Ransomware is no match for DataSecurity Plus' multi-layered defense strategy.
Least privilege for file access Review file permissions regularly to ensure that there are no unwarranted permissions to your sensitive files; if a victim has write permissions on a shared file, ransomware will encrypt those shared files too.
Visibility on file activity Gain visibility into your file server environment, events, and user behavior to identify malicious activity.
Ransomware detection Spot sudden spikes in file events like renaming, deletion, or permission changes, which are all telltale indicators of a ransomware attack.
Real-time alerts Generate instant notifications via email for all unwarranted file modifications and permission changes, and catch extremely time-sensitive incidents.
Stop the infection Cut off file encryption in the host machine within seconds by promptly shutting down the ransomware-infected machine.
Quarantine ransomware Isolate the corrupted device from the network to minimize the impact of ransomware on your organization.
Forensic investigation Identify infected machines faster using actionable, accurate forensic data. Generate clear and concise audit records as legal evidence.
Detect and shut down potential ransomware attacks with real-time alerts and an automated threat response mechanism.
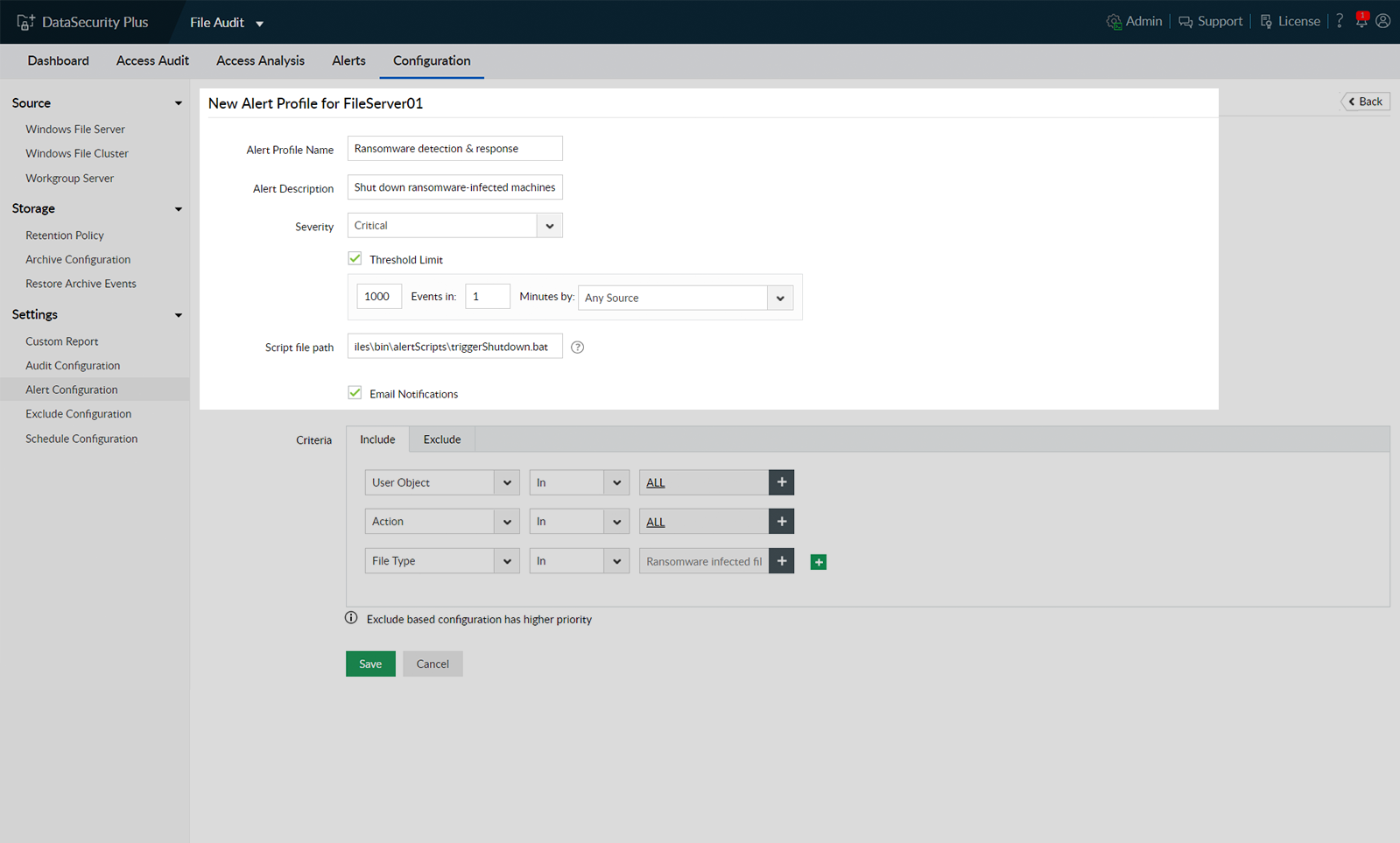
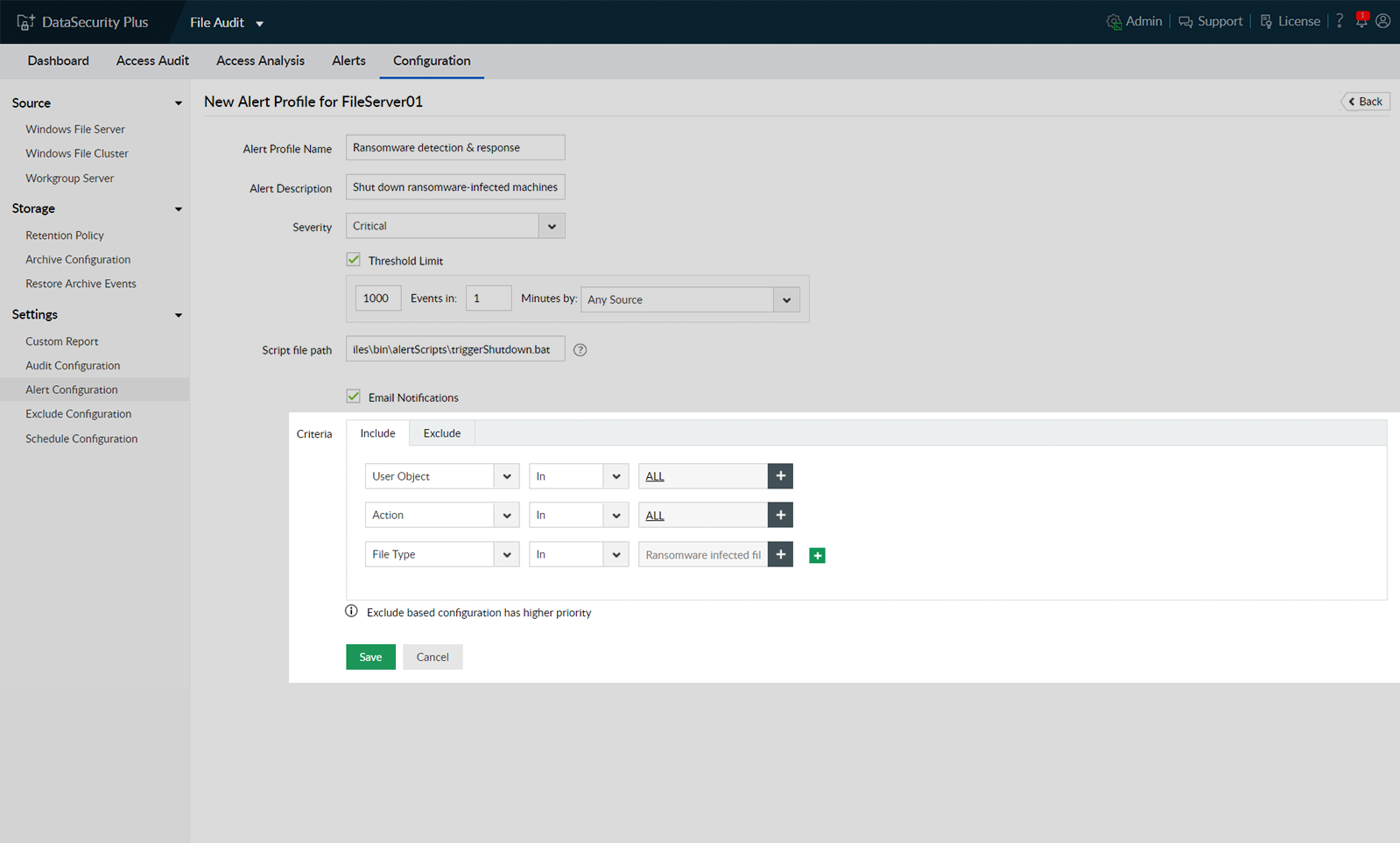
Stop a ransomware infection within seconds by automatically shutting down an infected machine. Execute custom scripts to perform actions tailored to your organization's needs (e.g. disconnect the user session or lock the user account).
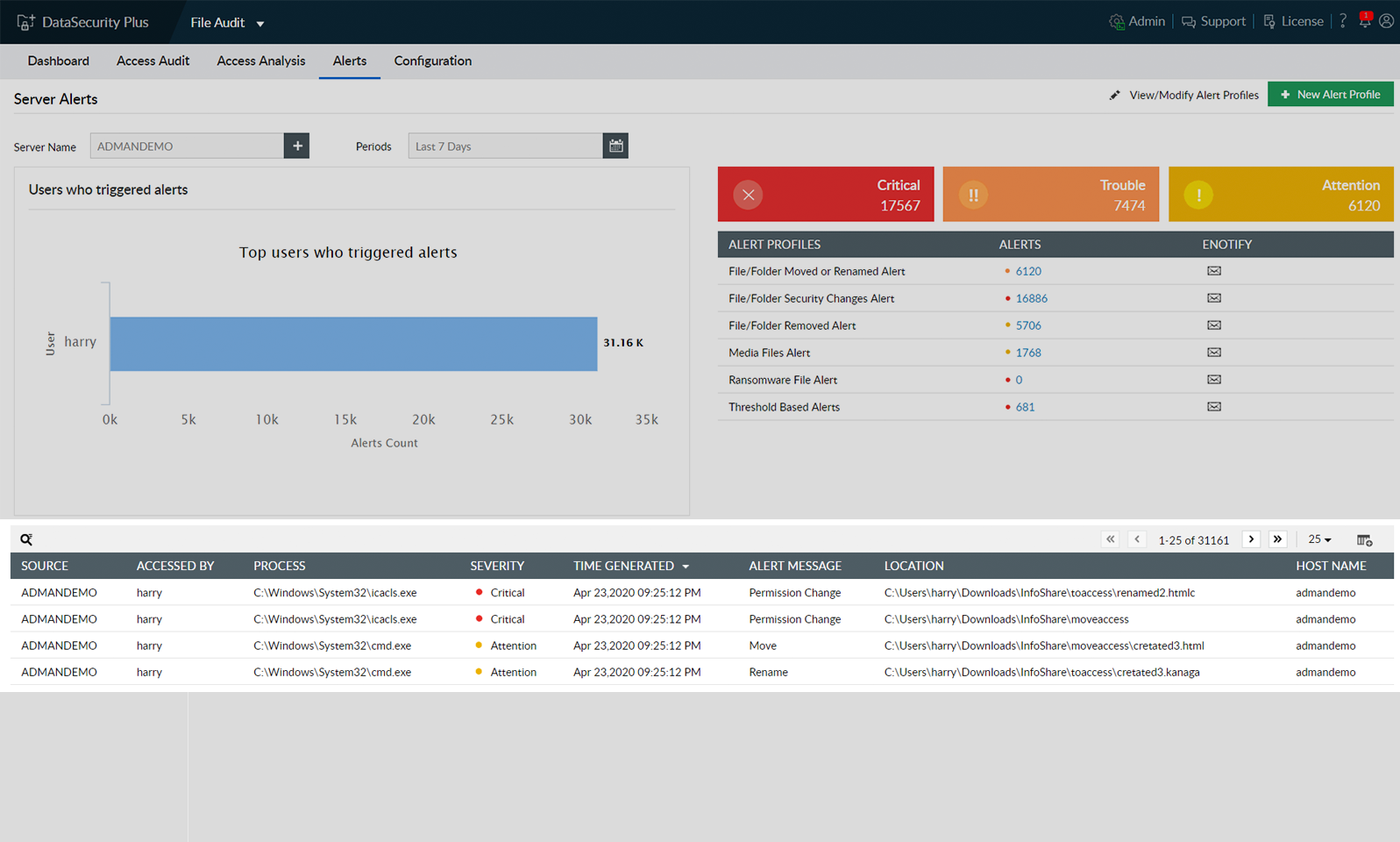
Speed up incident response with instant email notifications upon detection of malware attacks, especially ransomware, by watching for sudden spikes in file renaming and modification events.

Many ransomware variants use a specific file extension when they encrypt data. DataSecurity Plus uses these malicious extensions to identify known ransomware variants and block them instantly.

View in-depth details of any ransomware attacks to identify the client IP of the machine where the malware started spreading. You can use this and other information available to perform root cause analysis.

DataSecurity Plus allows you to execute your own scripts to perform actions tailored to your organization's needs (e.g. disconnect the user session, lock the user account, or shut down the system).
DataSecurity Plus identifies all ransomware attacks promptly and generates threshold-based alerts that are triggered when a set number of monitored events occur in a defined time span.
Many ransomware variants use a specific file extension when they encrypt data. DataSecurity Plus uses these malicious file extensions to identify known ransomware variants and block them instantaneously.
DataSecurity Plus lets you identify the client IP of the machine where the attack began. You can use this and other information to perform root cause analysis.
If that's the case, then DataSecurity Plus should have already shut down the potentially infected system. From here, you should analyze the audit data to identify which ransomware variant it is and start planning your strategy from there.
No problem! Just fill out this form with as much information as possible and we will contact you with the appropriate steps.
Have a question about features, trials, or licensing?Go ahead, ask us anything.