Direct Inward Dialing: +1 408 916 9892
Activities of privileged users can be tracked by following the below mentioned steps:
Login to ADAudit Plus
Select the required Domain from the dropdown list
Go to the Reports tab
Navigate to Account Management
Select Administrative User Actions
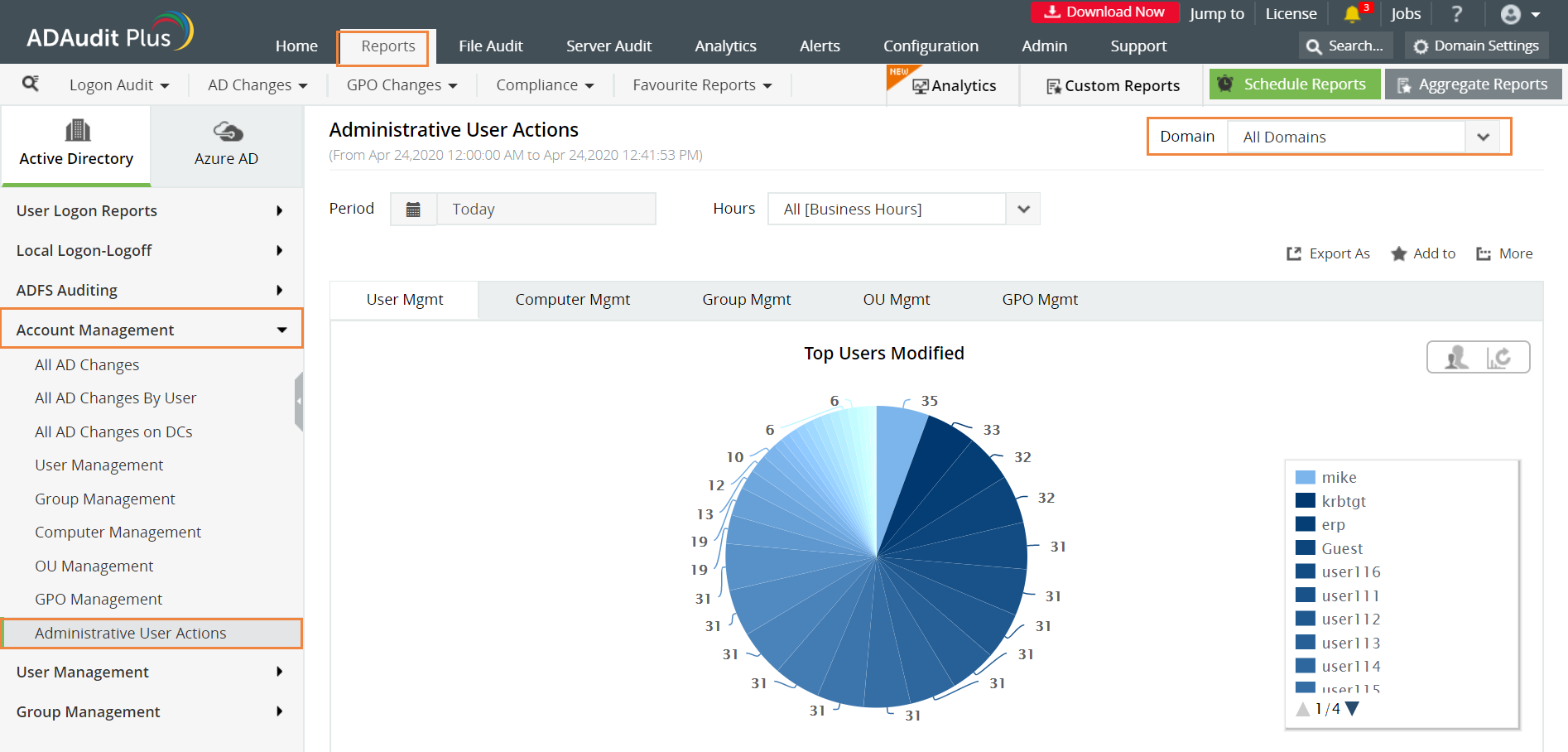
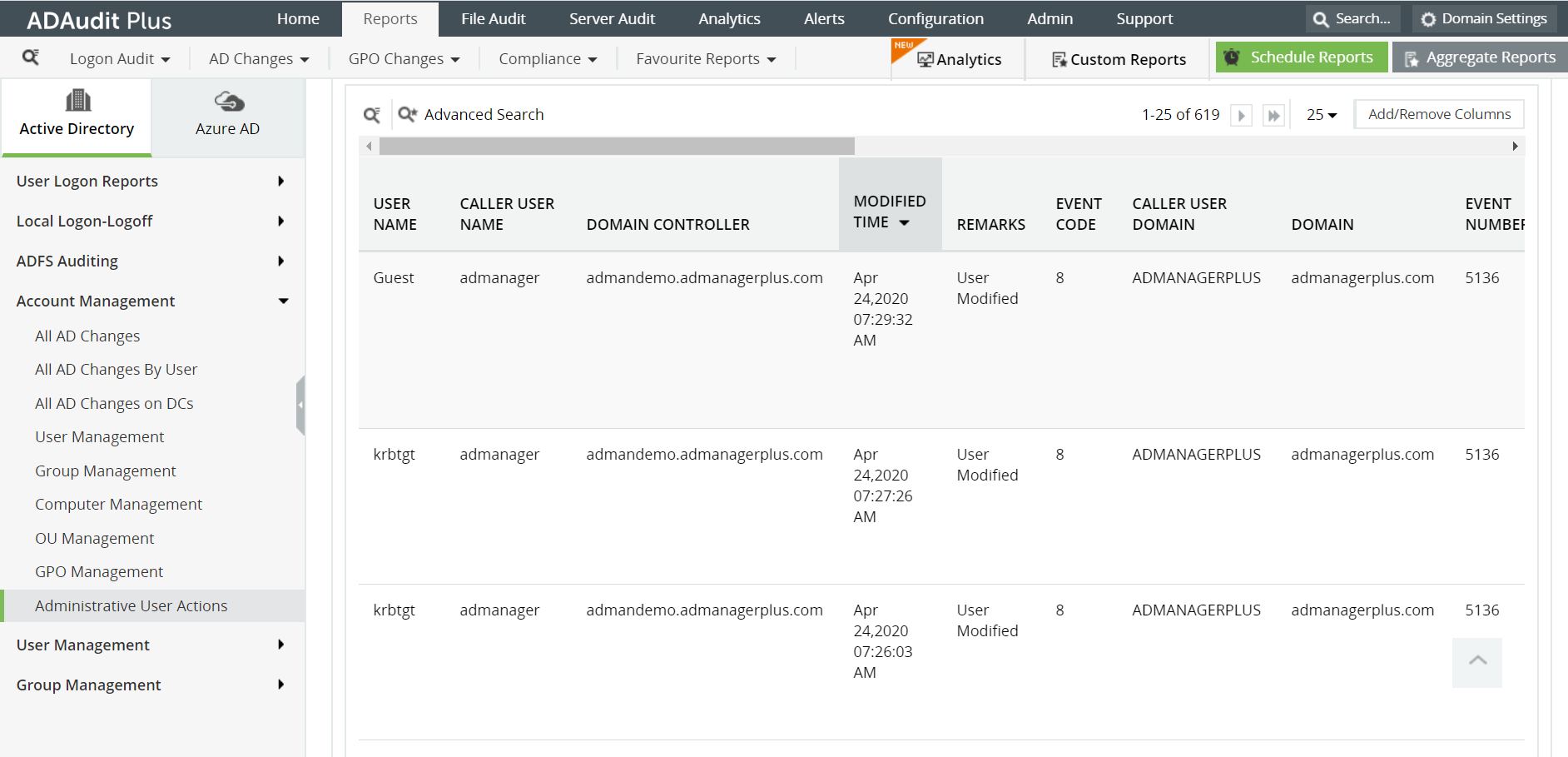
The following are some of the details you can get in this report:
User Name of the privileged account that made the changes
The time when the changes were made
The computer or server in which the changes were made from
The description of the changes made
With native AD auditing, here is how you can monitor privileged user accounts:
If a member satisfies any of the below mentioned criteria, they can be identified as privileged users.
Users/Groups who are members of any administrative groups.
Users/Groups who have received administrative privileges through their Organizational Unit.
Local user accounts and service accounts that may have received administrative privileges locally on domain controllers.
Users who have received privileges to reset passwords and unlock the accounts of other users.
Users who have administrative privileges using which they can access Service Accounts.
Users who have write access to Group Policy Objects related to domain controllers.
Users who have access to any application that manages Active Directory.
Users who are administrator of the Virtual System Environment.
You can list all privileged users by using Active Directory Users and Computers and Group Policy Management Console.
To discover other privileged user accounts customized scripts need to be executed. For instance, every member of any administrative group is a privileged user.
Launch Server Manager in your Windows Server instance.
Under Manage, select Group Policy Management and launch the Group Policy Management console.
Navigate to Forest ➔ Domain ➔ Your domain ➔ Domain Controllers.
Create a new GPO and link it to the domain containing the user object, or edit any existing GPO that is linked to the domain to open the Group Policy Management Editor.
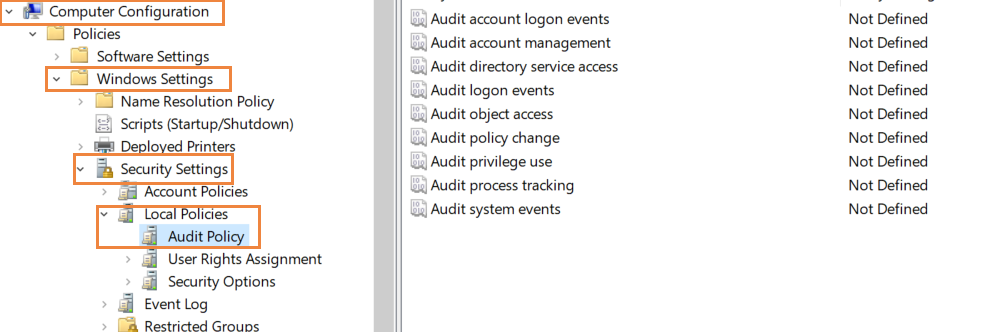
Navigate to Computer Configuration ➔ Windows Settings ➔ Security Settings ➔ Local Policies ➔ Audit Policy.
The Audit Policy lists all of its sub-policies in the right panel, as shown in the Figure below.
Select the policies you want to enable for both its successful and failure events. In the event of multiple failures, the organization can initiate security protocol, if necessary.
Click Apply and OK to close Properties window.
Launch Server Manager in your Windows Server instance.
Under Manage, select Group Policy Management and launch the Group Policy Management console.
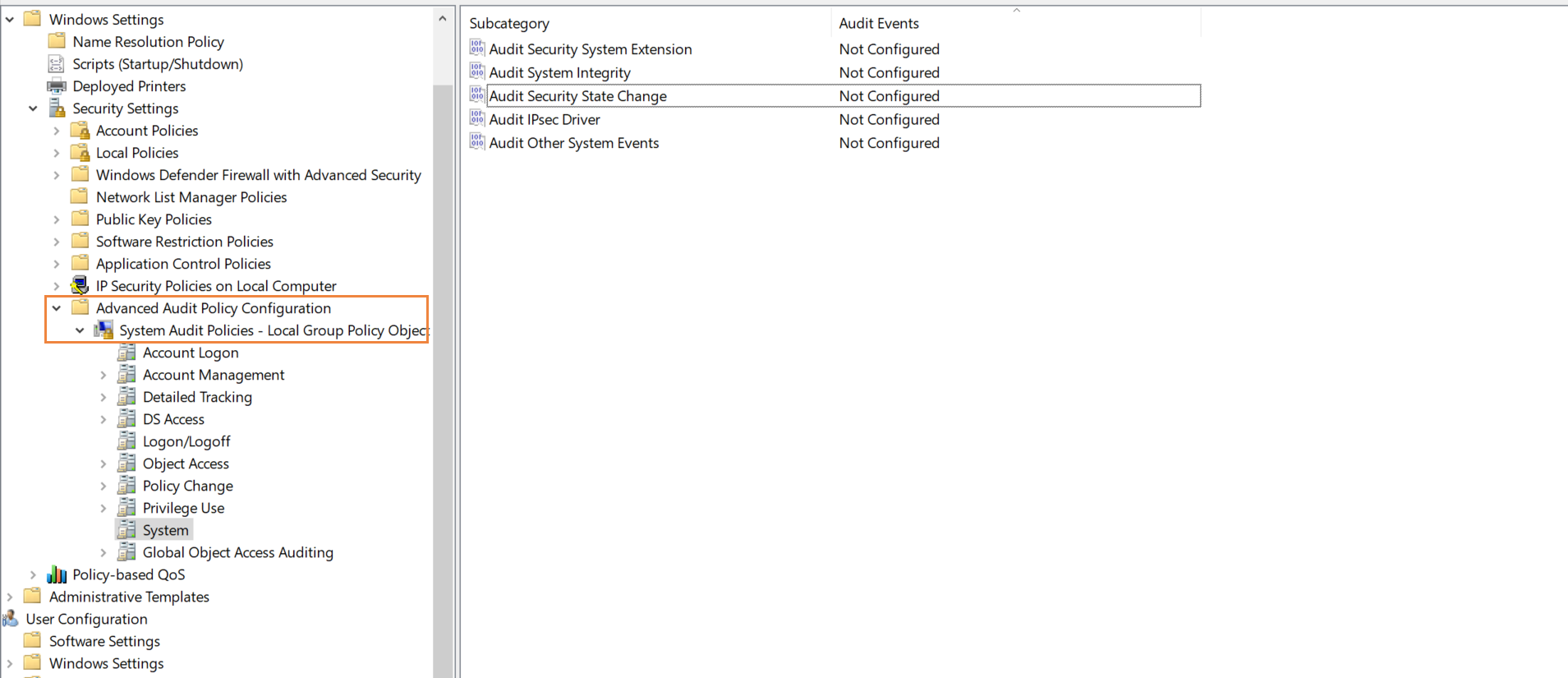
Navigate to Computer Configuration ➔ Windows Settings ➔ Security Settings ➔ Advanced Audit Policy Configuration ➔ System Audit Policies.
Select the required Audit Policies you want to enable and select both Success and Failure events.
Force audit policy subcategory settings to override audit policy category settings in Group Policy to make sure that basic auditing is disabled.
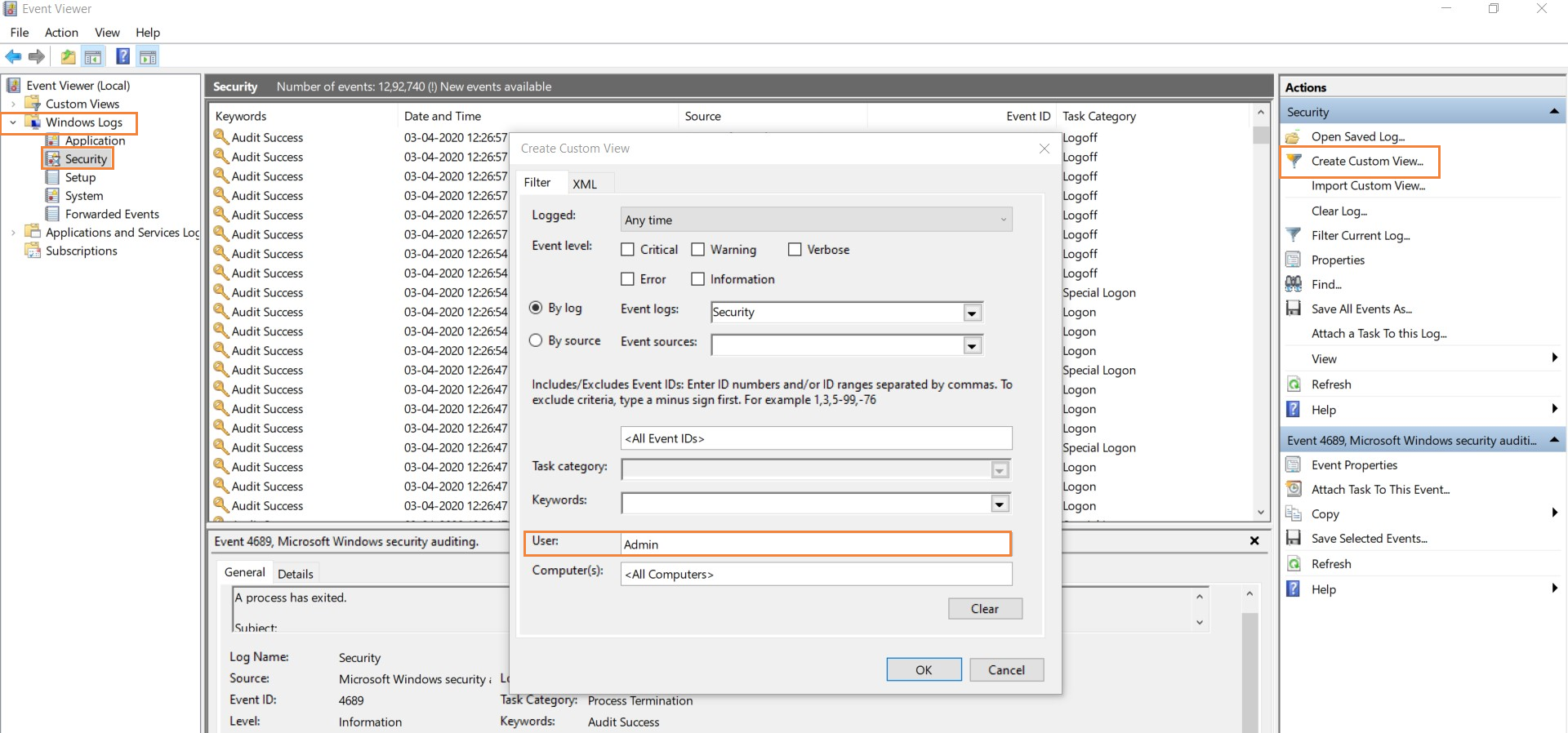
Click on Start ➔ Administrative Tools ➔ Event Viewer
Click Windows Logs and select Security. You will see all the events logged in security logs.
Search using Find option or create a custom view to display the events generated by a specific privileged account.
Native auditing becoming a little too much?
Simplify Active Directory auditing and reporting with ADAudit Plus.
Get Your Free Trial Fully functional 30-day trialADAudit Plus simplifies privileged user tracking by offering you predefined privileged user activity monitoring report along with intuitive graphical representation of the same for the ease of comprehension. ADAudit Plus also provides you the option to generate custom reports and export them in your preferred format (.pdf, .xls, .html and .csv).