What is a pass-the-hash cyberattack?
Pass-the-hash is an attack technique attackers use to obtain the NTLM or LANMAN hash of a user's password instead of the plain text password so they can use it to dupe an authentication system. This strategy, highly prevalent on Windows systems, is one of the successful lateral movement techniques.
However, if the user's password has been changed, then the stolen hash cannot be used. Therefore, best security practices insist upon changing passwords at least once every 45 to 60 days.
How does a pass-the-hash attack happen?
In Windows, the password hashes are stored in Security Accounts Manager (SAM), Local Security Authority Subsystem process memory and a Ntds.dit database in Active Directory. Attackers steal the hashes from any of these places using these techniques:
- With physical access to the system, they can boot the system drive into a different OS and copy the SAM file.
- Harvest password hashes by running hash-dumping tools by establishing a remote connection
- Sniff out password hashes using malicious programs as they traverse the network during the authentication process
- Some of the hash-dumping tools that are frequently used include Mimikatz, iam.exe, genhash.exe and others. pwdump.exe is a Windows program that can be exploited to obtain the password hashes.
How does pass the hash attack work?
Step 1: Attackers get into the network through a phishing campaign. After breaching the system, the malicious tools mentioned earlier are installed to harvest the password hashes from the local systems.
Step 2: Using the harvested user account and password hashes, the attackers authenticate to other systems and resources to which the account has access to achieve lateral movement within the network.
Pass-the-hash attacks are more damaging when the compromised user account has been enabled with a single sign-on (SSO) option for many business apps.
Detection mechanism
Pass the hash attacks can be detected by analyzing and correlating log data with user behavior anomalies.
To detect the attack in your network, you should configure your security tool to detect this criteria:
Source Host Event ID: 4624 An account was successfully logged on
Logon type: 9
Authentication package: Negotiate
Logon process: seclogo
Sysmon event ID: 10
Target Host
Event ID: 4768 A Kerberos authentication ticket (TGT) was requested
Event ID: 4769 A Kerberos service ticket was requested
To enable logging for the Event IDs indicated above, you'll need to configure the appropriate audit policies in the Group Policy Management Console or the Local Security Policy settings:
| Event ID | Event description | Audit policy category | Audit policy name |
|---|---|---|---|
| 4624 | An account was successfully logged on | Logon/logoff | Audit Logon |
| 4768 | A Kerberos authentication ticket (TGT) was requested | Account Logon | Audit Kerberos Authentication Service |
| 4769 | A Kerberos service ticket was requested | Account Logon | Audit Kerberos Service Ticket Operations |
To enable these policies, follow the steps mentioned below:
- Open the Group Policy Management Console or the Local Security Policy settings.
- Navigate to Computer Configuration > Windows Settings > Security Settings > Advanced Audit Policy Configuration > Audit Policies.
- Locate the policies mentioned.
- Check Configure the following audit events, enable both Success and Failure, and click OK.
- Apply the changes, and the selected events will now be logged in the Security event log.
How to minimize the impact of pass the hash attack?
- When you've enabled SSO, make sure that you also implement multi-factor authentication to safeguard the system. This way, even if the credential is compromised, the attacker will be unable to access the data.
- Implement principle of least privilege by creating separate Domain Admin and standard accounts for day-to-day work.
- Enforce password change policies frequently.
Detect and mitigate pass-the-hash-attack using Log360
Learn how to set up correlation rules, alerts, incident workflow and customize them to detect and remediate pass the hash attack.
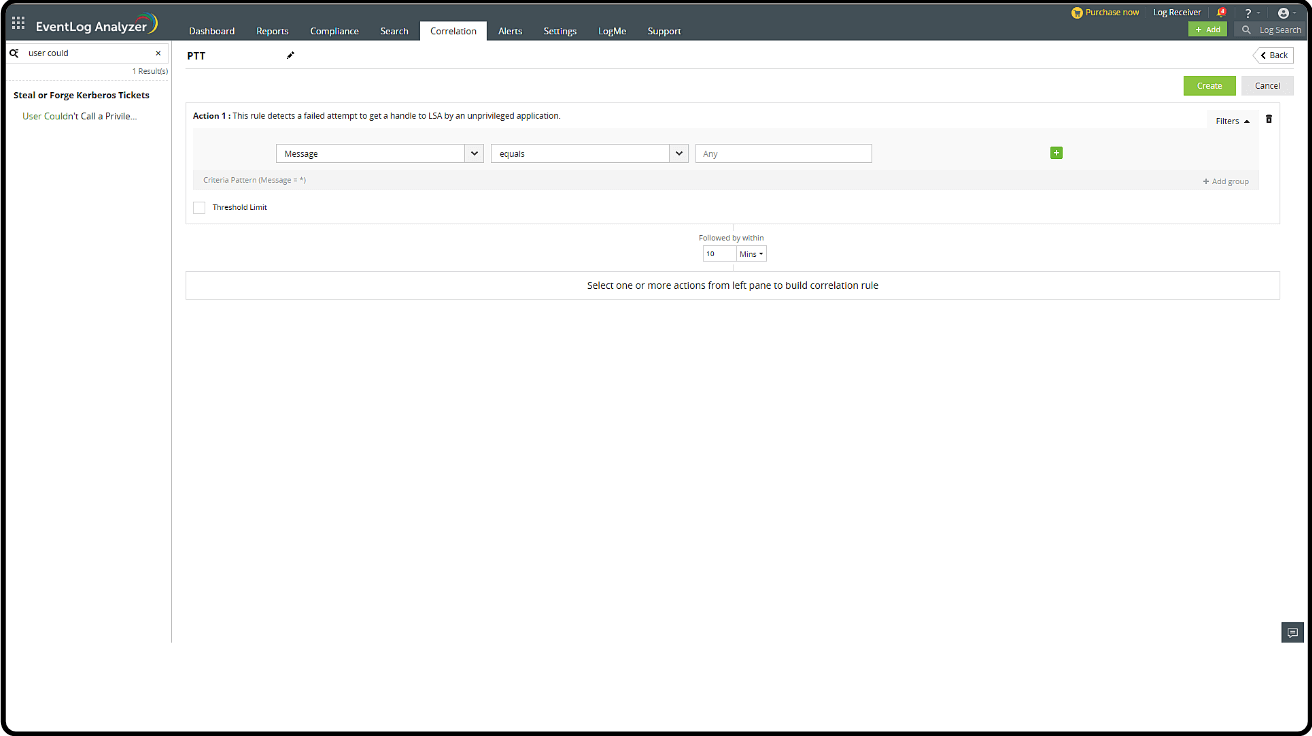
Detection through correlation
These are the pass-the-hash attack action sequence and associated event IDs:
- Event ID 10 (event generated by sysmon): Indicates that a process has accessed another process
- Event ID 4624: An account was successfully logged on
- Event ID 4672: Special privileges assigned to a new logon
A widely used method for detecting pass-the-hash attacks involve correlating and monitoring Event IDs 10, 4624, and 4672.
Real-time alerts
Adding alerts and a Workflow:
- Creating an Alert Profile with the Correlation Rule
- Adding a Workflow for the Alert Profile
Creating an Alert Profile:
- Go to the Log360 console > SIEM > Alerts > click the settings icon in the top-right corner > Manage Profiles > Correlation Alert Profiles > click the search icon and select the Pass the Hash rule that was created > click Configure.
- Select the severity level and configure the notification settings to receive alerts.

Adding a Workflow for the Alert Profile:
Step 1: Creating a Workflow
- In the Alerts tab, click the settings icon on the top-right corner of the page.
- Select Workflow.
- Click Create Workflow on the top-right corner.
- You can drag and drop blocks from the left panel to create a new workflow.

Step 2: Add the Workflow for the Alert Profile
- In the Alerts tab, click the settings icon on the top-right corner of the page.
- Select Manage Profiles.
- Navigate to Correlation Alert Profiles.
- In the newly created Pass the Hash attack alert profile, click Configure.
- Navigate to Workflow tab under Alert Notification.
- Click Enable Workflow.
- Select Modify Inputs if there are any fields that need to be modified.
- Once the fields are updated, click Save and Update in the main page.
These actions can help contain the threat until a security admin can take over and perform a deeper investigation and remediation.
- Send mail and SMS: Notify the security admin about the potential pass-the-hash attack.
- Disable AD user: Temporarily disable the affected user account in Active Directory to prevent further unauthorized access.
- Deny inbound rule and outbound rule: Update firewall rules to deny both inbound and outbound traffic for the compromised system to limit potential lateral movement, command and control communications, and data exfiltration.
- Windows log off: Log off any active sessions associated with the compromised user account to disrupt the attacker's access.
- Write to file: Log all relevant information about the detected pass-the-hash attack, including affected systems, user accounts, and suspicious activities.
- Forward logs: Forward security logs related to the incident to Log360 for further analysis.


Investigation through reports
Predefined reports
- In the Log360 console, select Reports.
- Navigate to MITRE ATT&CK in the drop-down available in the top-left. Select Defense Evasion. Search for Pass the Hash Activity with the search option in the LHS.

Explore a SIEM solution that protects you from cyber threats.
Log360 can combat sophisticated attacks like PtH with a suite of security features like:
- User activity monitoring
- Privileged access tracking
- ML-based anomaly detection
What's next?
Implement defensive strategies and incident response measures using the advanced security features of Log360.
- What is a pass-the-hash cyberattack?
- How does a pass-the-hash attack happen?
- How does pass the hash attack work?
- Detection mechanism
- How to minimize the impact of pass the hash attack?
- Detect and mitigate pass-the-hash-attack using Log360