- HOME
- Endpoint Management Analytics
- The IT admin's guide to prioritizing 'at risk' endpoints using vulnerability score
The IT admin's guide to prioritizing 'at risk' endpoints using vulnerability score
- Last Updated: July 1, 2024
- 436 Views
- 3 Min Read

It is a typical Monday workday morning for Jane, a system administrator, who sits in-front of her laptop, with a dozen tabs opened on her browser. As she sips coffee, she starts responding to emails and prepares a to-do list. Amidst the flood of notifications in Jane's inbox is an email to remind her to apply a patch for a vulnerability detected in one of their corporate devices.
Little did Jane know that a minor negligence could cause reputational damage to her organization. Fortunately, the vulnerability was noticed by one of her peers and appropriate patches were applied quickly.
ManageEngine's digital readiness survey says that only 56% of organizations globally have adapted a robust security strategy to protect their endpoints in hybrid environments.
With employees connecting to the company's network from anywhere and using any device, the number of endpoints secured by organizations has increased multifold. Two major problems IT leaders face are,
1. Detecting vulnerabilities among the plethora of devices spread across an organization.
2. Prioritizing vulnerabilities based on imminent threats.
While endpoint management solutions can help detect the threats, troubles arise when teams have to understand and prioritize the threats. Here's how the Asset Vulnerability Score can help. It is a measure of the number of vulnerabilities in an endpoint that makes it susceptible to internal or external threats.
Here's an example: an employee's desktop, which has Windows OS, is missing four critical security patches and has two outdated software programs running. The system's vulnerability score is six. Consider another corporate device, an iPhone owned by the same employee that has one prohibited app running. Its vulnerability score will be one. Comparing these two assets, the Windows laptop, with a vulnerability score of six is more exploitable and needs to be secured first.
Asset vulnerabilities can be customized to suit an organization's security requirements. An organization can choose to assign a higher weightage to missing security patches compared to prohibited software installations, while another can assign higher weightage to password compliance using MFA compared to the use of blacklisted apps.
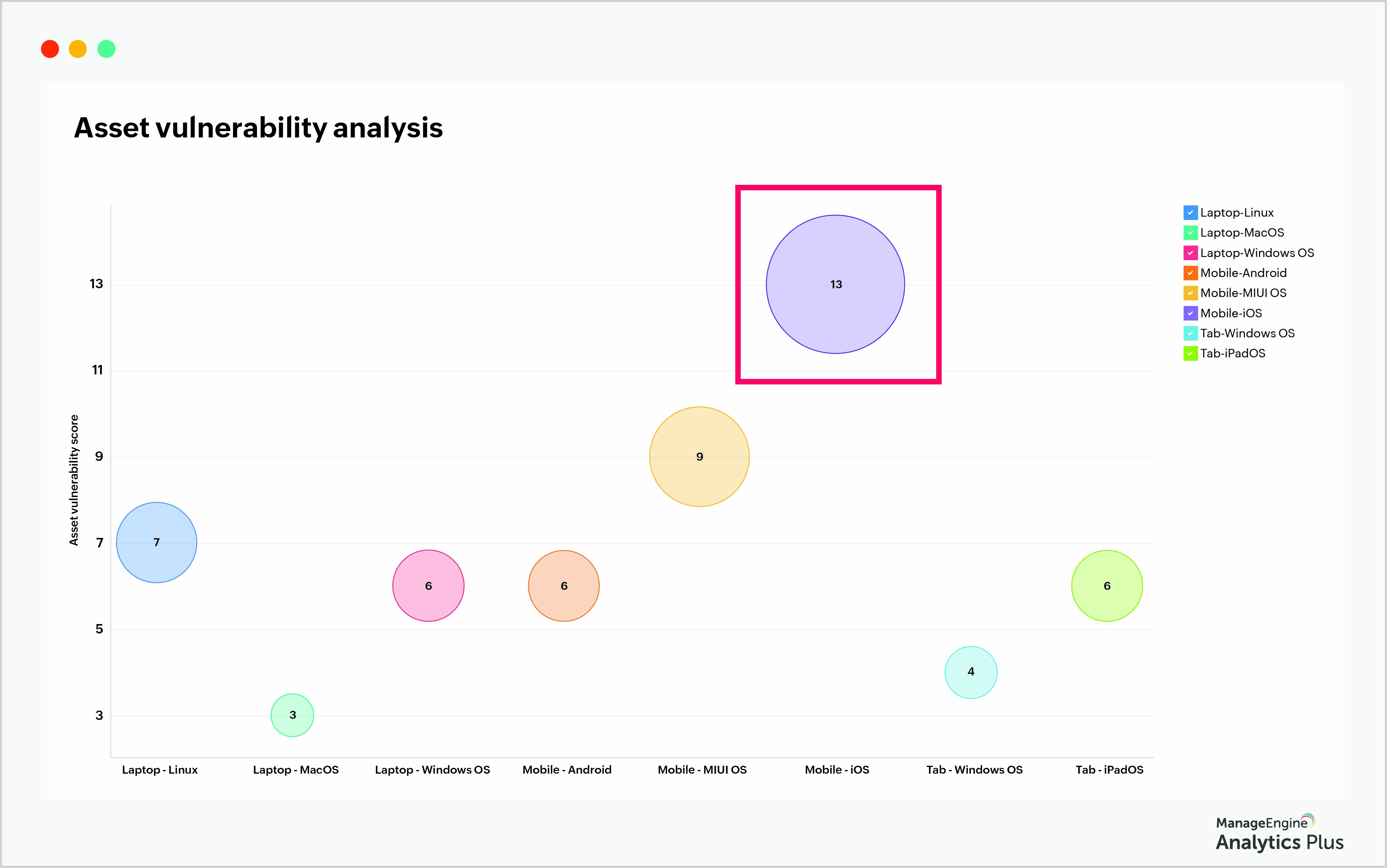
The report above shows the vulnerability scores of corporate devices at an organization. The size of the bubble indicates the vulnerability score. Quantifying the asset vulnerabilities helps IT teams prioritize and make better decisions. You can infer from the report that a corporate iPhone has a vulnerability score of 13 and naturally, this iPhone needs to be secured first.
Let's look at another version of the same report. Earlier, we viewed the vulnerability score of individual assets. Now, we receive an overall view of the number of type of vulnerable assets by categorizing them based on the vulnerability score.
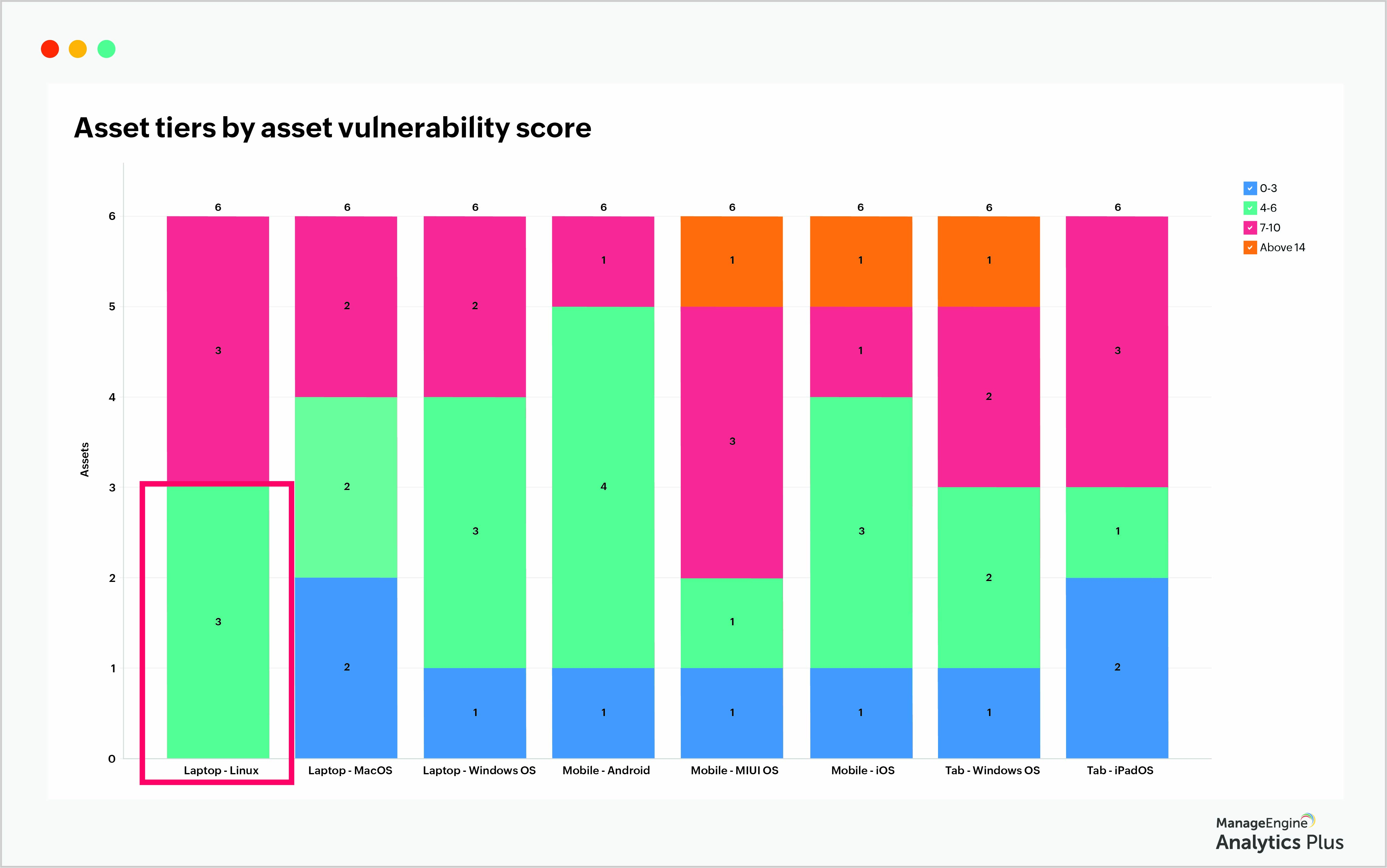
From the report, you can see that the assets are grouped into different tiers depending on their vulnerability scores. This approach is beneficial when there are many devices to maintain.
The report shows that there are three Linux laptops with vulnerability score ranging from seven to 10. The priority is high, which means that these laptops should be safe-guarded immediately.
Also, there is a Windows tablet with a vulnerability score of more than 14, which falls under the critical category. Dividing many assets into several categories will help you prioritize the ones that are critical and need immediate attention.
These reports are generated using ManageEngine Analytics Plus, an AI-enabled analytics solution custom built for IT users.
Click here to check out more interesting reports and dashboards built using Analytics Plus.
Schedule a personalized demo of Analytics Plus today with one of our solution experts who can answer your product-related questions. Or try Analytics Plus for free to explore on your own this powerful business intelligence and IT analytics application.
 Sailakshmi
SailakshmiSailakshmi is an IT solutions expert at ManageEngine. Her focus is on understanding IT analytics and reporting requirements of organizations, and facilitating blended analytics programs to help clients gain intelligent business insights. She currently spearheads marketing activities for ManageEngine's advanced analytics platform, Analytics Plus.





