- HOME
- More
- Security Analytics
- A 5-step guide to curbing shadow IT with advanced security analytics
A 5-step guide to curbing shadow IT with advanced security analytics
- Last Updated: July 1, 2024
- 663 Views
- 7 Min Read

Sarah, a sales manager for a large corporation, took great care in abiding by the rules and regulations of her organization. One day, she decided to download an application that her organization had not approved, in the hopes that it would make her job easier and faster. The use of such unapproved applications or devices is called shadow IT. Unfortunately for Sarah, she used her corporate email to sign up for the application, which created a loophole for cyberattackers to break into her system and steal confidential information. Sarah's confidential files would have been safe if she hadn't downloaded the prohibited application!
Though shadow IT endangers an organization in many ways, analytics can stop it. In this blog, we'll explore shadow IT in detail, how it impacts an organization, and how analytics can help you combat this menace.
What is shadow IT?
Any application, device, or cloud technology used by employees in an organization without formal or explicit approval from the organization's IT team is called shadow IT. Shadow IT results from one or more of these underlying problems:
- Employees find alternate tools that are more efficient than the ones given to them by their organization. For instance, employees may use WhatsApp to transfer corporate files.
- Employees may be biased due to their familiarity with other devices or software. For instance, an employee using an iPhone might not be comfortable using an Android phone.
- Employees feel the need to off-load work to tools that can automate their tasks. For instance, calendar apps that can send out alerts about events will be preferred over calendar apps that don't have this feature. Alerts eliminate the hassle of constantly checking calendars for meeting updates.
- The approval process is slow or there isn't a proper one in place for introducing new technology or applications as needed.
- There is a lack of support for technology, tools, or applications that are currently in use, prompting employees to try out alternatives.
- The flexibility to work in a hybrid mode results in employees using a mix of corporate and personal devices to fulfill their daily tasks.
How does shadow IT negatively impact an organization?
Shadow IT poses several risks to an organization. While the use of unapproved, un-vetted devices comes with a whole range of security risks, the use of unauthorized cloud storage puts organizational data directly at risk. Unauthorized apps are a tricky subject. Even if some of those apps are encrypted, they could still ask for permission to access stored files, make calls, access device cameras, and access your location. This could expose stored data and other information such as contacts to unwarranted applications.
Here are more reasons why shadow IT is a security hazard for organizations:
1. Reduced visibility and control
When your employees rampantly use shadow IT devices or applications, it means you have zero visibility and control over those devices and apps. With no visibility or control, it's impossible to ensure security for the data stored in those devices or applications.
2. An expanded attack surface
Typically, more devices in an organization mean a greater attack surface for cyberattackers. Shadow IT further compounds this problem by increasing the attack surface, and worse, the IT and SOC teams aren't even aware of its presence. This is because shadow IT hasn't been through the organization's penetration testing, sandbox testing, vulnerability assessments, or security tests that approved devices and apps typically go through.
3. Increased costs
Employees often misunderstand shadow IT as a means to save costs, while in fact, it does the opposite. According to Gartner, 30-40% of IT spending is on shadow IT. Individual teams or groups of employees often spend their allotted IT budget on devices or applications that offer similar functions as approved ones for a variety of reasons, ranging from costs to the perceived efficiency of those tools.
When spending on shadow IT does come to light, organizations have to shell out extra to get employees off of shadow IT and get them back on approved apps or devices. Additionally, shadow IT introduces several security risks that incur additional costs in the forms of damage control and fines, levies, or penalties for noncompliance.
4. Noncompliance
For organizations, it's impossible to produce proof of compliance for devices or applications they aren't even aware of in the first place. The implementation of the GDPR and other international and local privacy laws requires organizations to cyclically review, audit, identify, and disclose the scope and impact of security incidents. Failure to comply with such privacy-first mandates results in fines or restrictions that cost the business more than just money.
Taming the menace of shadow IT with advanced analytics
Despite its scary impact, shadow IT can be easily tracked, prevented, and eventually eliminated from corporate networks. Here are a few ways to do so:
1. Keep unauthorized devices out of your network
The flexibility of the hybrid work model is a major perk. Caution employees to use it prudently. Since the pandemic began, a lot of organizations have adopted the hybrid work model, which has increased the use of personal devices for work. Banning the use of personal and unmanaged devices altogether is not always a realistic solution. It would be more practical to keep an inventory of personal devices connected to your corporate network. Ruthlessly scrutinize the need for personal devices and discourage their use if they are found to be unnecessary.
Below is a report that shows the number of corporate and personal devices used across several departments in an organization. As the report reveals, the Marketing Department uses more personal devices than any of the other departments.
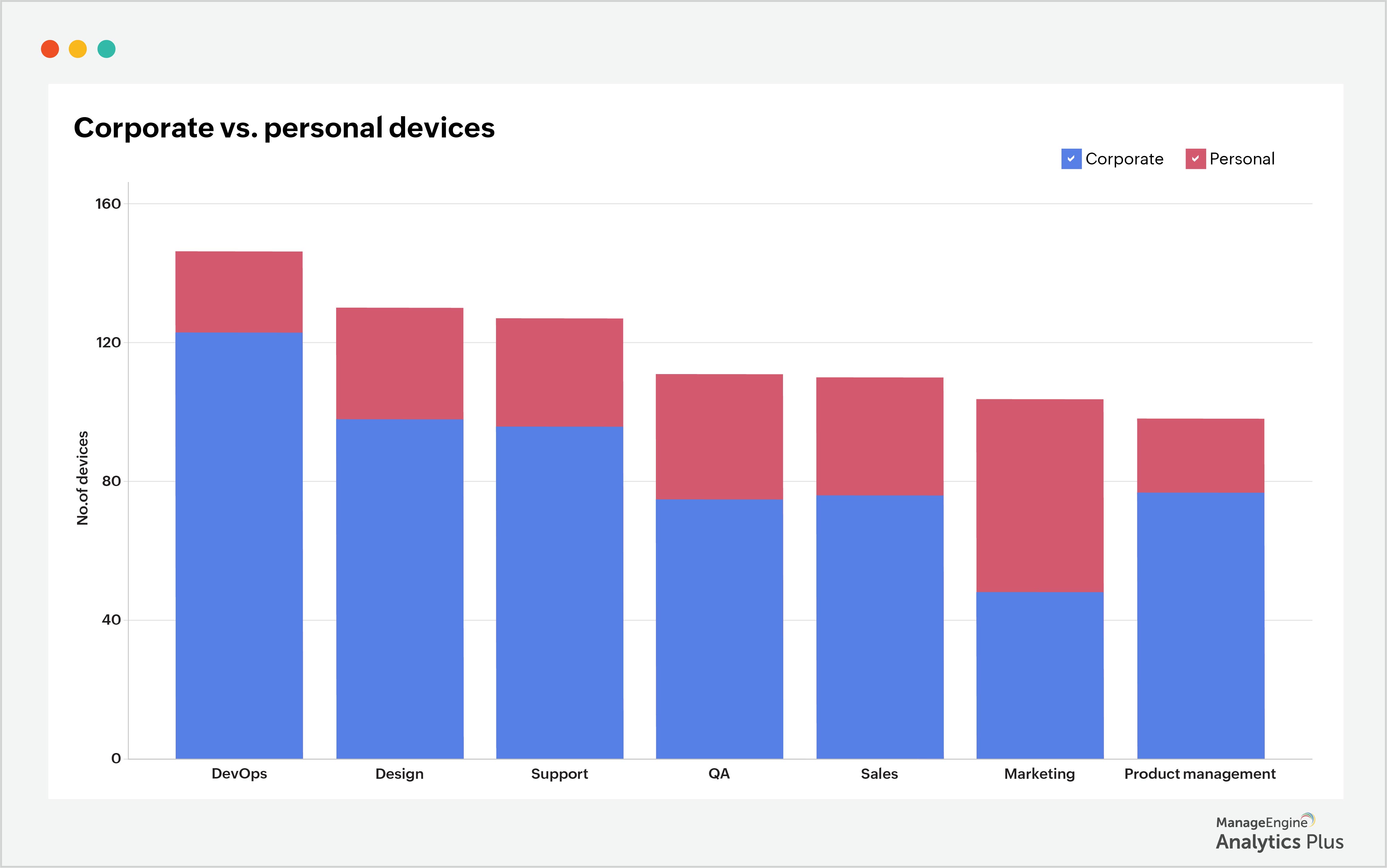
2. Track and manage the use of unauthorized applications
Employees tend to use certain devices such as mobile phones or tablets for personal matters. This means it wouldn't be uncommon to find prohibited applications on corporate phones or tablets. Apps such as Netflix, Amazon Prime Video, Zomato, Dunzo, Flipkart, Tinder, and Spotify are notorious for finding their way onto corporate mobile phones. While these apps don't impact your organization's security directly, it's nevertheless important to monitor their usage. Some of these apps are known to ask permission to perform functions they aren't entitled to, such as a video streaming app seeking permission to view stored files.
To curb this problem, first get visibility into the apps that are used on your corporate devices. Then, classify them as approved, sanctioned, or prohibited. Using these classifications, IT teams can decide whether to support, place restrictions on, or block an app. The sample report below shows the list of prohibited applications installed on an organization's corporate devices.
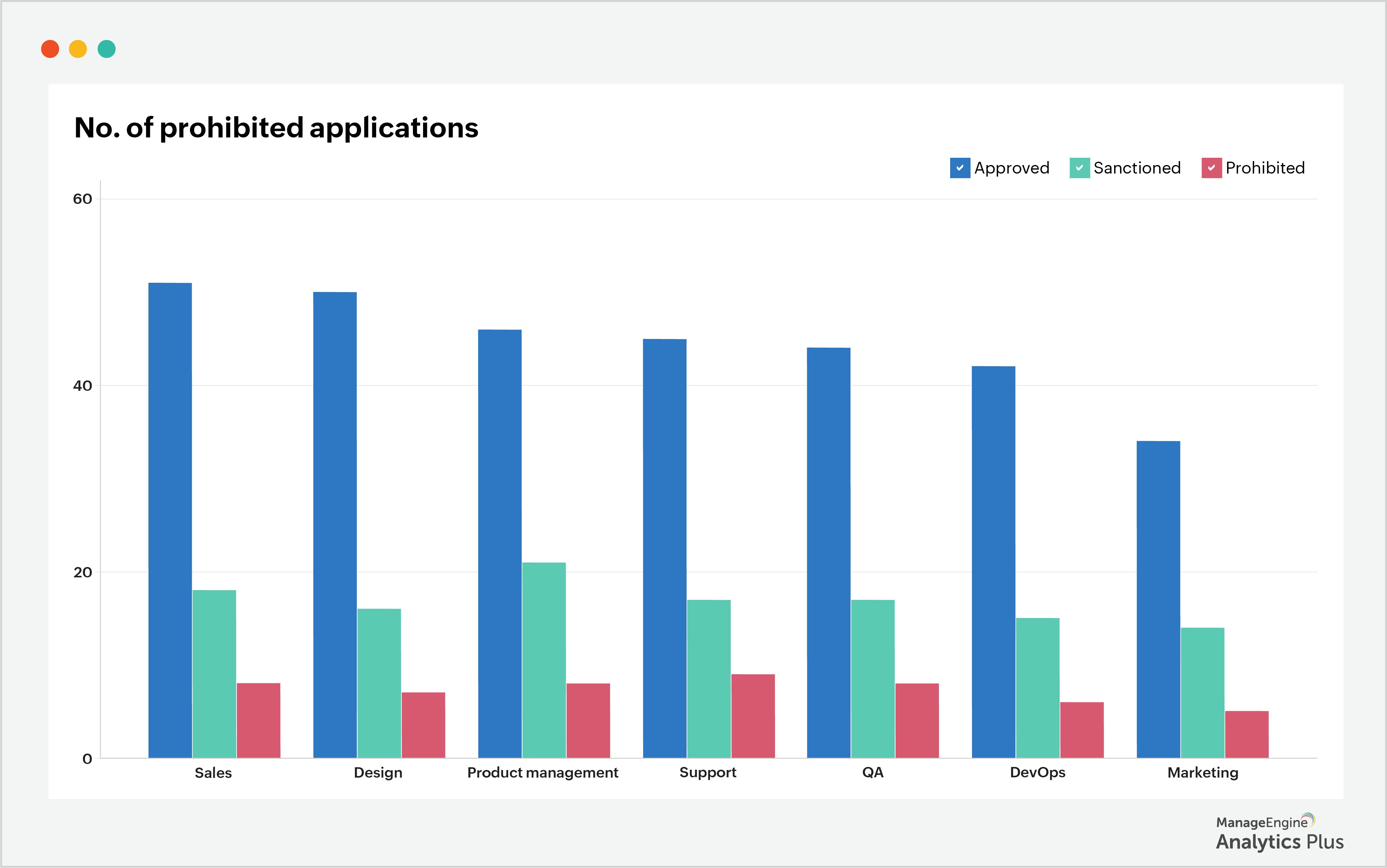
3. Manage the use of peripheral devices
Peripheral devices increase a computer's functionality and user experience. However, these devices can give threat actors new ways to access your organization's networks, systems, and information. The majority of peripheral devices are connected to the user's device via USB ports. Analyze the USB connections, paying attention to the count, frequency, and duration of USB port use.
The sample reports below show the number of computers with USB access and the computers that have the most USB connections. High numbers of connections warrant further investigation.
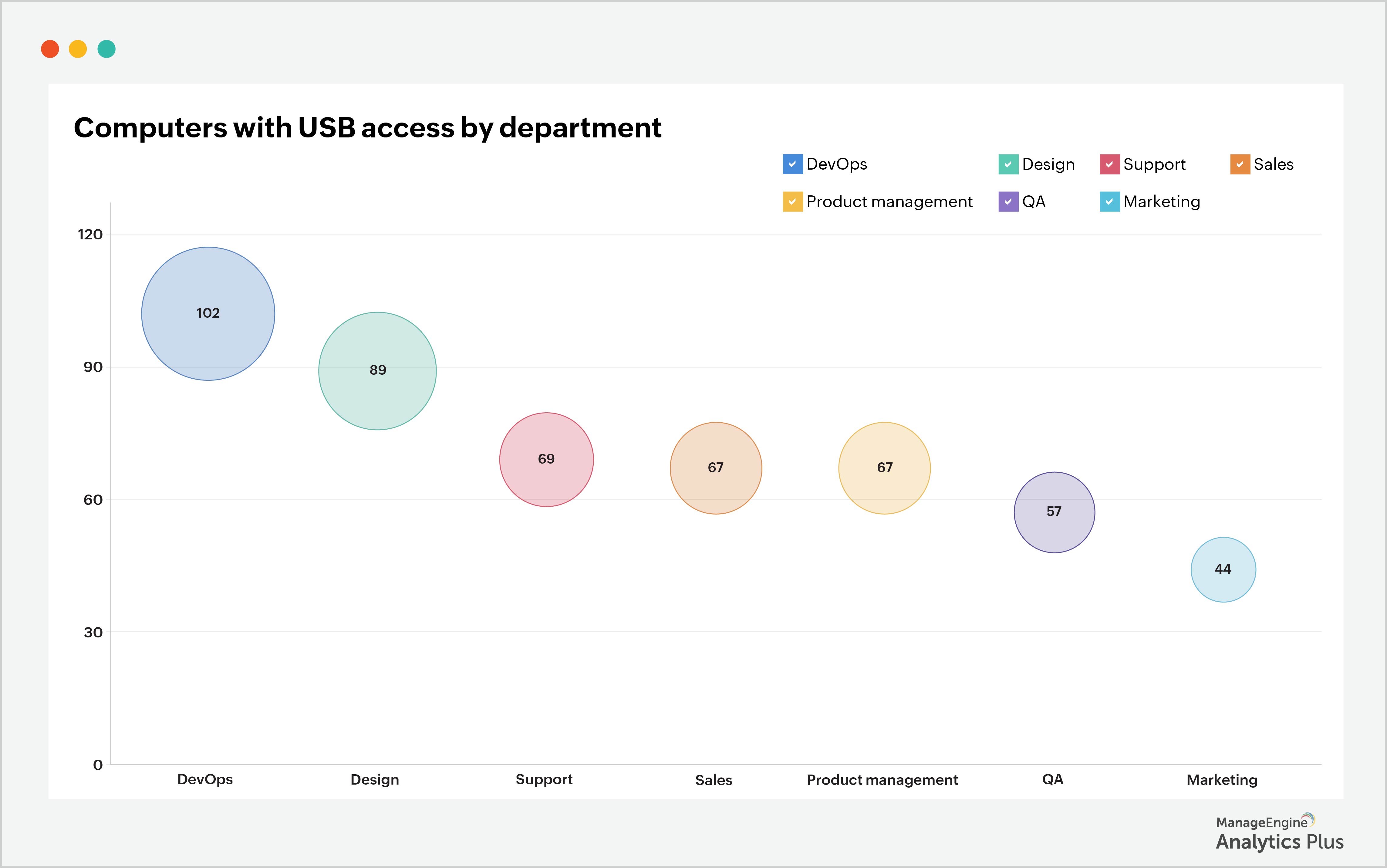
According to the above report, the DevOps Department has the most computers with USB access. Below is another report that lists the DevOps Department users who have the most USB connections to their devices, which can help in further analyzing the usage of shadow IT through peripheral devices.
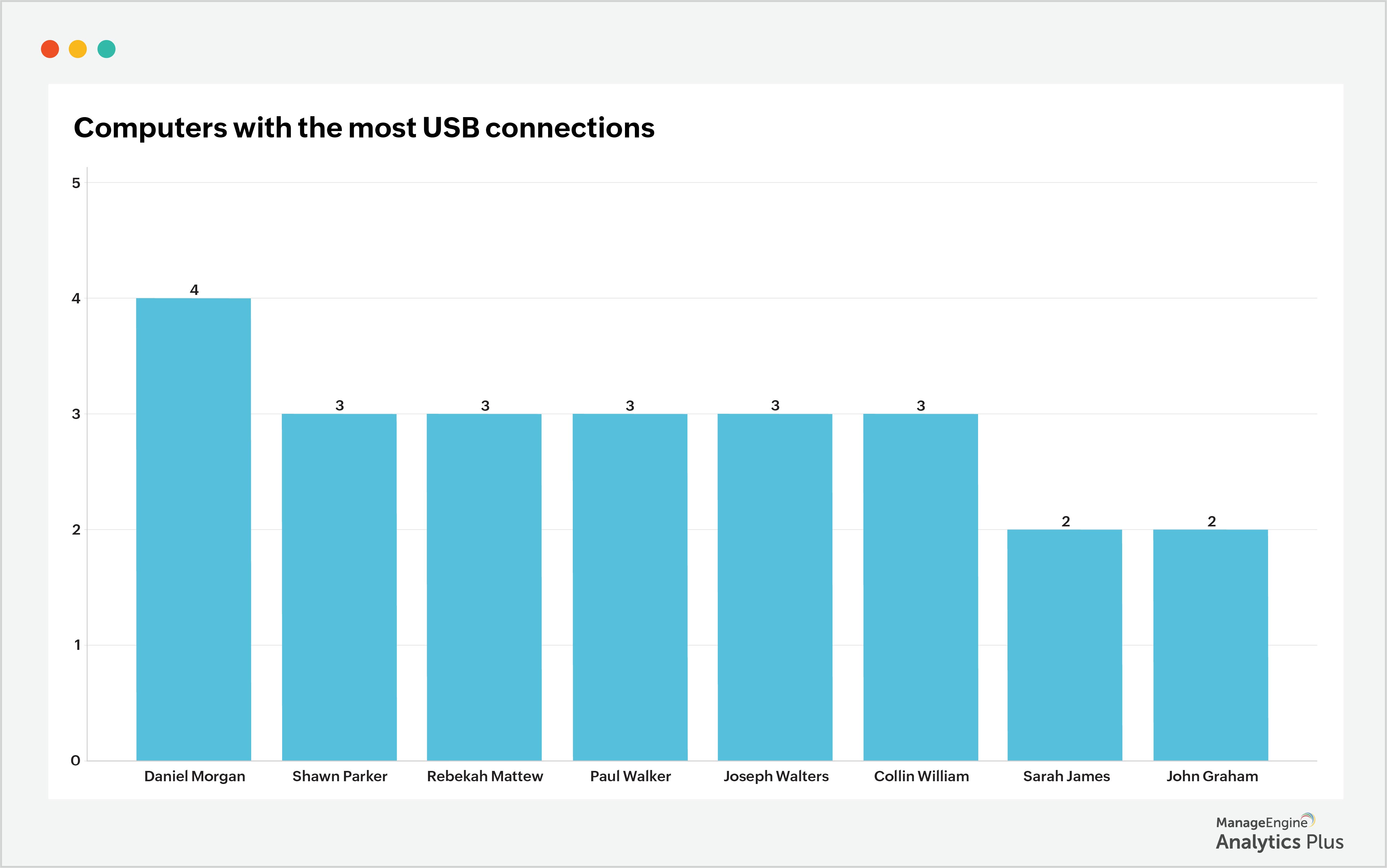
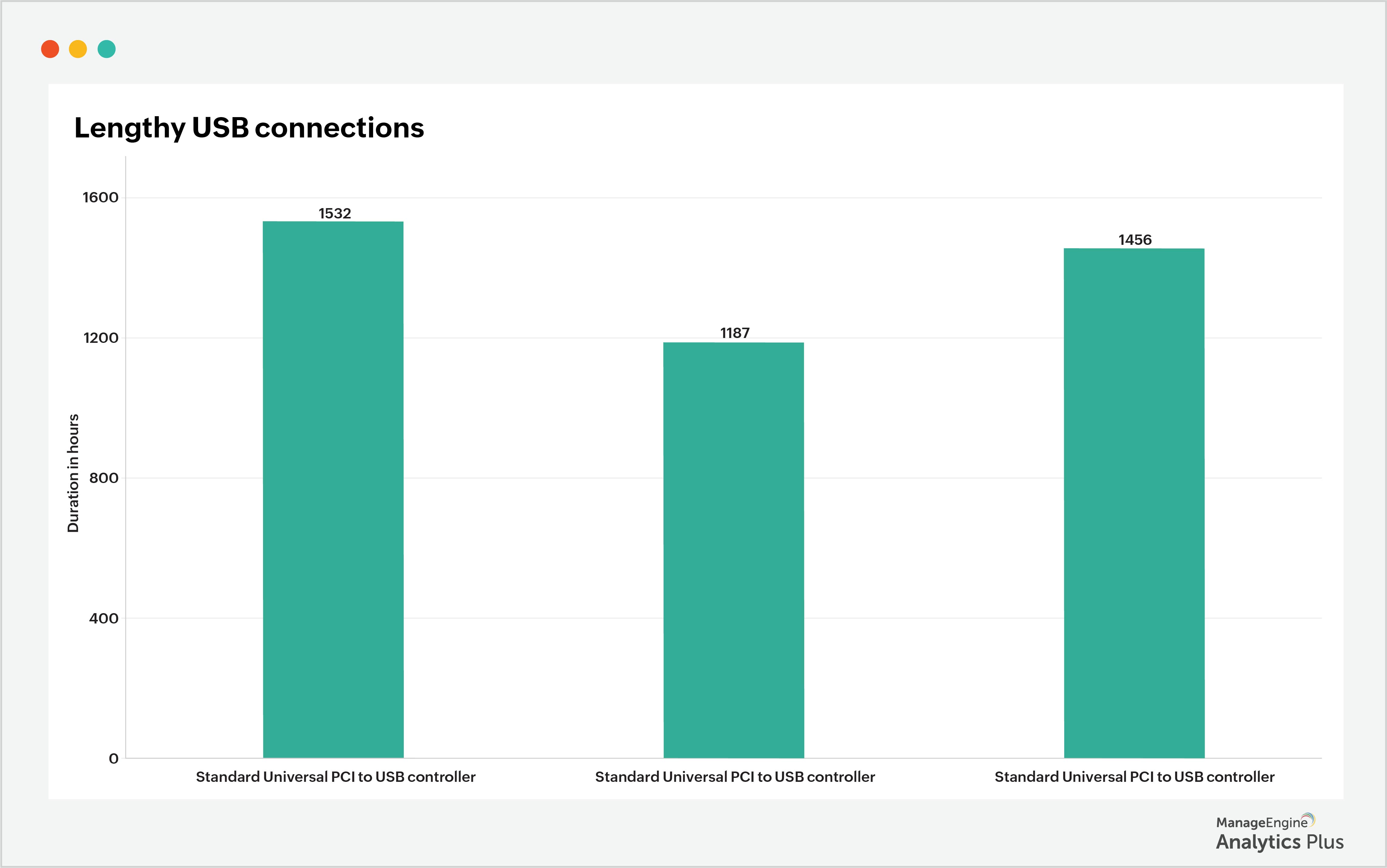
With the help of the above report, filter the computers that have had the longest USB connections. The report below shows the devices with lengthy USB connections. To discover why there are such long USB connections, get in touch with the end users to check if these are genuinely related to work.
4. Assess the current risk level of shadow IT
Analyze your organization's current shadow IT risk level by tracking the use of prohibited applications and peripheral devices connected to your organization's devices. Identify the users who often access prohibited applications or unauthorized devices and ensure they are aware of the consequences of using shadow IT.
5. Ensure all your employees complete their security training
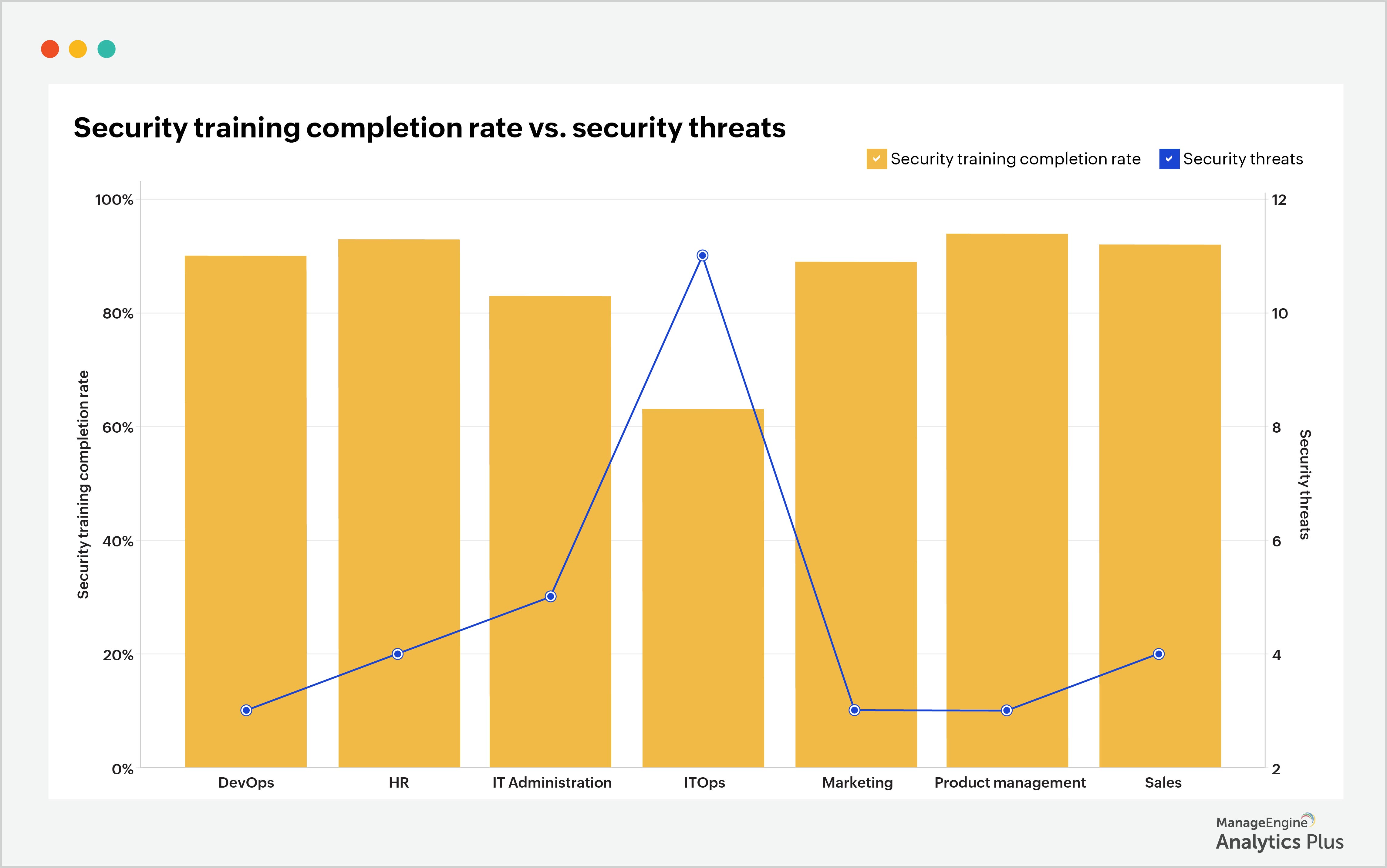
Most of the time, employees do not intentionally use shadow IT. They attempt to enhance the way they work, not realizing the security hazards of their actions. Organizations create policies and restrictions to prevent this, but tend to fail in explaining the significance of these to the workforce. Ensure your staff has completed security training to reduce the security risks brought on by shadow IT. The sample report below illustrates that the number of security threats is high when the employee training completion rate is low.
Conclusion
Shadow IT is a massive cybersecurity danger to your organization and its critical data. End users may use shadow IT intentionally or accidentally for a range of reasons, but regardless, it poses a danger to your organization's security and violates compliance. However, with the practices, we mentioned in this blog and the boost that security analytics offers, you can have the visibility and control you need to combat the dangers of shadow IT.
The reports shown in this blog were built using Analytics Plus, ManageEngine's AI-enabled IT analytics application. If you'd like to create similar reports using your endpoint management data, try Analytics Plus for free.
Talk to our experts to discover all the ways you can leverage analytics to step up your cybersecurity measures.





