- HOME
- More
- Security Analytics
- Fortify your organization against zero-day attacks by using analytics
Fortify your organization against zero-day attacks by using analytics
- Last Updated: July 1, 2024
- 991 Views
- 6 Min Read

Imagine bringing home your favorite pastry, only to lose it to a stray cat that had gotten into your home through a broken window—one that you weren't even aware was broken in the first place. Now replace the pastry with your data, the cat with an attacker, and the broken window with an application, and you have the perfect zero-day attack.
According to MIT Technology Review, the record for the highest number of zero-day attacks in a year was broken in 2021. Ponemon Institute found that 80% of successful data breaches in 2019 were a result of zero-day attacks. However, these stats don't necessarily mean that zero-day attacks are unavoidable. You can combat this threat by following certain best practices. In this blog, we'll discuss zero-day attacks in detail and discover ways to combat them effectively using security analytics.
What are zero-day vulnerabilities, exploits, and attacks?
The term zero-day means that security teams are unaware of a software vulnerability and thus have had zero days to work on a patch to secure the vulnerability.
- A zero-day vulnerability is a software security flaw that gets discovered by attackers before the software vendor or organization. Since the vulnerability is unknown to the organization and vendor, no patch is available, which means attackers are more likely to succeed in their attempts to exploit this vulnerability.
- A zero-day exploit is a technique that's used by attackers to take advantage of zero-day vulnerabilities. These exploits are used by malicious hackers to attack an organization's systems, which have an unknown number of flaws.
- A zero-day attack is an actual attack carried out by hackers. In the attack, a zero-day vulnerability is exploited to steal data from an organization.
How do zero-day attacks work?
There are four stages in a zero-day attack:
Stage 1: Attackers discover an exploitable vulnerability in software, of which, the organization using the software and the developers who built the software are both unaware.
Stage 2: The attacker then creates an exploit code to take advantage of this flaw. The vulnerability can be exploited via various methods, such as using zero-day malware that contains exploits, phishing emails that contain malicious attachments, or links that have exploit malware encoded in them. In this step, the attacker gains entry into the organization's network and systems by exploiting the vulnerability.
Stage 3: The attacker then implements the exploit code to take advantage of the zero-day vulnerability. At this stage, the vulnerability is still unknown to the software vendor and the organization. This means that the vulnerability is still open and available for further exploits.
Stage 4: In the last step, either the security team detects a zero-day attack or the vulnerability is exposed to the world by the attacker. However, an immediate fix is not available as the vulnerability remained unknown to the developers until this stage.
Stage 3 is considered to be the most harmful to an organization. However, it is critical to remember that the systems are vulnerable and exploitable at all stages.
Protecting your organization from zero-day attacks
Zero-day attacks occur on day zero, meaning organizations have little to no time to respond to them. Also, cybercriminals now use sophisticated attack and evasion techniques to sneak into an organization's secure perimeter. Analytics can help you proactively defend yourself from such attacks and, in some cases, detect them preemptively.
Here are four ways analytics can help you tackle zero-day attacks:
1. Keeping track of vulnerabilities
Zero-day attacks are challenging to prevent. However, you can reduce your risk by regularly evaluating your endpoint security. Keeping track of vulnerabilities gives you a reality check of your current security status, prompting remediation. Vulnerability assessments help organizations detect easily remediable vulnerabilities, such as missing security patches, the use of prohibited applications, configuration mismatches, and non-adherence to password protocols. Analyzing the known vulnerabilities enables you to prioritize fixing them and preventing them from becoming entry points for attacks.
The sample report below shows the vulnerability assessment results of endpoints in an organization. As a general practice, you can assume that you have as many unknown vulnerabilities as known vulnerabilities. This will help you prioritize and secure known vulnerabilities first, then kick-start your hunt for unknown vulnerabilities, thereby significantly reducing the possibility of zero-day attacks.
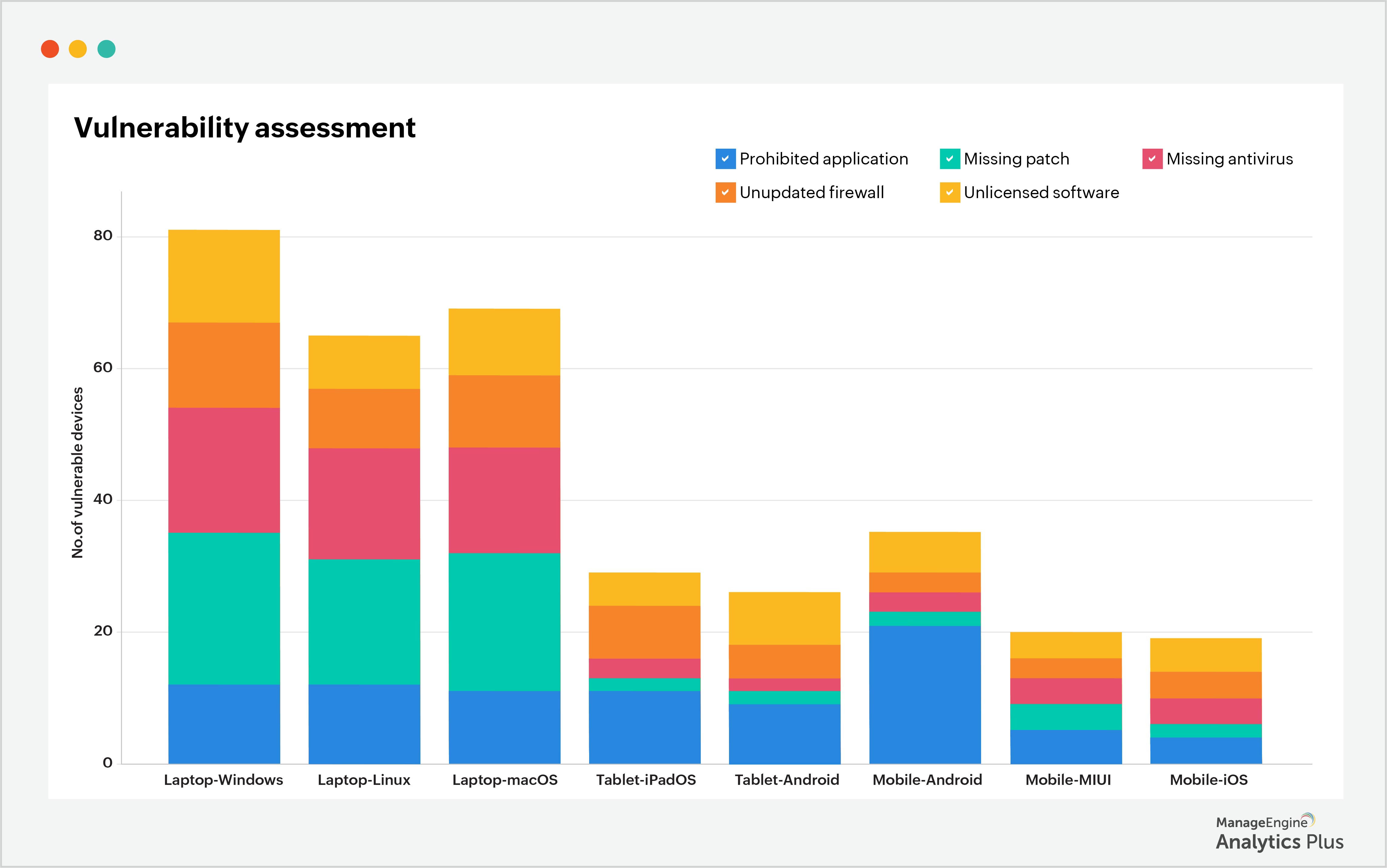
In order to understand and prioritize vulnerabilities, it's critical that your endpoints are in constant, or at least frequent, contact with the Endpoint Central agent. This will ensure that you're notified of changes or vulnerabilities that crop up now and then. The longer that endpoints go without contacting the Endpoint Central agent, the greater the chance for security teams to miss a vulnerability, and the greater the chance of a data breach occurring through that vulnerability. The report below shows the distribution of endpoints based on when they last contacted the Endpoint Central agent.
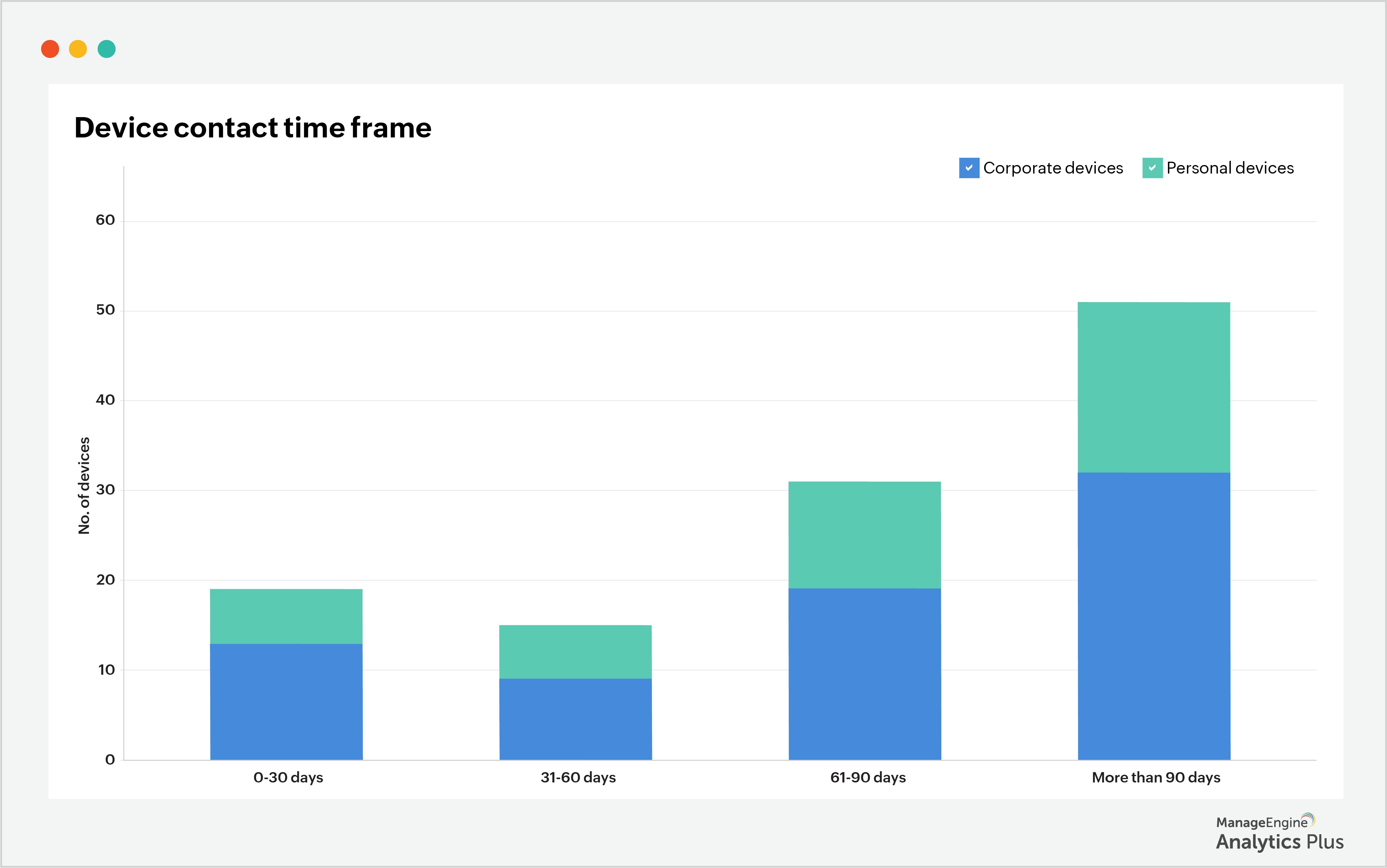
This report shows that many endpoints have been out of contact with the Endpoint Central agent for over 90 days. The maximum acceptable time frame for a device to go out of contact with the agent is 30 days. Beyond this period, security teams should reach out to the device owner and connect with the device.
2. Ensuring timely patch deployment
Software developers are in an uphill battle to provide timely security patches that can defend their software against various threats. It is then the organization's responsibility to apply these patches on time and secure its data. However, this requires an up-to-date record of assets and devices that need to be patched.
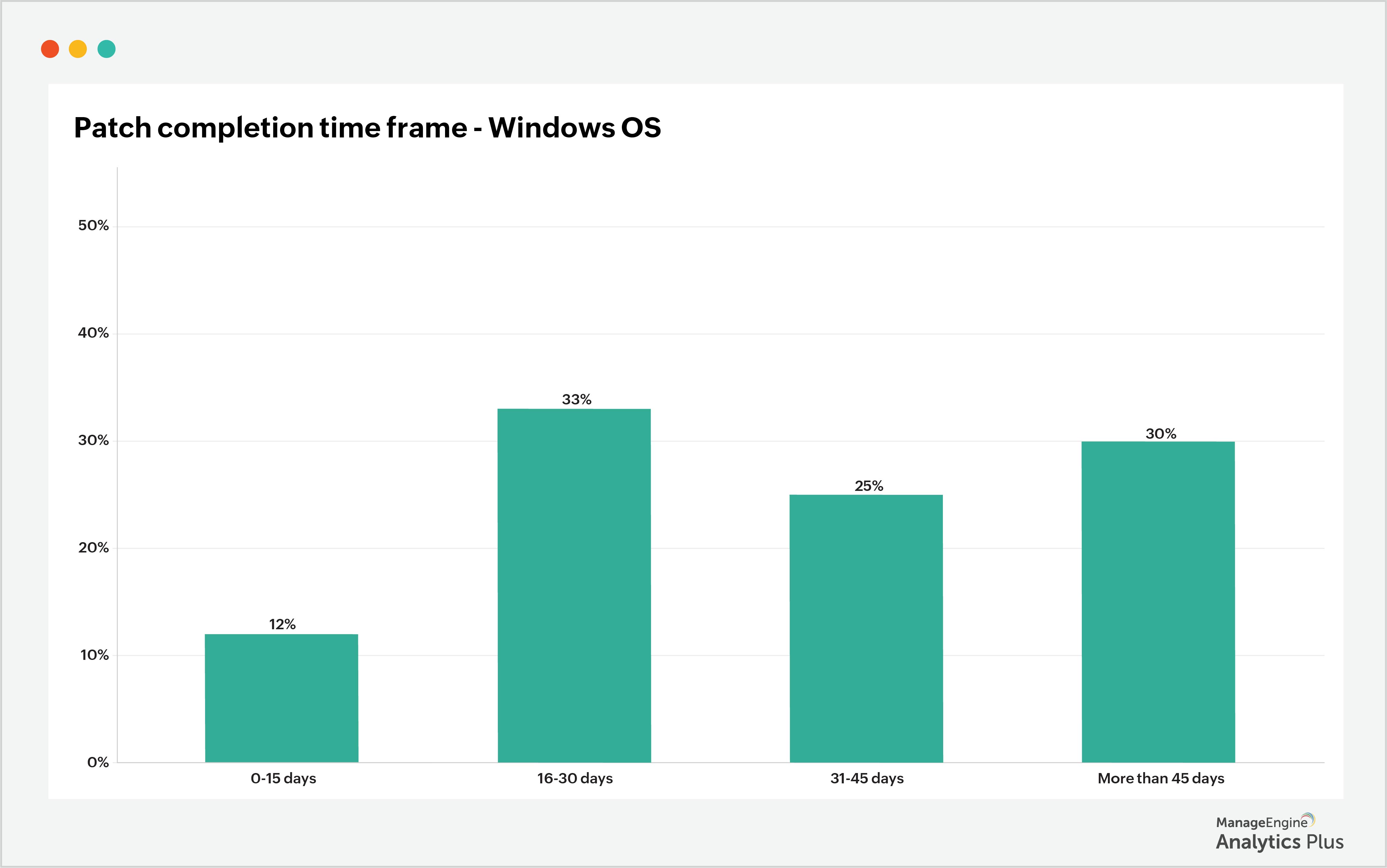
The report below illustrates the percentages of patches that have been applied within 15 days of their release, 16-30 days after release, 31-45 days after release, and more than 45 days after the date of the patch release for a CRM software. According to the report, only 12% of vulnerable devices were patched within 15 days, and 30% of devices were not patched until more than 45 days after the patch was released. This highlights a serious problem with patch management. At this stage, it's critical that patch application is automated so that devices are patched as soon as patches are released.
3. Watching out for zero-day attacks when there are spikes in network traffic
Watching out for surges in network traffic is a good way to catch possible data theft. A sudden increase in inbound traffic could hint at unauthorized users trying to access your data, while a sudden increase in outbound traffic could hint at your data being moved. The report below correlates in and out traffic with zero-day attacks. It shows that on the day of the attack, the network traffic is nearly five times more than the normal amount.
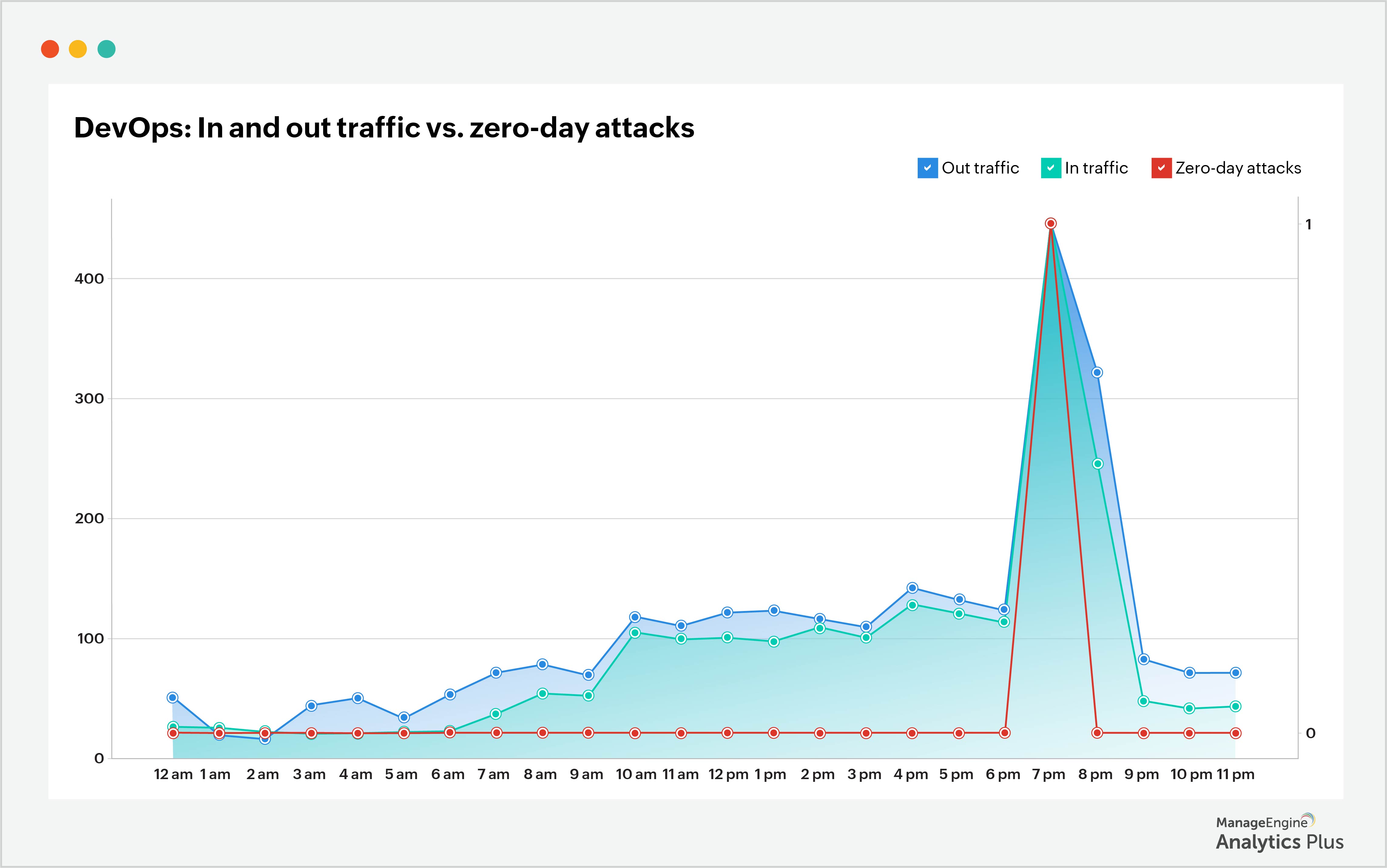
Though not all network traffic surges are the result of security attacks, an organization must remain vigilant about risks due to spikes in network traffic and must defend its valuable data.
4. Monitoring privileged accounts and their access logs
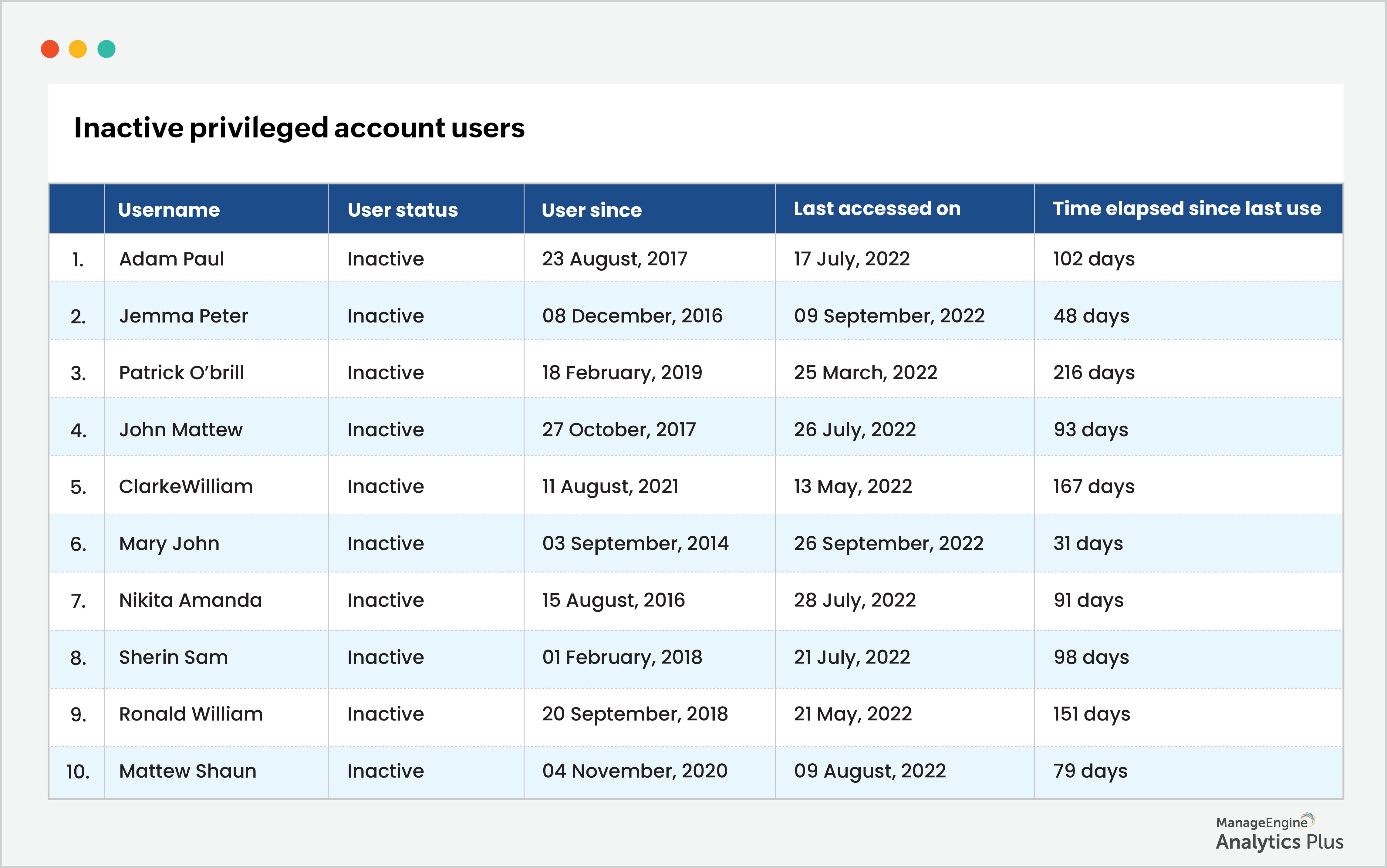
Spear phishing of privileged accounts is one of the most prevalent techniques used in zero-day attacks. To ensure your organization's safety against such attacks, keep tabs on who has access to privileged accounts and hand out access to privileged accounts on a least-privilege basis. First, filter out inactive users (users who haven't accessed their accounts in over 90 days) and revoke their access. Here's a report that shows the list of inactive users, their last date of access to a privileged account, and the time that has elapsed since the last access:
Another helpful strategy for securing privileged accounts is to keep tabs on the number of operations each performs, particularly for highly active user accounts. Create thresholds for each privileged account based on the maximum number of operations performed and get alerts when these thresholds are exceeded.
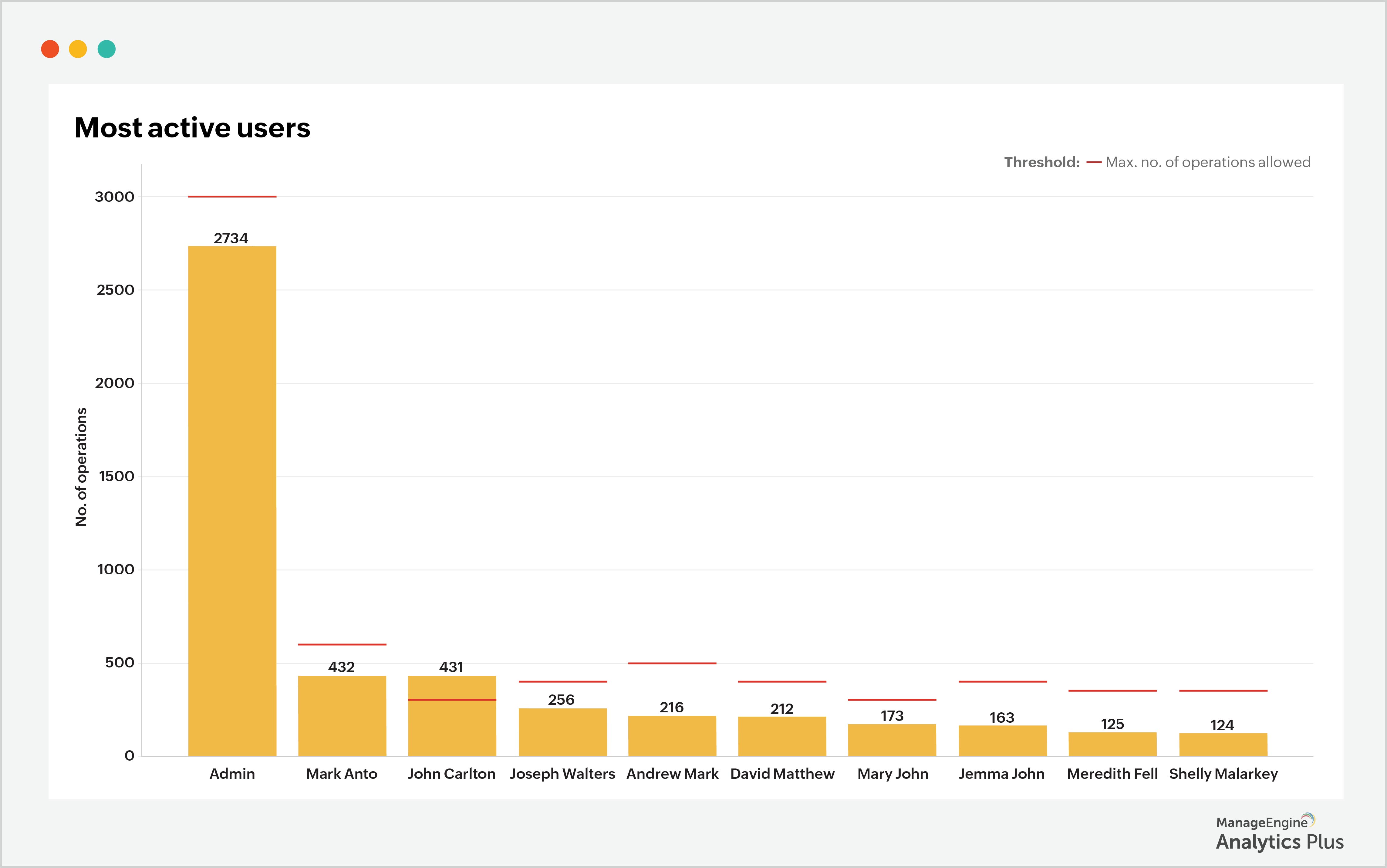
The sample report below lists the top 10 privileged accounts according to the number of operations they perform. The threshold limit for John Carlton is 300 operations. However, the user exceeded this limit and performed 431 operations. This could potentially be a sign of an attacker who gained access to the user's privileged account, which warrants further investigation.
Key takeaways
Zero-day attacks are one of the most potent security threats to an organization due to the uncertainty that is the very essence of zero-day. It may not be possible to immunize your organization against zero-day threats completely. However, it's not difficult to prepare to tackle them.
Start with simple practices such as conducting regular vulnerability assessments, patching all vulnerabilities as soon as possible, and keeping an eye on the access attempts of privileged accounts to catch anomalies. Advanced analytics for endpoint management and privileged account management can help you stay abreast of any changes to your security stance and can suggest steps to protect yourself from security threats.
The reports shown in this blog were built using Analytics Plus, ManageEngine's AI-enabled IT analytics application. If you'd like to create similar reports using your endpoint management data, try Analytics Plus for free.
Talk to our experts to discover all the ways you can leverage analytics to step up your cybersecurity measures.





