Strengthen control over your unstructured data with a file analysis solution that provides insights and analytics to help
manage junk files, enable effective storage planning, and ensure file security.
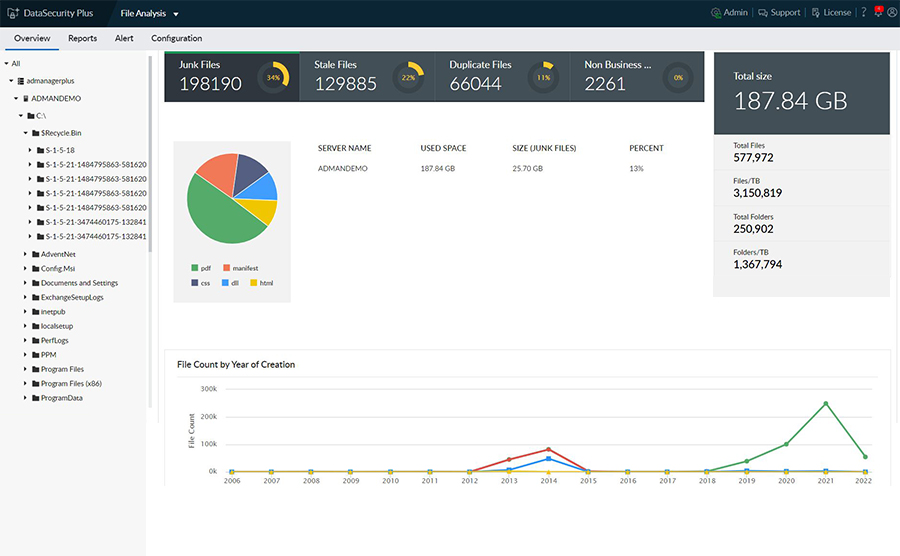
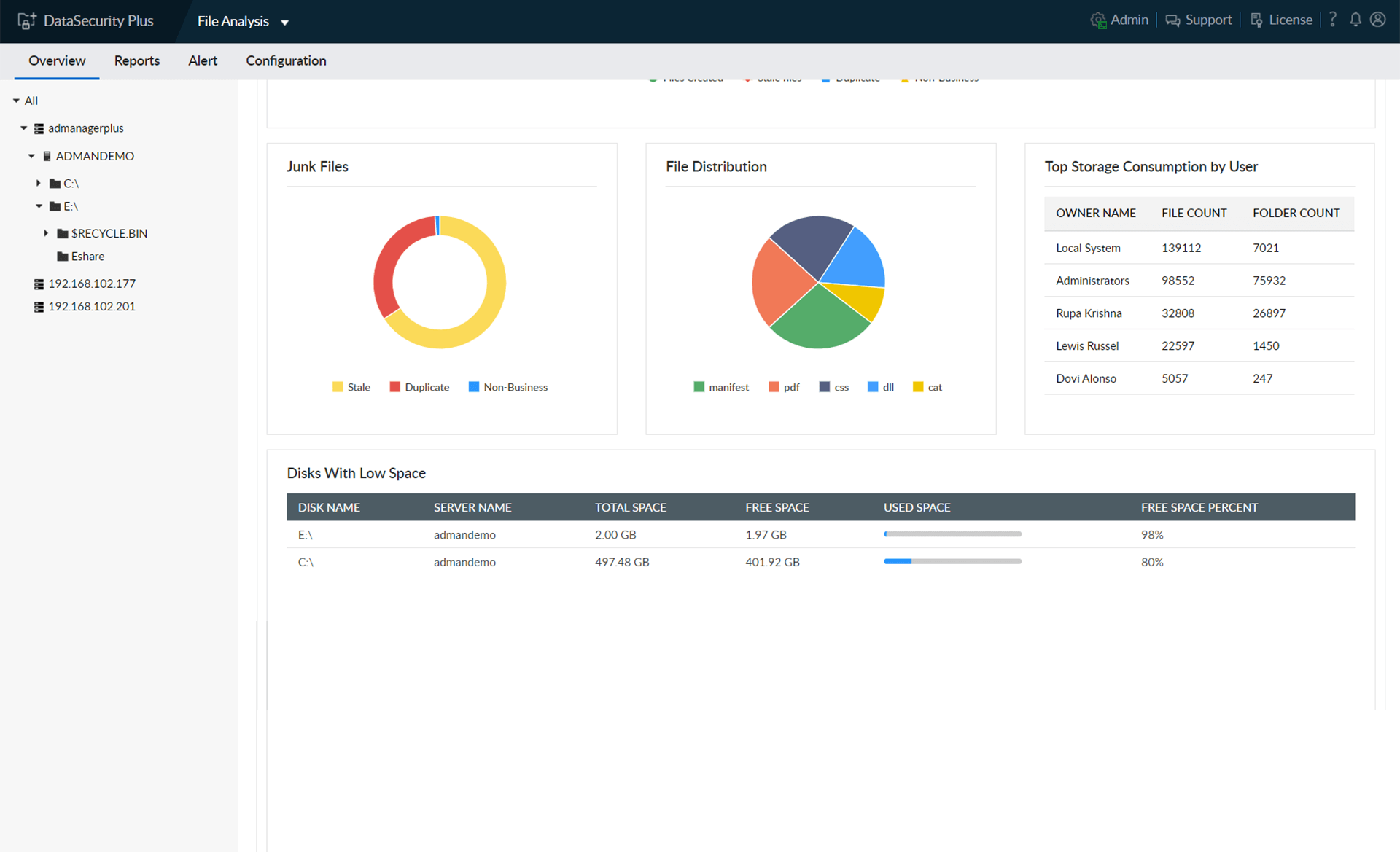
Understand your storage better with insights into file count and volume shown in graphs and charts.
Identify trivial, stale, non-business, and other junk files, and manage them according to your organization's needs.
Scan through the storage and security properties of directories right down to the file level.

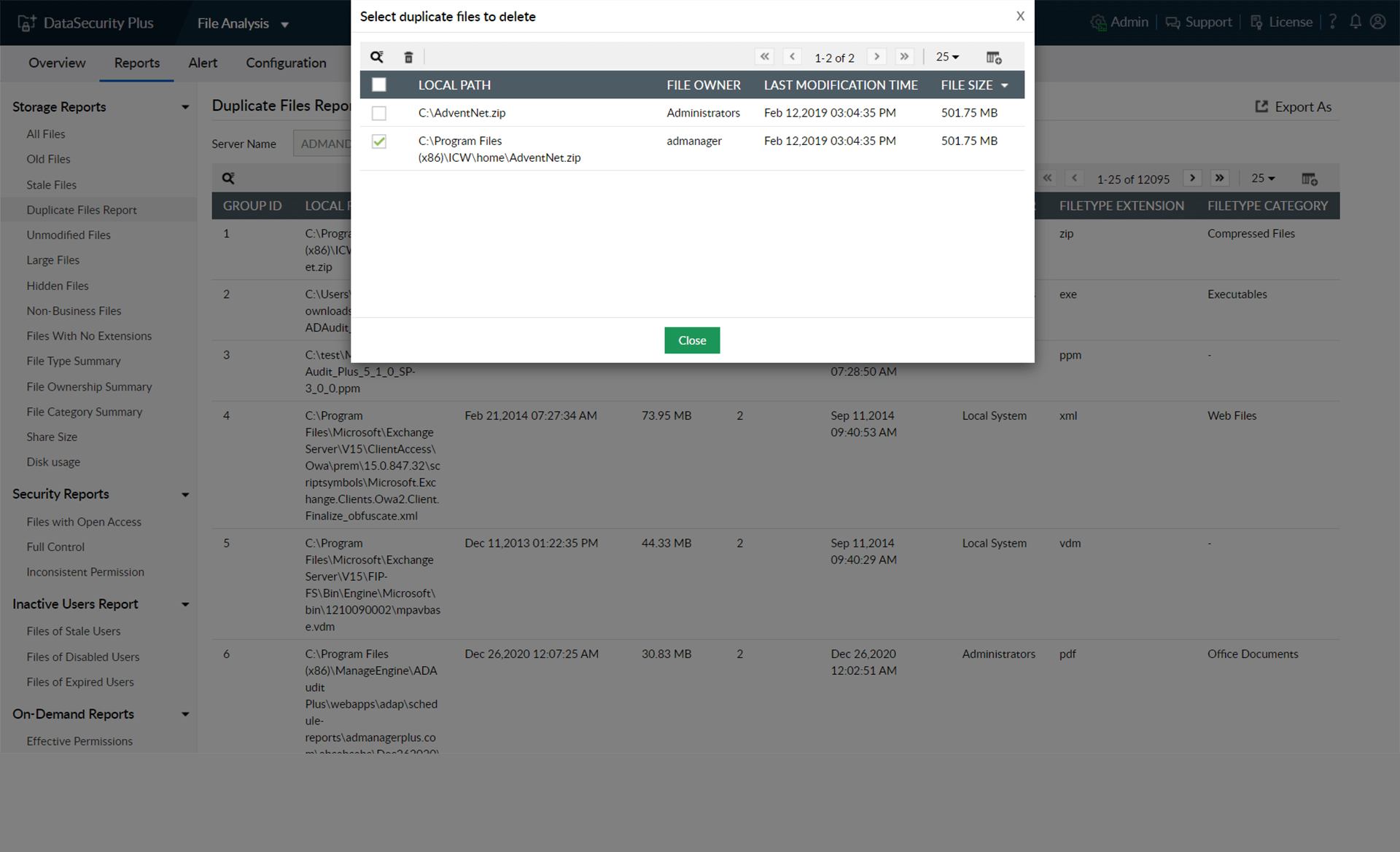
List duplicate files with details on the number of copies, their location, and size.
Manage duplicate files easily by deleting copies right from the user interface.

Receive detailed reports on disk space availability, usage, storage density, and more.
Get useful insights into the distribution of files by their type, category, and other attributes.
Identify the users whose files take up the most space in enterprise storage.

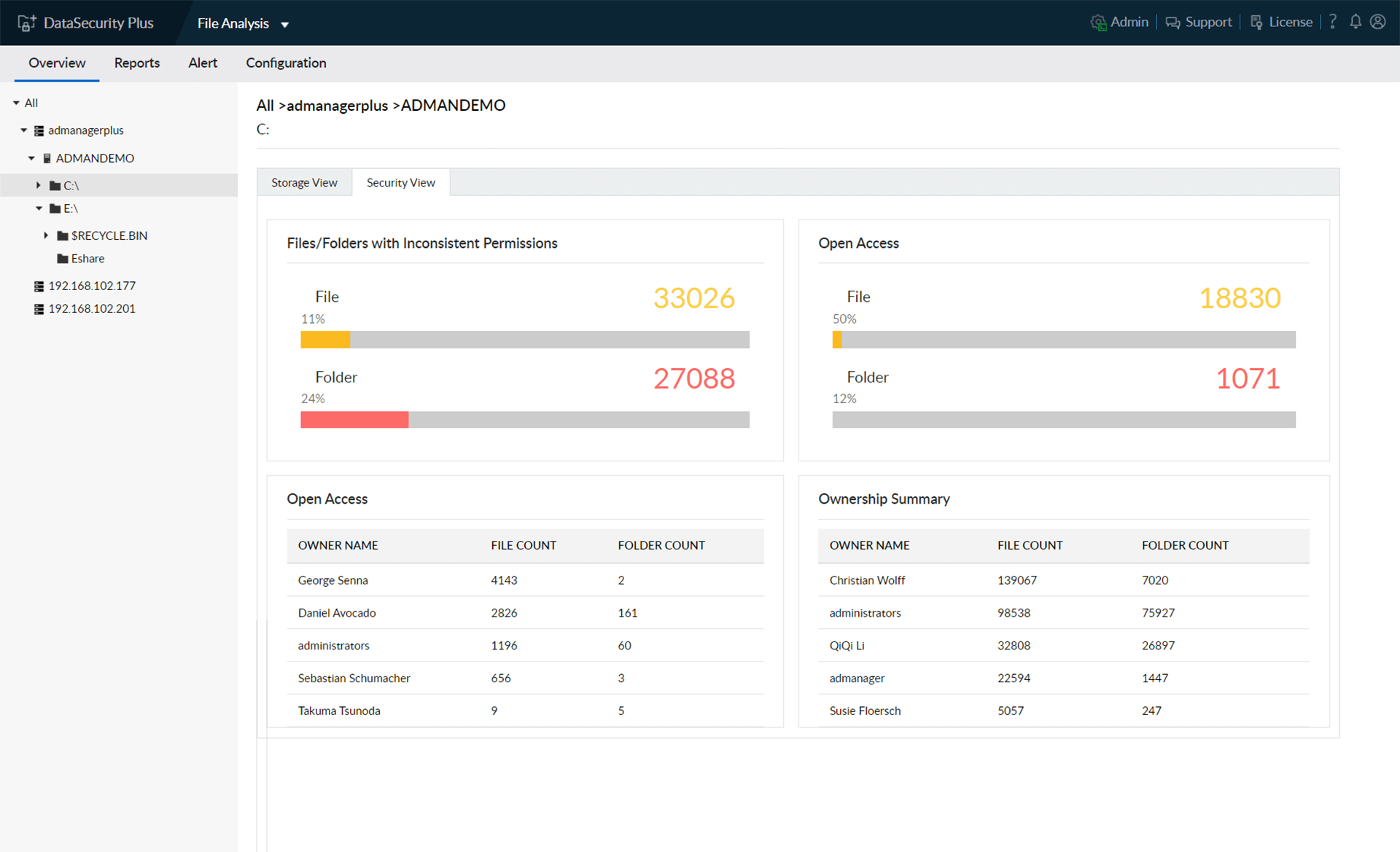
Get an overview of the permissions associated with every file and folder right from the dashboard.
Identify security vulnerabilities such as broken inheritances and files allowing unrestricted access to users.
Know the number and size of files owned by each user in your domain.

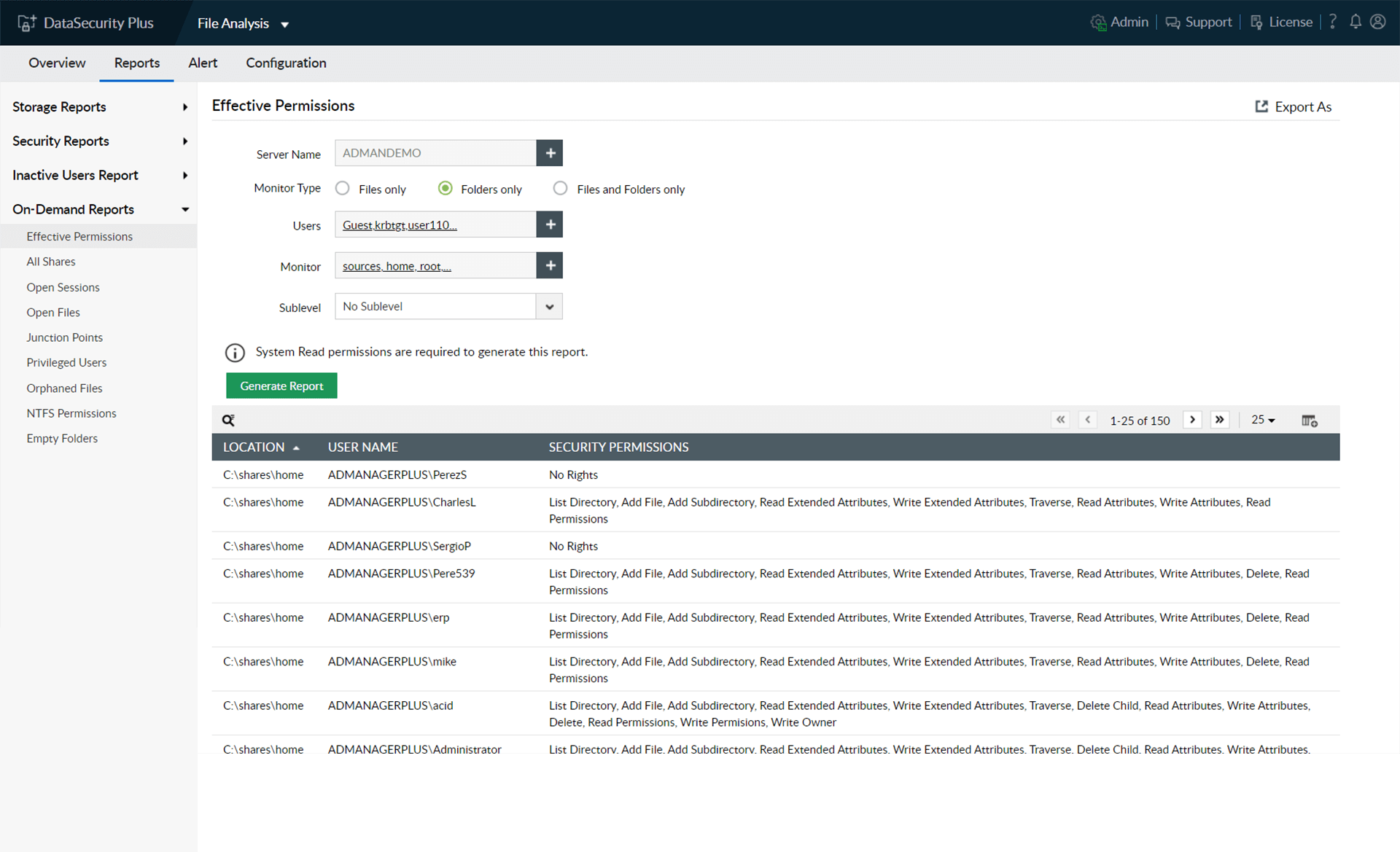
Generate reports on users' effective permissions to critical folders, and check if only the least privilege necessary is applied.
Run a secure ship with instant, informative reports on privileged users, shared files, orphaned files, and more.

Thanks! One of our solution experts will get in touch with you shortly.