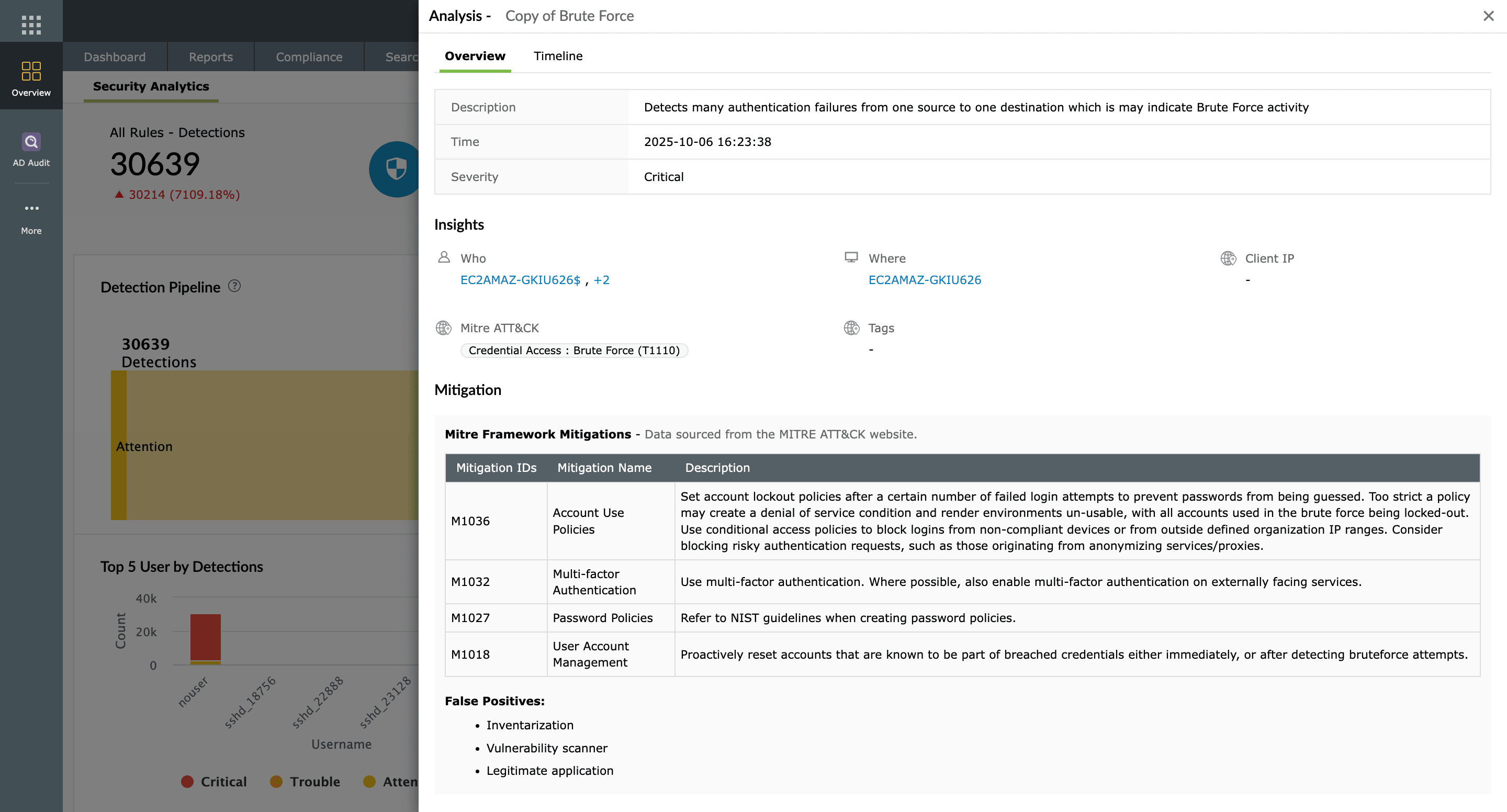
Using the MITRE ATT&CK framework, Log360 can help your security team detect the latest, advanced cyberthreats in your organization's network.
Gain valuable insights into various security-related events with intuitive dashboards and graphical reports that are updated instantly upon log collection.
Simplify forensic analysis with Log360's powerful log search engine. Analyze raw and formatted logs, and generate forensic reports to find the root cause of a security incident.
Resolve security incidents with ease by assigning tickets to security administrators automatically using Log360's built-in ticketing tool.
Integrate with external ticketing tools, such as Jira Service Desk, Zendesk, ServiceNow, ManageEngine ServiceDesk Plus, Kayako, or BMC Remedy Service Desk to manage incidents effectively.