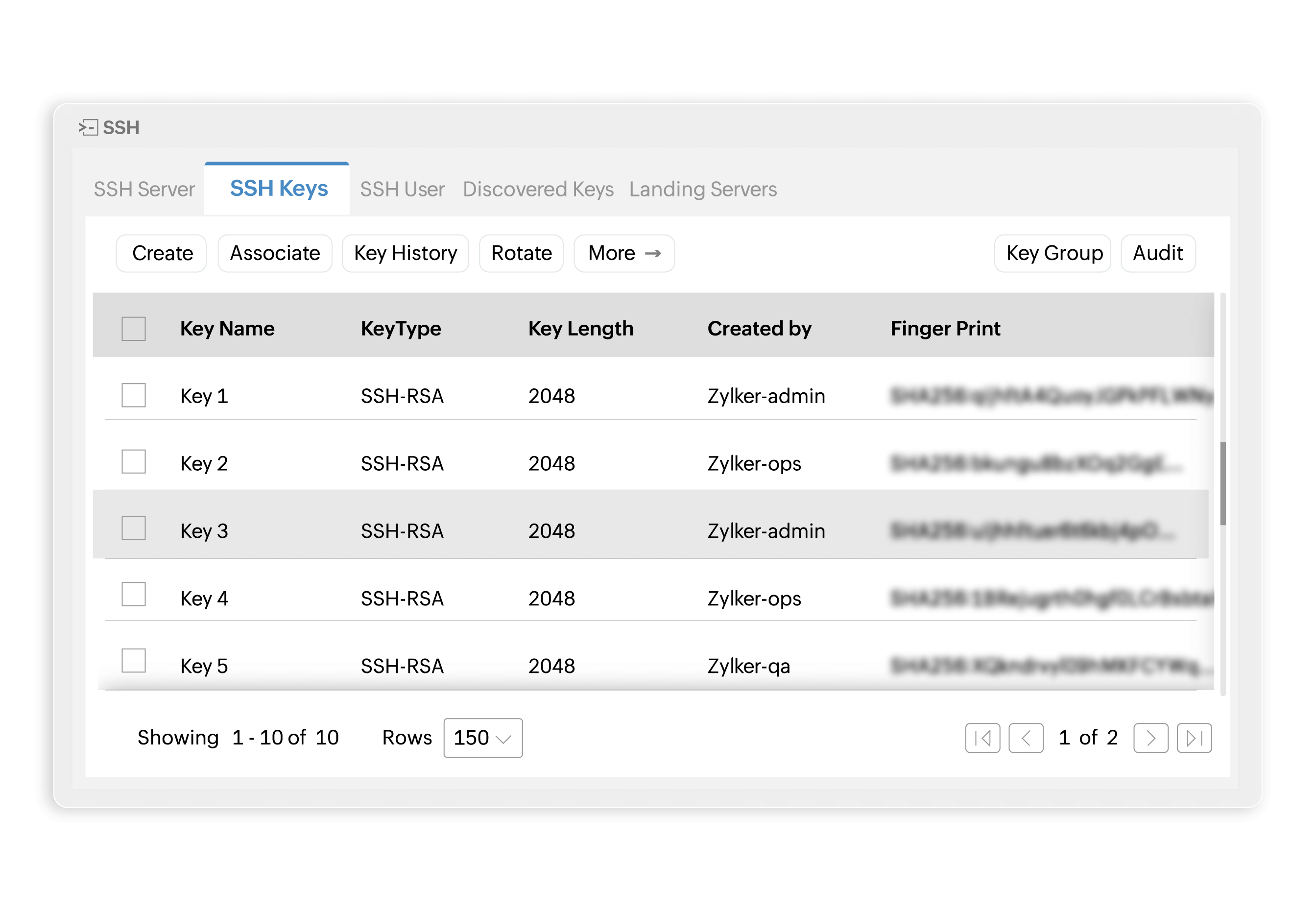
Get a holistic view of all SSH keys
Gain comprehensive visibility of all your SSH keys from a single console. Key Manager Plus discovers and inventories keys across your infrastructure, along with critical information like their associated SSH users, deployment status, location, and usage history. The discovery process can also be automated using Key Manager Plus' customizable scheduling options, ensuring continuous oversight of your SSH key infrastructure.
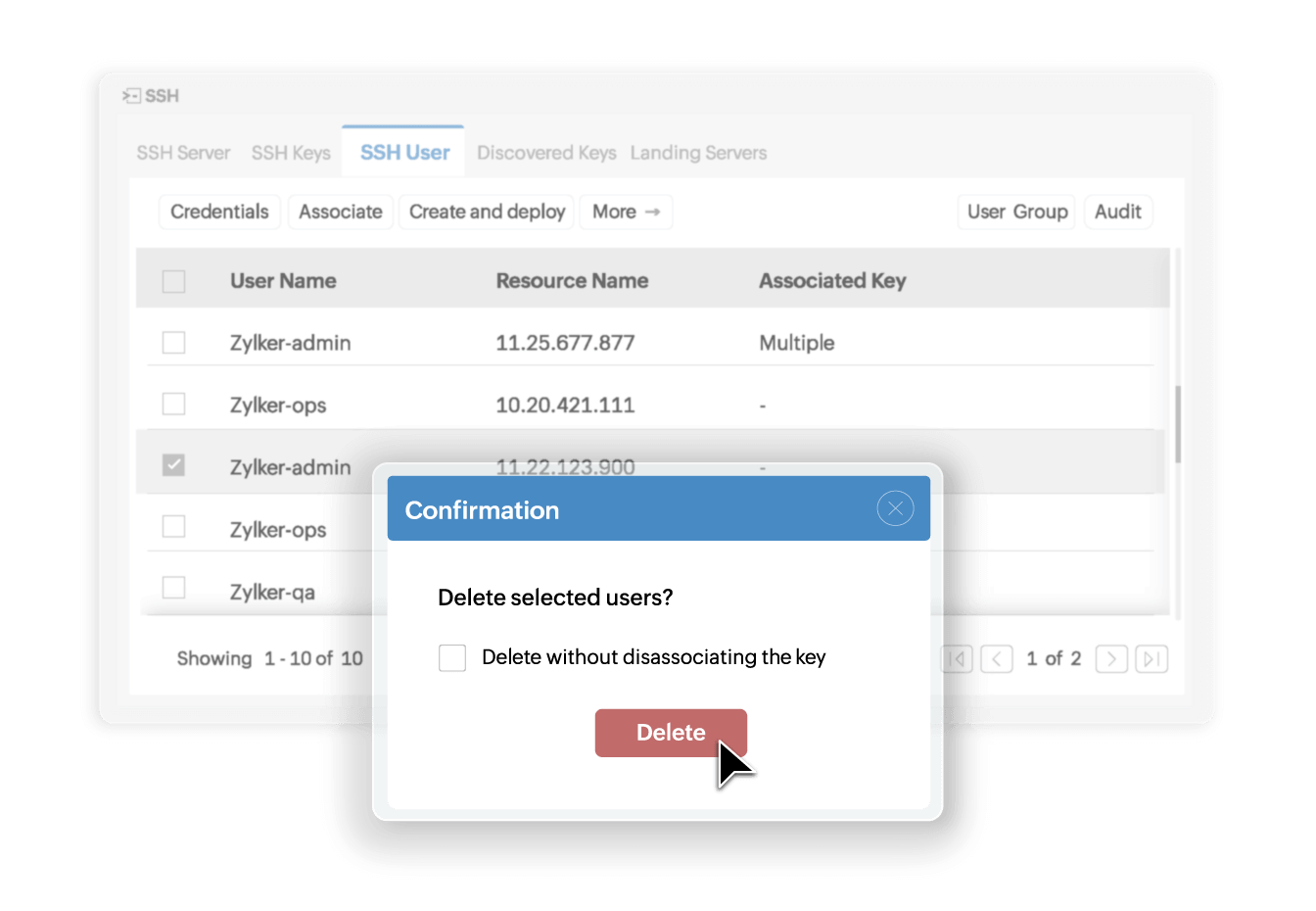
Curb the risk of orphaned keys
Eliminate security risks from orphaned and unused SSH keys with automated life cycle management. Key Manager Plus automatically disassociates keys when user accounts are deleted, preventing former employees from retaining access to sensitive resources. The platform's key-user account relationship mapping easily identifies and removes unused keys across the network, ensuring that privileged access is revoked promptly when roles change.
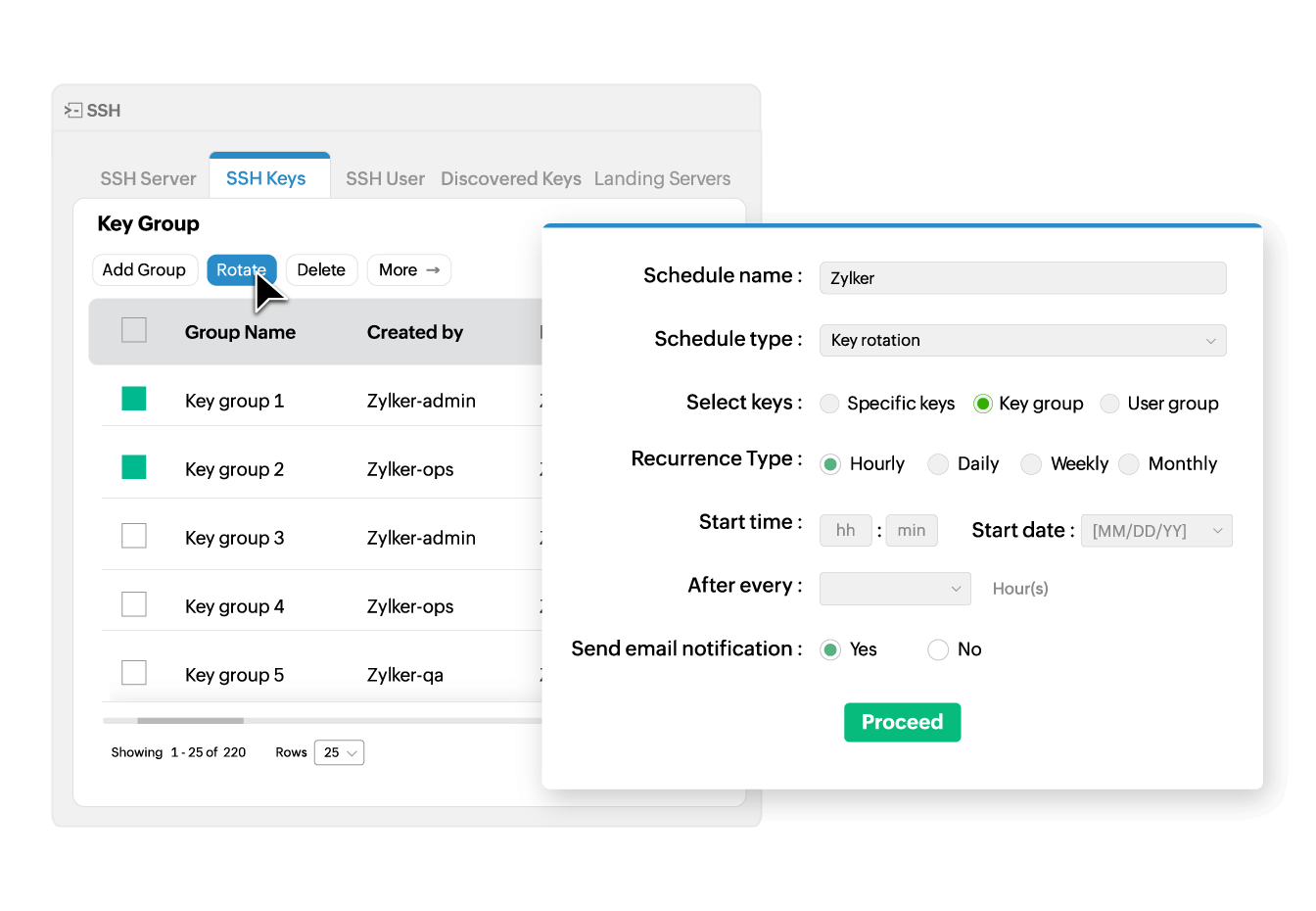
Manage SSH keys in bulk
Create groups of SSH keys, users, and resources for easy organization and to carry out bulk operations. Key Manager Plus enables administrators to perform key rotation, deployment, deletion, and association operations on multiple keys, users, and resources simultaneously, eliminating the need for time-consuming repetitive, manual processes.
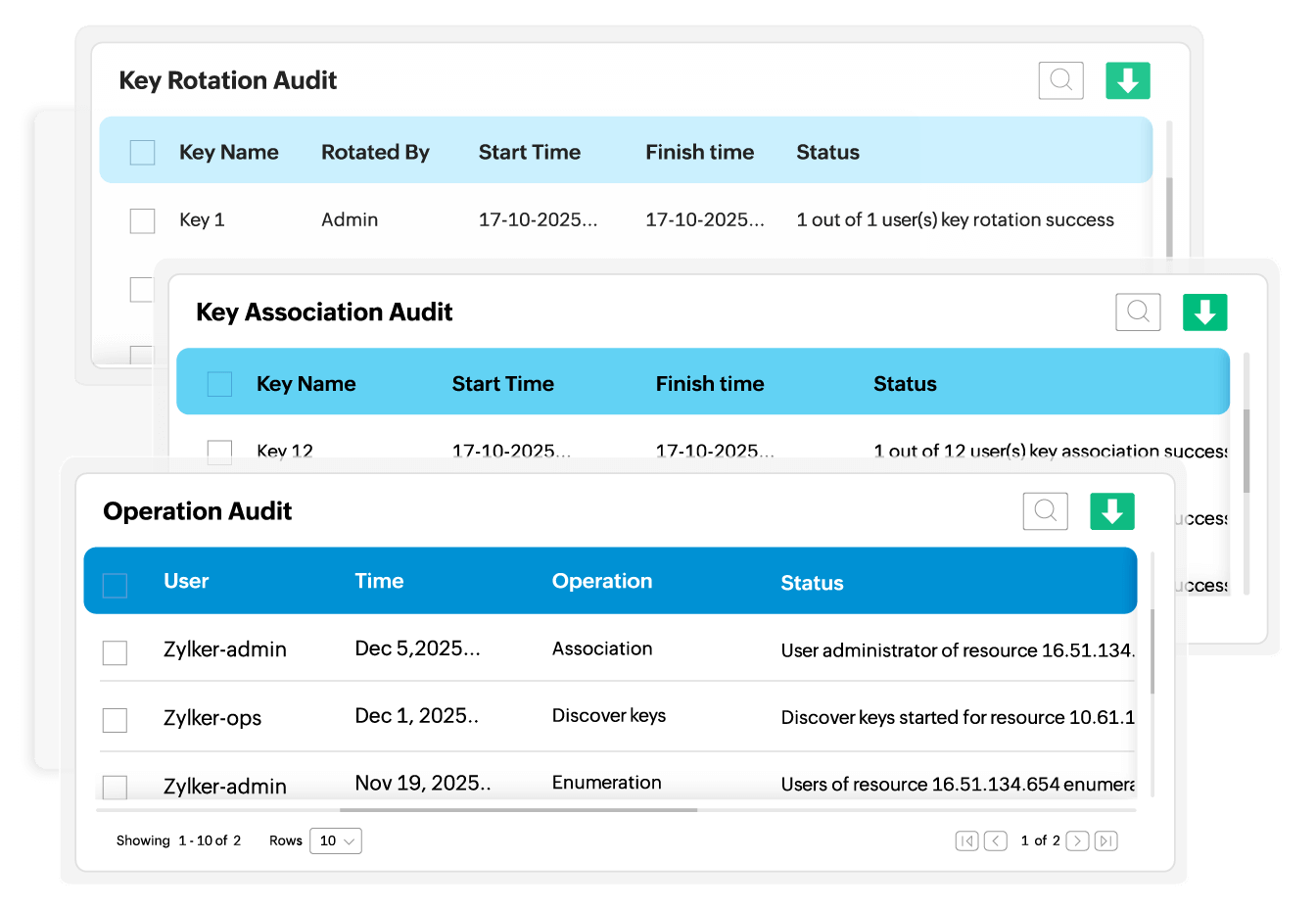
Stay on top of user activities
Maintain complete accountability of SSH key operations with comprehensive audit trails and activity monitoring. Key Manager Plus tracks each user's activity and records their actions along with timestamps, enabling administrators to identify suspicious behavior quickly and take appropriate remedial actions. Key Manager Plus features dedicated audits for key rotation, key association, discovery, and schedule operations to capture every detail of activities performed.