Direct Inward Dialing: +1 408 916 9892
ADAudit Plus is real-time, web-based Windows Active Directory change reporting software that audits, tracks and reports on Windows (Active Directory, workstations logon/logoff, file servers and servers), NetApp filers and EMC servers to help meet the most-needed security, audit and compliance demands. Track authorized/unauthorized AD management changes, access of users, GPO, groups, computer and OU. Also, track all modifications, access and permissions changes with 200+ detailed event-specific reports and instant emails alerts. These reports can be exported to XLS, HTML, PDF and CSV formats to assist in interpretation and computer forensics.
ADAudit Plus lets administrators see all failed attempts at modifying a file and information on who attempted to modify, what machine they attempted to make changes from, when, and the reason for failure access.
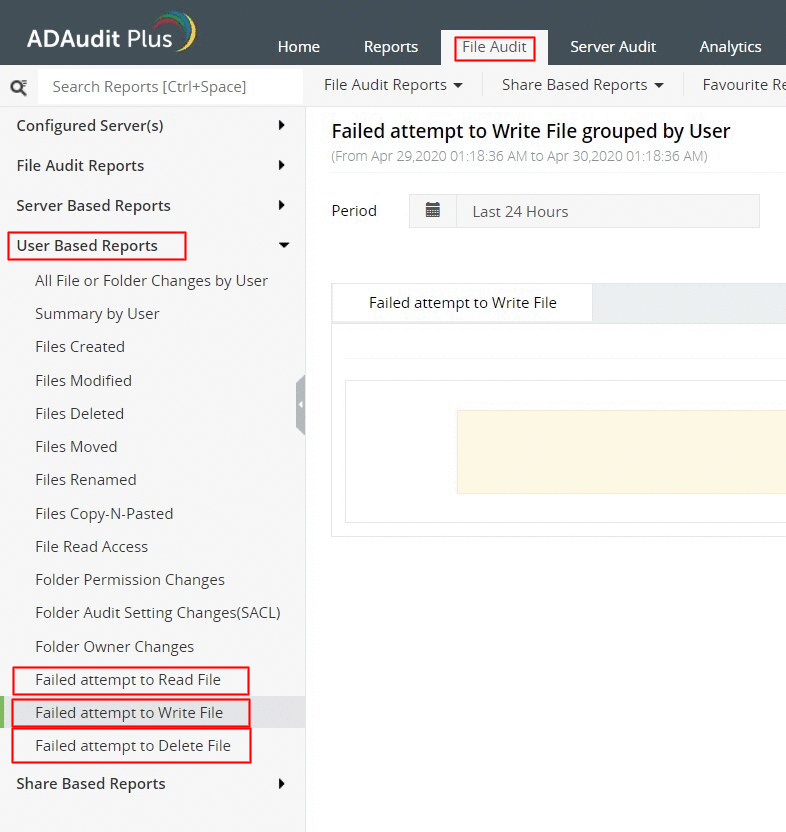
Login to ADAudit Plus ➔ Go to the File Audit tab ➔ Under User Based Reports ➔ Navigate to any of the below mentioned reports.
Failed attempt to read file
Failed attempt to write file
Failed attempt to delete file
Select the Domain.
Select Export As to export the report in any of the preferred formats (CSV, PDF, HTML, CSVDE and XLSX).
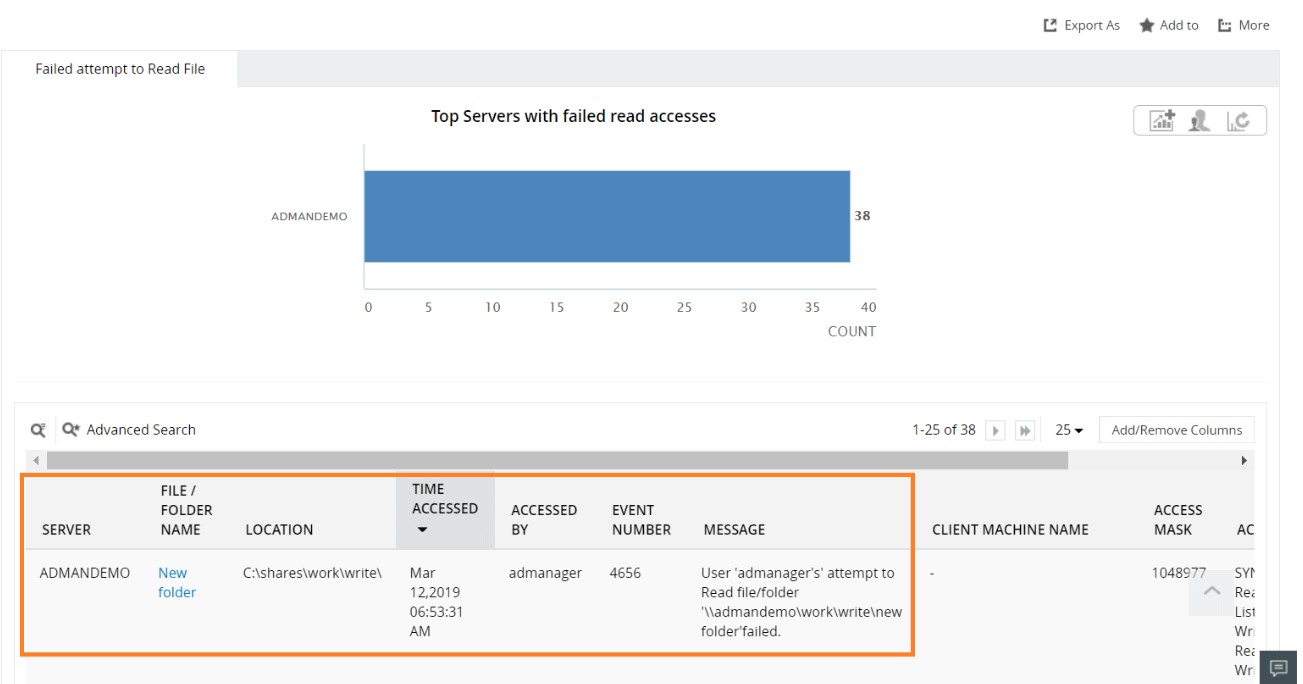
The details you get in this report are:
User Name of that account that tried to modify the file and failed.
IP address of the user.
The time when the access failure happened.
The computer or server in which the failure took place.
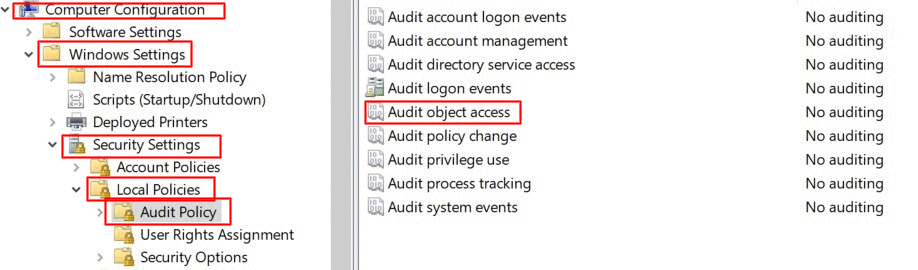
With native auditing, here is how you can track failed attempts to modify a file.
Logon to your domain controller with administrative privileges and launch the Group Policy Management console.
Right-click the appropriate Group Policy Object linked to the Domain Controllers container and select Edit.
Navigate to Computer Configuration -> Windows Settings -> Security Settings ->Local Policies -> Audit Policy.
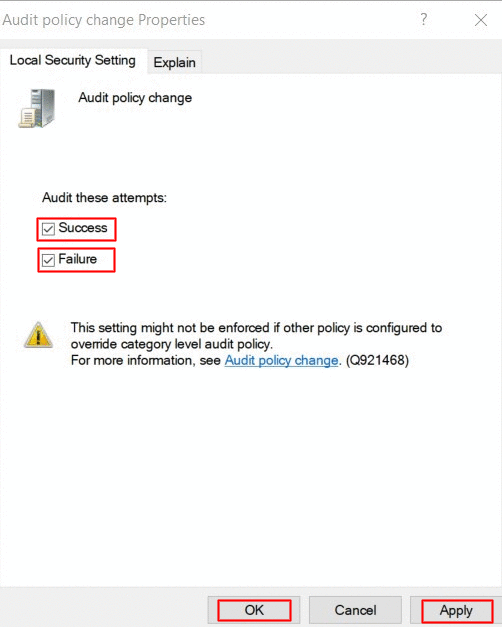
Under Audit Policy, select 'Audit object access' and turn auditing on for both success and failure.
After enabling auditing, you can use Event Viewer to see the logs and investigate events. Follow the below mentioned steps:
Open Event Viewer
Expand Windows Logs > Security
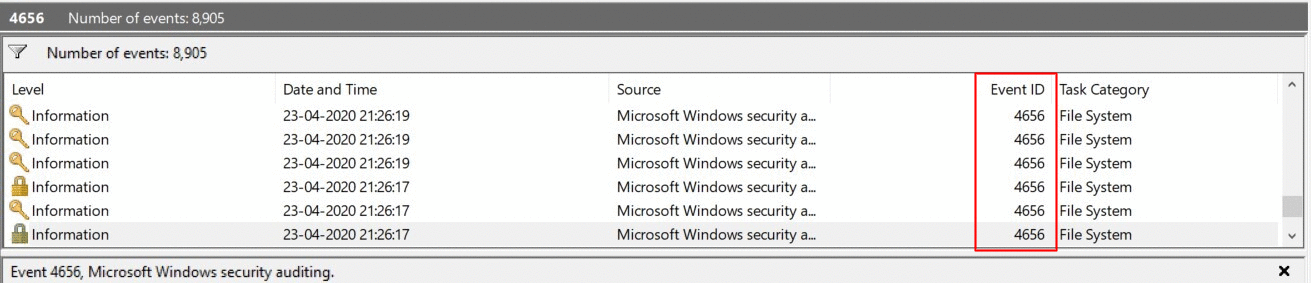
Create a custom view for Event ID 4656/4663. This ID indicates object access request.
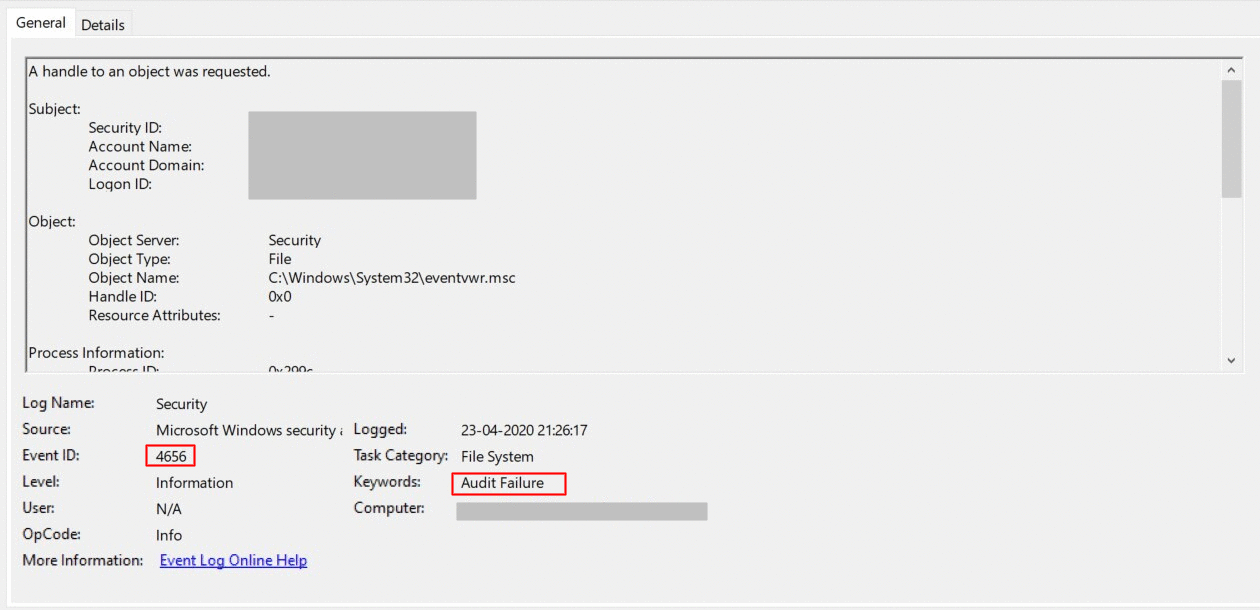
Double click on the event. You can view detailed information about the activity such as account name, date and time of login failure.
Native auditing becoming a little too much?
Simplify File Server auditing and reporting with ADAudit Plus.
Get Your Free Trial Fully functional 30-day trial