Event ID 4625 is a Windows Security log entry that appears whenever a logon attempt fails. It captures details such as the user account, the time of the attempt, the logon type, the originating workstation or IP address, and the reason for the failure. The event is recorded on the computer or domain controller where the logon was attempted.
Failed logons in AD may seem like harmless typos, but they can also signal the early stages of an account compromise. It’s essential for administrators to quickly trace the origin of these failed attempts, identifying who tried to log in, when the attempt occurred, and where it came from.
This page walks you through two effective methods to investigate failed login attempts. First, how to use the native Windows Event Viewer to manually locate and interpret Event ID 4625, which logs all failed logon attempts. Then, we'll explore a faster, more efficient approach using ManageEngine ADAudit Plus, which automates event collection, correlation, and reporting.
Why tracking failed logons matters
- Detect brute-force attempts and password-spray activity early.
- Identify misconfigurations such as services or scheduled tasks that are running on stale credentials.
- Speed up incident response and compliance investigations with clear audit trails.
- Native auditing
- ADAudit Plus
Steps to enable logon failure auditing using group policy:
- 1. Open the Group Policy Management Console (GPMC) or run the command gpmc.msc.
- 2. If you want to audit all the accounts in the domain, right-click the domain name and click Create a GPO in this domain, and Link it here. If you want to audit accounts in a specific organizational unit (OU), right-click the OU and click Create a GPO in this domain, and Link it here.
- 3. Provide a relevant name for the GPO, right-click it, choose Edit, and navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Advanced Audit Policy Configuration > Audit Policies > Logon/Logoff > Audit Logon. In the Audit Logon Properties window, select the Failure check box (selecting Success is optional), and click OK.
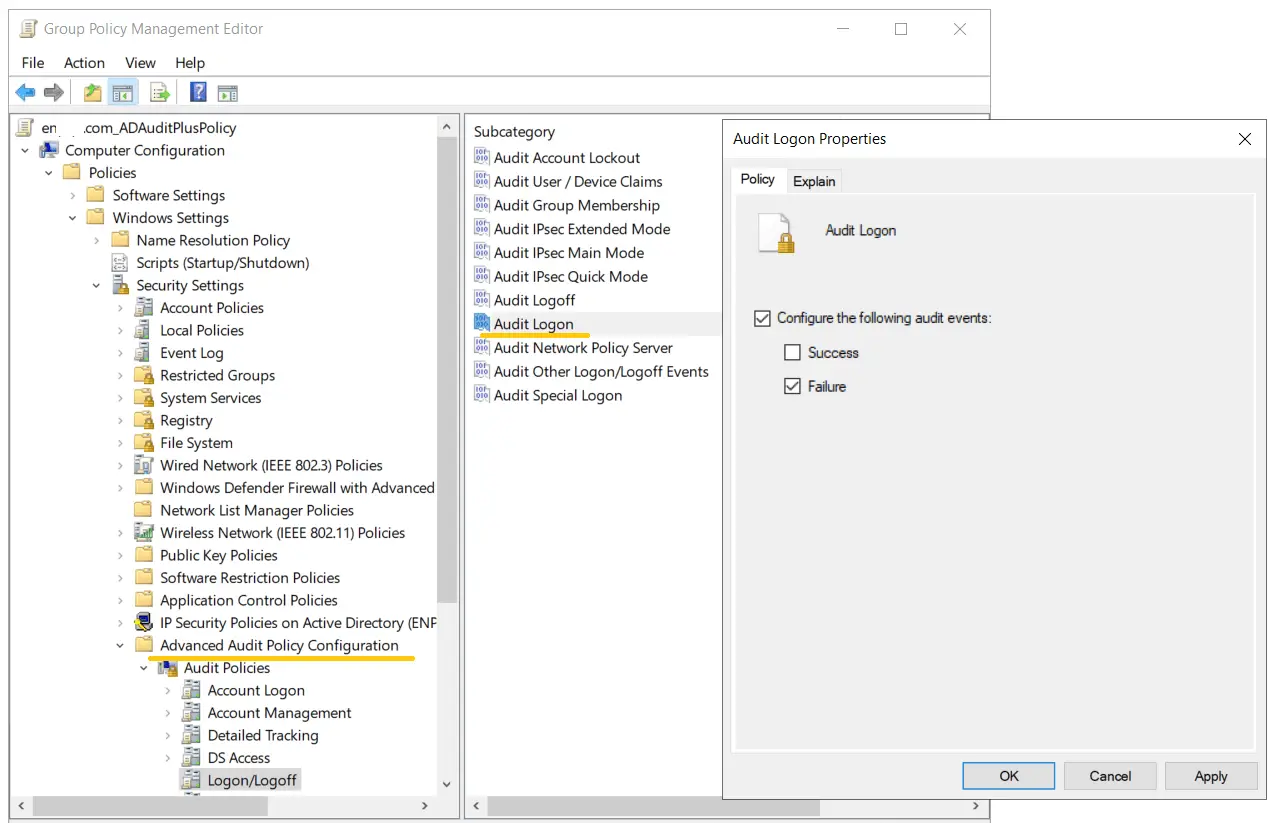
- 4. Go back to the GPMC, right-click the OU or domain in which the GPO was linked, and click Group Policy Update. This step makes sure the new Group Policy settings are applied instantly instead of waiting for the next scheduled refresh.
Once the above steps are complete, logon failure events will be recorded as event logs, and they can be viewed in the Event Viewer by following the steps below.
Steps to find the source of failed login attempts in Windows Event Viewer:
- 1. Open the Event Viewer. On the left pane, navigate to Windows log > Security.
- 2. On the right pane, navigate to Security > Filter current log.
- 3. In the pop-up window, enter the 4625 in the field labeled <All Event IDs>. This will provide you with a list of occurrences of Event ID 4625. Double-click the Event ID to view its properties.
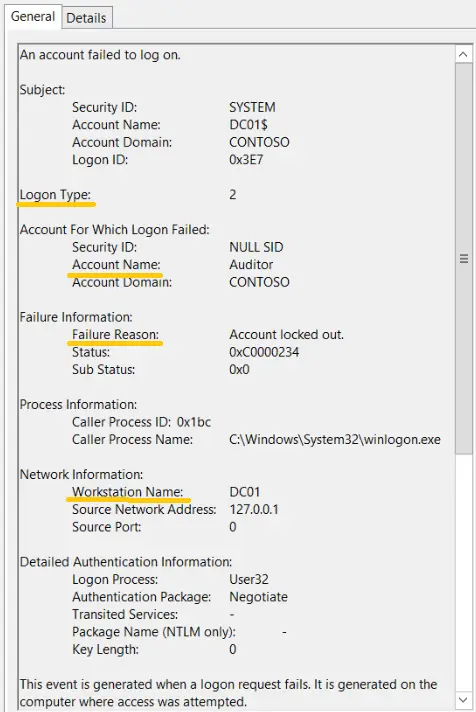
Important information that can be derived from Event ID 4625 includes:
- Account Name: Name of the user.
- Failure Reason: Why the failure occurred, such as a bad password.
- Logon Typ: How access was attempted.
- Workstation Name: NetBIOS name of the the computer.
- Source Network Address: IP address of the computer.
Workstation Name and Source Network Address together help identify where the failed attempt came from.
Logon types you’ll see most:
| Code | Meaning | Typical scenario |
|---|---|---|
| 2 | Interactive | Local console sign-in |
| 3 | Network | Access over the network (e.g., SMB, mapped drives) |
| 7 | Unlock | Workstation unlock |
| 10 | RemoteInteractive | RDP/Remote Desktop sign-in |
| 11 | CachedInteractive | Cached domain logon (e.g., laptops) |
Steps to find the source of failed login attempts using ADAudit Plus:
- Ensure Audit Logon Failure is enabled via GPO.
- Download and install ADAudit Plus.
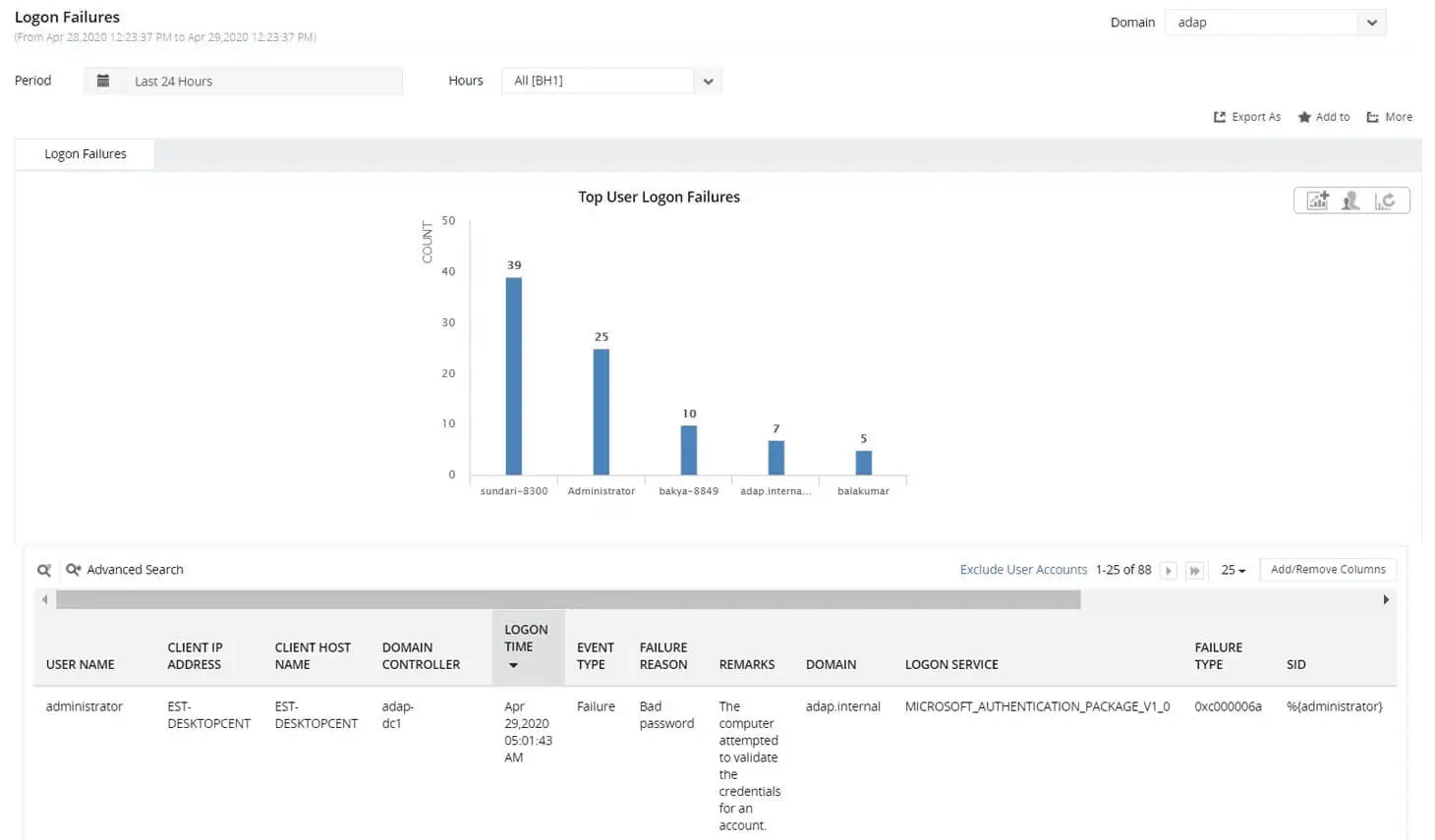
- Log in to ADAudit Plus, navigate to Active Directory > Auditing > User Logon Reports > Logon Failures.
Select the Domain and Period. Filter the report by user, client IP address, host name, domain controller, time range, or failure reason to quickly identify the source of the failed logon.
Bridging the gaps in native auditing with ADAudit Plus
Native Windows auditing requires expertise, is time-consuming, and lacks some capabilities, making third-party tools like ADAudit Plus essential. ADAudit Plus helps with:
- Centralized auditing: Collects logs from all computers without the complexity of Windows Event Forwarding.
- Threat mitigation: Detects suspicious patterns such as multiple failed logons followed by a success using correlation and machine learning, unlike Task Scheduler’s limited event alerts.
- Compliance reporting: Consolidates fragmented event data into a complete audit trail and helps meet compliance requirements.
For more information on how ADAudit Plus helps organizations overcome the limitations of native Windows auditing tools, check out this e-book.
A one-stop solution for all your IT auditing, compliance, and security needs
ADAudit Plus provides capabilities like change auditing, logon monitoring, file tracking, compliance reporting, attack surface analysis, response automation, and backup and recovery for diverse IT systems.
FAQ
Logon Type 10 (RemoteInteractive) usually points to a Remote Desktop Protocol (RDP) session. Logon Type 3 (Network), on the other hand, is more common for file sharing or network-based access where there’s no active desktop session.
Yes, ADAudit Plus can collect failed logon events from all configured computers across your domain. With the Logon Failures report, you can quickly pinpoint where repeated logon failures are coming from and understand why they’re happening. In many cases, the issue turns out to be services, mapped drives, or scheduled tasks that are still using stale credentials.
Experience
ADAudit Plus for free
With ADAudit Plus, you can:
- Get full visibility into logons
- Monitor employee attendance
- Detect attacks like Kerberoasting
- Generate logon audit trails
- And much more