Routines like data backups, cache clearing, and other tasks can easily be managed with task automation tools. Task schedulers, cron jobs, and similar automation utilities help administrators achieve just that. Once these automations are scheduled, an array of administrative tasks are executed without missing a beat.
However, as a security manager, you always need to remember that legitimate automation utilities can also attract threat actors. Attackers can manipulate these utilities into running con scripts on your network. It then becomes imperative that scheduling tools in any environment must be audited.
This blog discusses how all cron job/scheduled task utilities can be manipulated for a threat actor's benefit. You'll also learn how to defend your network against the threats that task automation tools present.
This section discusses common ways that administrative cron jobs can be abused to benefit the attacker's goals.

Use: Most IT administrators are probably using cron jobs and task schedulers to schedule routine backups as part of their data recovery strategy. Along with this, cron jobs are also used to schedule automatic software updates, disk space cleanups, and sometimes even scans for system integrity checkups.
Abuse: Your backup routines can be injected with malicious code through maintenance hooks (shortcuts developers use to enter their development codes without authentication). These maintenance hooks can be abused by attackers to enter into the code and wreck havoc on your environment. Hackers can push plugins with code that can steal data, disrupt system behavior, or launch further attacks through maintenance hooks.
Other malicious cron jobs can also be scheduled along with your legitimate tasks, such as routines that can overwhelm your systems or scripts that allow malware installations.

Use: Network administrators often rely on automation utilities to schedule routine data management activities like data ingestion and data archiving at specific intervals and data synchronization activities across multiple systems.
Abuse: If you aren't properly monitoring your cron jobs and other automation utilities, you may find that malicious tasks have been scheduled on your systems for data exfiltration or to corrupt the data on your systems. This is easy to accomplish by an attacker, as cron job scripts are fairly easy to craft. Threat actors may set the cron job to run during non-business hours, when there's less chance of someone noticing the data transfer, modifications, or replacement of files.

Use: Cron jobs can be used to schedule automatic updates to website content (example: automatic updates to the date and time on a subscription page) or to schedule the publication of content at specific times. Other ways cron jobs can assist administrators is by clearing out cache and sending automated emails and notifications.
Abuse: Yet again, hackers can find a way to spoil things when it comes to web applications. Imagine how bad it would be for your brand if your home page or feature page said something unsavory. Attackers can abuse cron jobs to deface your web content, and can go a step further and schedule cron jobs to steal user session cookies or gain unauthorized access to accounts. As a security manager, you need to use the right tools to get insight into whether attackers have scheduled tasks that inject malicious code into websites.
Also, keep in mind that cryptojacking attacks have been conducted through the use of cron jobs to execute malicious scripts that utilize the victim's system processing power to mine cryptocurrency for the attacker.
ManageEngine's Log360 is a powerful SIEM solution that offers security teams enhanced log management, detection, and incident response. With Log360 a security manager can leverage different capabilities, like AD management and auditing, DLP, CASB and UEBA available on a single platform to secure different aspects of their network. Log360 offers security practitioners extensive reporting styles that offer in-depth insights on every nook and cranny of an organization's network for possible threat occurrences.
In this specific case of cron job or scheduled task monitoring, several prebuilt analytics in Log360 will help you track automated tasks in your network.
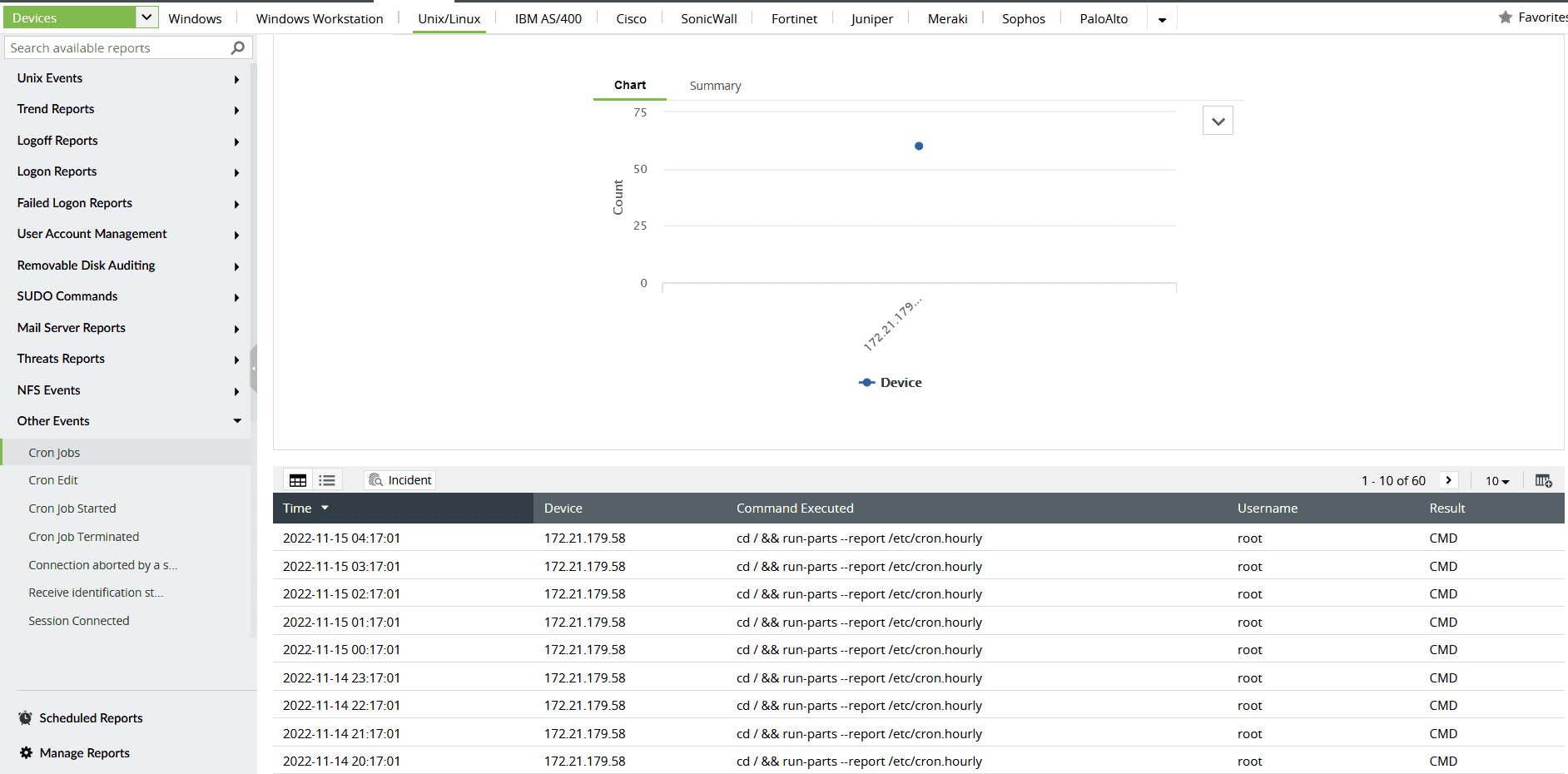 Figure 1: Log360 has a category of reports on cron job creations, modifications, and deletions.
Figure 1: Log360 has a category of reports on cron job creations, modifications, and deletions.
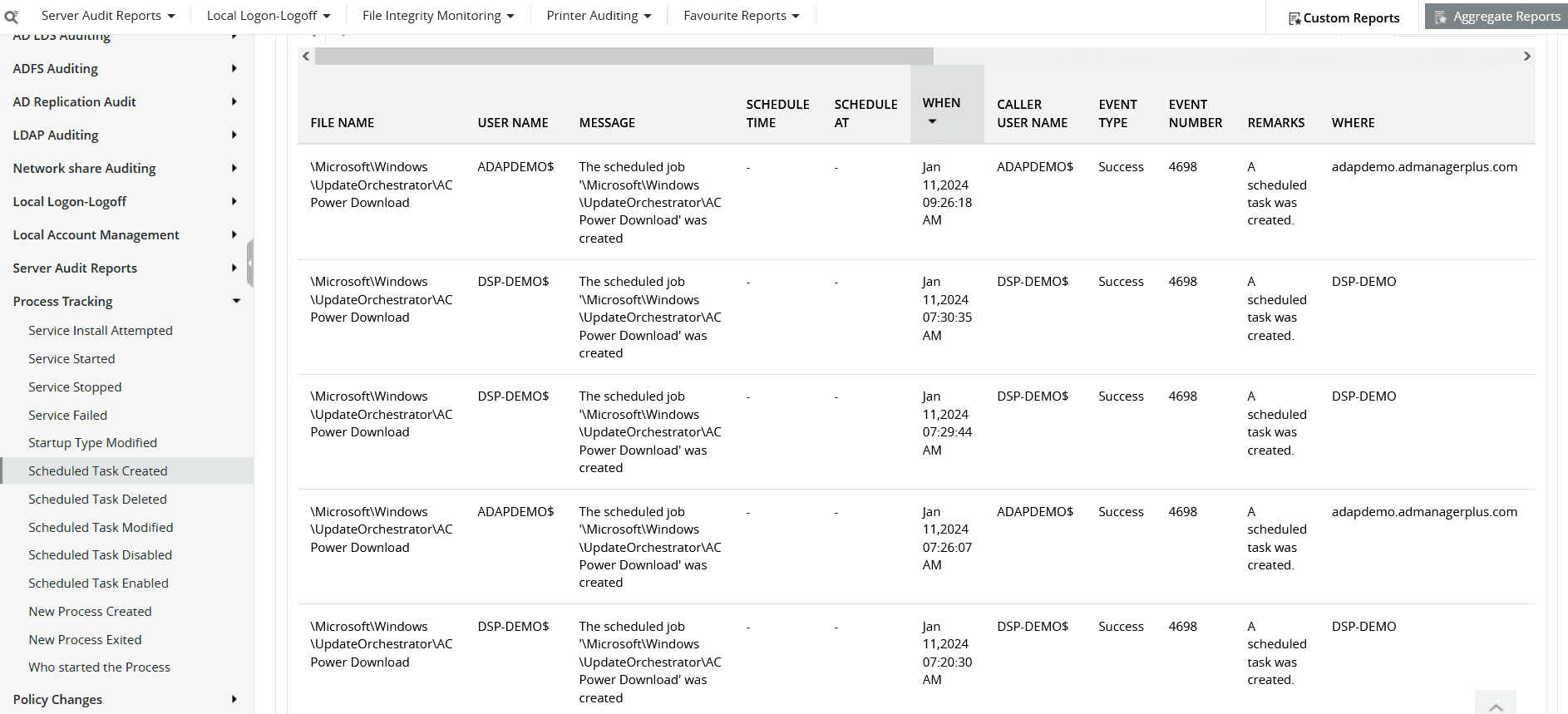 Figure 2a: Log360 also gives you a category of reports on task creations, deletions, and modifications on Windows Task Scheduler.
Figure 2a: Log360 also gives you a category of reports on task creations, deletions, and modifications on Windows Task Scheduler.
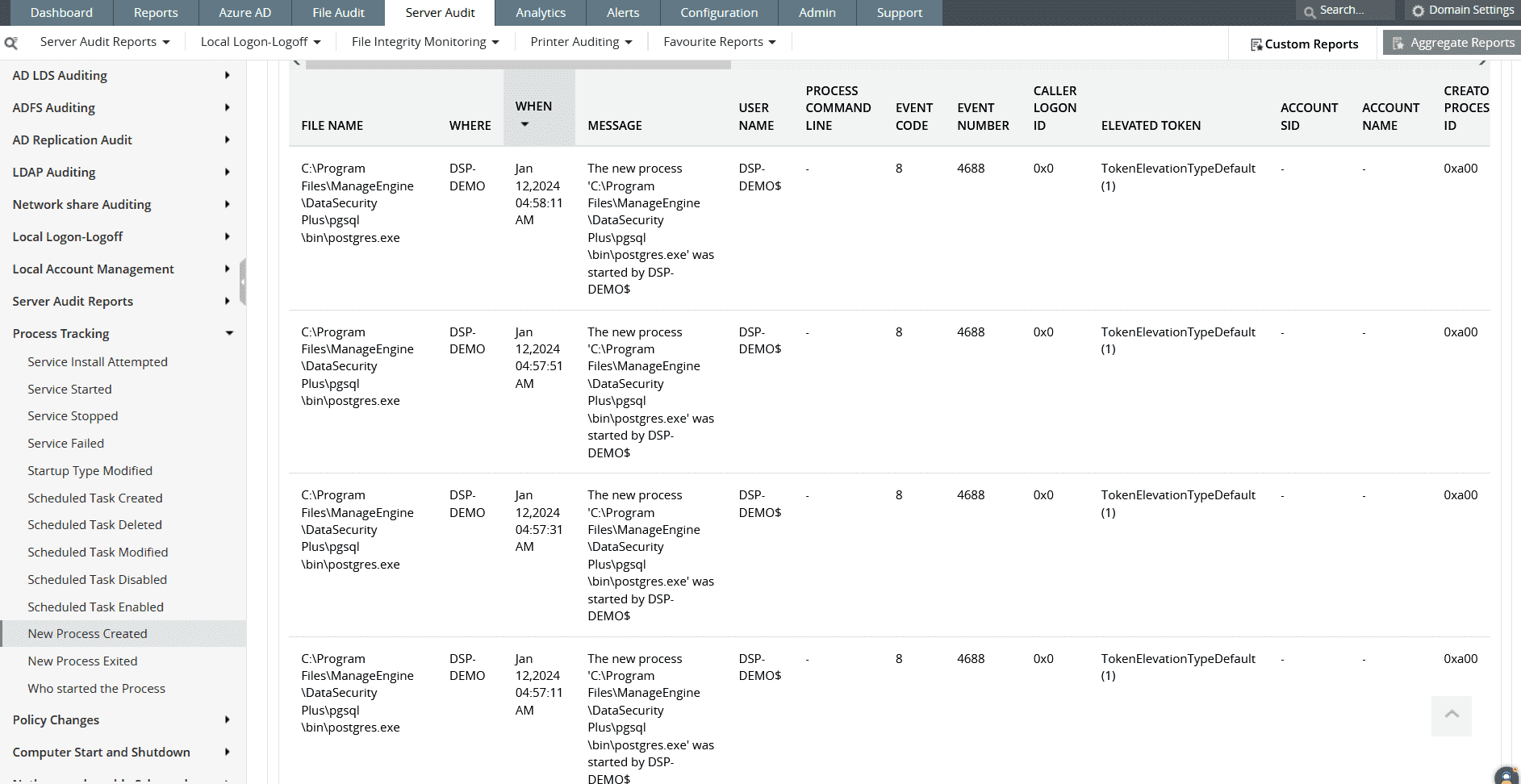 Figure 2b: You can also track process creations and deletions and the users associated with these events in Log360.
Figure 2b: You can also track process creations and deletions and the users associated with these events in Log360.
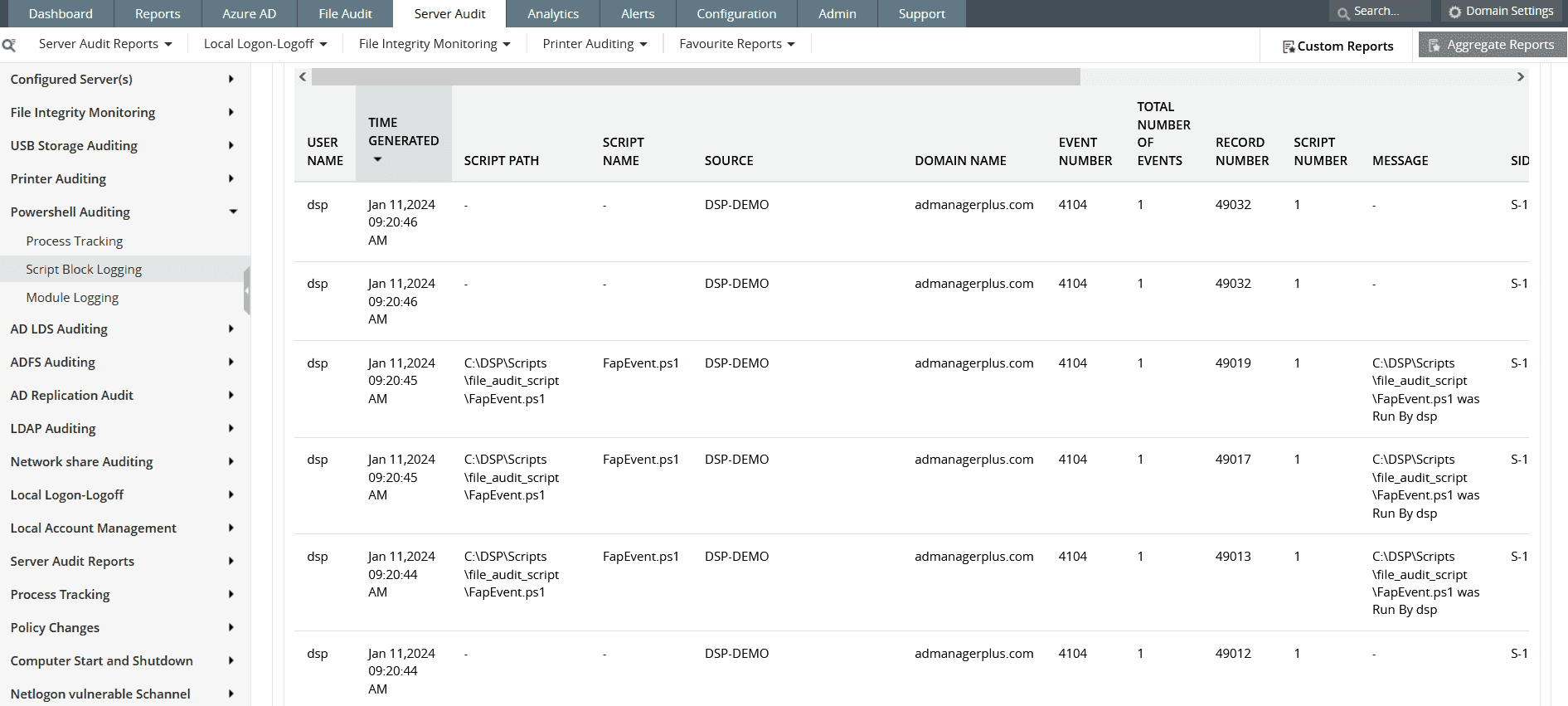 Figure 3: With Log360 you can also audit Powershell to see if any suspicious commands are being executed.
Figure 3: With Log360 you can also audit Powershell to see if any suspicious commands are being executed.
 Figure 4: Log360 helps you audit all changes to your files through the File Audit category of reports.
Figure 4: Log360 helps you audit all changes to your files through the File Audit category of reports.
Interested in these features of Log360? Then sign up for a personalized demo to learn about all the different SIEM capabilities Log360 can offer your security team.
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.