ManageEngine Vulnerability Manager Plus is an Enterprise vulnerability management software that helps you scan, assess, prioritize and remediate vulnerabilities in your network endpoints. It comprises of features like vulnerability scanning and vulnerability assessment, automated patch management, CIS compliance, security configuration management, zero-day vulnerability mitigation, high-risk software audit and web server hardening.
The following guide will help you understand the process of vulnerability management with the help of an architecture diagram.
The Security Research Team at Zoho Corp. plays a vital role in maintaining cybersecurity as they . They continuously probe the internet to:
Then the authenticity and functional correctness of the patches are tested and correlated with the corresponding vulnerability it addresses.
The Central Vulnerability Database hosted at the Zohocorp site gets updated periodically with the latest details of
The Central Vulnerability Database is a portal in the Zoho Corp. site, which is constantly updated with the latest information that serves as the baseline for vulnerability management in the customer organization.
IT administrators or network security teams need the following components to perform vulnerability management in the enterprise:
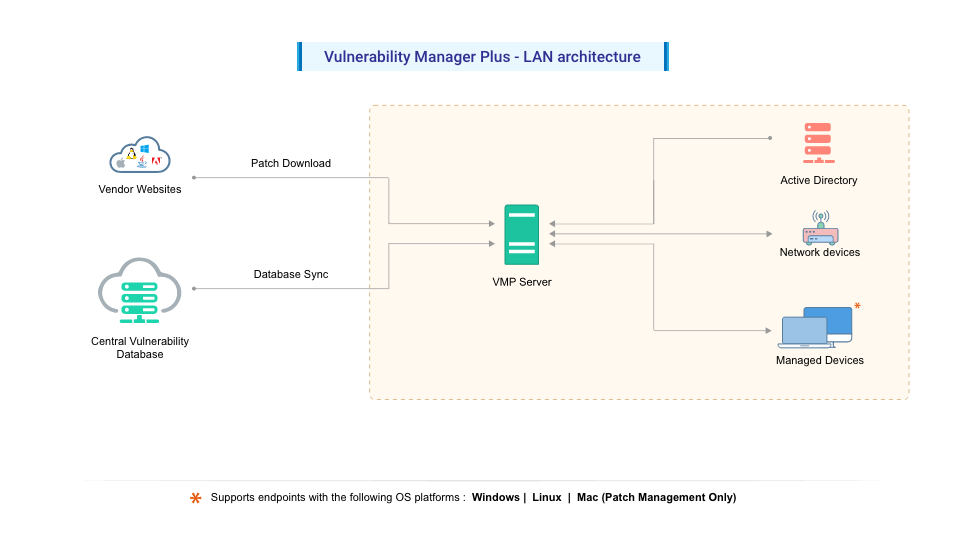
The Vulnerability Manager Plus Server helps you to centrally perform all the vulnerability management and compliance tasks in your network endpoints. Some of the tasks include the following:
Any of the Windows computers in your network with the requirements mentioned here can be hosted as your Vulnerability Manager Plus Server. This Vulnerability Manager Plus Server at the customer site subscribes to the Central Vulnerability Database, from which it synchronizes the latest information on threats, patches, vulnerabilities, and compliance policies. Patches are downloaded directly from vendor sites and stored centrally in the server's patch store and will be replicated to your network endpoints to conserve bandwidth.
Ports utilized for vulnerability management:
| Port | Purpose | Type | Connection |
|---|---|---|---|
| 8020 | Agent/Distribution Server to VMP Server | HTTP | Inbound to server |
| 8383 | Agent/Distribution Server to VMP Server | HTTPS | Inbound to server |
| 8027 | Agent Server communication | TCP | Inbound to server |
Ports utilized for Network Devices:
| Port | Purpose | Type | Connection |
|---|---|---|---|
| 161 | VMP Server to Network Device (SNMP) | TCP | Inbound to Network Device |
| 22 | VMP Server to Network Device (SSH) | TCP | Inbound to Network Device |
Distribution Server
| Port | Purpose | Type | Connection |
|---|---|---|---|
| 8384 | Agent to Distribution Server | HTTPS | Inbound to Distribution Server |
| 8021 | Agent to Distribution Server | HTTP | Inbound to Distribution Server |
To perform Vulnerability scanning and management, a lightweight agent will be installed by the server in your managed endpoints. The agent contacts the server every 90 minutes to get the data to carry out the tasks delegated by the server. It returns back the result to the server after completion of the task. The agent also maintains a continuous thin connection with the server in order to perform on-demand tasks.
After server installation, network devices can be discovered and added from the server console. Once the vulnerability database sync is complete, agentless scanning of network devices occurs for the credential mapped devices, enabling the detection of network devices' firmware vulnerabilities.
The web console is a graphical user interface to access the server and perform vulnerability management tasks. It empowers users with a single pane view to perform all the vulnerability management tasks from anywhere, anytime.