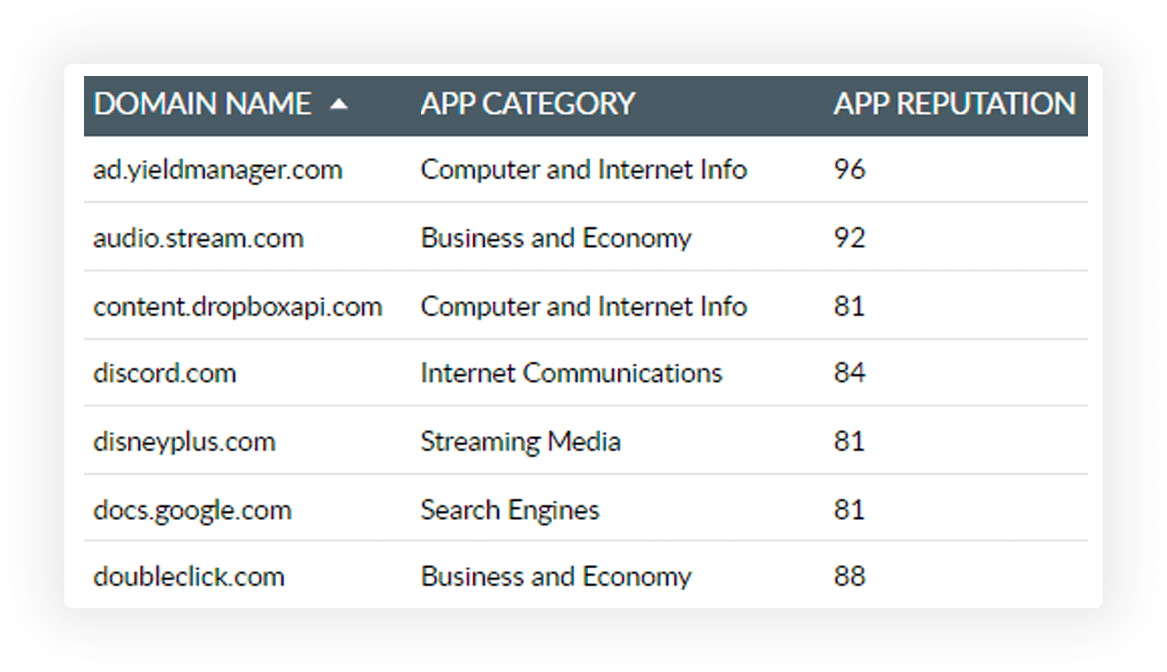
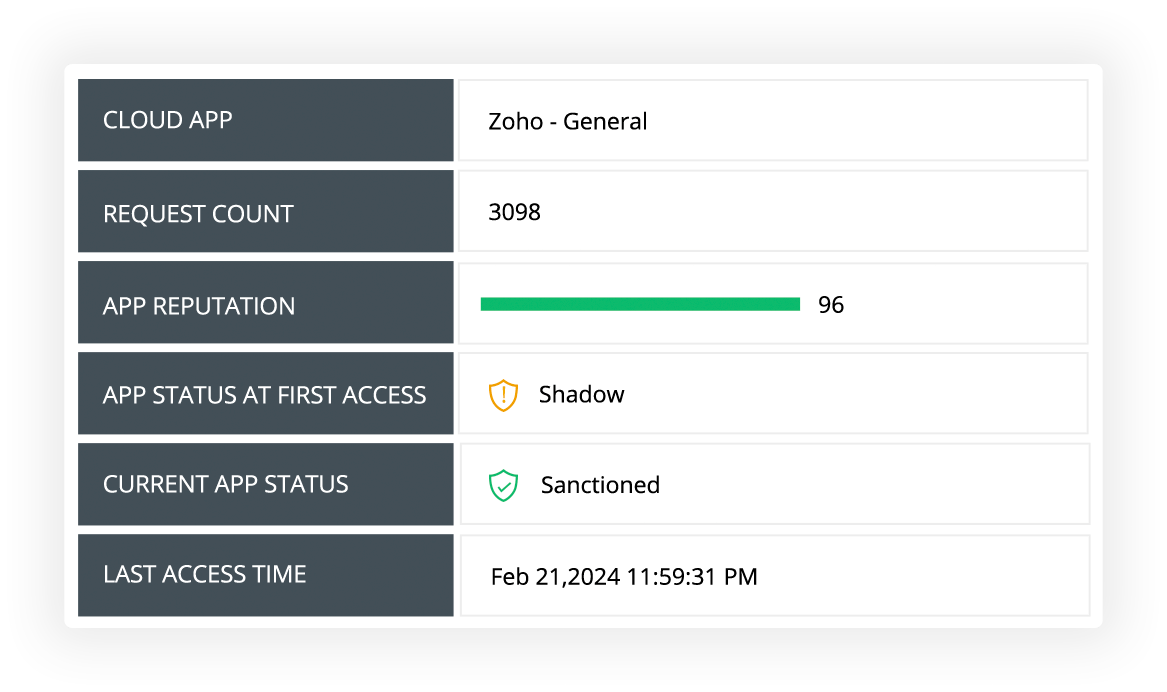
Monitor all accessed cloud apps, with details on their reputation score, category, and the employees accessing them.
Control cloud usage by sanctioning and banning applications with help from built-in threat analytics.
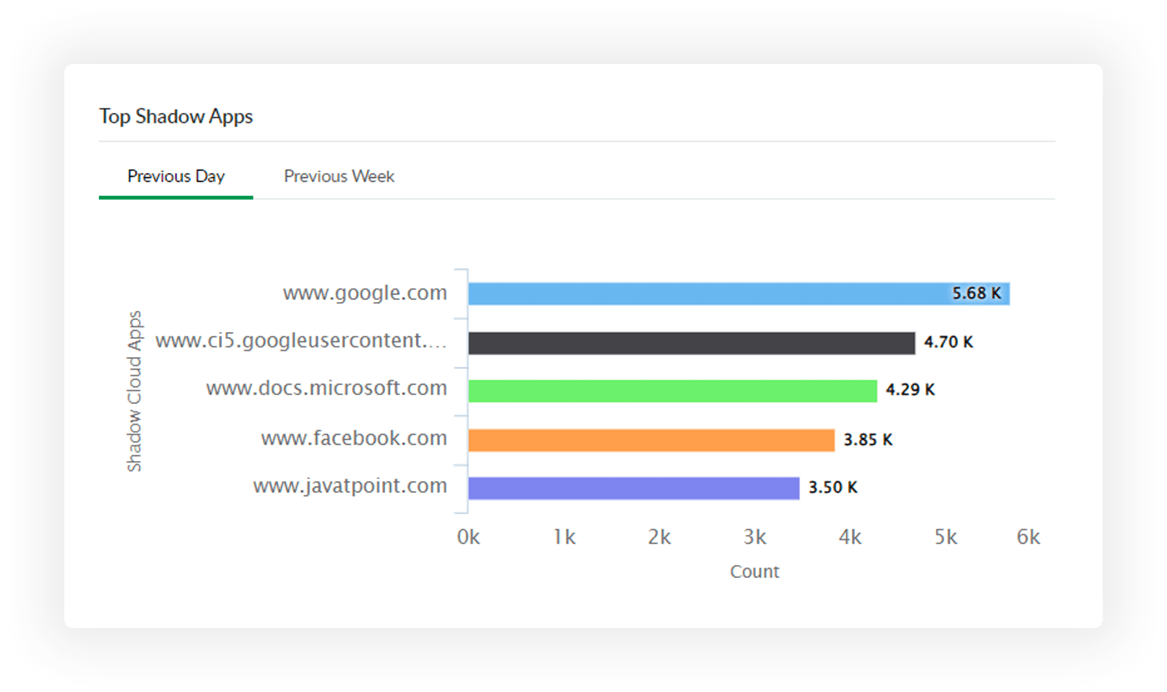
Expand your cloud discovery horizon with intricate insights on the usage of shadow IT applications.
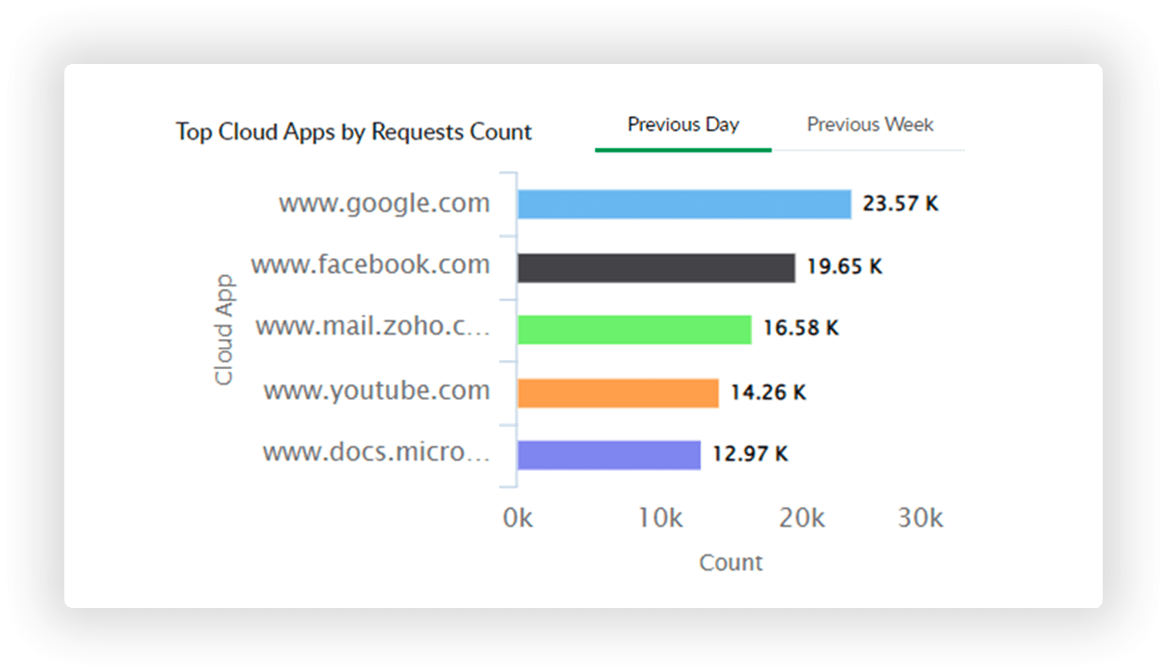
Leverage the cloud application report for insights on frequently accessed domains, types of applications accessed, and upload and download activities performed through your gateway servers.
Spot critical events such as employees uploading large volumes of data onto cloud applications or accesses during non-business hours.
Use the app category and reputation parameters to ascertain the type of cloud applications accessed—such as streaming media or games—and regulate their usage.
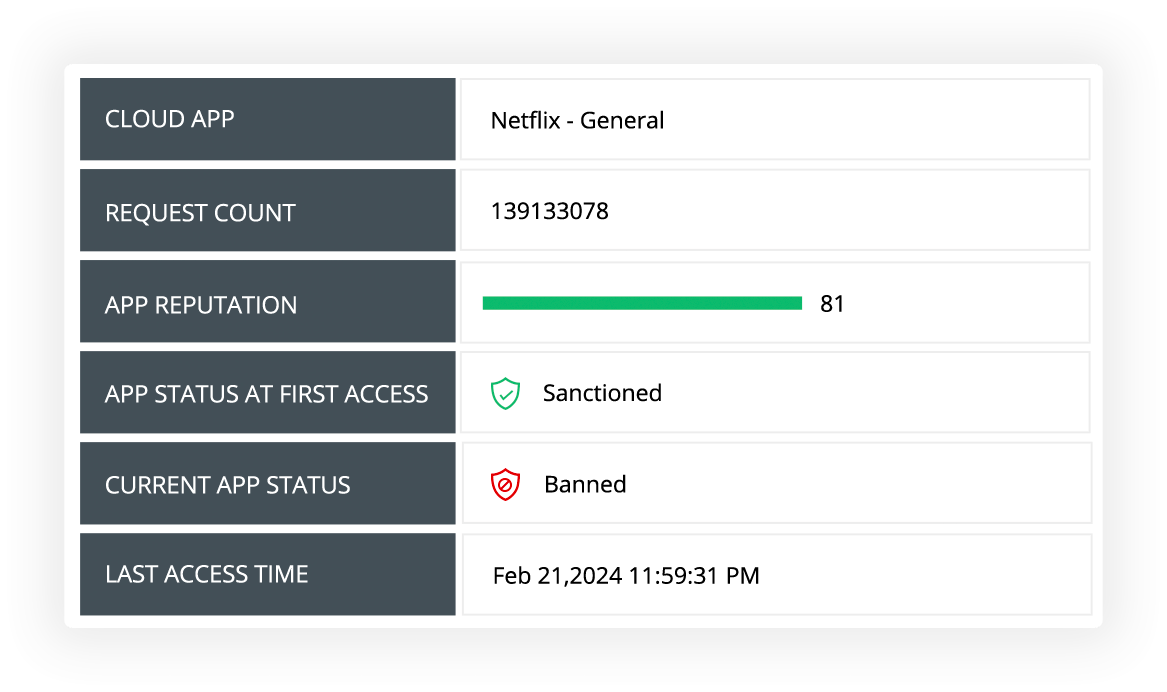
Easily curate a database of secure and business-relevant cloud applications with the help of built-in threat analytics, and sanction their usage to boost productivity.
Detect the use of shadow IT applications to understand the IT requirements of your employees, expand your IT arsenal, and prevent potential data leaks.
Prevent your employees from accessing or uploading corporate data via high-risk applications by blocking their usage in real time.
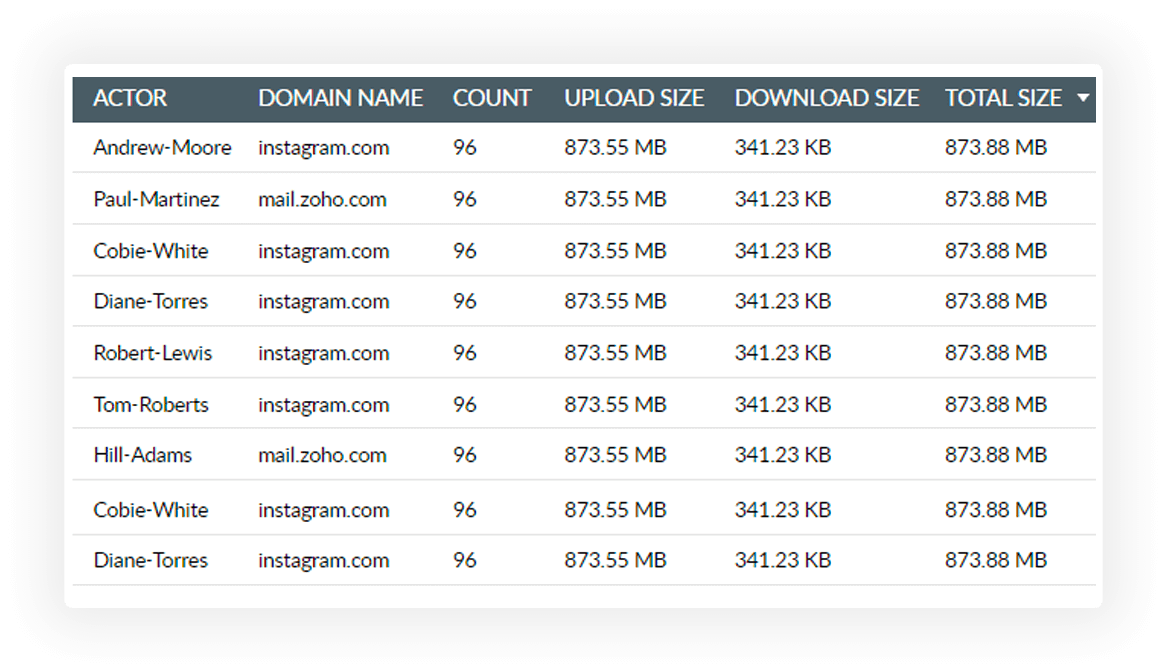
DataSecurity Plus' cloud app discovery tool provides you with actionable insights on cloud applications, domains, and actors.
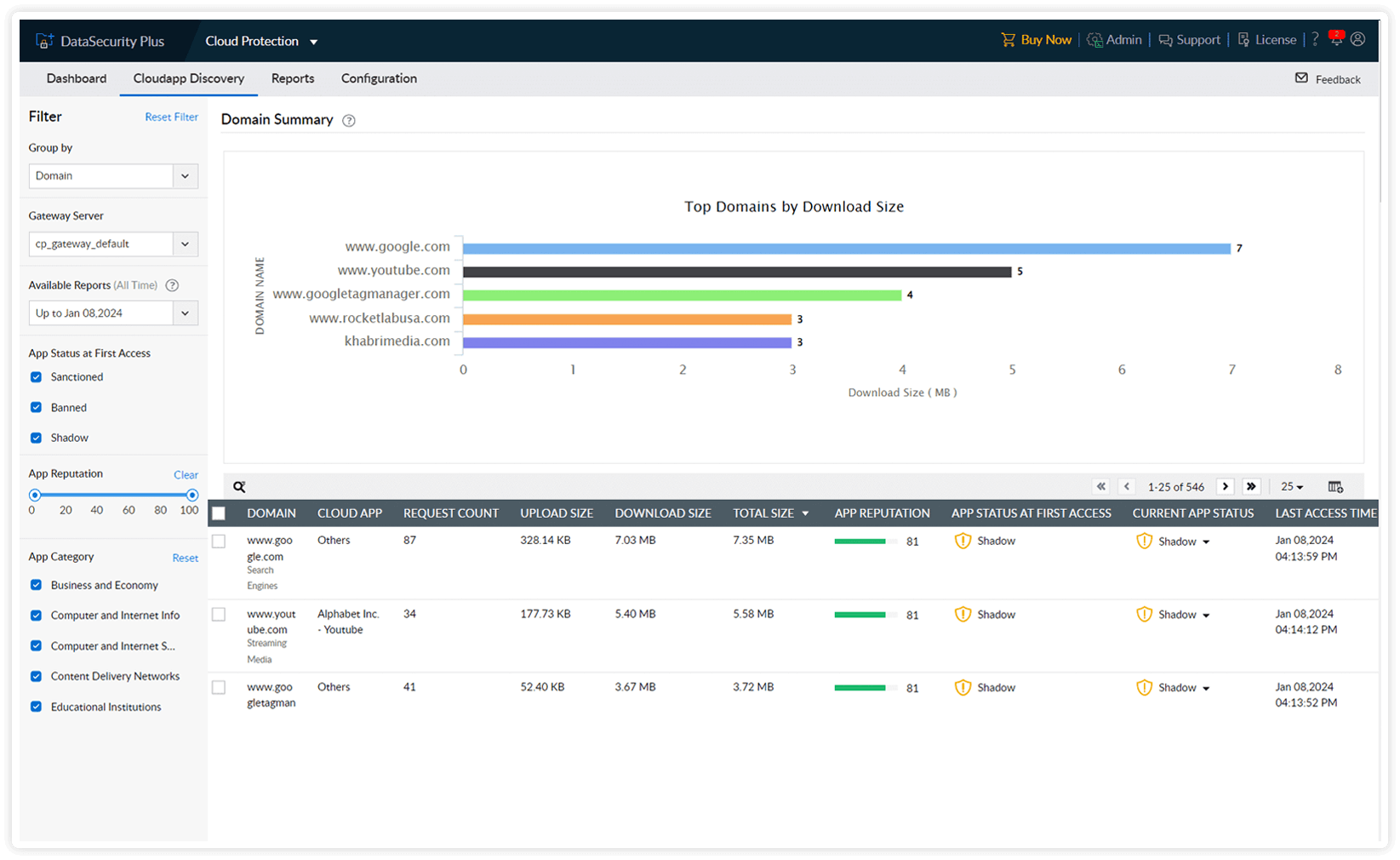
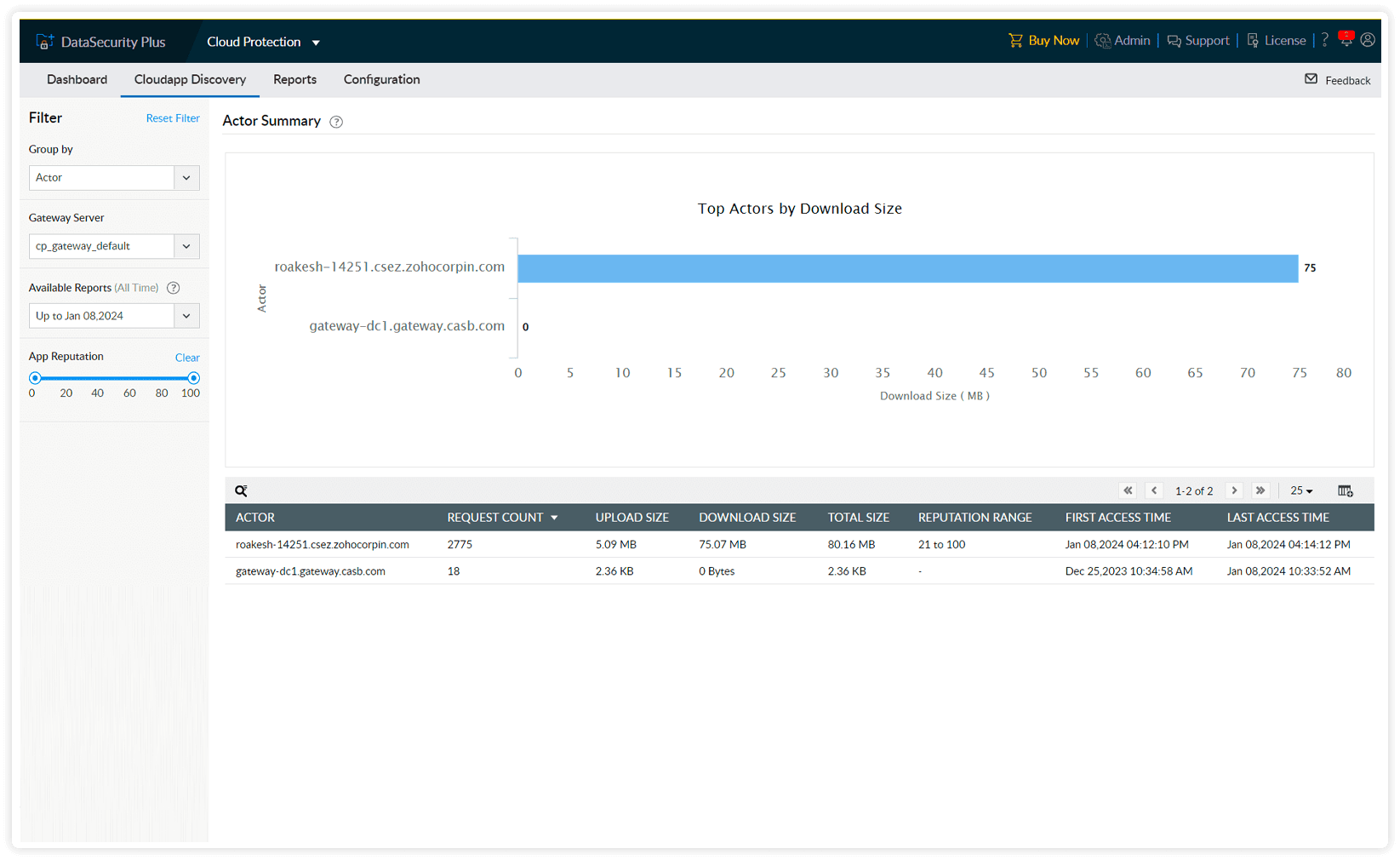
Gain a comprehensive understanding of domains accessed, encompassing attributes such as reputation range, access time, and upload or download size.
Leverage the filters to generate a plethora of views and dashboards to drill down to the information you need.
Determine the business relevance of domains accessed and classify them into sanctioned or banned applications.

Get insights on employee access to cloud apps and their download activities, and access the apps to identify the scope of any insider threat.
Identify high-risk employees by assessing the reputation ranges of the applications they visit.

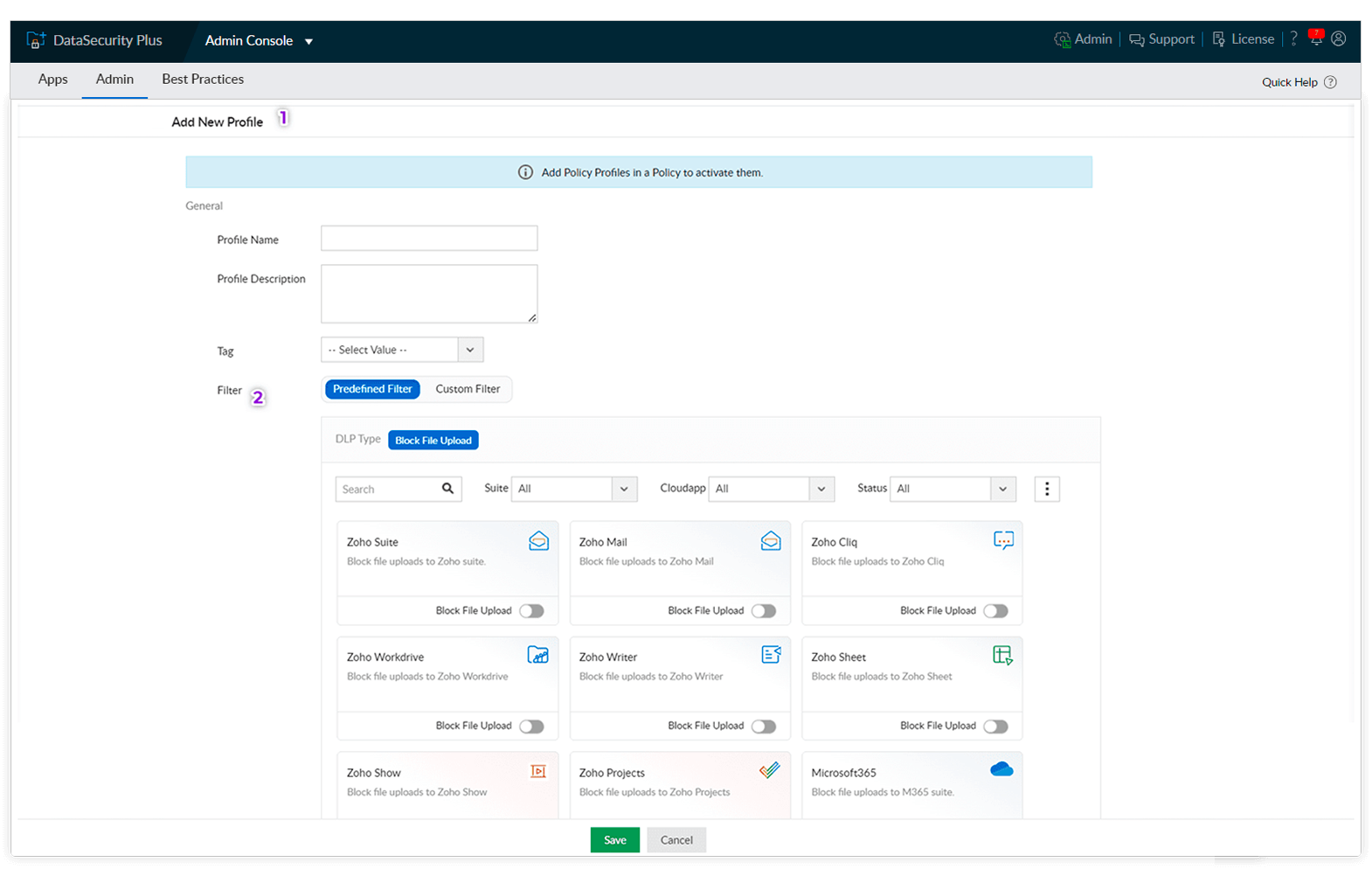
Configure cloud DLP policies to restrict employees from uploading business-critical data onto non-business applications, and prevent data loss.
Choose from a myriad of preconfigured suites and cloud applications or leverage custom filters to meet specific cloud DLP needs.

Detect the transfer of data to and from the web by monitoring upload and download activities.
Audit the usage of Outlook across endpoints and prevent data leaks via emails.
