What is NIST CSF?
NIST CSF is a framework that has been developed by the National Institute of Standards and Technology (NIST) to help organizations manage and reduce their cybersecurity risk. Through its guidelines, best practices, and standards, it provides organizations with a structured approach to assessing and strengthening cybersecurity posture.
NIST CSF can be used by organizations to:
- Learn about and choose a desired security-based outcome.
- Create a plan to achieve that outcome.
- Evaluate the progress taken to attain the desired outcome.
- Assess the organization's present cybersecurity capabilities and evaluate the challenges to achieve the desired outcome.
Evolution of NIST CSF
Work on the NIST CSF began after Executive Order 13636 -- Improving Critical Infrastructure Cybersecurity -- was signed by United States President Barack Obama on February 12, 2013. According to this order, repeated cyber intrusions into critical infrastructure demonstrated the dire need for a cybersecurity framework. It advises that such a framework should provide a prioritized, flexible, repeatable, performance-based, and cost-effective approach to help operators of critical infrastructure identify, assess, and manage cyber risk.
Exactly one year later, NIST CSF 1.0 -- Framework for Improving Critical Infrastructure Cybersecurity--was released to the public. It was developed through a collaboration among various stakeholders from the government, industry, and academia. Standards already set by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) also contributed to the NIST CSF. The updated NIST CSF 1.1 was released in April 2018, and NIST CSF 2.0 was released in February 2024. It's expected to evolve more over time, as it vies to be more informative, up-to-date, and useful.
As per the Executive Order, NIST CSF 1.0 was targeted to critical infrastructure organizations. However, it was apparent that the guidelines were applicable to organizations across all sectors and industries. NIST CSF 1.1 clearly states that the Framework can be used by organizations in any sector. In NIST CSF 2.0, the title, "Framework for Improving Critical Infrastructure Cybersecurity," is no longer used. Figure 1 shows how it has evolved through the years.
Figure 1: The evolution of NIST CSF from 2013 to 2024.
Components of NIST CSF
The NIST CSF consists of three components to help organizations reduce their cyber risk:
- Core: The Core, which is comprised of Functions, Categories, and Subcategories, describes the various security-based outcomes that organizations can choose from.
- Profiles: The CSF Profiles refer to the state of an organization's security posture in terms of outcomes. The current and target Profiles help organizations identify gaps that need to be addressed.
- Implementation Tiers: Implementation Tiers define the level to which an organization follows risk management and governance practices. They can be applied to both current and target Profiles. To achieve a target Profile, an organization should be at a target Tier as well. There are four possible Tiers or levels that organizations can be at: Tier 1 (Partial), Tier 2 (Risk-informed), Tier 3 (Repeatable), and Tier 4 (Adaptive).
Figure 2 shows the structure of NIST and how all of this comes together.
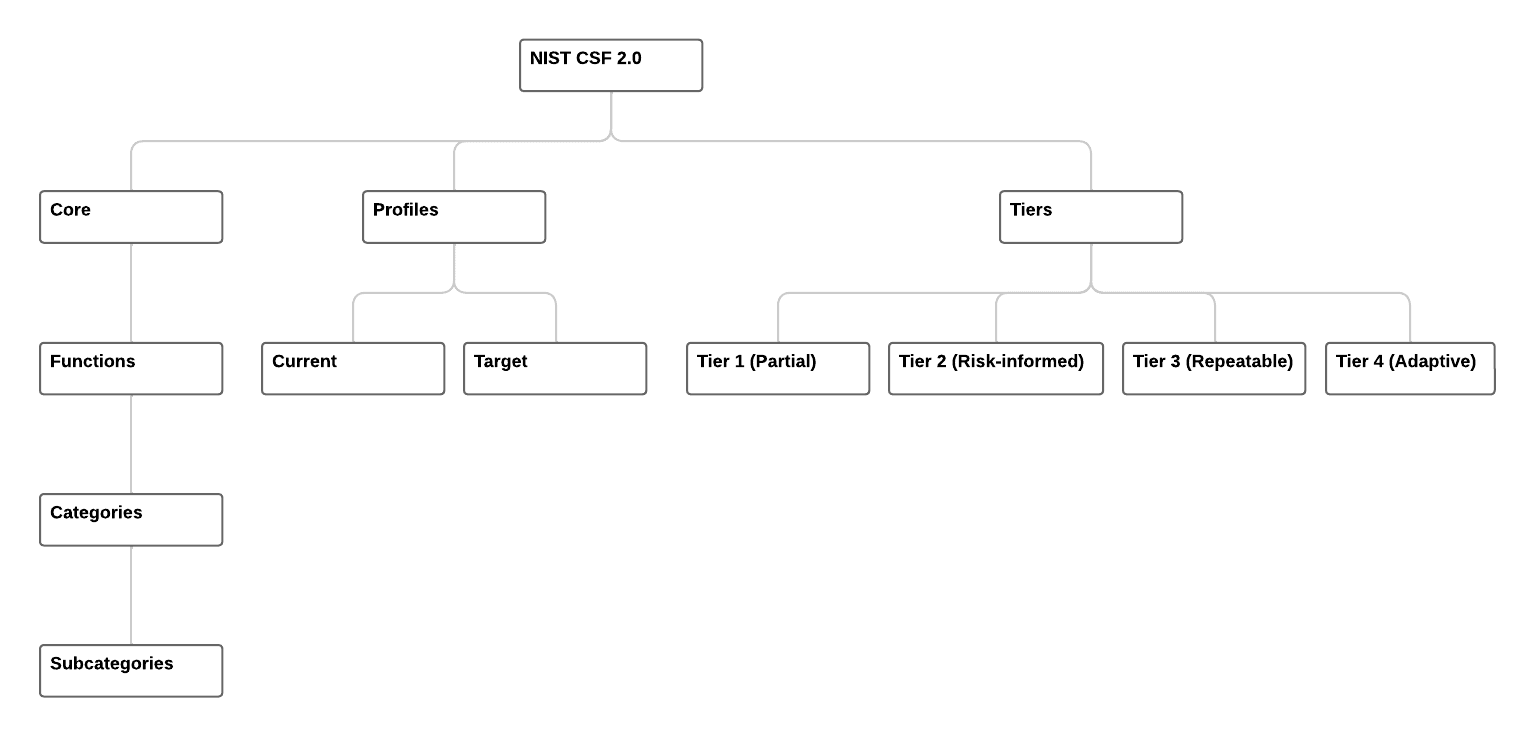
Figure 2: The structure of NIST CSF - Framework Core, Profiles and Tiers.
Who must comply?
Complying with the NIST CSF is mandatory for US federal government agencies. Although developed as policy for the US federal agencies, the NIST CSF is also designed to accommodate the various approaches of the global business ecosystem. The framework can be adopted by organizations from any country, size, or industry.
What is new in NIST CSF 2.0?
One of the main differences between NIST CSF 1.0 and NIST CSF 2.0 is the update to the Framework Core. While the NIST CSF 1.1 Core had five functions, 23 categories, and 108 subcategories, the NIST CSF 2.0 Core has six functions, 22 categories, and 106 subcategories. Categories have also been contextually rearranged in NIST CSF 2.0. The "Govern" function has been sub-headduced to provide greater executive and stakeholder oversight over organizational cybersecurity.
NIST CSF Core Functions
The NIST CSF Core has six Functions:
Govern (GV)
This Function establishes security outcomes related to the governance processes, enables informed decision-making, increases management effectiveness, and strengthens strategic planning capabilities.
Identify (ID)
The comprehensive documentation of network assets and those in the operational pipeline is the main emphasis of this Function. It requires organizations to understand the risk posed by systems, people, data, services, and other assets.
Learn moreProtect (PR)
Safeguarding assets from cybersecurity attacks is the aim of this Function. It also helps to contain the impact radius of a possible cybersecurity attack.
Learn moreDetect (DE)
This Function requires the implementation of monitoring procedures and systems in order to identify attacks. Using SIEM solutions integrated with anomaly detection and automated response capabilities can help discover threats and respond promptly.
Respond (RS)
This Function neutralizes a cybersecurity incident by limiting and minimizing its impact. Attack action plans are put into force, and response teams are formed in accordance with the threats that have been recognized.
Recover (RC)
The Recover Function helps you promptly get back to the normal course of business. This lessens the impact of a cyberattack.
NIST CSF Core Categories and Subcategories
Each of the six Functions has several Categories, which in turn have several Subcategories. You can think of the Categories as requirements of the NIST CSF. The subcategories are the security-based outcomes that organizations can choose from.
| Function | Category | Category identifier |
|---|---|---|
| Govern | Organizational Context | GV.OC |
| Risk management strategy | GV.RM | |
| Roles, Responsibilities, and Authorities | GV.RR | |
| Policy | GV.PO | |
| Oversight | GV.OV | |
| Cybersecurity Supply Chain Risk Management | GV.SC | |
| Identify | Asset Management | ID.AM |
| Risk Assessment | ID.RA | |
| Improvement | ID.IM | |
| Protect | Identity Management, Authentication, and Access Control | PR.AA |
| Awareness and Training | PR.AT | |
| Data Security | PR.DS | |
| Platform Security | PR.PS | |
| Technology Infrastructure Resilience | PR.IR | |
| Detect | Continuous Monitoring | DE.CM |
| Adverse Event Analysis | DE.AE | |
| Respond | Incident Management | RS.MA |
| Incident Analysis | RS.AN | |
| Incident Response Reporting and Communication | RS.CO | |
| Incident Mitigation | RS.MI | |
| Recover | Incident Recovery Plan Execution | RC.RP |
| Incident Recovery Communication | RC.CO |
How to implement NIST CSF in your organization?
Do you want to start implementing NIST CSF in your organization? Here's a step-by-step breakdown on how. Compliance with the NIST CSF requires a methodical approach that is customized to the unique requirements and risk profile of a company.
Step 1: Familiarize with NIST CSF 2.0 updates.
- Understand the new Functions, Categories, and enhancements introduced in the NIST CSF. Identify how these changes impact your current cybersecurity policies, processes, and controls.
Step 2: Secure executive buy-in and form a team.
- Obtain commitment from executive leadership to allocate the necessary resources, budget, and support for implementation.
- Assemble a cross-functional team comprising members from IT, cybersecurity, legal, compliance, and other relevant departments to lead the implementation process.
Step 3: Conduct a current state assessment
- Perform a gap analysis comparing your current cybersecurity practices to the NIST CSF requirements.
Step 4: Define implementation scope and objectives
- Decide the scope of NIST CSF implementation: Is it for the entire organization or specific departments or systems?
- Define clear objectives for what you aim to achieve with the NIST CSF implementation, such as improving threat detection, enhancing incident response, or meeting compliance requirements.
Step 5: Develop a customized NIST CSF Profile
- Create a NIST CSF profile tailored to your organization’s specific risk environment, business needs, and regulatory requirements.
- Map your organization’s current and desired cybersecurity practices to the NIST CSF core Functions and their associated Categories and Subcategories.
Step 6: Plan and prioritize implementation
- Create a detailed roadmap outlining the steps, timeline, resources, and milestones for implementation. Focus first on mitigating high-risk areas and enhancing critical cybersecurity capabilities.
Step 7: Integrate with existing cybersecurity frameworks
- Integrate NIST CSF with other existing cybersecurity frameworks, standards, or compliance requirements (e.g., ISO 27001, HIPAA) to streamline efforts and ensure consistency.
Step 8: Prepare for external audits and assessments
- Perform internal audits to assess compliance with NIST CSF and identify gaps before any external assessments.
- Conduct external audits or assessments to validate your compliance with NIST CSF and demonstrate your organization’s commitment to cybersecurity.
NIST CSF Implementation Tiers
Implementation Tiers show the level to which an organization follows the framework's features in its cybersecurity program. It facilitates understanding the range of risk-management strategies based on the current established cybersecurity procedures.
Tiers can help enhance the cybersecurity posture of an organization. For example, they can be used to measure internal communications for a company-wide strategy for controlling cybersecurity threats. When there are more requirements or dangers, or when a cost-benefit analysis shows that reducing negative cybersecurity risks is both achievable and economical, moving up the Tiers is recommended. The different Implementation Tiers along with their descriptions are shown in the table below.
| Tier 1: Partial | Tier 2: Risk informed | Tier 3: Repeatable | Tier 4: Adaptive |
|---|---|---|---|
| Inconsistent, ineffective, and reactive risk management techniques that don't fully consider cybersecurity threats. | There is a certain degree of knowledge regarding cybersecurity threats, but there hasn't been much risk to the organizational management program development. | An organization-wide cybersecurity risk management program that is uniform and has procedures in place to adapt to shifting threat conditions. | An intelligent reaction system with the ability to efficiently enhance its risk management strategy using historical data and forecast indications. Cybersecurity risk management is integrated into company culture and budgetary choices in adaptive companies. |
NIST Compliance Checklist
Non-compliance to NIST CSF can be avoided to a major extent by following certain guidelines and best practices. Here is a checklist of strategies that can help your organization strengthen its cybersecurity posture:
- Ensure cybersecurity is considered as a built-in culture and top-down approach from top management, so strategies are designed accordingly.
- Make sure that antivirus and endpoint protection software is installed on all devices and is updated on a regular basis to guard against malware and other harmful threats.
- Identify and address vulnerabilities in software, systems, and network infrastructure, and implement frequent vulnerability assessments and scans.
- Enable logging and tracking of system modifications, file access, and logins to identify and handle unauthorized or suspect activity.
- Adopt a Zero Trust strategy for network security, where access is only allowed based on stringent permission and authentication procedures, independent of the user's location within or outside the corporate network boundary.
- Develop and test incident response and recovery procedures to guarantee that the company can respond to and recover from cybersecurity issues with little impact on business operations.
- Create a patch management procedure to systematically find, evaluate, and update software and systems with security patches to fix known vulnerabilities.
- Use DLP technologies to track, identify, and stop sensitive data from being shared or sent without authorization, both internally and externally.
Use cases
Collect and analyze logs from various sources in your environment, including end-user devices, and gain insights in the form of graphs and intuitive reports that help spot security threats. (Helps with ID.RA-03, PR.PS-04, DE.CM-01)
Identify unusual file or data accesses, cut down malicious communications from command and control servers, and prevent data from being exfiltrated. (Helps with PR.DS)
Leverage STIX/TAXII format threat feeds to discover malicious IPs, domains, and URLs through threat intelligence. (Helps with ID.RA-02)
Non-compliance implications of NIST CSF
Failure to adhere to the NIST CSF places businesses that collaborate with federal agencies at the risk of losing federal contracts or facing penalties under the Federal Acquisition Regulation. In addition, it may result in baseless litigation and unfavorable public opinion, which might be harmful to marketing and upcoming contract negotiations. Furthermore, the agency may be subject to both direct and indirect repercussions, including termination of the contract, imprisonment, dismissal for negligence, or dissolution of the concerned department. The repercussions will be dependent on the regulatory body, the relevance of the data handled, and the probable effects of the breach.



