As the attack surface widens, and the attacks become more sophisticated, the weight of the battle against cyberattackers falls on the security operation centers (SOC). SOCs can reinforce an organization's security posture by utilizing a security orchestration, automation and response (SOAR) platform. This collection of compatible security-focused software accelerates incident investigation and response. A SOAR platform increases visibility to all security data, streamlines IT processes, automates security-related manual tasks, reduces redundant and repetitive work, and improves collaboration between security tools.

Gather security data seamlessly from various sources in your network including Active Directory (AD) users, groups, organizational units; network devices such as firewalls, servers, endpoints; and applications such as vulnerability scanners, data loss prevention software, threat applications, and more. Log360 provides meaningful security context to the data to identify security events quickly and accurately.
Ensure accountability for incident resolution by utilizing ticketing tool integration to assign detected incidents to security administrators. Log360 allows configuration of external help desk solutions, such as ServiceNow, ManageEngine ServiceDesk Plus, Jira Service Desk, Zendesk, Kayako, and BMC Remedy Service Desk.
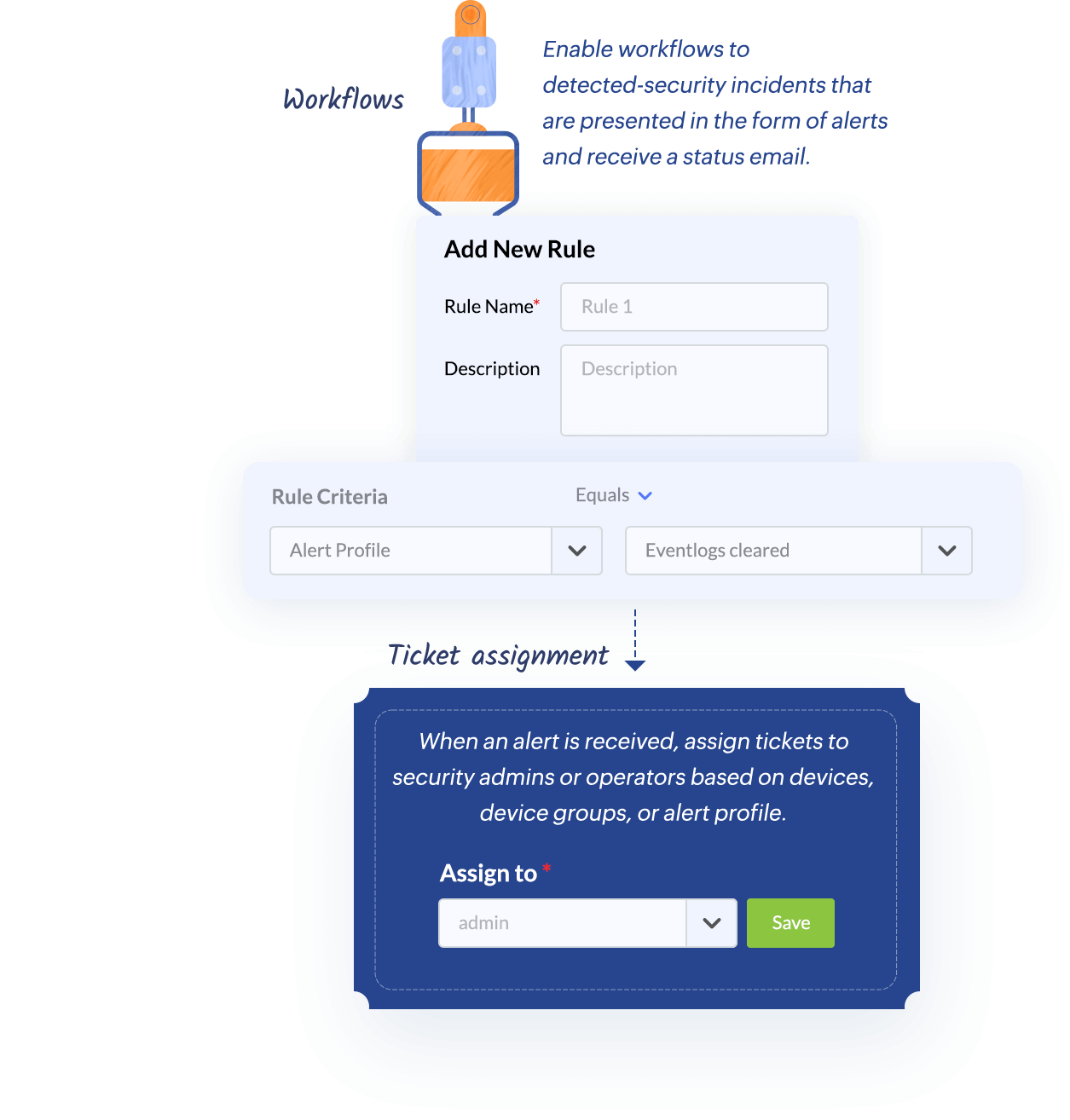
With prebuilt workflows for common use cases, Log360 enables you to automate incident response across your security and IT processes.
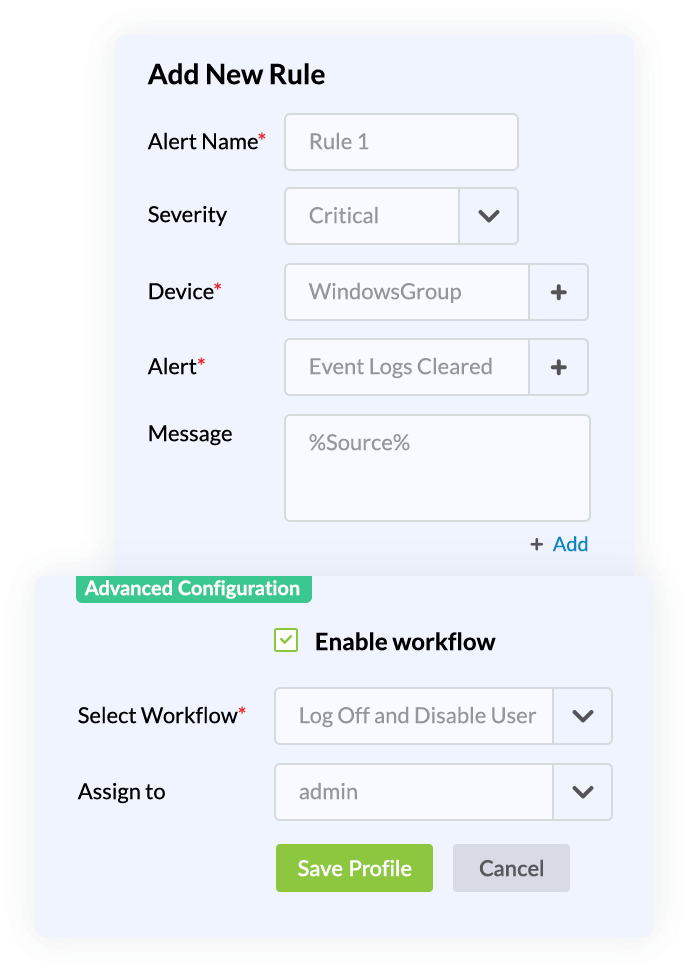
Ensure that no critical security incidents slip through the cracks by automating ticket assignment and workflow execution in Log360. For instance, you can enable a workflow related to event logs that triggers an alert and automatically assigns a ticket to a security admin.
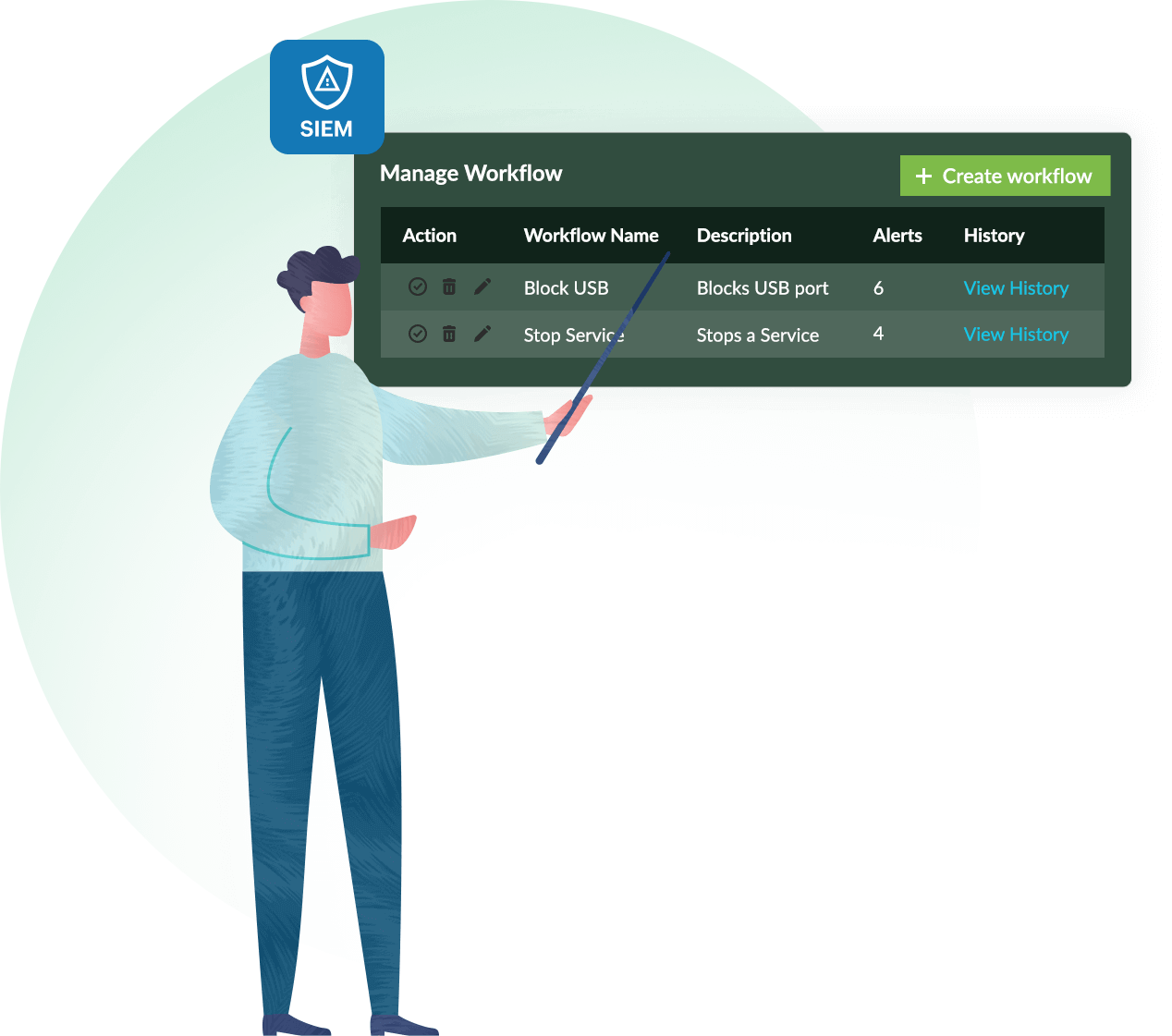
Log360's incident response management reduces the workload for your SOC by automatically executing a series of common remedial measures based on the type of security incident detected in your environment. Automating incident workflows helps contain potential long-lasting security damage to your network, reduces alert response times, and increases SOC efficiency so the team can tackle other challenges.
When alerts are triggered, automate response workflows to mitigate network security incidents before they cause any damage or result in a breach. Log360 provides prebuilt workflow profiles to initiate quick and accurate security responses. You can also associate workflows to alert profiles, correlation alerts, and other security alarms to automate threat remediation.
Automate incident workflows that stop critical security threats from exploiting your organization's assets. With Log360's incident response module, you can:
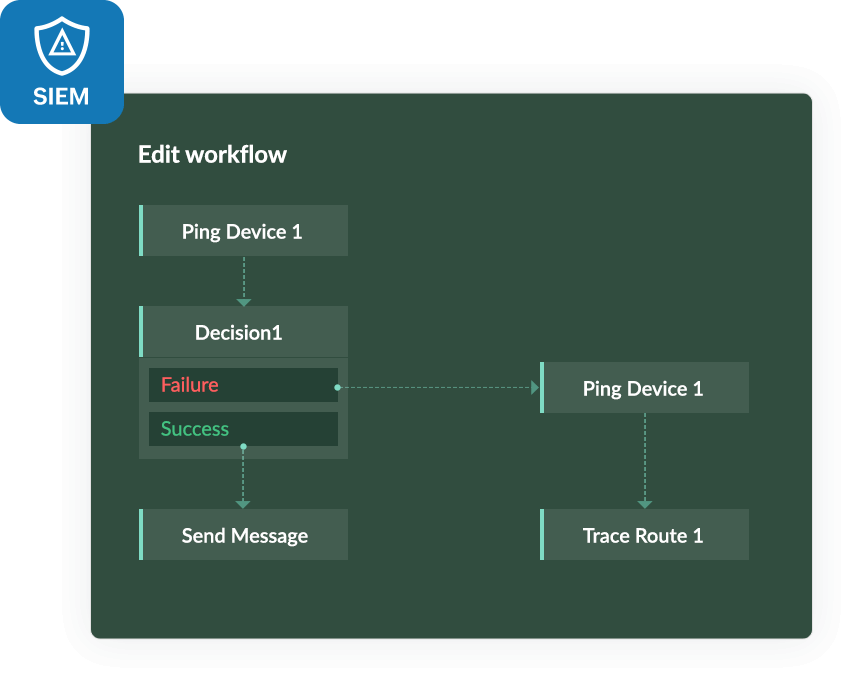
With Log360, you can build incident workflows based on your security requirements using the custom workflow builder. Utilize the simple drag-and-drop interface to link consecutive actions, construct the flow based on the success or failure of the previous action, execute time delays, and more.
Log360 supports seamless workflow integration with different applications and platforms including

Security orchestration automation and response (SOAR) is a comprehensive cybersecurity approach that combines security orchestration, automation, and incident response within a single platform. It enables organization to detect, investigate, and respond to security incidents in a streamlined and automated manner.
The three major components of SOAR are:
SOAR stands for security orchestration, automation, and response. SOAR integrates multiple security tools, including SIEM, to automate repetitive and manual tasks, enabling efficient responses to security threats. It promptly notifies security administrators to take action against threats and streamlines incident response processes, resulting in fast and effective threat detection and mitigation.
SIEM stands for security information and event management. A SIEM solution collects and analyzes log data in real time from various network devices, servers, domain controllers, applications, and more to identify abnormal behavior. SIEM tools provide real-time monitoring, correlation, and analysis of security events, generating alerts when something fishy is happening.