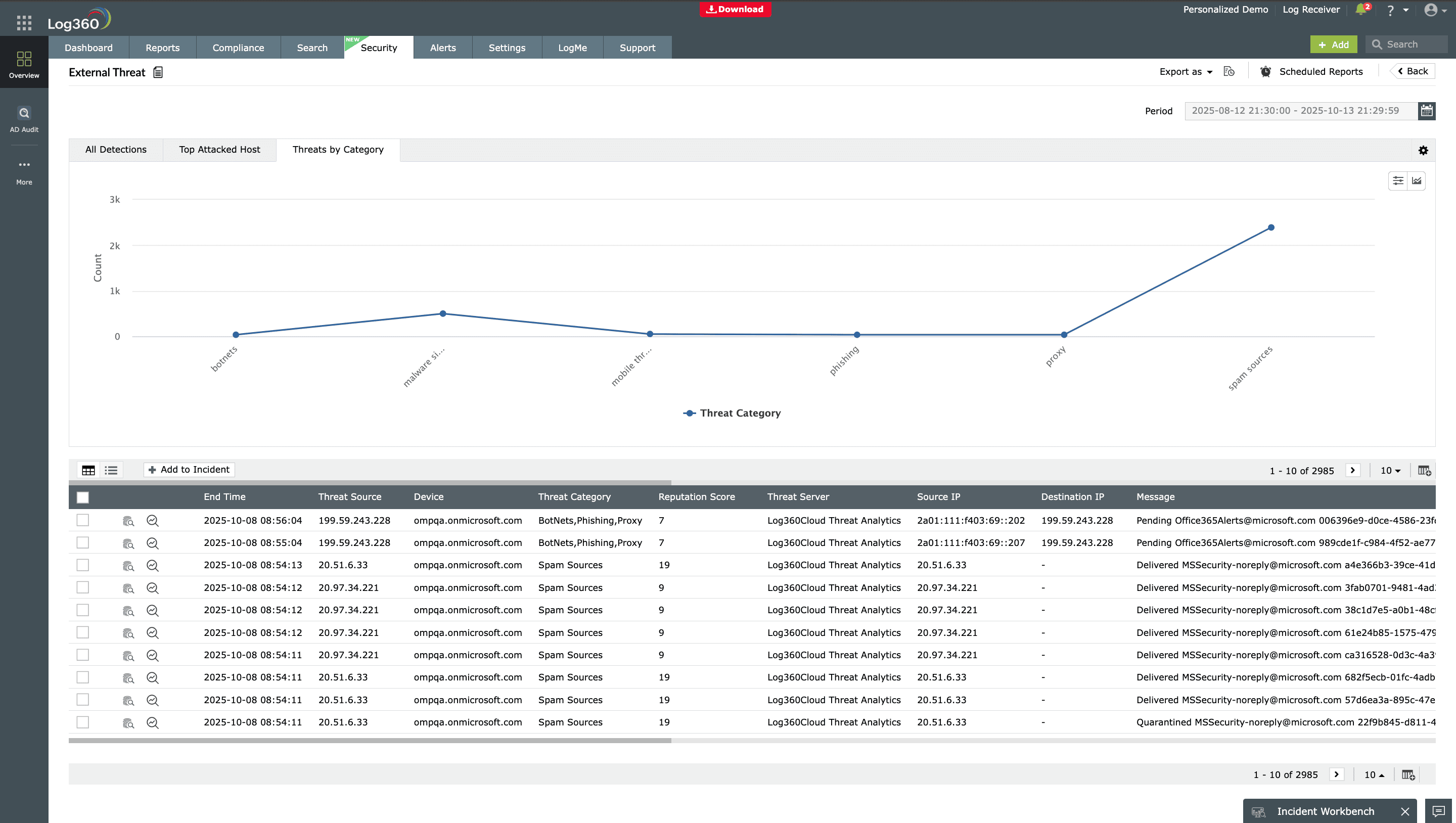
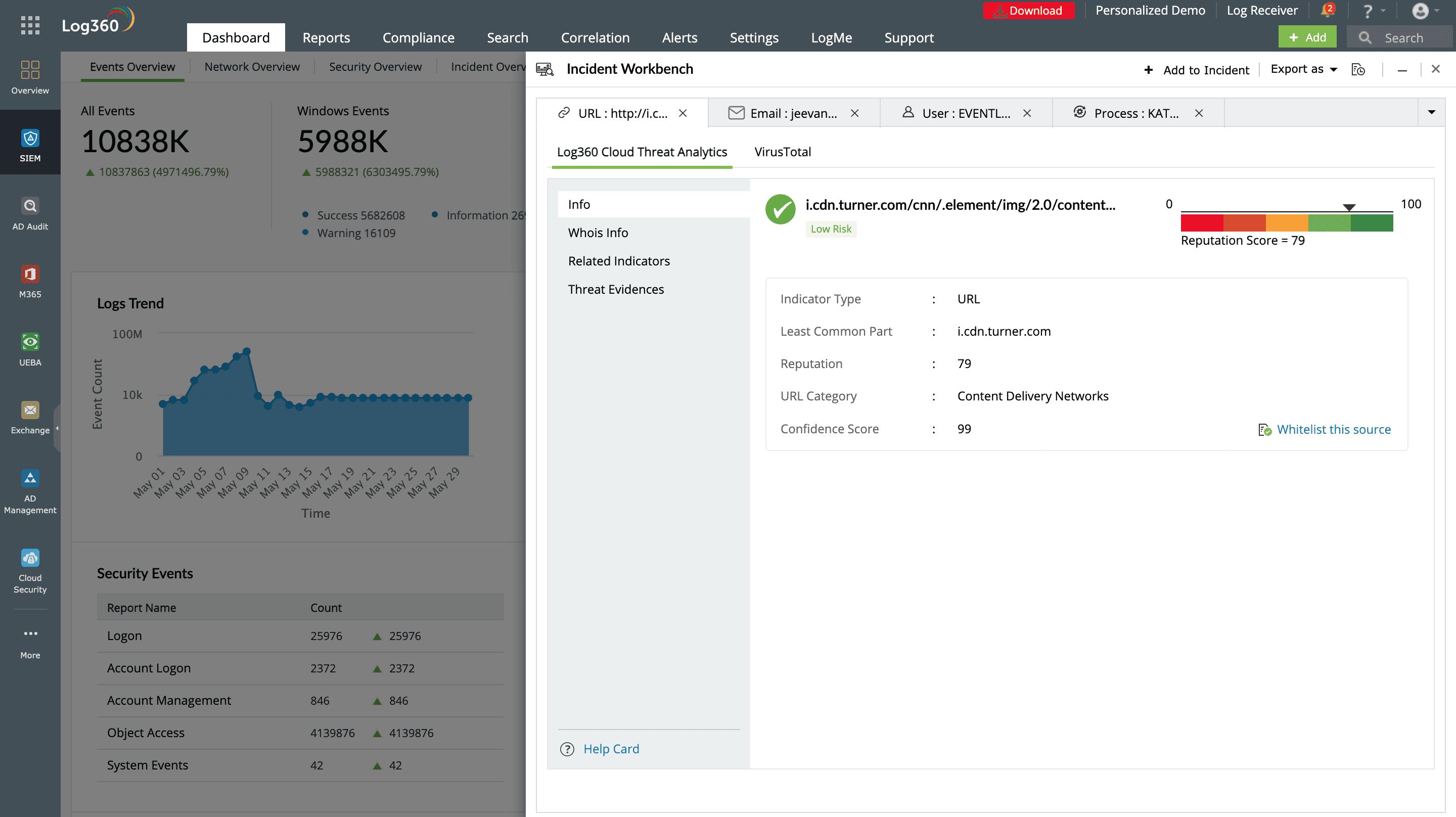
Threat intelligence
Enhance your hunts with actionable threat intelligence. Log360 integrates with global threat feeds to enrich your log data with known malicious IPs, domains, and file hashes, helping you detect IoC faster and correlate them with real-time activity in your network.
Learn more
Automated incident response
With predefined correlation rules, Log360 can pinpoint attack patterns and initiate automated responses, helping you respond swiftly to incidents and reduce potential damage.
Learn more
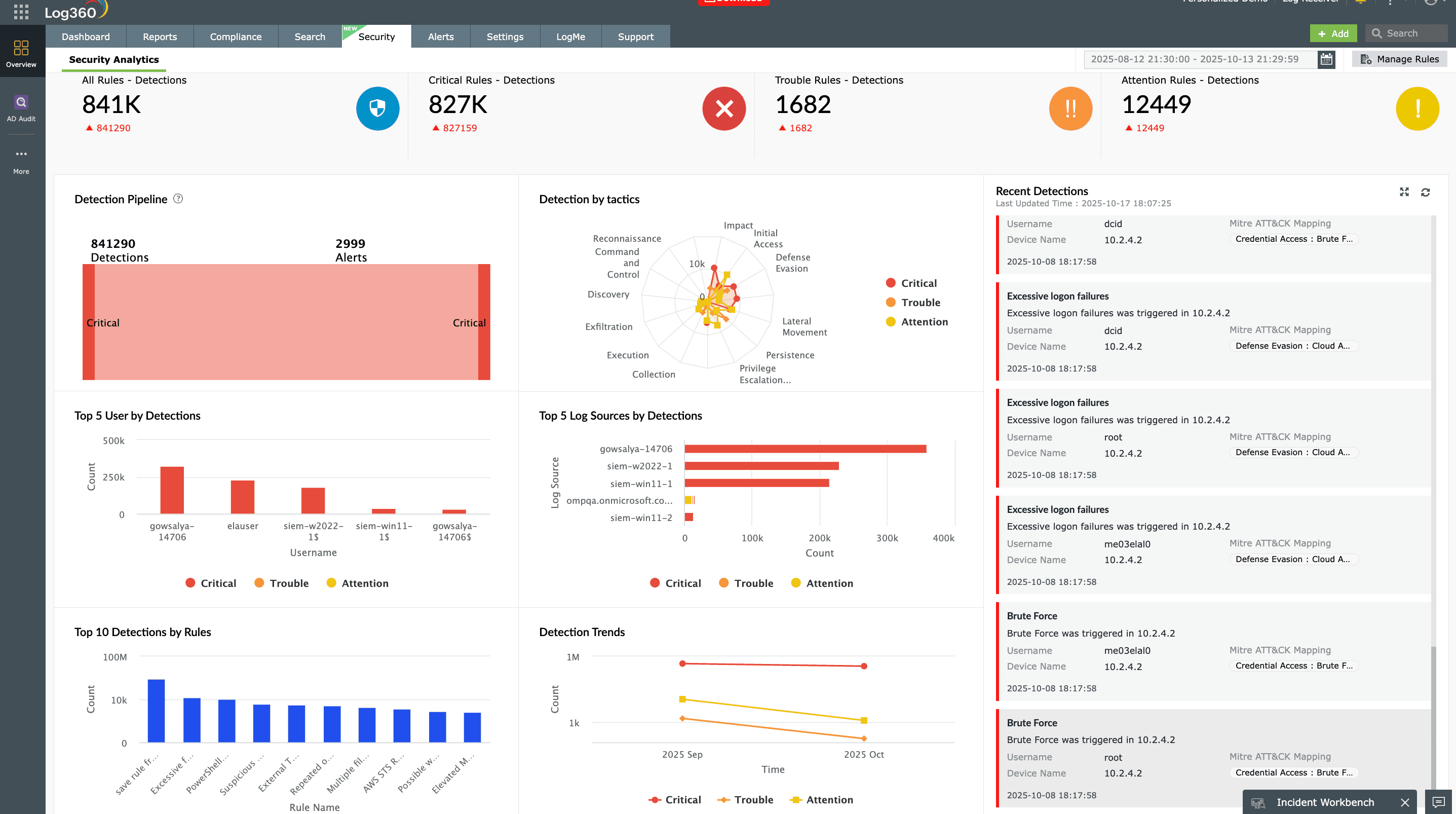
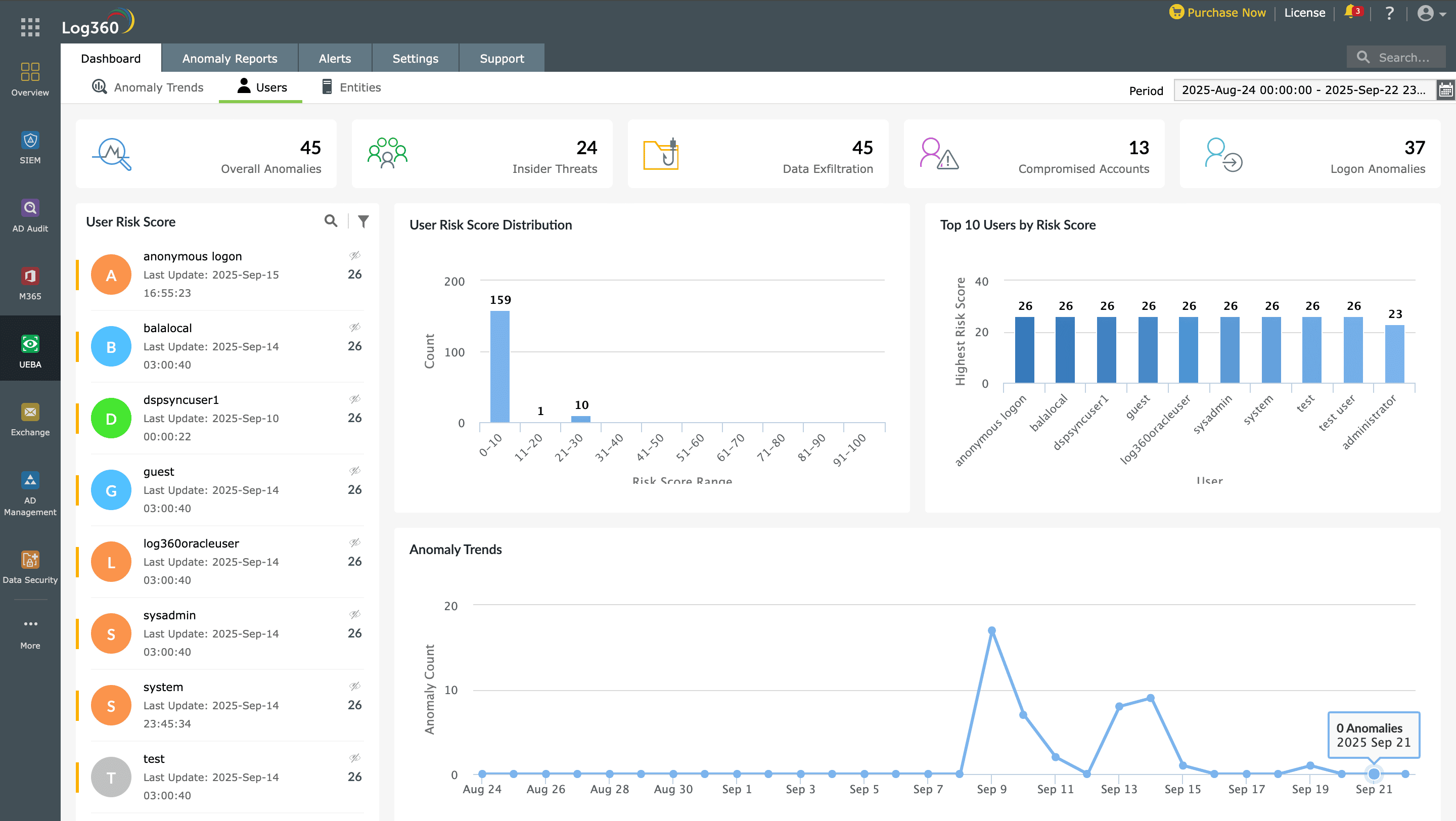
Advanced threat detection
Log360 continuously monitors logins, permissions, and data access across your network to spot suspicious activity in real time. With UEBA, it establishes baselines for users and devices, instantly flagging anomalies that signal insider threats or compromised accounts.
Learn more
Integrated compliance management
Log360 simplifies compliance with automated reports for standards like PCI DSS, GDPR, CCPA, HIPAA, and SOX, while ensuring secure, tamper-proof log archival for long-term retention and audit readiness.
Learn more