Related content
What is threat detection?
Cyberattacks have evolved far beyond the days of obvious viruses and noisy intrusions. Today, threats often unfold quietly over days or even months. Attackers blend into normal activity, wait for the right moment, and strike when no one’s watching. That's why threat detection is critical.
According to Secureframe’s 2025 breach statistics, organizations take an average of 204 days to identify a data breach and 73 days to contain it. That is more than half a year of potential exposure— proof of how vital effective threat detection has become.
Threat detection is about identifying malicious or suspicious activity before it causes real damage. It is the watchtower of your cybersecurity defenses, scanning your network, endpoints, and cloud environments for any sign that something’s wrong. Without it, even the strongest firewalls or encryption cannot help you if an attacker is already inside your network.
Understanding threat detection
Threat detection is the process of monitoring systems, networks, and user activity to spot indicators of compromise (IoCs) or behavior that deviates from normal activity. Think of it as your organization’s early warning system.
In modern environments, cybersecurity threat detection isn’t limited to one place. Cybersecurity threat detection spans:
Network threat detection: Network threat detection tools monitor data flows for unusual traffic patterns, suspicious connections, or policy violations. This includes analyzing packet data, monitoring bandwidth usage, and identifying communication with known malicious IPs.
Endpoint monitoring: Detect malware, privilege escalations, and unauthorized processes on devices. Modern endpoint detection goes beyond traditional antivirus, using behavioral analysis to catch zero-day exploits and fileless malware.
Cloud threat detection: Track changes, access patterns, and activity in SaaS platforms and cloud infrastructure. With 94% of enterprises using cloud services, cloud-native threat detection is essential for identifying misconfigurations, unauthorized access, and data exfiltration attempts.
Identity and access monitoring: Analyze user behavior to detect compromised credentials, insider threats, and privilege abuse across both on-premises and cloud environments.
Because attacks can move across these layers, effective detection requires visibility everywhere.
The detection lifecycle
Effective cybersecurity threat detection is a continuous cycle that evolves as attackers adapt and new threats emerge. This ensures that every suspicious activity is not only spotted but also analyzed, acted upon, and used to strengthen future defenses.
1. Monitoring
The cycle begins with constant monitoring of your environment, network traffic, endpoint activity, user behavior, and cloud workloads. This creates visibility across all assets. Advanced threat detection systems, such as SIEM or network threat detection tools, collect and normalize logs from multiple sources so patterns can be identified in real time. Without this visibility, the rest of the lifecycle can’t function.
2. Alerting
When activity deviates from the norm—an unusual login location, a suspicious file transfer, or a policy violation—the detection system triggers an alert. Efficient threat detection software prioritizes these alerts based on severity and context, helping security teams focus on what matters most. To avoid overwhelming analysts with noise, modern solutions use correlation, machine learning, and contextual enrichment to reduce false positives. This ensures teams concentrate on real threats instead of benign anomalies. Effective configuration and use of detection rules remains critical to keeping alerts actionable.
3. Investigation and forensics
Once an alert is raised, analysts move to the investigation phase. This involves gathering evidence, correlating events, and determining whether the activity is a true threat or a benign anomaly. For example, a flagged data transfer could be a malicious exfiltration attempt or simply an automated backup. Investigation typically follows the MITRE ATT&CK framework, mapping observed behaviors to known adversary tactics. Modern threat detection platforms offer investigation workbenches that combine automated evidence collection (such as IP reputation checks), data enrichment, and timeline reconstruction with human expertise to reduce false positives.
4. Response
If the threat is confirmed, the team initiates a response. This involves isolating a compromised endpoint, blocking a malicious IP address, revoking user access, or applying a firewall rule. Speed is critical here; the longer a threat lingers, the more damage it can cause. Integration between detection tools and response mechanisms (as in EDR or XDR platforms) can automate some actions to reduce dwell time.
5. Feedback loop
The final step is feeding insights from the incident back into the detection system. This could mean refining detection rules, updating threat intelligence feeds, or improving playbooks for future incidents. This feedback loop is what makes modern cyber threat detection adaptive. Over time, it reduces false positives, strengthens defenses, and ensures that the same attack method won’t bypass detection again.
Core detection techniques
Signature-based detection
This method compares observed activity to a database of known malicious patterns; for example, a file hash linked to ransomware. It’s fast and accurate for known threats, but can miss new or modified attacks.
Anomaly and behavior-based detection
Instead of looking for exact matches, this approach establishes a baseline of normal activity and flags deviations. For example, if a user logs in from another country at three am. and downloads gigabytes of data, this is worth investigating. This is essential for advanced threat detection, where attackers use novel methods that don’t match known signatures.
Threat intelligence integration
Modern systems use feeds of Indicators of Compromise (IP addresses, domains, malware signatures) and frameworks such as MITRE ATT&CK to improve detection accuracy. This enriches alerts with context so analysts can prioritize the most dangerous ones.
Modern detection technologies
Attackers adapt quickly, so advanced threat detection has evolved to use:
- AI and machine learning to spot subtle patterns humans might miss.
- Real-time analytics to reduce detection time from hours to seconds.
- Automated alert categorization to prioritize the most urgent cases.
These capabilities are often built into threat detection software like Extended Detection and Response (XDR), Network Detection and Response (NDR), and Endpoint Detection and Response (EDR) platforms. The goal is to give analysts fewer, more meaningful alerts without losing coverage.
Threat detection tools and their integration with SIEM
| Tools | Primary focus | Key capabilities | SIEM integration benefits |
|---|---|---|---|
| Extended detection and response (XDR) | Unified detection across endpoints, networks, and cloud | Correlates alerts from multiple sources, automated response, and threat intelligence enrichment | Centralizes alerts for easier correlation, reduces alert fatigue, and improves response times |
| Endpoint detection and Response (EDR) | Endpoint activity (PCs, servers, mobile devices) | File/process monitoring, behavioral analysis, isolation/quarantine | Supplies SIEM with endpoint alerts to correlate with network and cloud events |
| Threat Intelligence platforms | External threat context | IOC feeds, MITRE ATT&CK mapping, reputation scoring | Enriches SIEM alerts with context, improves prioritization, reduces false positives |
Measuring detection effectiveness
Quick detection is not enough. Effectiveness depends on accuracy, consistency, and adaptability. Measuring it helps teams understand how well their cyber threat detection works and where improvements are needed.
Key metrics
1. Mean time to detect (MTTD)
This is the average time between the initial occurrence of a malicious activity and the moment it’s detected by your threat detection software or security team. A lower MTTD means your monitoring systems and analysts are spotting threats quickly, reducing the time attackers have to cause damage.
2. Mean dwell time
Also known as the attacker dwell time, this measures how long a threat remains in the environment before being contained or removed. Long dwell times often indicate blind spots in network threat detection, especially if attackers are using stealthy techniques such as living-off-the-land or encrypted C2 channels.
3. False positive rate (FPR)
A high false positive rate wastes analyst time and can cause alert fatigue, making it easier for real threats to slip by unnoticed. Measuring FPR helps fine-tune detection rules, anomaly thresholds, and threat intelligence feeds so your cybersecurity threat detection efforts stay sharp and efficient.
4. Detection coverage
This metric assesses how much of your attack surface is actually monitored. Coverage should span across endpoints, servers, network traffic, cloud workloads, and SaaS platforms. Even the most advanced threat detection system can fail if large parts of your infrastructure are outside its scope.
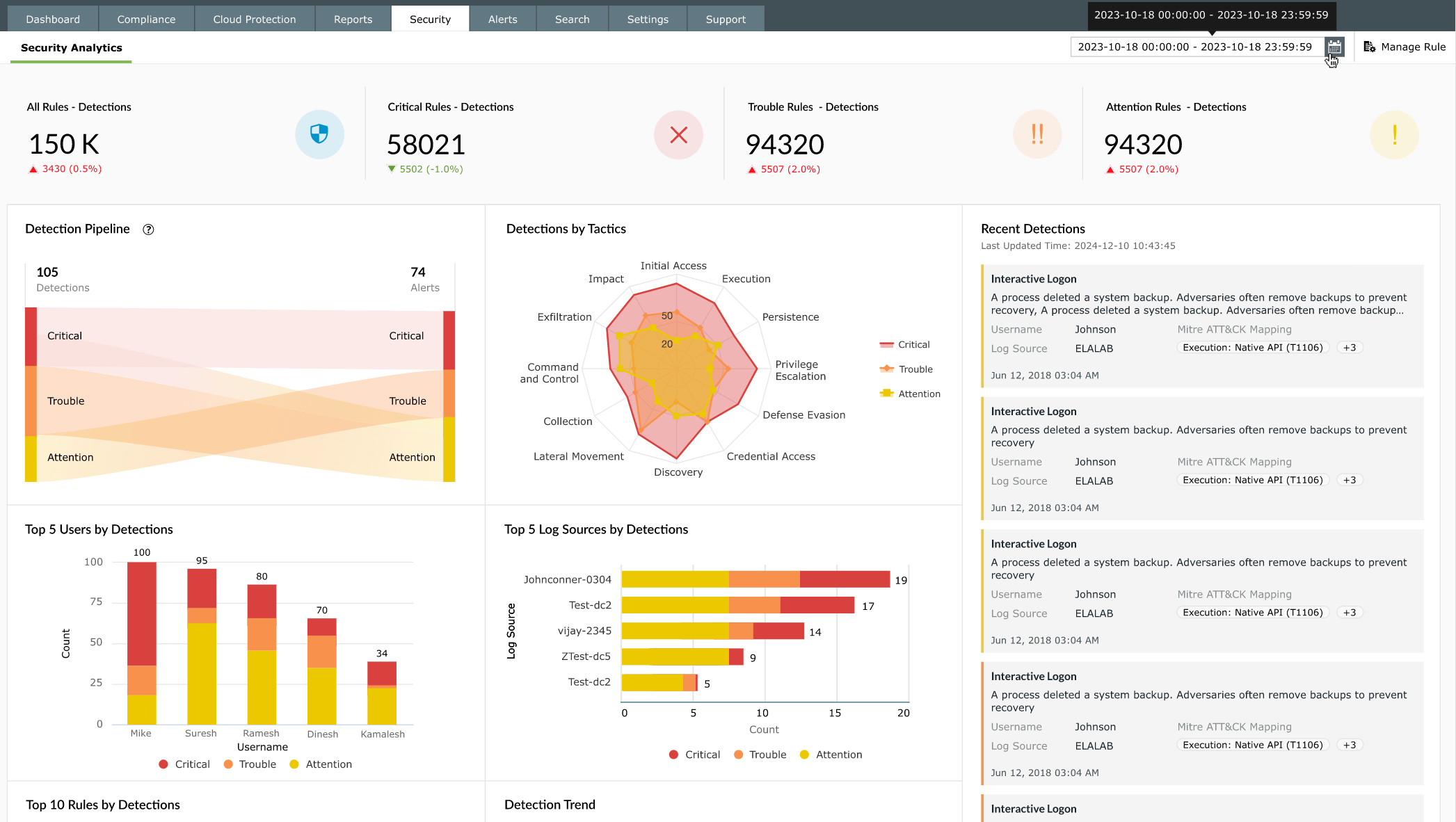
How Log360 helps with threat detection
Real-time event correlation
Log360 collects and correlates events from firewalls, endpoints, cloud platforms, and databases, giving security teams a unified view of activity across the environment. This correlation helps identify attack patterns that might otherwise go unnoticed, enabling early detection and faster incident response.
Threat Intelligence integration
The platform integrates with trusted threat intelligence feeds such as Webroot, STIX/TAXII, and other global threat networks. It automatically matches telemetry against known malicious IPs, domains, and URLs. Log360 generates high-fidelity alerts with contextual details when a match is found, helping teams prioritize actions based on severity and potential impact.
Behavioral analytics and anomaly detection
Using machine learning-powered UEBA, Log360 continuously monitors user and entity behavior across endpoints, servers, and cloud workloads. This enables the identification of unusual activity that could indicate compromised accounts, insider threats, or subtle attack patterns.
Precision tuning and false positive reduction
Log360 allows organizations to fine-tune detection rules according to their environment and operational priorities. By applying context-aware correlation, automated anomaly scoring, and rule customization, it significantly reduces false positives, ensuring analysts focus on genuine threats instead of benign anomalies. This precision tuning helps maintain SOC efficiency in complex environments.
Cloud-delivered rules for comprehensive coverage
Log360 provides over 2,000 continuously updated correlation rules covering endpoints, networks, cloud workloads, and applications. These rules can be adjusted to fit organizational needs, providing broad coverage while minimizing alert fatigue.
MITRE ATT&CK alignment and contextual insights
Detections are aligned with MITRE ATT&CK techniques, giving teams visibility into active attack tactics. Correlating multiple events across devices and platforms provides actionable insights,enables a faster and informed response.
Rapid alerting and response
Real-time, risk-prioritized alerts allow teams to triage and respond quickly. Flexible rule configuration and automated responses reduce dwell time and improve operational efficiency
What’s next?
Ready to strengthen your threat detection strategy? Start your free 30-day trial with expert guidance and experience the full capabilities yourself.
FAQs
1. How does threat detection handle encrypted traffic?
Network threat detection tools analyze metadata, flow patterns, and TLS/SSL traffic characteristics to detect anomalies without decrypting all content, ensuring visibility while maintaining performance.
2. What role does threat intelligence play in automated detection?
Threat detection software leverages external feeds, indicators of compromise (IOCs), and attacker reputation data to enrich alerts. This improves the accuracy of cybersecurity threat detection and helps prioritize response actions.
3. How are MITRE ATT&CK frameworks applied in detection systems?
Many advanced threat detection tools map observed activities to MITRE ATT&CK tactics. This approach provides structured insight into attacker behavior and helps analysts understand the sequence of attacks.
- What is threat detection?
- Understanding threat detection
- The detection lifecycle
- Core detection techniques
- Threat detection tools and their integration with SIEM
- Measuring detection effectiveness
- How Log360 helps with threat detection



