Any employee within a company may access operating systems, devices, and applications, but with different usernames and credentials. Consider for a moment whether your username is the same for your Linux, Windows, or SQL accounts. Devices and applications use platform-specific user registries that are distinct from each other.
Linking these user accounts is a common challenge organizations face especially during single sign-on implementation. This administrative challenge can hinder an organization's security performance if the security analytics solution is not able to map user behavior across platforms and assign risk scores accordingly. Imagine monitoring various user accounts in separate silos, each with a different risk score, even though they all actually belong to the same user. This is the issue at hand. The table below shows one user, Michael Bay, using different user identities to log on and access various devices and applications.
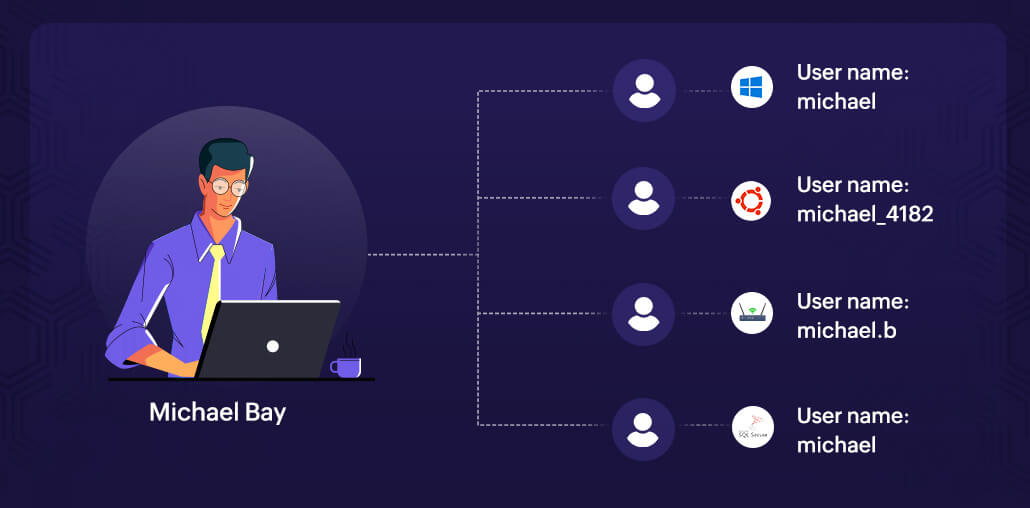
A UEBA solution is able to track anomalous activities of users and entities, and generates a risk score, thereby helping you track and prevent occurrences of insider threats, account compromise, and data exfiltration. User identity mapping (UIM) is the process of mapping different user accounts in an enterprise to a base account such as Active Directory by matching common attributes. With UIM, the activities of discrete user accounts from different sources are attributed to the one user who is actually performing them.
Users are mapped across the network using their AD account as the basis, or Source Account using mapping configurations. Mapping configurations are rules that the admins can create by specifying attributes of account target and account source across domains. Users identified by these specified attributes will be automatically mapped. Here's how it works in four easy steps.
The individual user accounts are then mapped to the AD account, and all anomalies associated with the user across sources can be viewed in a single dashboard.
The user accounts that were earlier considered separate and had individual risk scores, will now have only one representation and one risk score. The consolidated risk score is calculated from the individual's action across platforms (Windows, Linux, and SQL).
Interested in learning more about ManageEngine Log360? Sign up for a personalized demo with our product experts here.
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.