What is a Golden Ticket attack?
A Golden Ticket attack is a powerful domain persistence attack carried out by abusing vulnerabilities in the Kerberos authentication protocol to forge authentication tickets and gain unlimited access to all the Kerberos-enabled services in the domain, including the domain controller services, file servers, DNSs, print servers, and more.
About the attack
The Kerberos protocol comprises a set of request and response messages between the user, the key distribution center (KDC) and the server that the user wants to access. The KDC is a service that runs on the domain controller and is responsible for the whole Kerberos authentication process.
Overview of the Kerberos protocol
- When a user logs in to a system in the domain, the pre-authentication data, which is the timestamp encrypted with the password hash of the user account, will be sent to the KDC.
- The KDC reads the username and obtains the password hash from the account manager database in the DC and tries to decrypt this message. If the message gets successfully decrypted, it implies the user has valid credentials and will be authenticated to access the domain services.
- The KDC sends the ticket-granting ticket (TGT) in response to the user. The TGT contains the details of the user and is encrypted with the KRBTGT account's password hash. The default lifetime of a TGT is 10 hours, but this can be altered by the admin. During this period, the user can send any number of requests to access the domain services without going through authentication each time.
- The TGT is used to create the service requests, which will be sent to the ticket granting server (TGS), which is part of the KDC. The TGS will then decrypt the message, add a new session key, and send the service ticket signed by the service account's password hash to the user. The user can now directly connect with the server using the TGS ticket.
Vulnerabilities
- The KRBTGT account's password is the most critical element of the Kerberos authentication process. By stealing this password hash, attackers can create the Golden Ticket, i.e., the TGT that appears authenticated by the KDC, and can be sent to a TGS to generate authentic service tickets.
- In the forged TGT, the lifetime of the ticket can be increased to 10 years. This will enable the continuous use of the ticket until the KRBTGT password is reset.
Attack flow
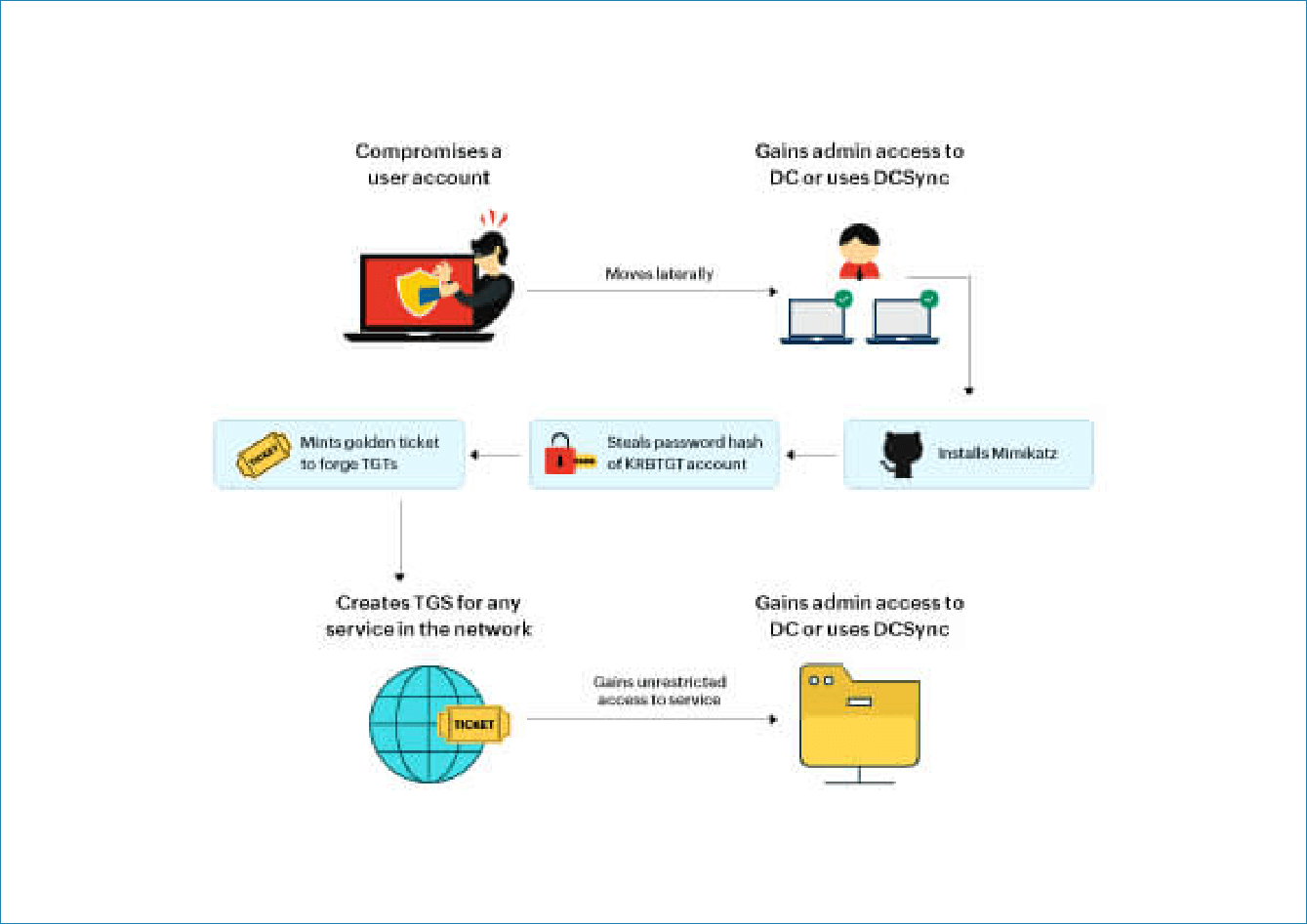
Imagine an attacker has gained access to a user account in your network using a phishing email.
- Escalate the privileges of a user account by adding administrative access or replication privileges to a domain controller (DC).
- Install Mimikatz, malicious software, and run the DCSync command to obtain the password hash of the KRBTGT account.
- Create the Golden Ticket using the username, domain name, domain security identifier (SID), group ID, and obtained password hash. This ticket will be dumped in the credential cache and used to obtain the TGS tickets.
For example, the attacker can create a TGT with the AD group name and the relative identifier (RID) of the file administrators to obtain service tickets to access critical files containing sensitive data.
- Lurk in your environment for as long as needed—the golden ticket may not expire for years to come.
Detection mechanism
To detect a Golden Ticket attack, you must monitor your network constantly to look for the following indicators of comprise (IoCs):
- Privilege escalation
a. Execution of a new process by a user account (DCSync)
b. Anomalous behavior of privileged user accounts
- Mimikatz installation
a. Installation of malicious software detected by antivirus software
- Malicious activities after the attack is executed
a. First-time access of a critical resource by an end user
b. Accumulation of data at endpoints
c. Unusual user behavior such as requesting access to resources at abnormal times
- Investigating events
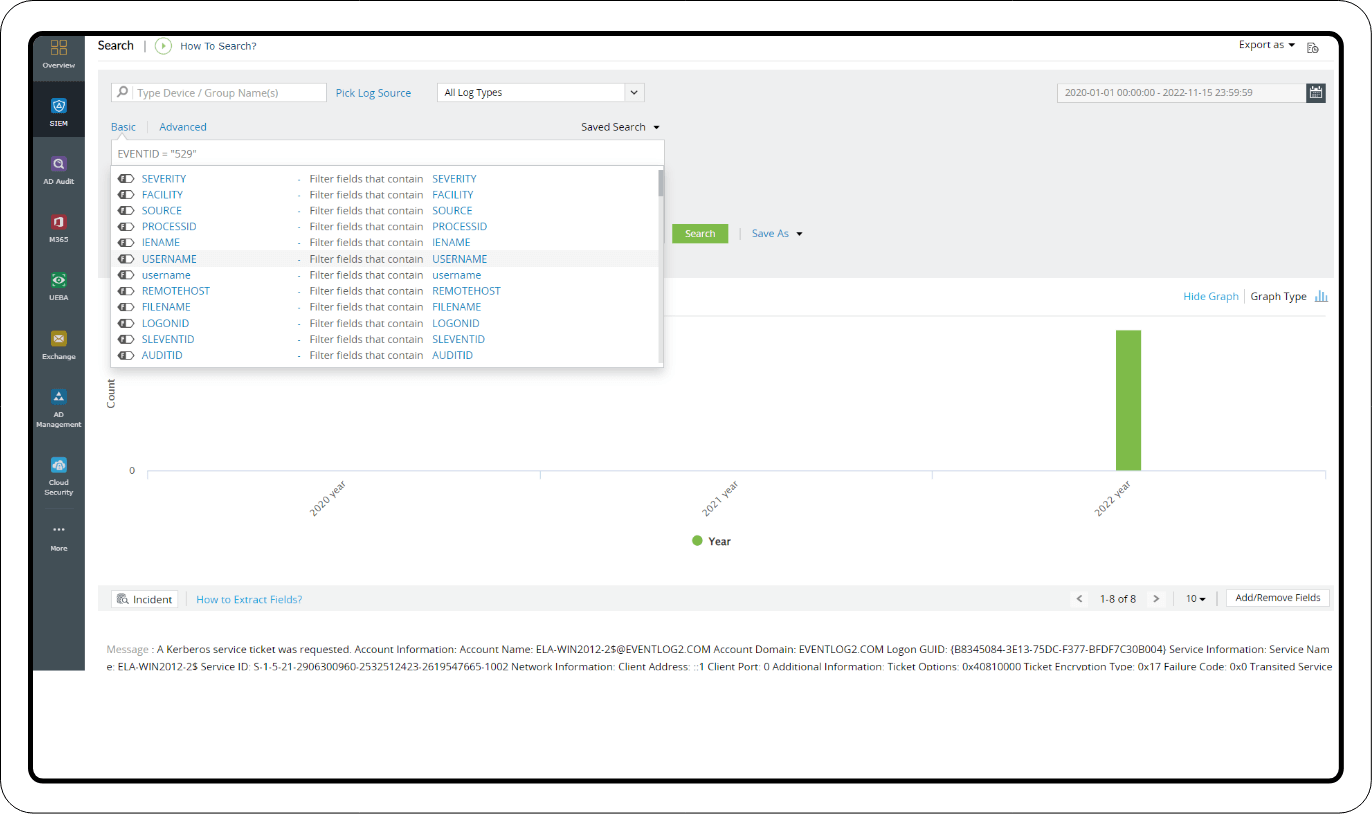
Event ID: 4769
This event is recorded in the domain controller for the TGS ticket requests from the users. Failure of this event may have genuine reasons, but examining certain result codes and investigating further will reveal important anomalies like:
- Discrepancies in the forged tickets. The TGTs generated by tools might differ from the original Kerberos tickets. Some fields like the group ID might be missing, fake usernames might be in use, etc.
- Multiple attempts to access different services that the user is not authorized to access.
- Use of weaker encryption.
- TGTs signed by the old password hash and sent multiple times by the user after resetting the KRBTGT account password.
These IoCs can be easily spotted by a security information and event management (SIEM) solution. SIEM solutions can track and alert on suspicious activities in real time to mitigate the attack.
A good SIEM solution should offer the following features to detect the IoCs of a Golden Ticket attack:
- In-depth analytics and real-time alerts: Collecting and analyzing log data from your network helps a SIEM solution identify anomalous activities. It then can raise real-time alerts for threats and help you look into the incident and mitigate it. Privilege escalation attempts, suspicious user activities, and installation of malicious software can be easily identified with the help of interactive dashboards containing crucial network security information.
- User and entity behavior analytics (UEBA): Often going hand in hand with SIEM solutions, UEBA helps form a baseline of user activity based on everyday network activity patterns. If users deviate from their baselines, the solution increases their risk scores, indicating a threat.
- Incident response: A SIEM solution can help you respond to the IoCs of a Golden Ticket attack by allowing you to automate incident response using predefined workflows for specific alerts from its incident management console.
Remediating a Golden Ticket attack requires resetting the KRBTGT account's password twice; this is because Active Directory stores all of the current and previous passwords of the accounts. So the Kerberos tickets containing the password hash of the old passwords will be valid even after you reset the KRBTGT password once.
You can manually reset the password twice from your AD or from the password management console of your SIEM solution. Finally, you need to reorganize your AD members and groups to assign only necessary privileges to users to prevent the risk of this attack in the future.
Detecting and mitigating Golden Ticket attacks using Log360
Golden ticket attacks are stealthy and difficult to detect. It's important to use a strategy that combines identifying IoCs and thorough investigation to avoid being hit with a spree of false alarms and acting upon them.
Log360 aids SOCs in implementing investigative strategies to deal with such persistent attacks. This SIEM solution offers useful features like
- Real-time alerts to keep tabs on important events.
- Predefined reports that filter out anomalous activities.
- Log search capabilities that help with forensic analysis.
Detection through alerts
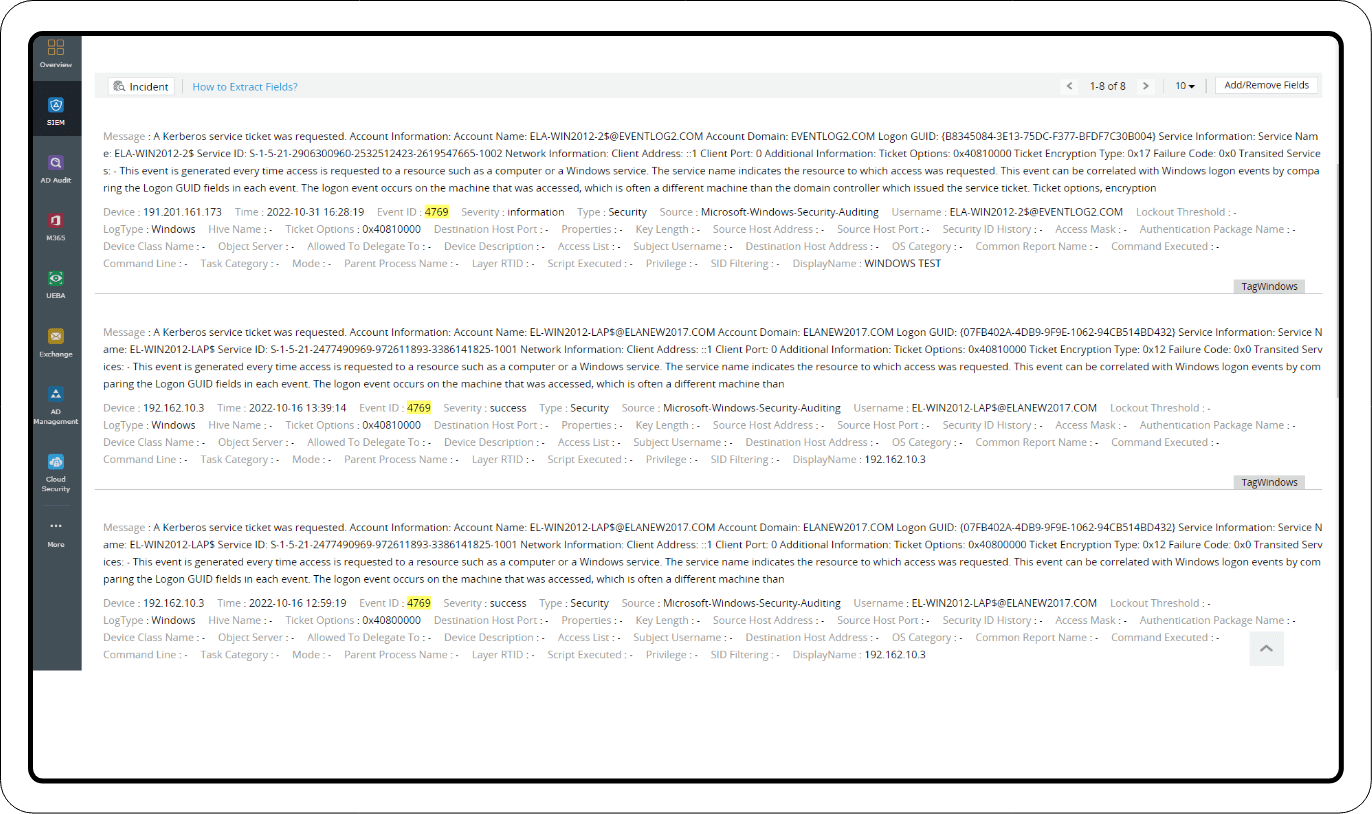
Failure of event ID: 4769
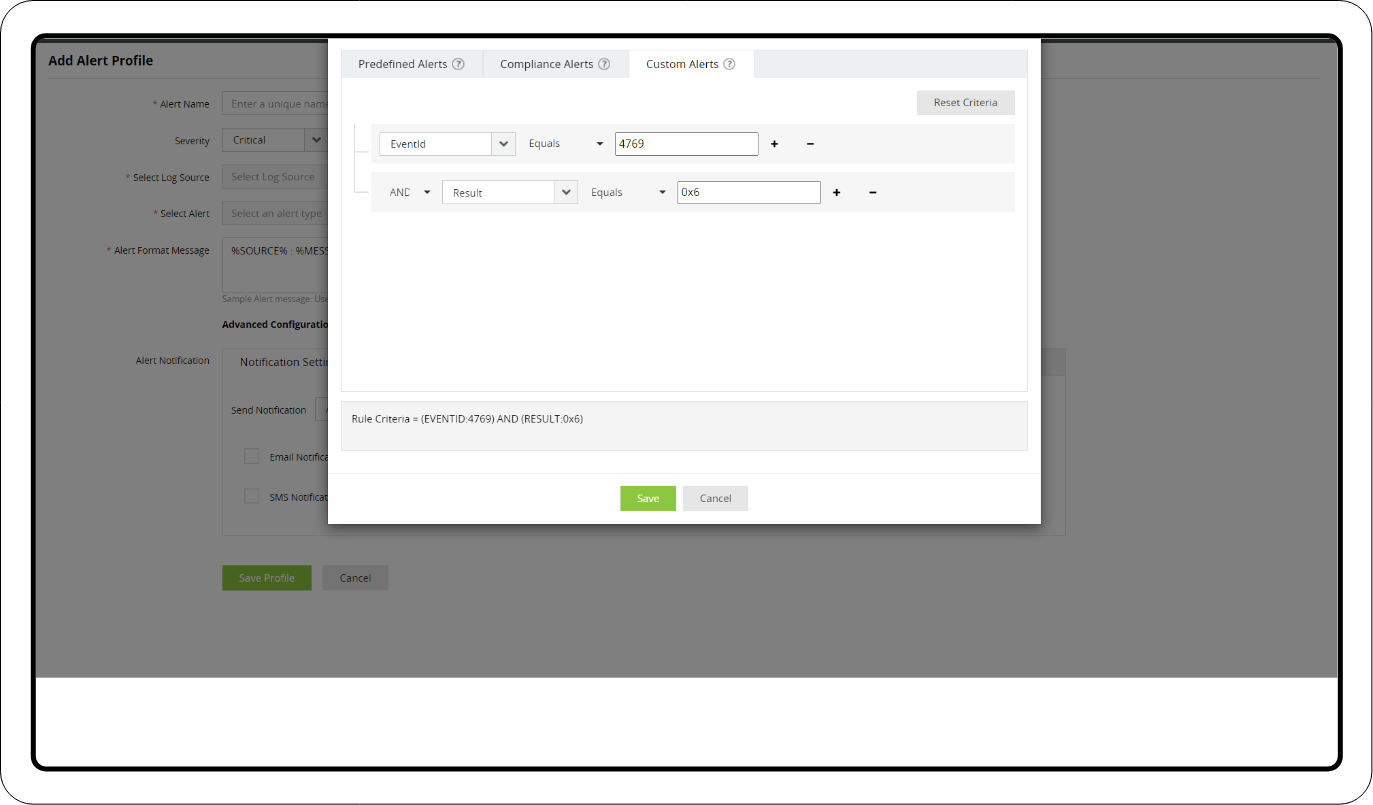
1. Log360 captures the TGS ticket failure event (event ID: 4769) and sends a notification including the cause of the event failure. Additional criteria can be set to trigger alerts for the following result codes that indicate the use of a Golden Ticket:
- 0x6 - TGS request for a username that doesn't exist
- 0xC - The user is not allowed to access the service
- 0x40 - TGT signature is invalid
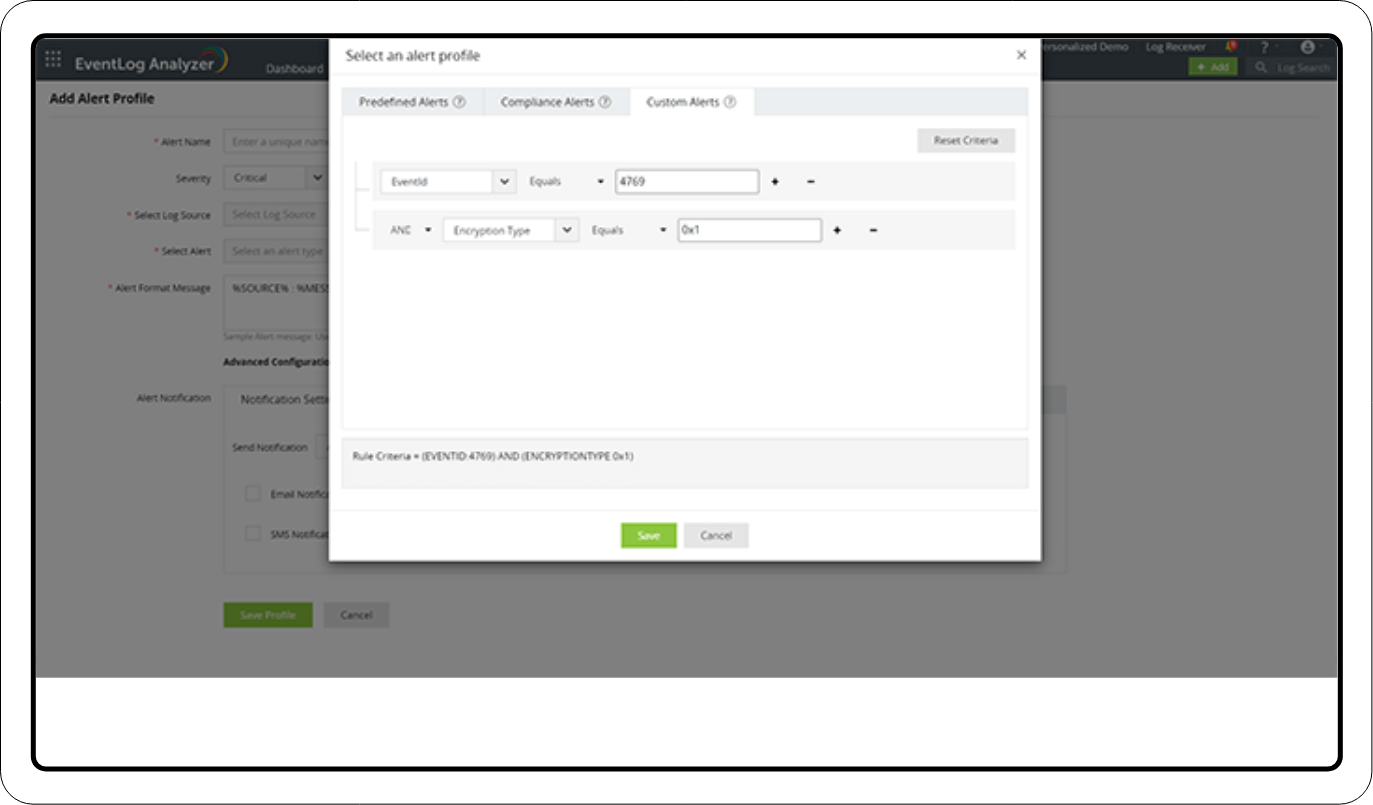
2. Log360 also offers alert profiles to check for weaker encryption in the Kerberos tickets. Result codes like 0x1 and 0x3 are used to set up these alerts.
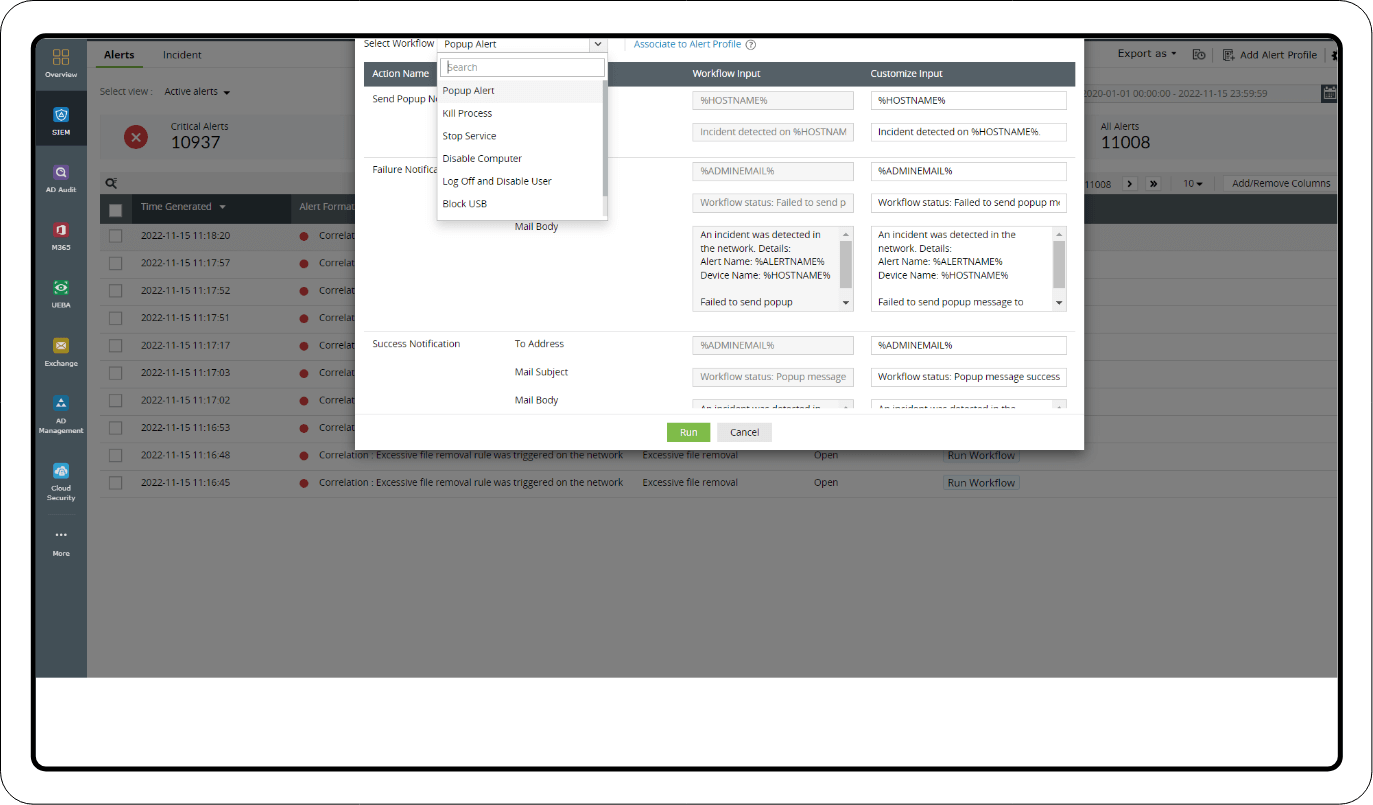
Remediation: Add the triggered alerts as incidents and use Log360's incident dashboard to run response workflows immediately. The workflow has actions like killing the process, logging off and disabling the user, and disabling the computer to stop the attack from proceeding further.
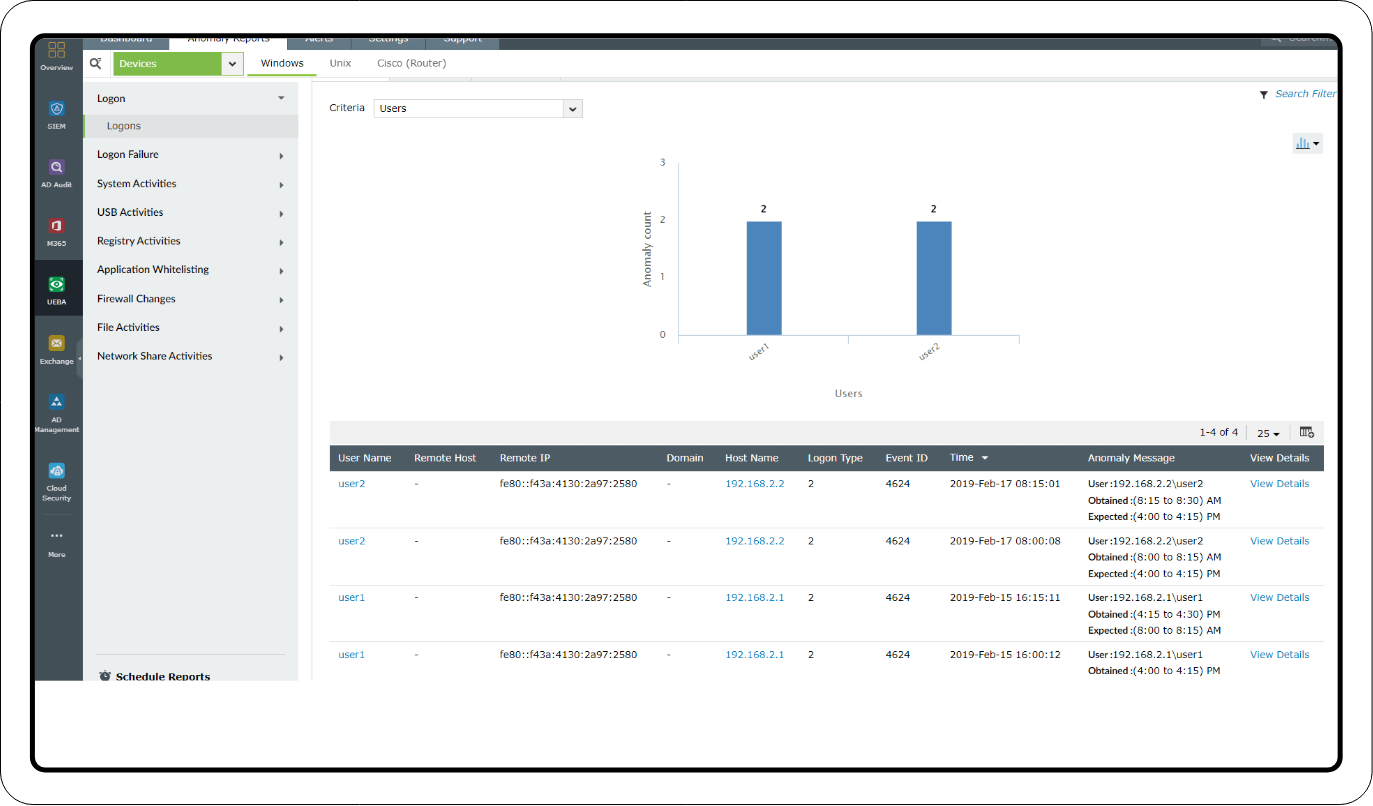
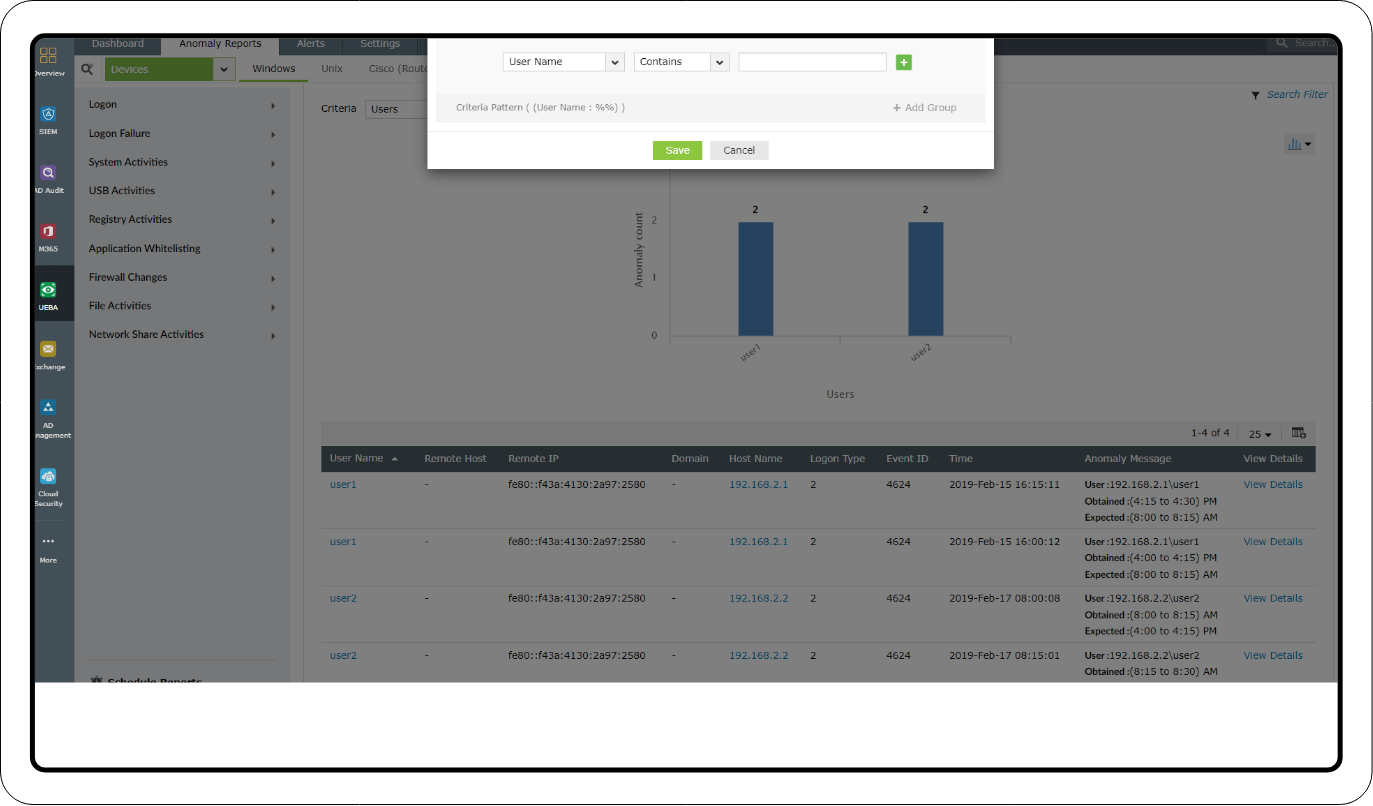
Investigation through log search
Once you start observing alerts for the above-mentioned events, you can investigate further through a log search. Use event IDs 4624 and 4672 to analyze the logon activities. Log360 helps you spot unusual data in the log fields and empty fields. Go through the event history and add additional criteria like username and SID to filter the log data.
Investigation through reports
UEBA Reports
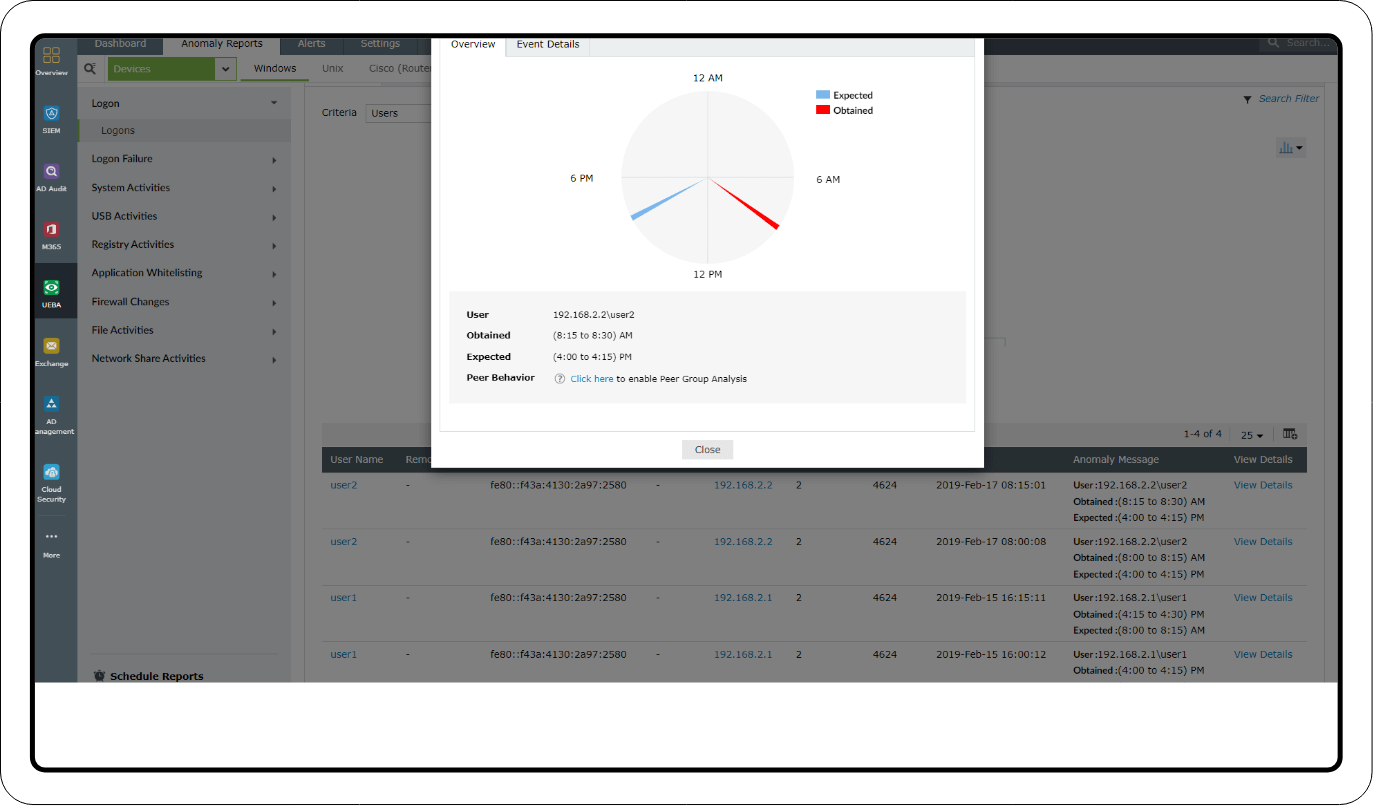
Privileged user monitoring: Investigate suspicious logon activities based on time, count, and pattern anomalies using the Logon and Logon Failure reports. You can also add filters to examine the activities of specific user accounts and privileged users.
Mitre ATT&CK® reports
Log360's Mitre ATT&CK dashboard offers advanced threat analytics with exhaustive reports for each ATT&CK tactic and its sub-techniques. The following Mitre ATT&CK reports help with the detection of Golden Tickets.
1. Credential Access reports
The Steal or Forge Kerberos Tickets section under the Credential Access tactic has important reports, like the Suspicious Kerberos RC4 Ticket Encryption report, that detect the use weaker encryption in the TGS request.
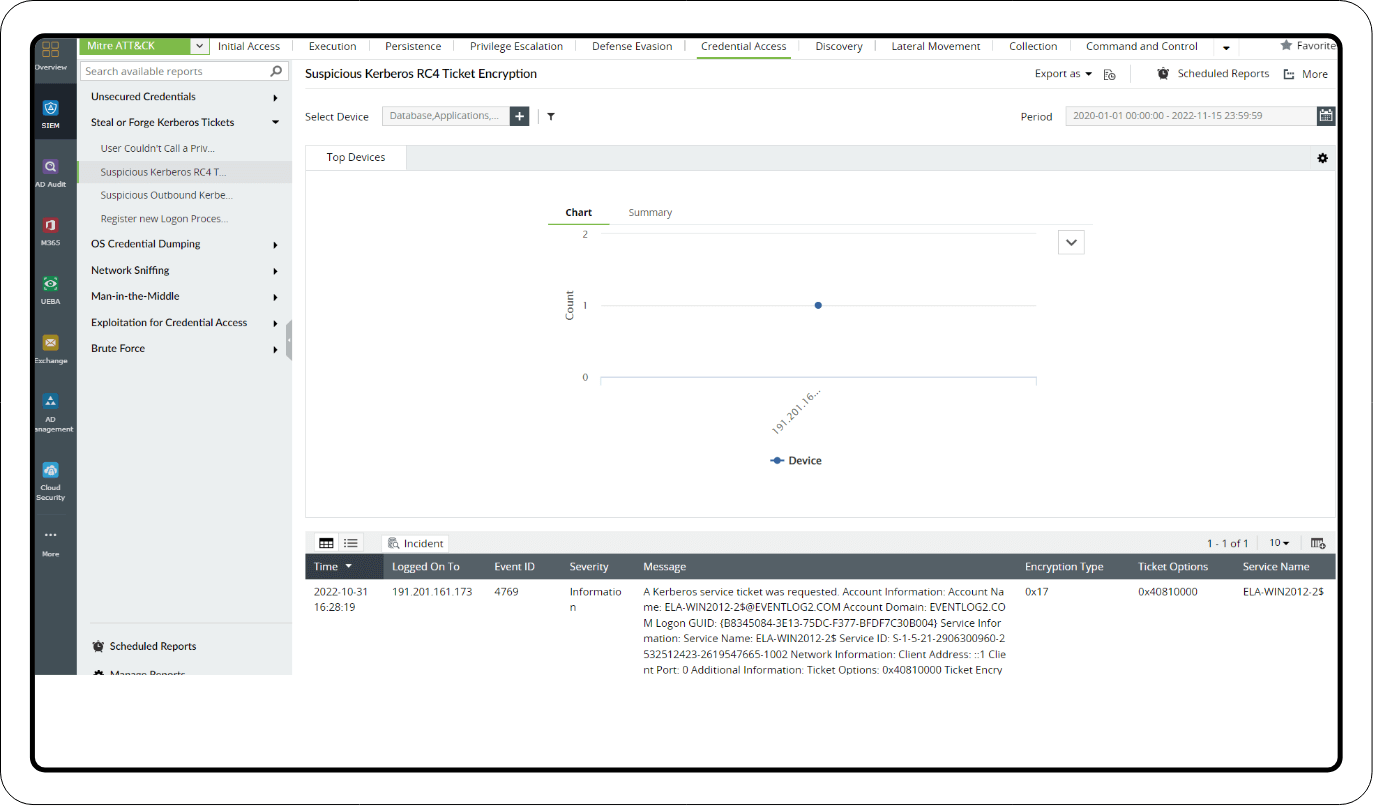
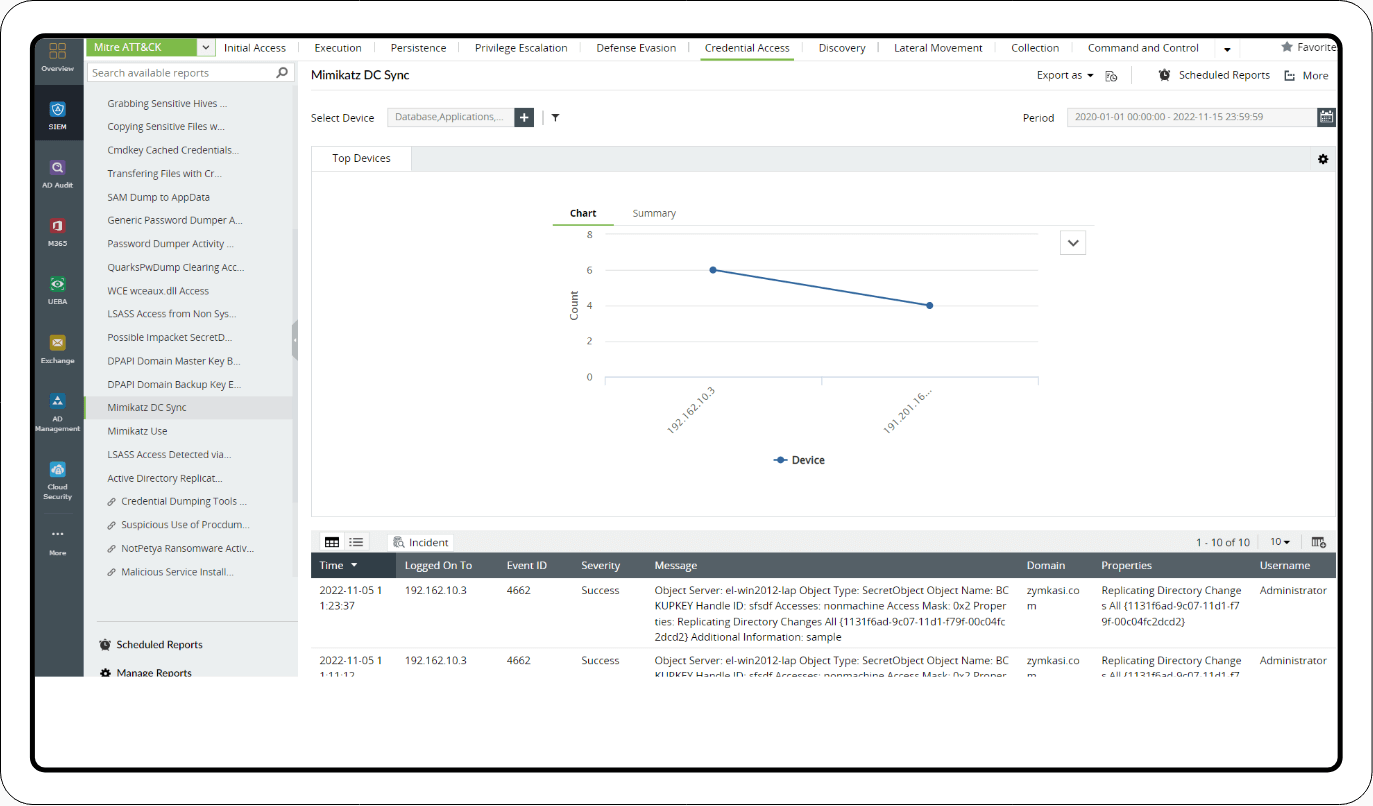
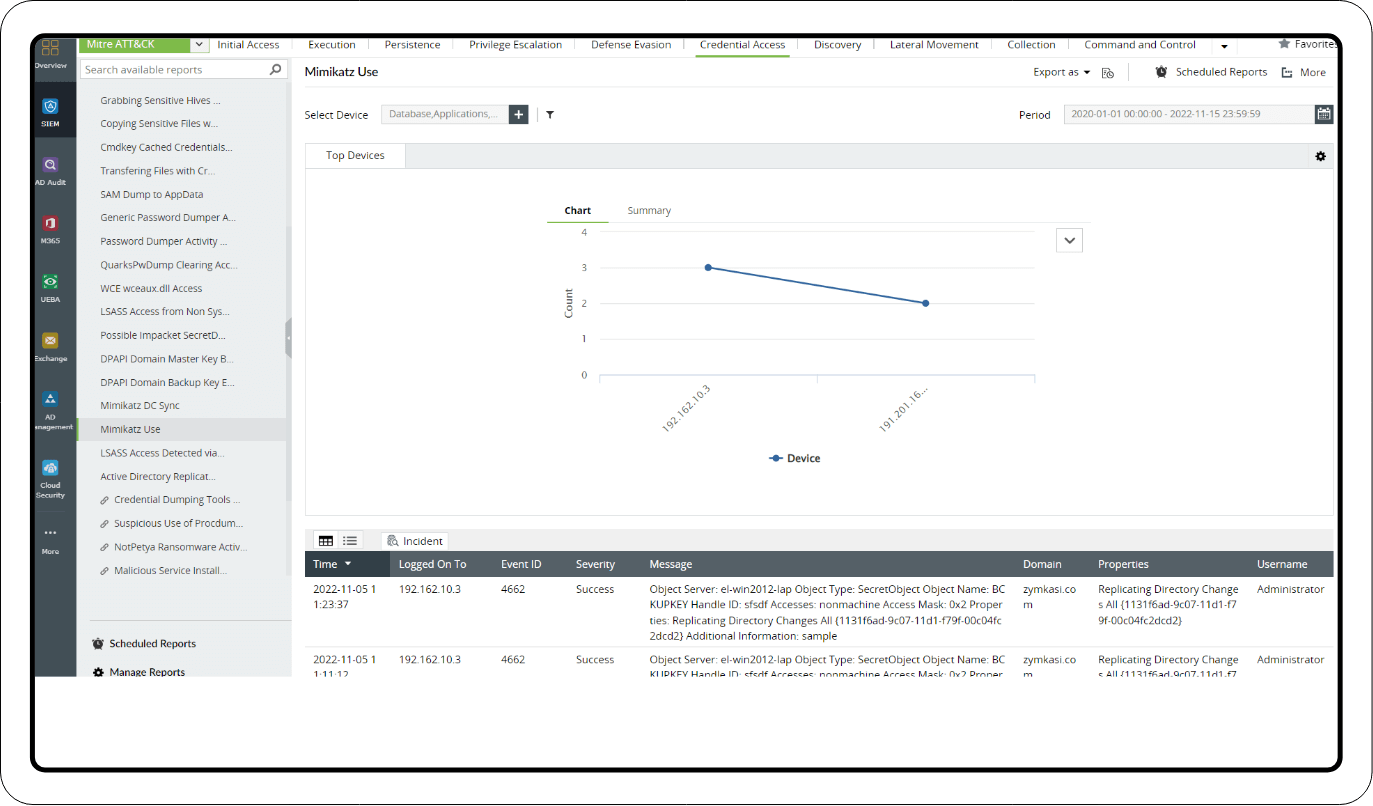
2. Mimikatz reports
The OS Credential Dumping section has the following reports to detect the use of Mimikatz:
- Mimikatz Command Line
- Mimikatz DC Sync
- Mimikatz Use
What's next?
Implement defensive strategies and incident response measures using the advanced security features of Log360.
- What is a Golden Ticket attack?
- About the attack
- Attack flow
- Detection mechanism
- Detecting and mitigating Golden Ticket attacks using Log360