What is privilege escalation attack?
Privilege escalation is the act of evading established access and authorization controls in an enterprise network to gain elevated privileges and access critical network assets. It is the intermediate phase in the cyber kill chain and one of the 14 major attack tactics in the MITRE ATT&CK framework. A threat actor with escalated privileges can exploit that to steal data, tamper with security settings, and persist on the network to launch multiple attacks. According to IBM's Cost of a Data Breach Report 2024, malicious insider attacks, which often involve privilege escalation, cost organizations an average of $4.88 million per incident.

Privilege escalation types
Privilege escalation can be classified into two categories:
- Vertical privilege escalation: Vertical privilege escalation occurs when an attacker elevates their access rights, transitioning from a regular user account to one with higher privileges, such as an administrator or root account. For example, an attacker might exploit an unpatched kernel vulnerability in a Linux server to execute arbitrary code and gain root-level access. Common techniques used in this type of attack include exploiting unpatched vulnerabilities, abusing misconfigured services, and bypassing access controls.
- Horizontal privilege escalation: Horizontal privilege escalation occurs When attackers gain access to accounts with the same privilege level by impersonating another user or using stolen credentials. A typical example would be using stolen session cookies to impersonate another user's account in a web application. Common techniques for horizontal privilege escalation include credential theft, session hijacking, and exploiting weak password policies.
Understanding privileges in an enterprise network
Enterprise networks are composed of various internal resources such as file servers, print servers, business applications hosted in data centers, and services running on individual systems. To access these resources, users must log in using their account credentials. These user accounts serve as unique identifiers on the network and come with predefined privileges.
Privileges in this context are determined by two primary factors:
- Entities a user can access: The specific resources or systems users are allowed to interact with.
- Actions a user can perform: The operations they are permitted to execute, such as viewing, editing, creating, sharing, or executing files and applications.
Let's delve into how these privileges are assigned and managed at the account level. User accounts in enterprise environments typically fall into two main categories: local account privileges and domain-level privileges, each with distinct characteristics and implications for security.
1. Local account privileges
Local accounts are user accounts created on and restricted to individual systems. These accounts are stored locally and managed differently across operating systems like Windows and Linux. While they can perform tasks such as browsing the web, accessing local files, and using some network resources, their functionality is limited to the host system. However, these accounts can sometimes be elevated to gain administrative or root-level access, though they cannot be used on other systems.
2. Domain-level privileges
In enterprise environments, directory services like Active Directory (AD) are used to centralize the management of users and resources. AD structures these entities into groups called domains. Users with domain-level privileges can log in to multiple systems within the domain and access shared resources. Additionally, special trust relationships will be established to allow access to resources on other domains. Role-based access controls (RBAC) are often implemented to further restrict and manage privileges within a domain.
Now that privileges on a network are defined, let's understand how privilege escalation works.
How does a privilege escalation attack work?
Privilege escalation occurs when attackers exploit weaknesses to gain unauthorized access or elevated permissions. The typical stages include:
- Initial access: Attackers breach the system through phishing, exploiting vulnerabilities, or leveraging weak credentials.
- Reconnaissance: They analyze system configurations, roles, and processes to identify escalation opportunities.
- Privilege escalation: Exploit vulnerabilities or misconfigurations to elevate privileges.
- Exploitation: Use escalated privileges to steal data, sabotage systems, or propagate further attacks.
Want to know how Log360, a SIEM solution, can protect your organization from privilege escalation attacks?
Privilege escalation techniques
Attackers use various methods to escalate privileges, which can be categorized into two: system-level and domain-level techniques.
System-level privilege escalation techniques
UAC bypass (Windows)
In Windows systems, the services, processes, or applications are launched with low privileges by default. When users want to run any application or process with admin privileges, the User Account Control (UAC) on Windows systems will prompt them for confirmation. Malicious actors with reverse shell access will bypass UAC by hijacking processes that can auto-elevate and run without prompting the users. They create new child processes with inherited privileges or inject arbitrary code into the files of those services.This technique is categorized under the MITRE ATT&CK ID T1548.002. Detection involves monitoring Event IDs such as 4688 (New process creation) and 7045 (New service installed). ManageEngine Log360 maps and correlates these Event IDs, providing real-time alerts to detect UAC bypass attempts effectively.
Kernel exploits
Kernel exploits are done to gain root access on a system and make OS-level changes. Using reverse shell access, an attacker can obtain details such as the kernel version of the system, processes running on the system and the privileges they have, users and their privileges, cached data, and more.There are detailed enumeration cheat sheets with commands for different OSs. Just with the simple detail of the kernel version, the threat actors can find active vulnerabilities for that version available openly on the internet. Or, they can proceed to perform a vulnerability scan and deploy a suitable exploit using tools like SearchSploit and Linux-Exploit-Suggester. This technique corresponds to MITRE ATT&CK ID T1068. Key detection methods include monitoring kernel logs, auditing unauthorized privilege escalation attempts, and using tools like Sysmon. Log360 helps analyze kernel-level logs and detects malicious activity for timely response.
Boot logon autostart exploit (Windows)
Windows allows certain applications to auto-start post logon. These can be web browsers or security programs like Microsoft Defender and antivirus software. The Startup folder stores the shortcuts to all these apps and launches them with the privileges of the users who log on. If the threat actors gain write permissions to this folder, they can add malicious applications, then when administrators log on to this system, these malicious apps will be launched with elevated privileges. This attack aligns with MITRE ATT&CK ID T1547.001. Detection methods include monitoring Event IDs such as 7040 (Startup configuration change) and 4688 (Processes launched from startup). ManageEngine Log360 tracks these changes and alerts on unauthorized modifications to prevent privilege escalation.
Domain-level privilege escalation techniques
Tampering domain group policies through DC replication
Attackers can launch a rogue domain controller (DC) through SID history injection, which can be used to add users, change permissions, and modify critical policies. Any changes made by a DC will be replicated in all other DCs in the domain and the replication stream activities are not logged. This helps threat actors to quickly gain elevated domain privileges, make permanent changes which will be applied on the actual DCs, and eventually disappear without detection by unregistering the rogue DC. Tools like Mimikatz can be used for this attack.
Protocol vulnerabilities with Kerberoasting
The Kerberos authentication protocol issues ticket granting tickets (TGTs) to access the domain services. These tickets are generated by DCs and can be used to authenticate users without requiring credentials every time. Attackers can forge these tickets by adding the SID, username, and group ID of privileged accounts, then increasing the lifetime of the ticket to be valid for years. This gives a free pass to access all the critical domain services.
Exploiting certificate misconfigurations
Active Directory Certificate Services (AD CS) issues certificates to authenticate users, devices, and services, and to secure communication through public key encryption. Attackers leverage enumeration techniques to get details of the certificate templates with weak settings and configurations or with elevated permissions to generate new certificates with those templates.
Linux privilege escalation
Linux systems are common targets for privilege escalation due to their widespread use in enterprise environments. Attackers often exploit misconfigured file permissions, kernel vulnerabilities, or SUID binaries to gain unauthorized root access. For instance, exploiting a vulnerable kernel module can provide attackers with the ability to execute privileged commands, while improperly configured SUID files may allow unauthorized actions.
- Enumeration is an initial step where attackers gather system information such as installed software, user accounts, and configurations to identify vulnerabilities. Tools like LinPEAS or manual techniques help attackers in locating weaknesses for privilege escalation.
- Kernel exploits take advantage of vulnerabilities in the Linux kernel, enabling attackers to escalate privileges and potentially gain root access. Attackers often use tools like SearchSploit or Linux-Exploit-Suggester to identify kernel-level vulnerabilities and deploy appropriate exploits.
- SUDO exploitation involves abusing misconfigured SUDO rights or exploiting vulnerabilities in the SUDO command to run commands with superuser privileges. Such attacks are particularly effective when sensitive tasks are improperly restricted.
Windows privilege escalation
Windows privilege escalation typically involves bypassing built-in security measures or exploiting weak configurations. Attackers often bypass UAC, manipulate Active Directory settings, or use cached credentials to achieve elevated privileges. These attacks are particularly dangerous in enterprise environments where AD plays a critical role in managing permissions.
UAC bypass is a common tactic where attackers hijack processes that auto-elevate or inject malicious code into trusted services to execute commands with administrative rights, bypassing user account control prompts.
MITRE ATT&CK framework association: Privilege escalation techniques are mapped to the MITRE ATT&CK framework, which provides insights into adversary tactics, techniques, and procedures (TTPs). Key associations include:
- T1003 Credential dumping (6): Extract credentials or password hashes from the memory or storage of compromised devices.
- T1548 Abuse elevation control mechanism (3): Exploiting operating system mechanisms like bypassing User Account Control (UAC).
- T1134 Access token manipulation (1): Modifying tokens to impersonate privileged users.
- T1078 Valid accounts (2): Leveraging stolen credentials to authenticate as legitimate users.
- T1550 Pass the ticket (3): Using stolen Kerberos tickets to authenticate and escalate access.
Access token manipulation allows attackers to impersonate privileged accounts by modifying or hijacking access tokens, enabling unauthorized access to critical resources.
How to detect privilege escalation attacks
Privilege escalation detection requires proactive monitoring and hunting for indicators of compromise like:
- Unusual logon activities, as well as files and applications accessed by accounts with low privileges for the first time.
- Indicators of access token manipulation, process injection attacks, and SID history injection.
- Launch of DC sync and DC Shadow attacks, as well as the presence of forged Kerberos tickets.
- Unauthorized changes made to services that run with administrator privileges.
- Detecting the use of command line tools like Mimikatz and SearchSploit.
- System events like sudden application crashes, system shutdowns, and malfunctioning caused by the presence of malware and threat actors tampering with the OS and Kernel.
Detect privilege escalation attacks effortlessly with Log360's predefined correlation rules that spot abnormal logons, file permission changes, and DC sync attempts in real time.
Best practices to prevent privilege escalation
Privilege escalation activities and techniques are vast and can't be put down in a finite list to track and monitor. The UAC bypass technique alone has 60+ known methods for implementation, including exploits for open vulnerabilities on Windows OS with no patches released so far. The best bet for organizations is to implement strict access control policies, follow the best practices religiously, and never let a threat actor proceed until privilege escalation. Here are some of the best practices to be followed and the detection mechanisms to use in case privileges get escalated.
- Implement access control policies like role-based access control (RBAC), mandatory access control (MAC), and discretionary access control (DAC).
- Enforce multi-factor authentication (MFA) and strong password policies.
- Enable log collection on your devices, retain your logs, and deploy tools used for SIEM and UEBA to continuously monitor and correlate activities.
- Conduct penetration testing periodically to be aware of the vulnerabilities on your network.
- Keep your OS environment and applications updated with the latest patches. Have a system to automate patch management.
How Log360 helps detect and prevent privilege escalation attacks
Detection through correlation
Log360 offers around 40 predefined correlation rules that are precisely created to match attack patterns and avoid raising false alerts. The following rules can be used to detect possible privilege escalation attempts:
- Suspicious file access: This rule tracks modification of a file after multiple attempts to access it.
- Multiple file permission changes: This rule is matched when a user modifies permissions of multiple files within a short span of time. Event ID 4670 is used to track this.
- Possible worm activity: This rule tracks the installation of malicious services on multiple devices in a short span of time. Event IDs 601 and 4697 are used.
- Suspicious service installed: This rule is matched when a user logs onto a system after multiple failed attempts and then installs and runs a service.
- Repeated failed SUDO commands: This rule is matched when a user attempts and fails to run SUDO commands (which offer admin privileges).
Remediation: Once the correlation alerts are triggered, you can respond to them immediately by executing workflows to kill the process, disable the user, and shutdown the system.
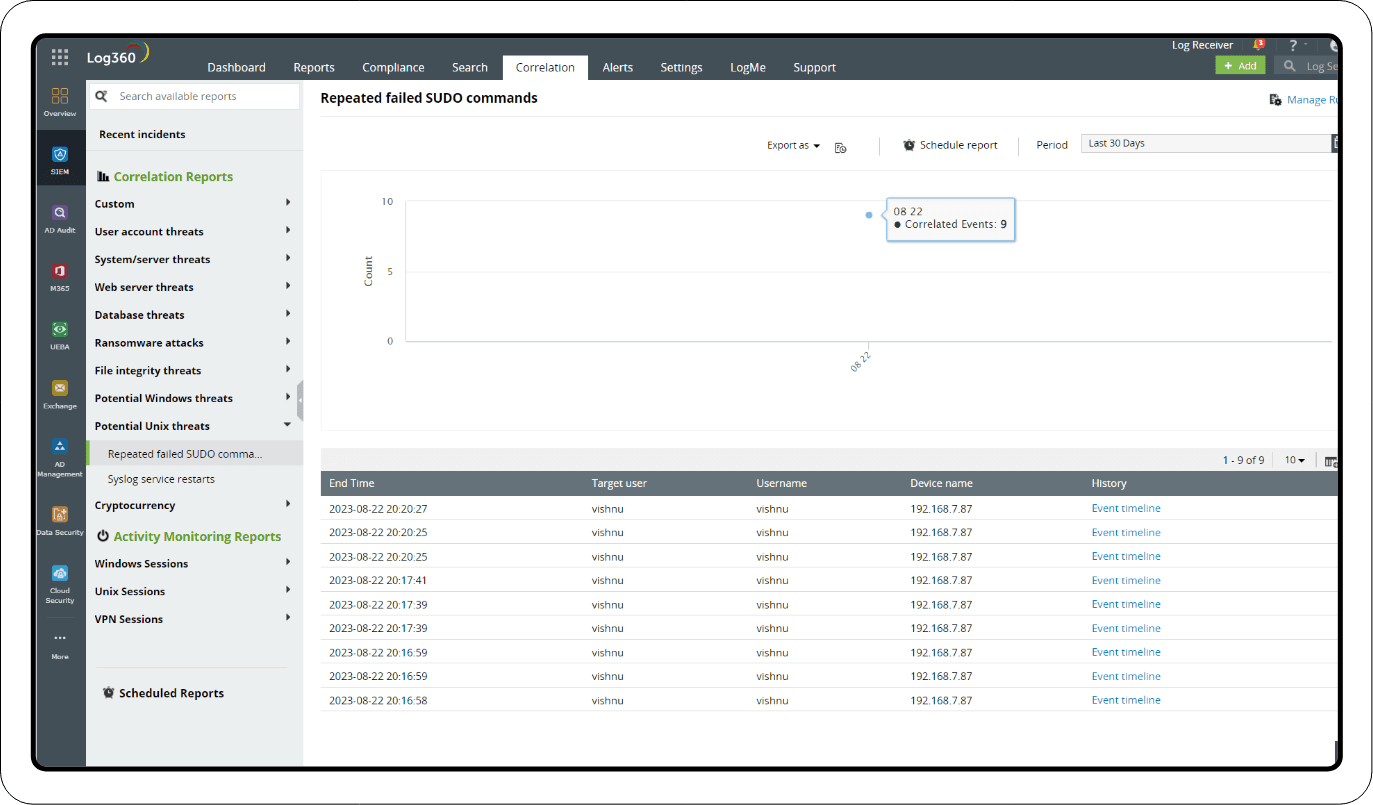
Investigation through reports
MITRE ATT&CK dashboard
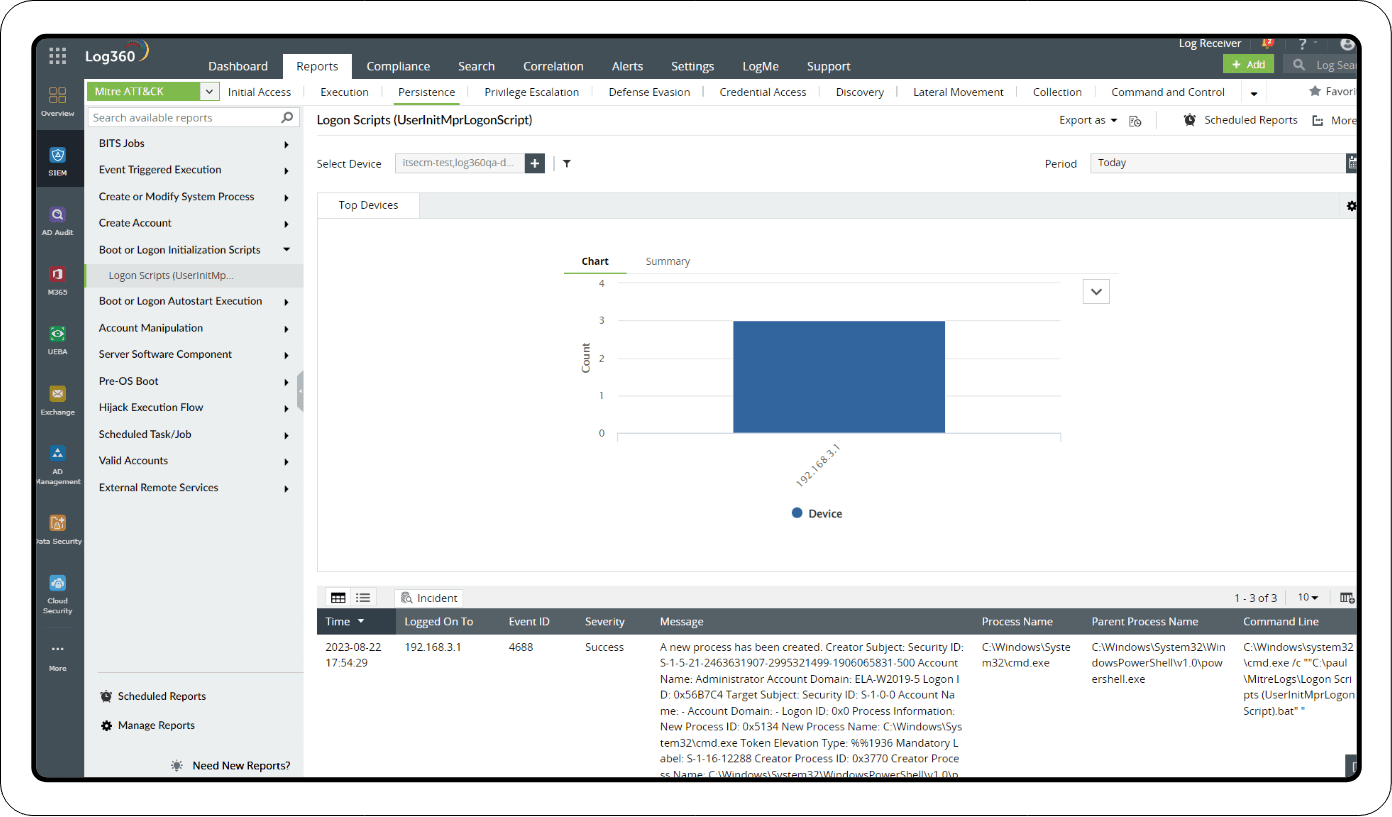
Log360 has an integrated MITRE ATT&CK dashboard that contains exhaustive reports for all major privilege escalation techniques, including the following:
- Abuse elevation control mechanism: These reports track UAC bypass attacks and the different ways they can be achieved using multiple tools.
- Access token manipulation: These reports track SID history injection and the use of tools like Meterpreter and Cobalt Strike.
- Boot or logon autostart execution: These reports detect direct autorun keys modification by tracking the Event ID 4688.
- Credential access: These reports detect forged Kerberos tickets by tracking the result codes of TGT failure Event ID 4769.
Apart from the MITRE ATT&CK reports, Log360 has reports for Windows and Linux systems that track user logon activities, domain events, system events, application crashes, threat reports, and device severity reports.
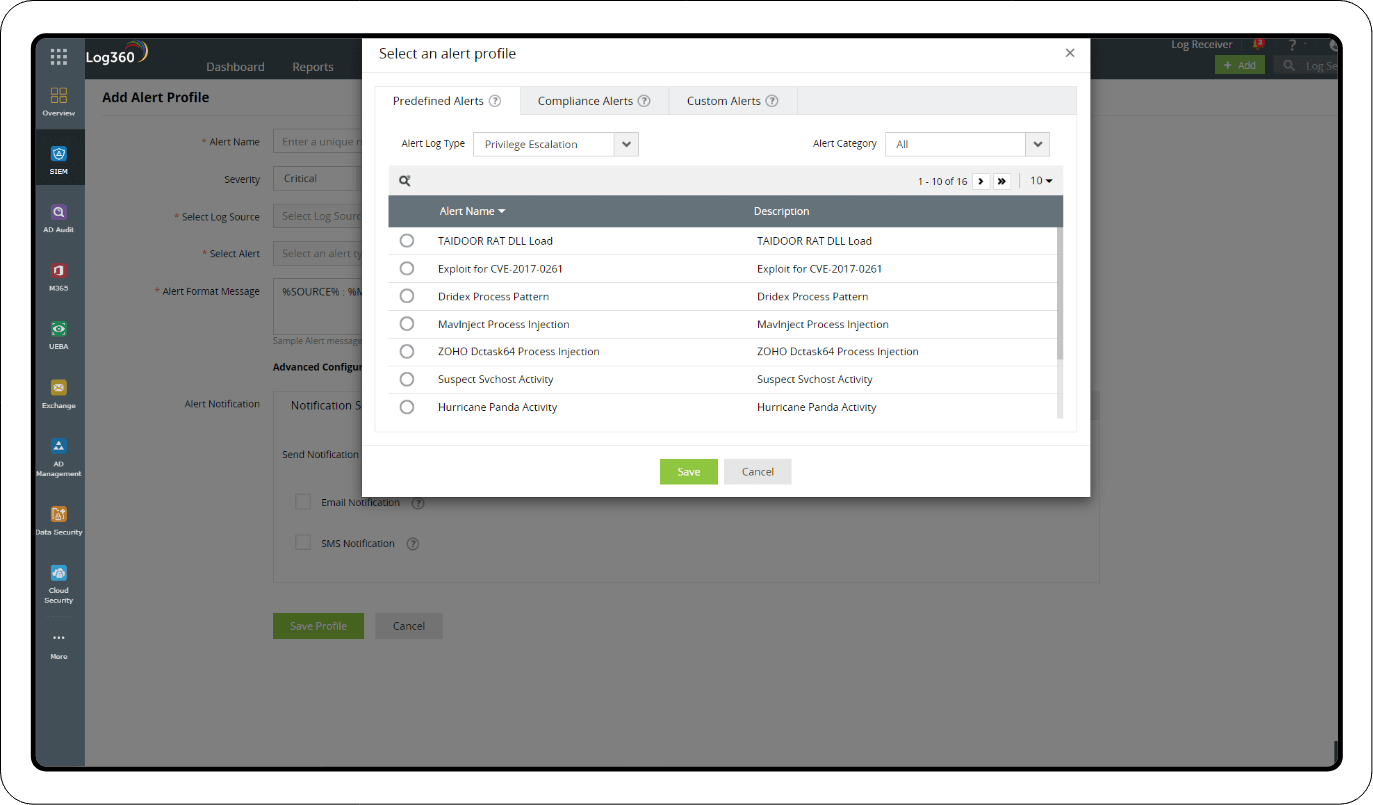
Real-time alerts
All the reports mentioned in the investigation section are available as predefined alerts in Log360's real-time alerts dashboard. You can enable or disable the alerts, customize them to add additional criteria, and configure notifications via email and SMS.
Ready to secure your network from privilege escalation attacks? Leverage Log360’s advanced security features to implement robust defensive strategies and incident response measures.
- What is privilege escalation?
- Types of privilege escalation attacks
- Understanding privileges in an enterprise network
- How does a privilege escalation attack work?
- Privilege escalation techniques
- Linux privilege escalation
- Windows privilege escalation
- How to detect privilege escalation attacks
- Best practices to prevent privilege escalation attack
- How Log360 helps detect and prevent privilege escalation attacks