In today's world, data is the most important form of currency that you hold as an organization, and how you manage that data can make or break your business. Efficiently securing data from breaches can become a tricky process in the long run. You need a solution that can manage all your data, safeguard it, and help meet compliance standards.
Log360 helps you achieve all this and more.
Sensitive data discovery
Organizations are required to store large amounts of sensitive data ranging from customer details, employee information, financial data, and more. Often, users store this data in different systems throughout the network. The first step in protecting sensitive data is to identify where it is stored.
Log360 locates sensitive information using preconfigured data discovery policies. It allows you to:
- Locate personally identifiable information (PII) such as email addresses, credit card information, and more.
- Create a custom data discovery policy to detect your organization's sensitive data.
- Define the sensitivity of content and determine the associated risk.
- Automate classification of files containing PII and electronic protected health information (ePHI) to set appropriate security policies for high-risk files.
Log360 makes it easy to automatically detect sensitive data and
Data leak prevention
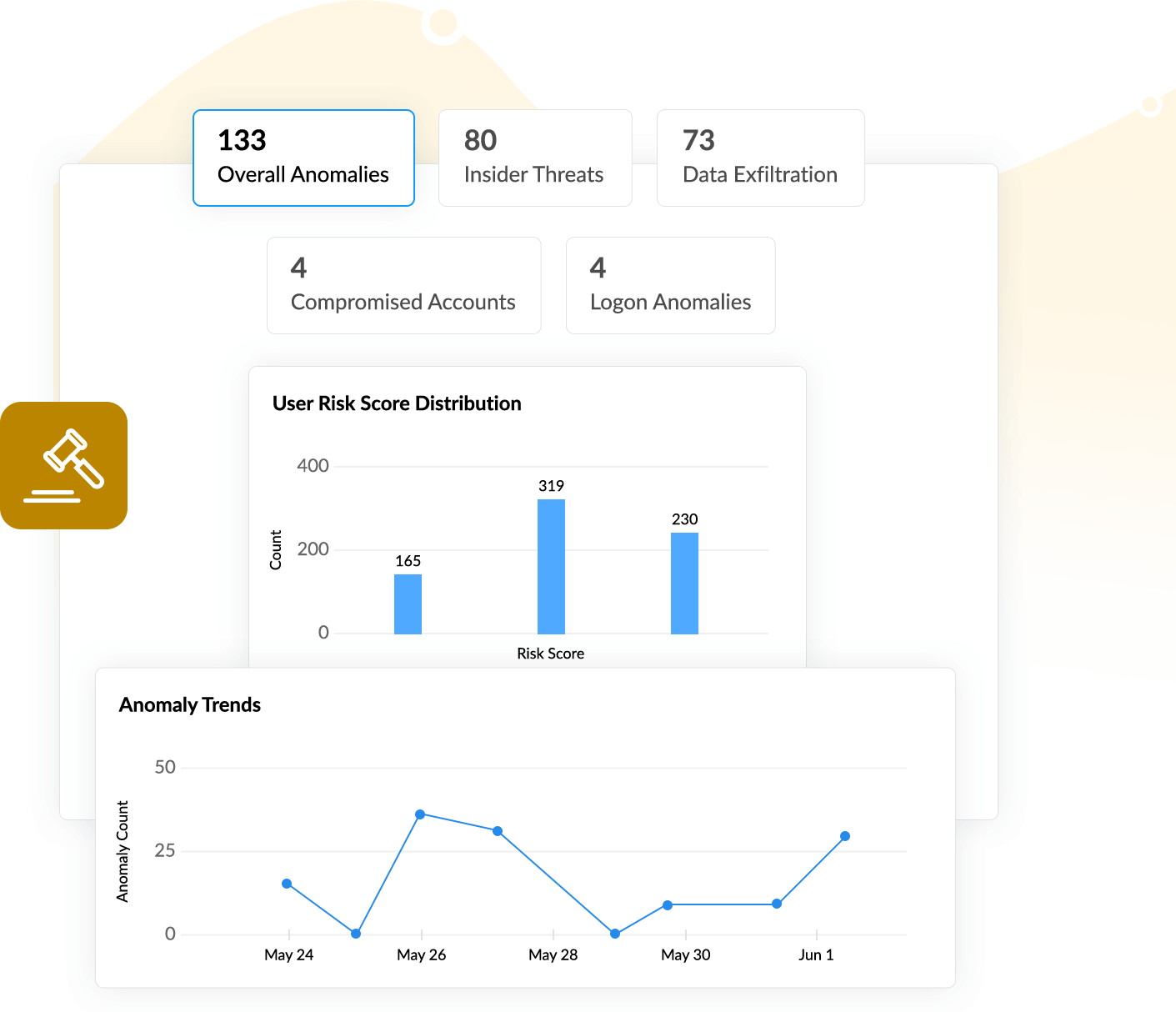
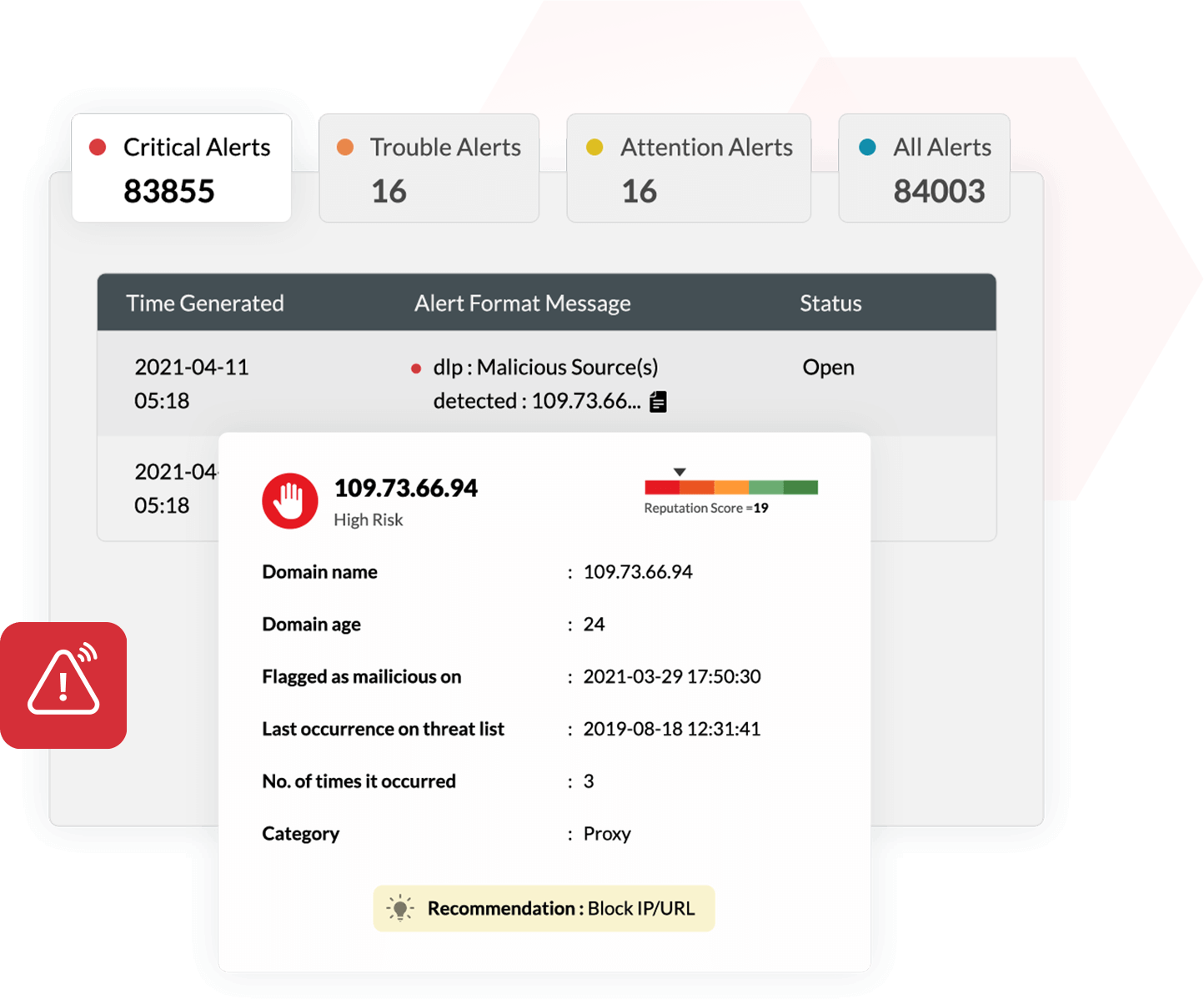
Keeping an eye on security threats that might lead to a data breach will help you prevent damage. Log360 offers capabilities to:
- Spot abnormal user behavior, such as unusual file or data accesses using its machine-learning-based user and entity behavior analytics (UEBA) module.
- Cut down malicious communication to command and control (C&C) servers to stop sensitive files from being extorted.
- Get notified about various data exfiltration techniques including the execution of malicious DNS and tunnelling tools that extort and transmit data to C&C servers.
- Delete and quarantine malicious files that might steal sensitive information such as personal data or credentials.
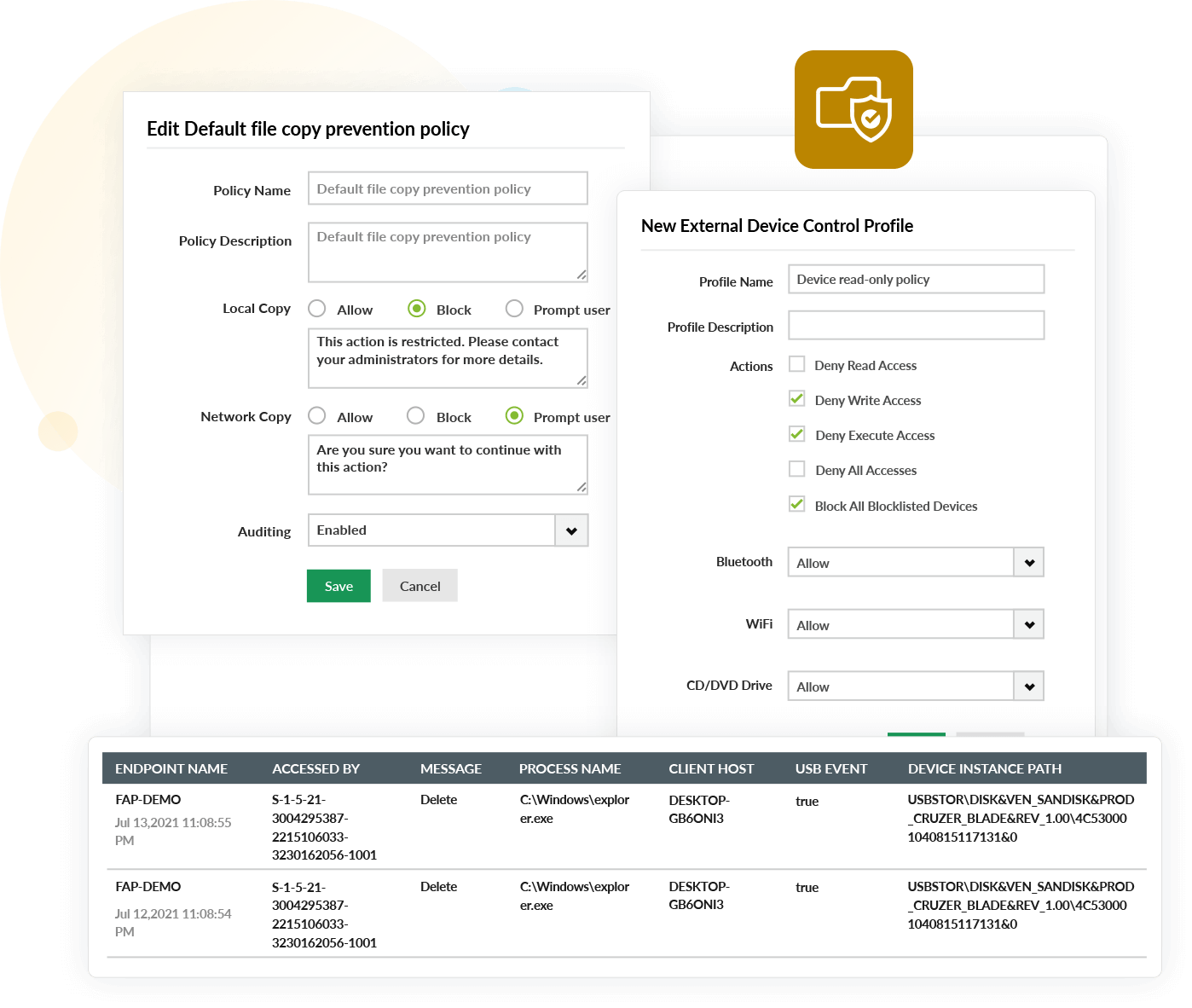
- Block USB ports indefinitely on detecting suspicious behavior and prevent data from being exfiltrated to external devices.
Interested in learning how Log360 protects your enterprise from attacks? Find out more.
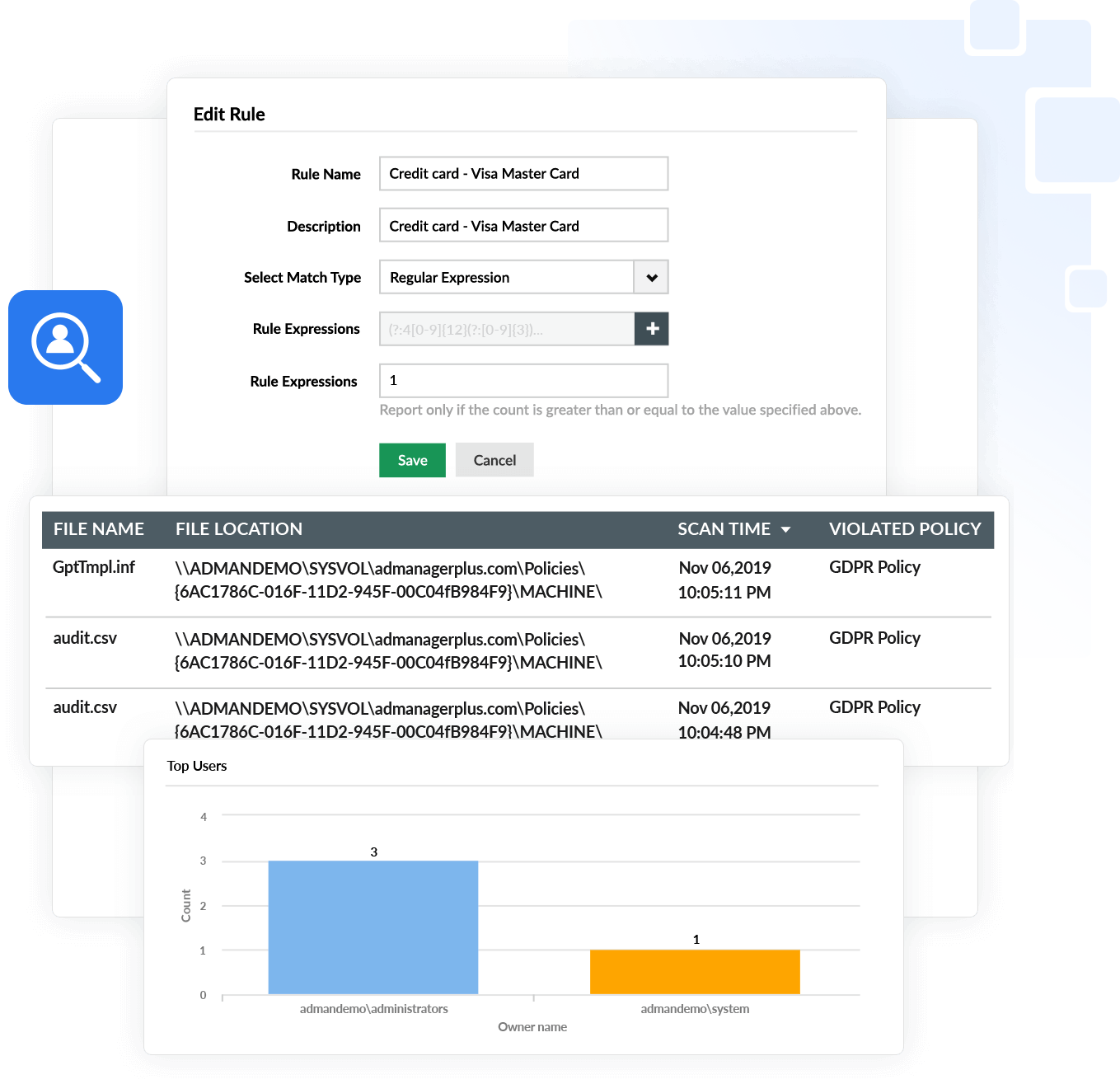
Data risk assessment
Data stored by an organization has varying levels of risk depending on its sensitivity. Using Log360, you can locate sensitive information and classify it based on its sensitivity to help set up necessary protective measures.
- Monitor storage locations and scan for PII.
- Analyze the risk associated with files by inspecting details on the amount and type of personal information contained.
- Automate classification of files containing PII and ePHI to strengthen the security of essential files.
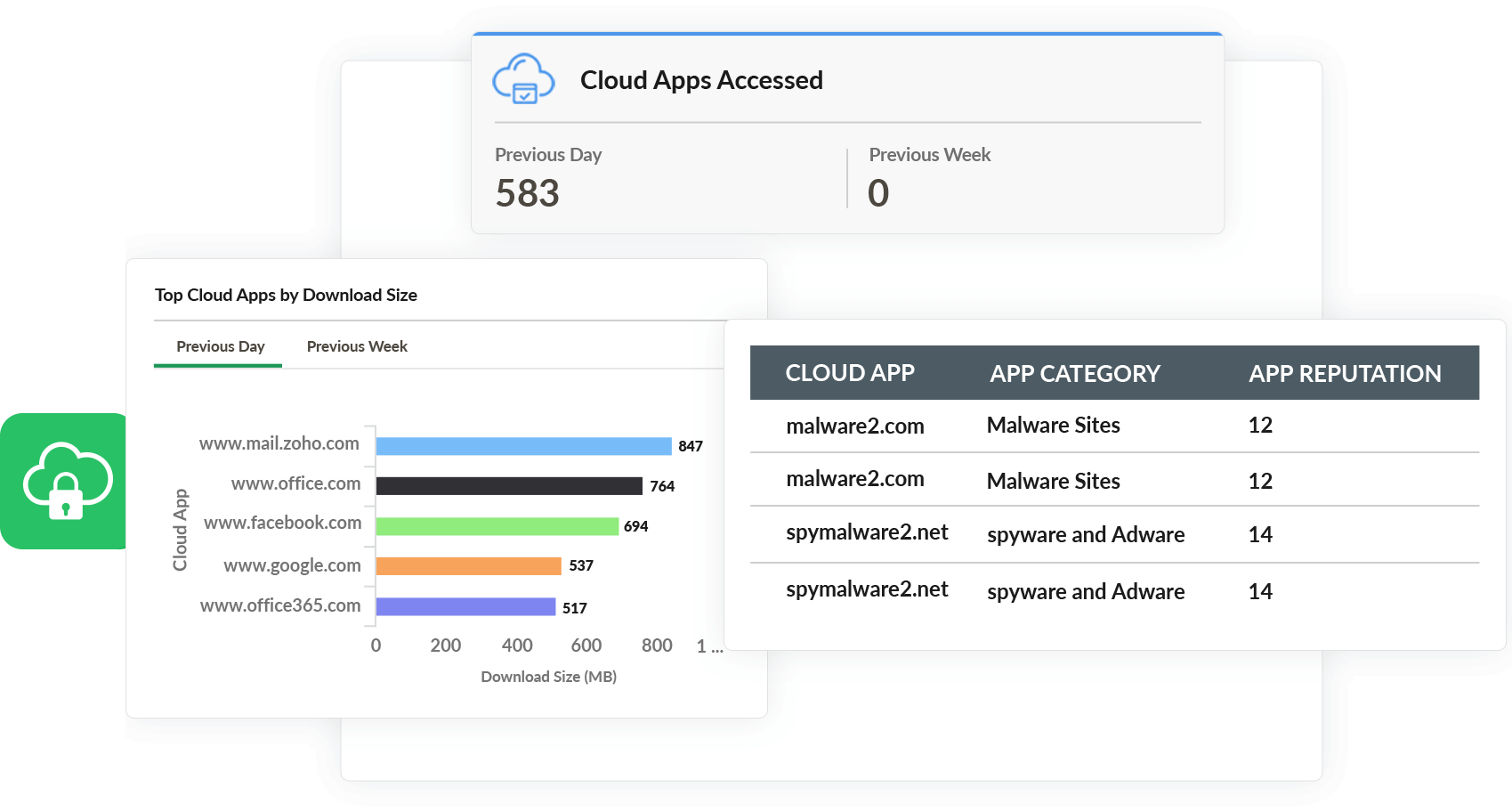
Cloud data security
Ensuring data security on the cloud is even more complex than protecting on-premises data. Continuous monitoring of user accesses, privileged user activities, and changes to security configurations is highly essential to secure data stored on the cloud.
Log360 provides you with:
- Deeper visibility into who accesses what data stored on the cloud.
- The option to restrict web traffic to unsafe, non-business cloud services to prevent data leaks.
- Detailed reports on websites and access requests.
Learn more about Log360's cloud data securing capabilities.
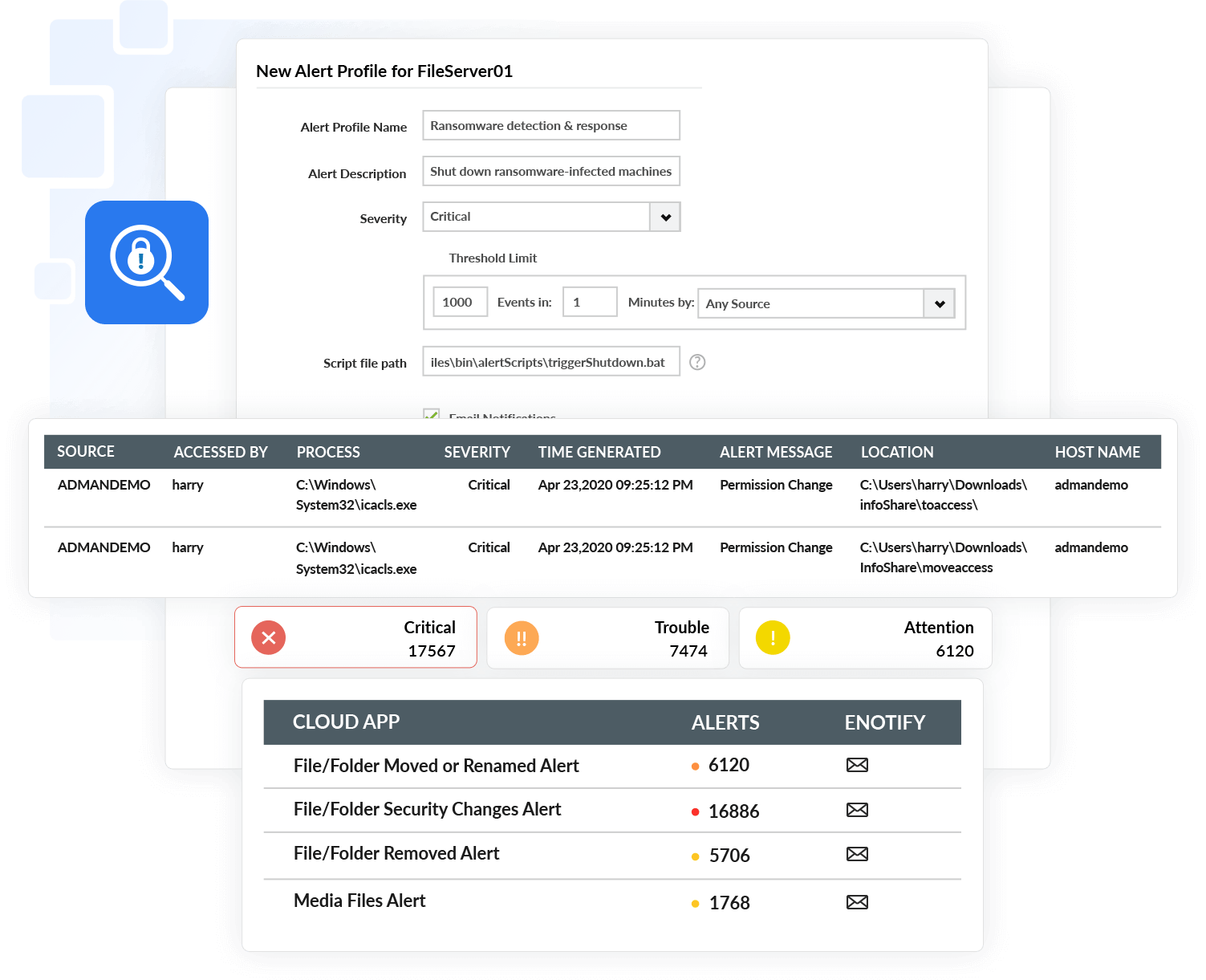
Ransomware detection
Log360 can help you defend against and thwart ransomware attacks by closely monitoring your network for known ransomware attack patterns. You can also configure incident response plans that will automatically get triggered in the event of an attack.
With Log360 you can:
- Gain visibility into user activities and detect anomalous behavior.
- Spot sudden spikes in suspicious file activities such as file renaming, deletion, and permission change events, which are a few of the important indicators of a ransomware attack.
- Immediately act on potential ransomware attempts by isolating the patient-zero machine and preventing the infection from spreading.
Complying with regulatory mandates to secure data
Log360 helps you stay compliant with different regulatory mandates by allowing you to:
- Demonstrate your adherence to compliance mandates using audit-ready compliance report templates.
- Discover and set up security policies for high-risk and sensitive data.
- Spot data exfiltration using the rule-based and behavior-based data breach detection module.
- Generate incident reports within minutes to investigate data breach attempts.
- Get notified in real time about compliance violations.
Thwart off attackers attempting to steal your sensitive data. Try Log360's free, 30-day trial now.