Direct Inward Dialing: +1 408 916 9892
ADAudit Plus has a simple and straightforward method to get the reason behind logon failures.
You need to enable auditing for the logon events for ADAudit Plus to capture and analyze those events. Check out the first step of the previous section.
Once you enable auditing, follow the below steps to get reports on logon failures using ADAudit Plus
Login to ADAudit Plus web console.
Click on the Reports tab, navigate to User Logon Reports and select Logon Failures. 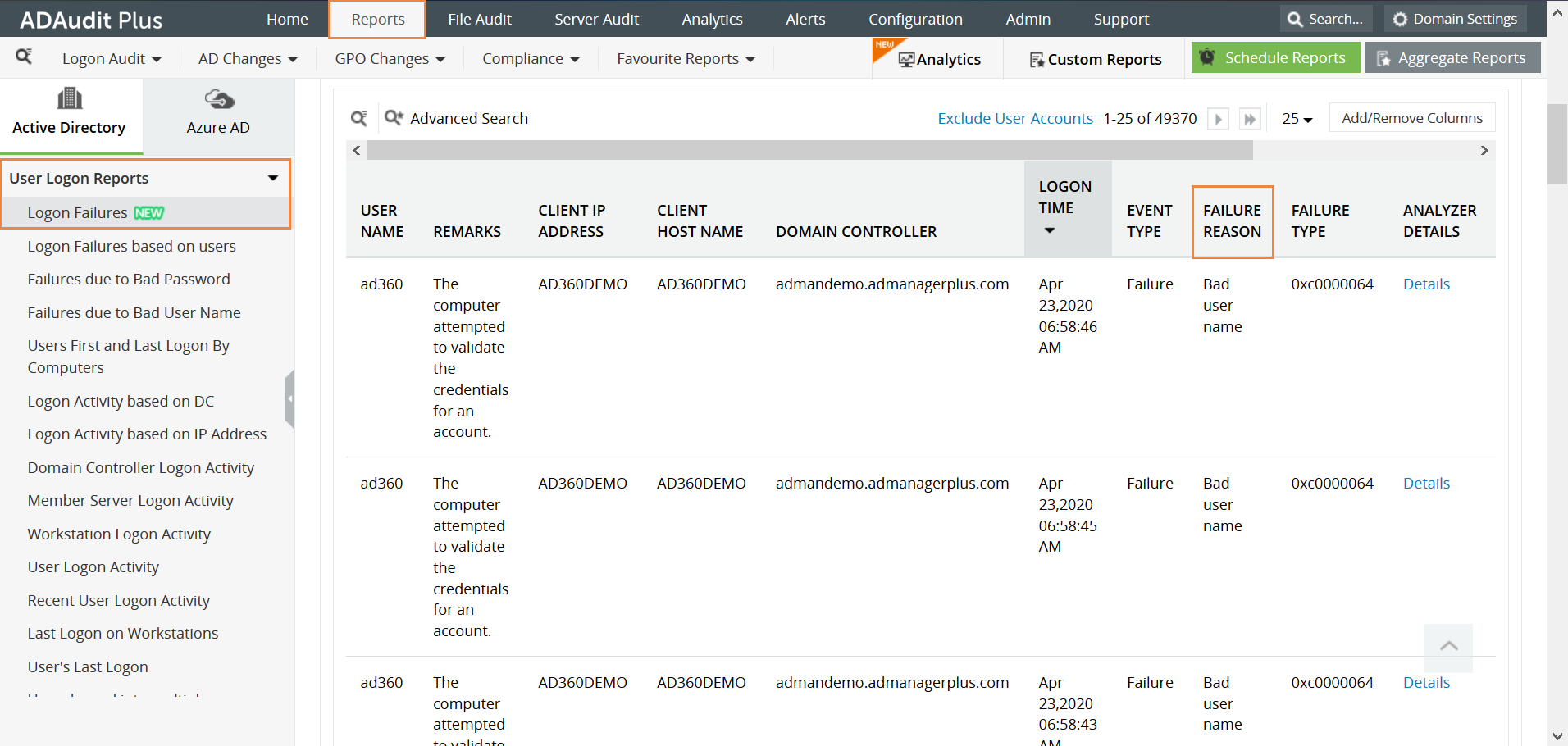
This report helps administrators verify the reason for the logon failure. Based on the reason, the administrator can decide whether it is a potential security threat or not.
ADAudit Plus can generate clear, user-friendly reports for all the important events in the domain and also has a real-time alert feature which alerts the admins in case of any unanticipated activity. Explore other capabilities of ADAudit Plus here.
Here is how you can find the reason for failed logon attempts in native AD.
Open 'Server Manager' on your Windows server.
Under the 'Manage' tab, select 'Group Policy Management' to view the 'Group Policy Management Console'.
Navigate to Forest>Domain>Your Domain>Domain Controllers.
Either create a new group policy object or you can edit an existing GPO.
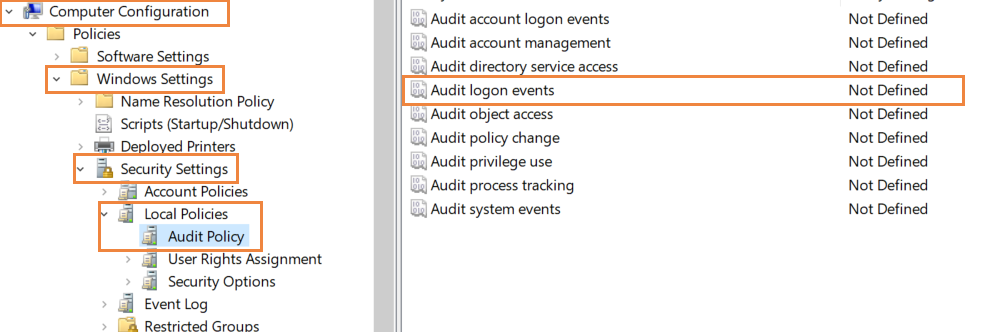
In the group policy editor, navigate to Computer Configuration > Windows Settings > Security Settings > Local Policies > Audit Policy.
In Audit policies, select 'Audit logon events' and enable it for 'Failure'.
Once Audit Policy is enabled, the Event Viewer records those events against their respective event IDs. Look for event ID 4625 that denotes a failed logon attempt.
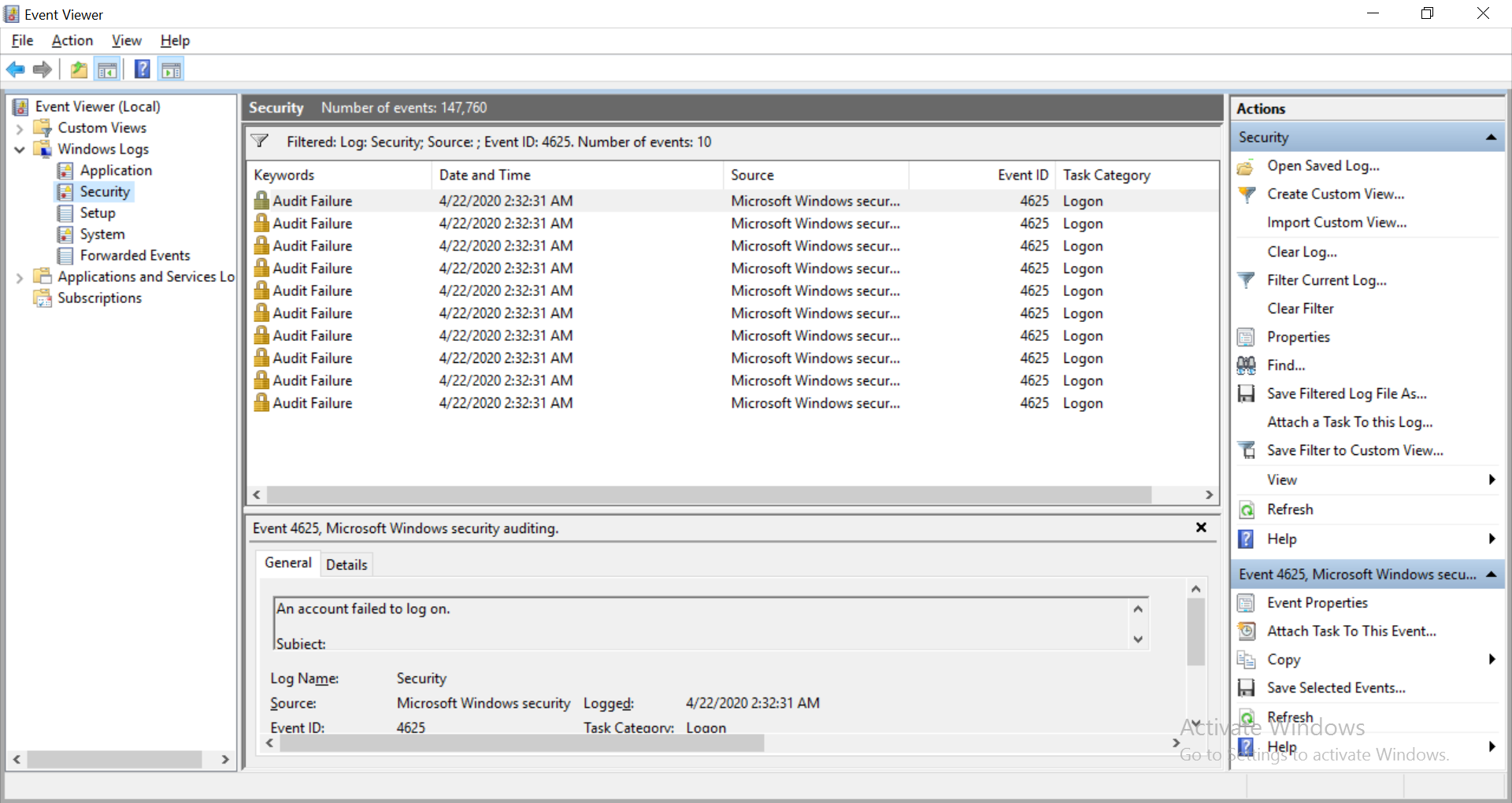
Run a filter for event ID 4625 to get a list of all the failed logon attempts recorded in the Event Viewer. Right-click on the relevant event and select Event Properties. Scroll down the General information of the event to verify the reason for the failed logon.
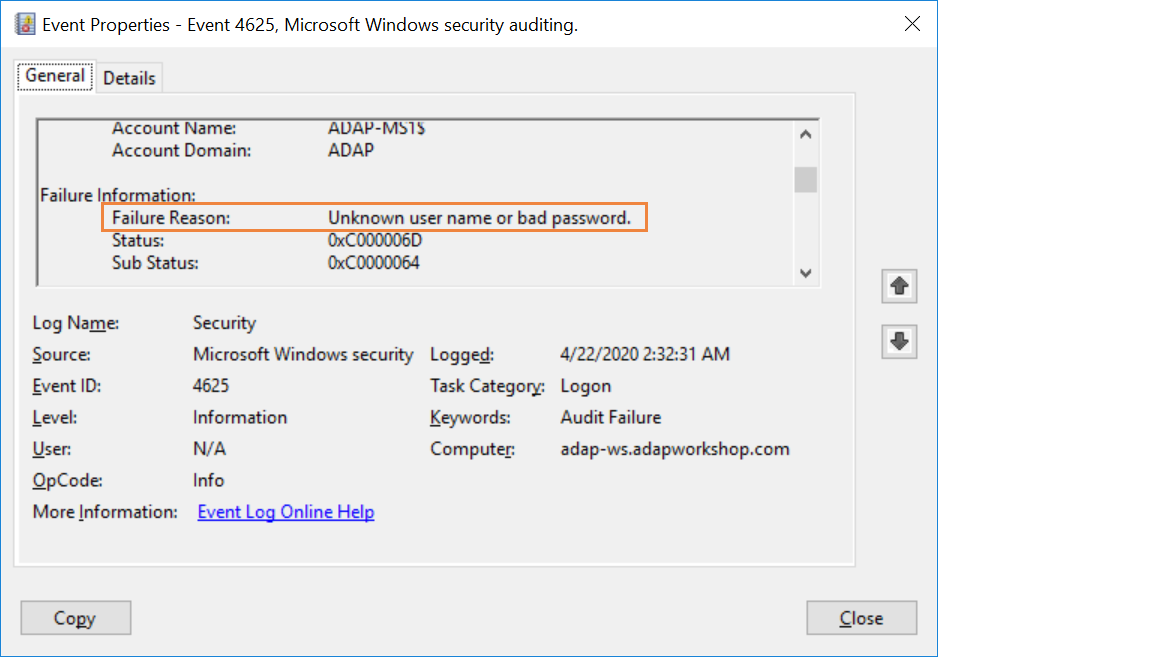
You will have to repeat this process multiple times to ascertain the reason for each failed logon attempts.
Native auditing becoming a little too much?
Simplify Active Directory auditing and reporting with ADAudit Plus.
Get Your Free Trial Fully functional 30-day trial