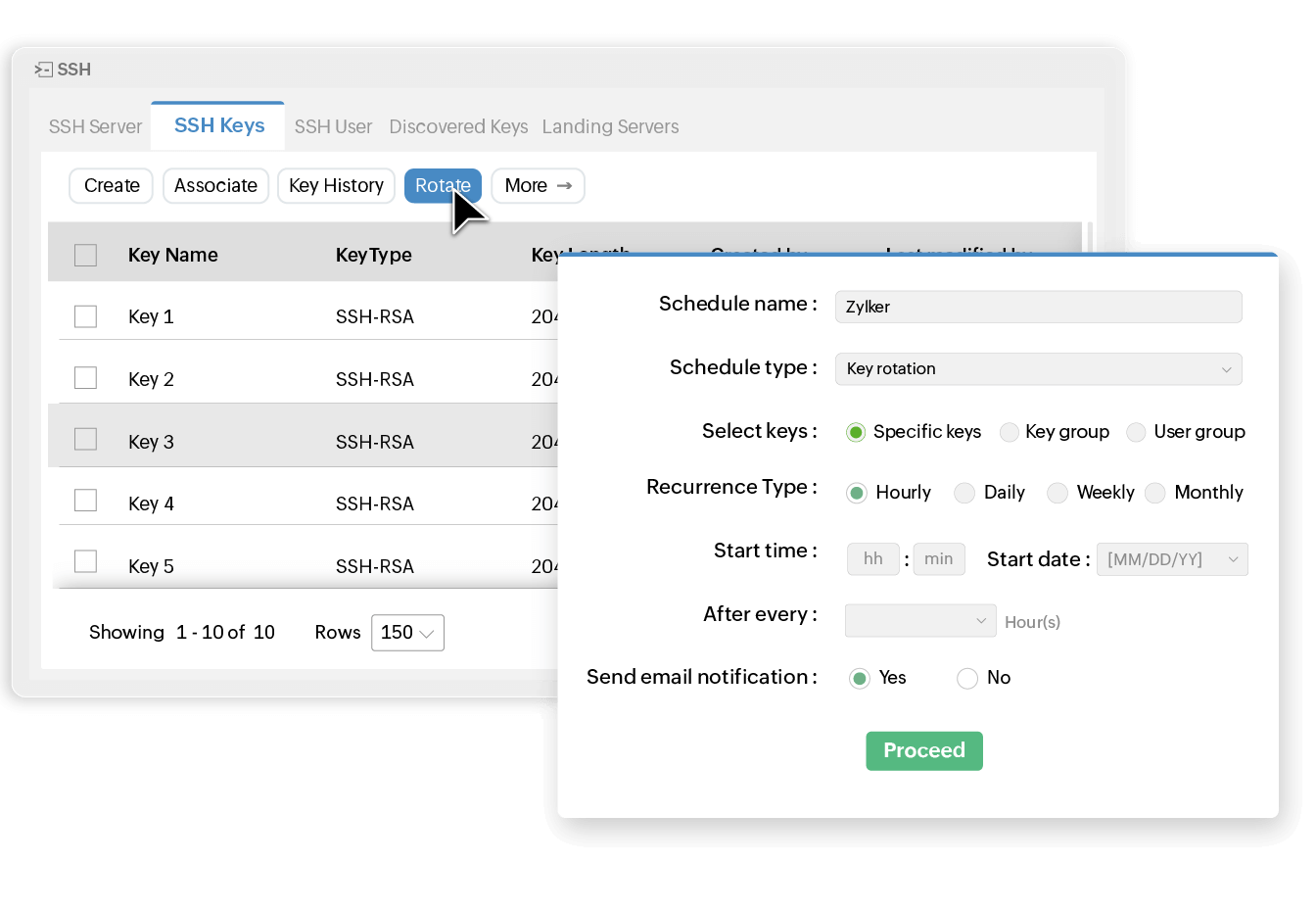
Create automatic rotation cycles
Automate the rotation for your SSH keys at periodic intervals that match your requirements. With Key Manager Plus, you can perform instant key rotations on demand or schedule recurring rotations to happen automatically.
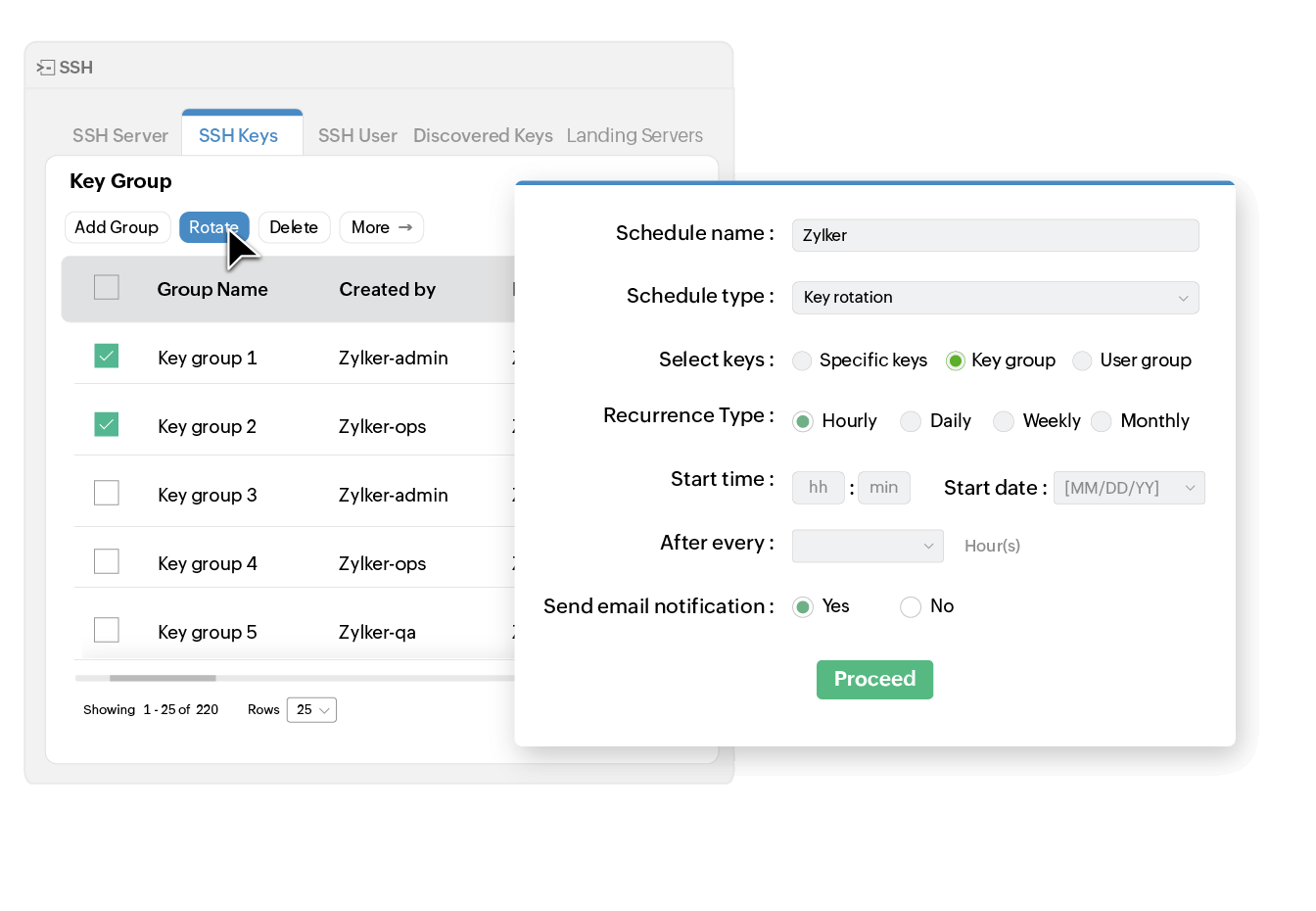
Efficiently rotate numerous keys in groups
Execute rotation operations efficiently across large volumes of SSH keys in your environment. Key Manager Plus helps you organize keys into groups and perform bulk rotations simultaneously, reducing the time required to update credentials at scale. Further, you can notify stakeholders via email after every key rotation.
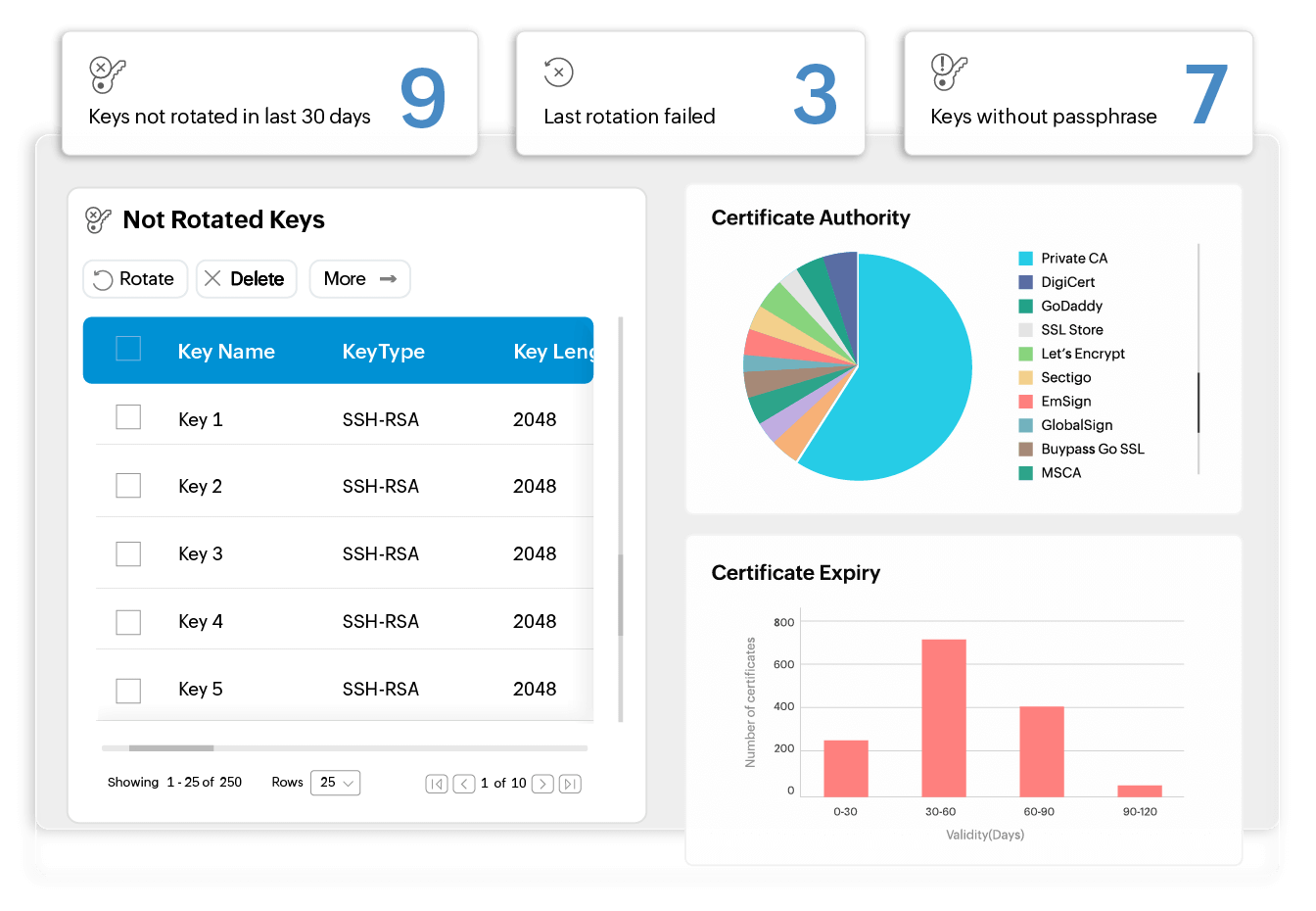
Get notified about static keys
Stay ahead of security risks with proactive monitoring of SSH keys. Key Manager Plus has dedicated dashboard widgets to inform you about keys that have not been rotated for a long time. It also allows you to configure the maximum number of days for a key to remain unrotated, after which you will be promptly notified.
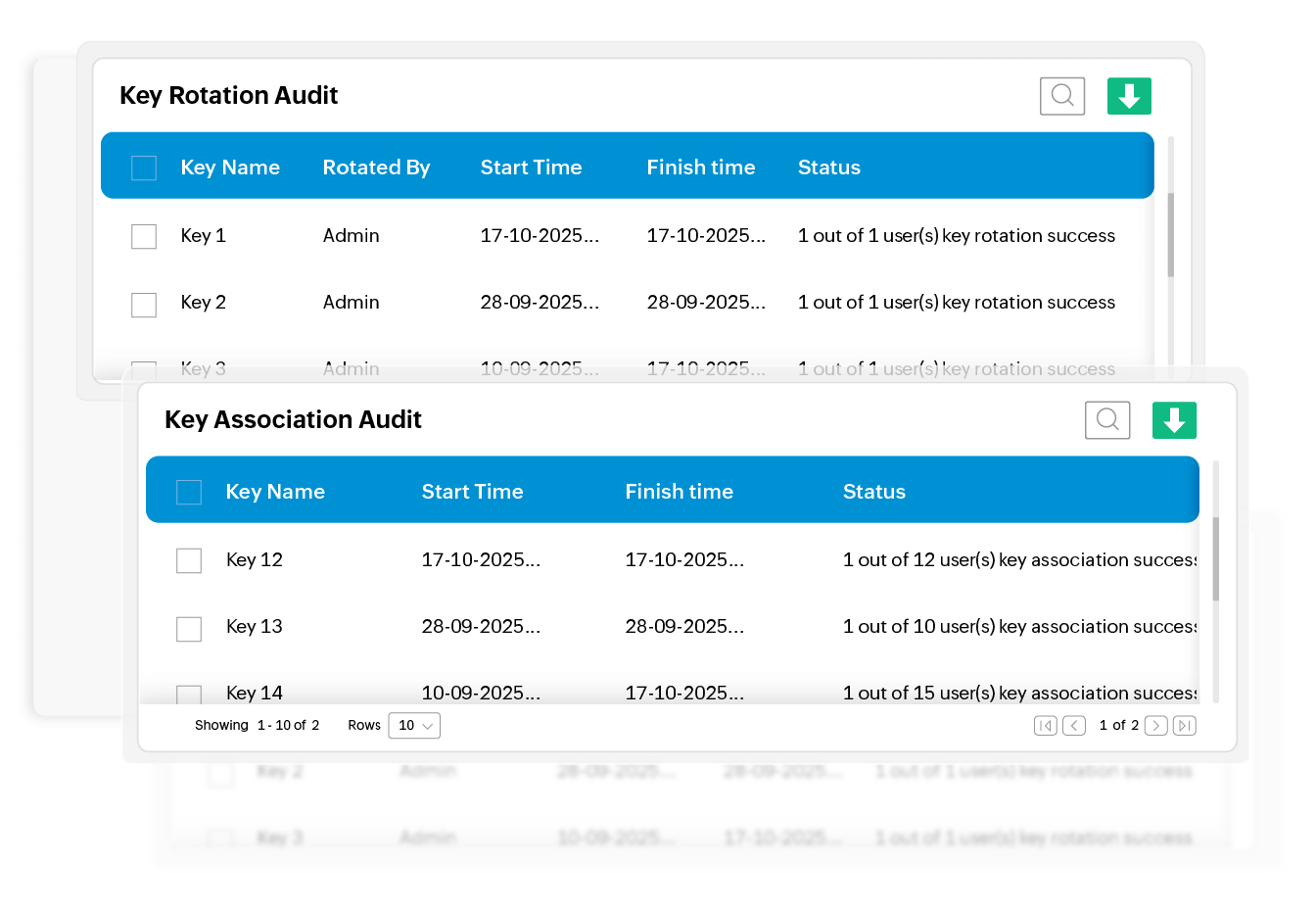
Maintain comprehensive audit trails
Get complete visibility into key rotation operations, associated resources, when changes took place, which users performed them, and more with Key Manager Plus' comprehensive SSH audits and reports.