Direct Inward Dialing: +1 408 916 9892
Open Server Manager on your Windows server.
Under the Manage tab,click on Group Policy Management to open the Group Policy Management Console.
Navigate to Forest >Domain >Your Domain >Domain Controllers.
You can choose to either edit an existing group policy object or create a new one.
In the Group Policy Editor, navigate to Computer Configuration >Windows Settings >Security Settings >Advanced Audit Policy Configuration.
Expand the node and navigate to Audit Policy >Object Access and then configure Audit Application Generated. Enable it for both 'Success' and 'Failure'.
To open ADFS Management snap-in, navigate to Programs >Administrative Tools > ADFS Management
Click on Actions and then select Edit Federation Service Properties.
In the dialog box that opens, click on the Events tab. Enable it for Success and Failure.
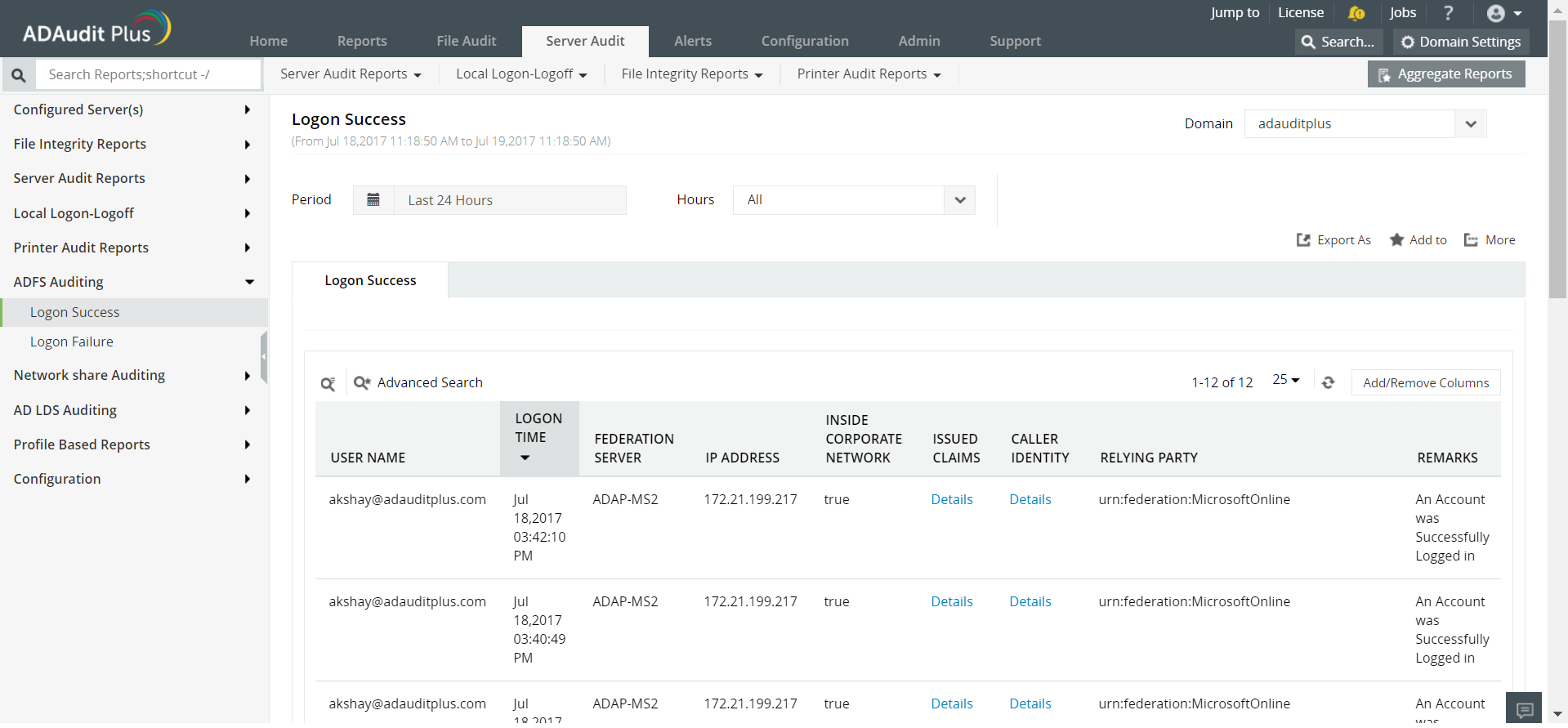
ADAudit Plus can perform auditing efficiently by generating multiple reports on ADFS. To access them, open the ADAudit Plus console, find the Reports tab at the top and navigate to ADFS Auditing. Here you can generate multiple reports, on ADFS, such as Logon success, Logon Failures and so on. Here is a sample report:
Open Server Manager on your Windows server.
Under the Manage tab,click on Group Policy Management to open the Group Policy Management Console.
Navigate to Forest >Domain >Your Domain >Domain Controllers.
You can choose to either edit an existing group policy object or create a new one.
In the Group Policy Editor, navigate to Computer Configuration >Windows Settings >Security Settings >Advanced Audit Policy Configuration.
Expand the node and navigate to Audit Policy >Object Access and then configure Audit Application Generated. Enable it for both 'Success' and 'Failure'.
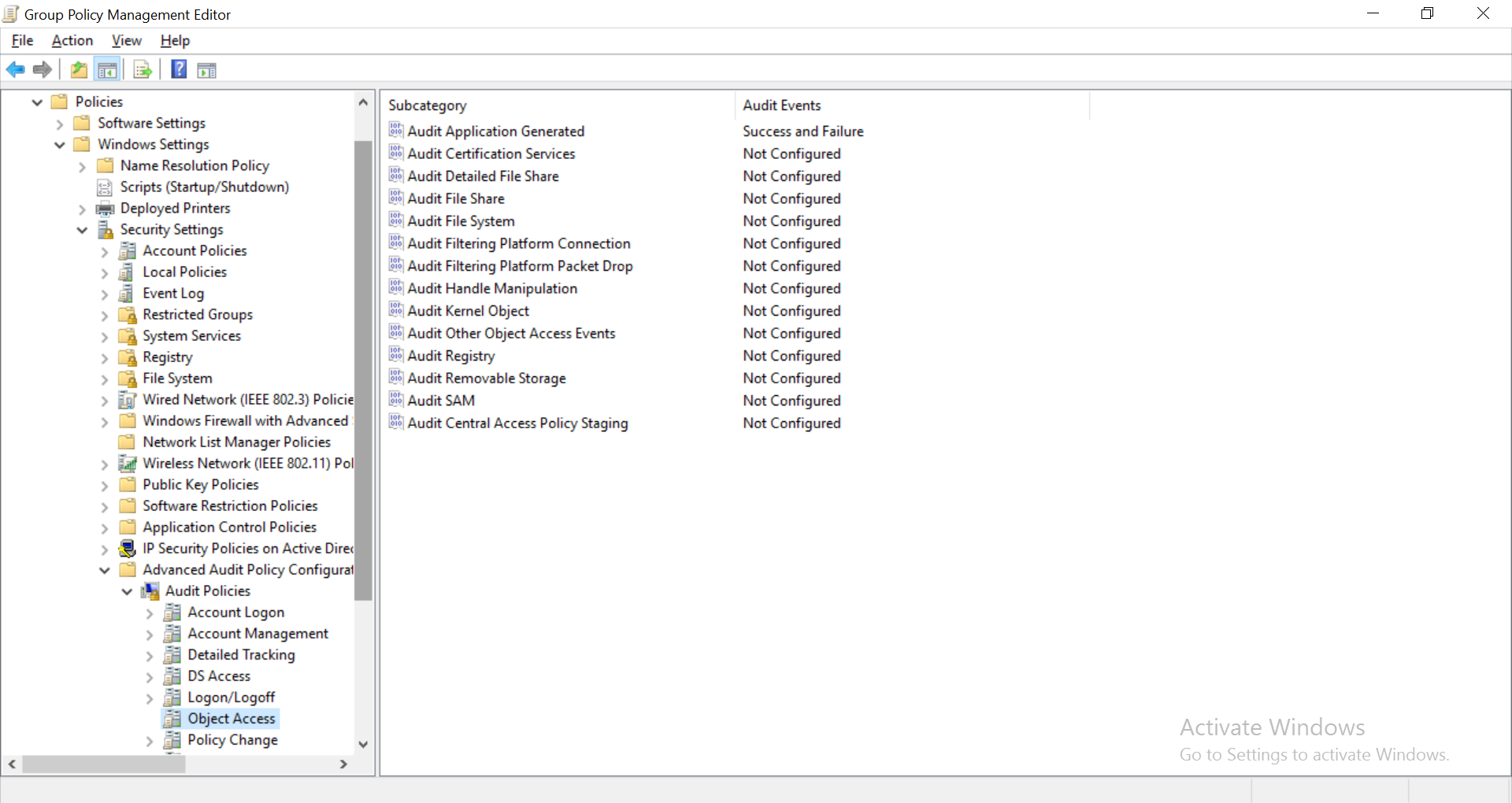
[Highlight policies, windows settings, security settings, Advanced audit policy, audit policy, object access and audit application generated]
To open ADFS Management snap-in, navigate to Programs >Administrative Tools > ADFS Management
Click on Actions and then select Edit Federation Service Properties.
In the dialog box that opens, click on the Events tab. Enable it for Success and Failure.
Event Viewer records all the events connected to the objects in Active Directory that have been enabled for auditing with unique event IDs.
To view the events, open Windows Event Viewer and navigate to Windows Logs > Security and look for events IDs 1200 (Application Token Success), 1201 (Application Token Failure), 1202 (Fresh credential validation success), 1203 (Fresh Credential Validation Error), 1204 (Password Change Request Success), 1205 (Password Change Request Error), 1206 (Sign Out Success), 1207 (Sign Out Failure).
Native auditing becoming a little too much?
Simplify Active Directory auditing and reporting with ADAudit Plus.
Get Your Free Trial Fully functional 30-day trial