Focus on suspicious user activity in critical files to detect potential insider threats.
Quickly identify unauthorized changes by configuring custom alerts and instant responses.
Satisfy GDPR, HIPAA, and other regulatory requirements with real-time change detection.
View real-time reports on both successful and failed file access attempts like read, write, modify, delete, move, rename, permission change, and more.
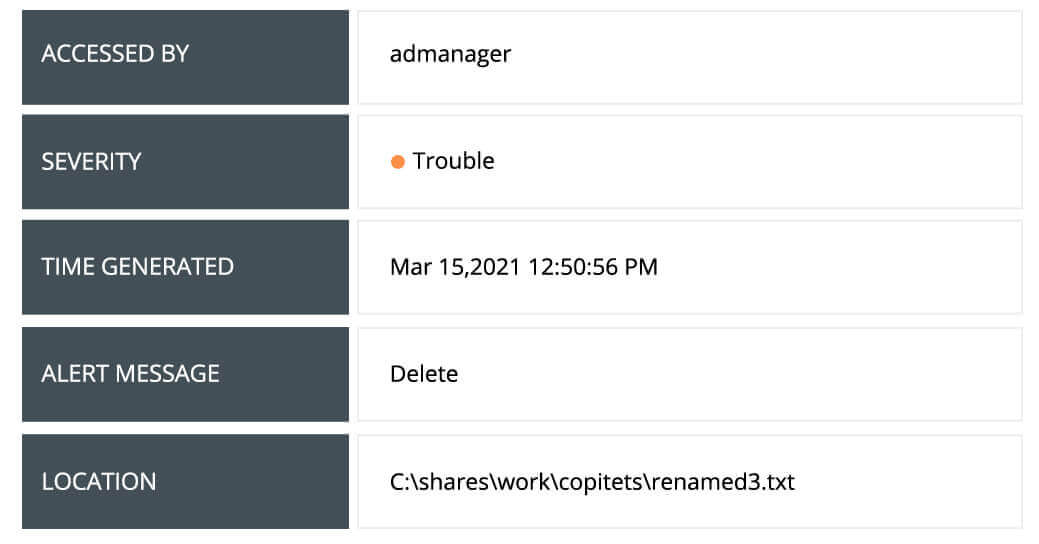
Examine file activity reports based on user, host, shares or location as the focal point to drill-down to the source of deviation and spot potential data exfiltration.
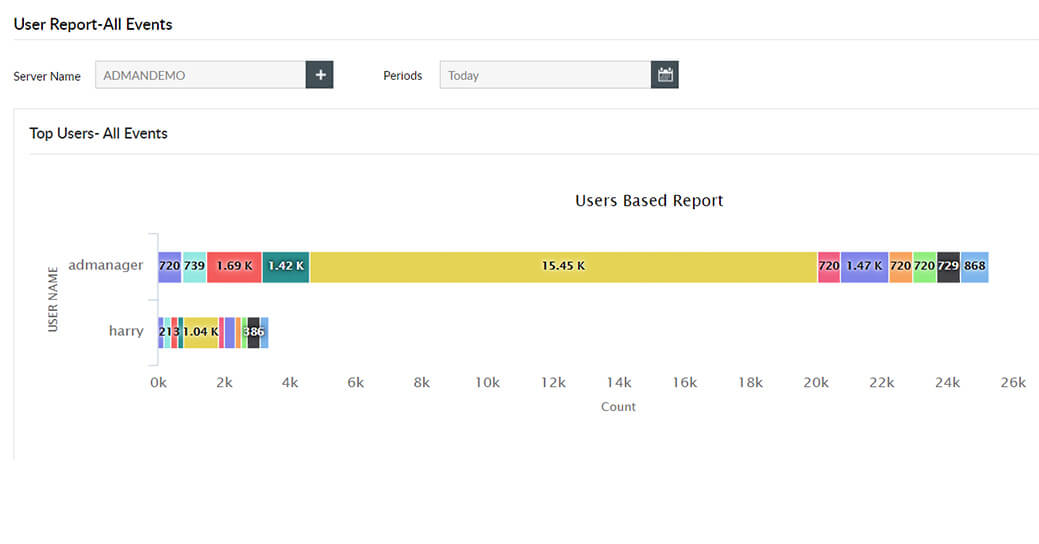
Keep track of accidental file changes made by users including files moved or renamed to revert them to the original location or version.
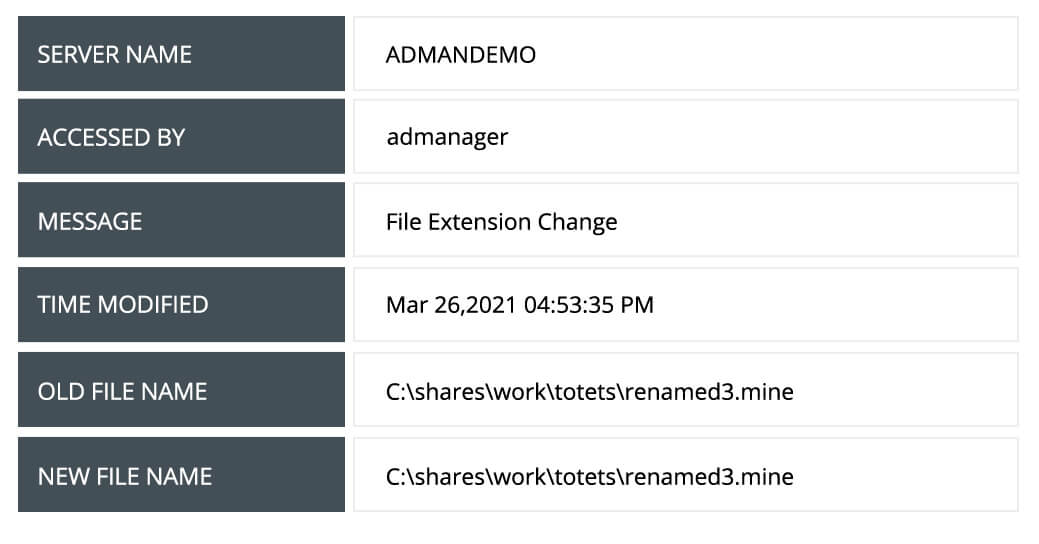



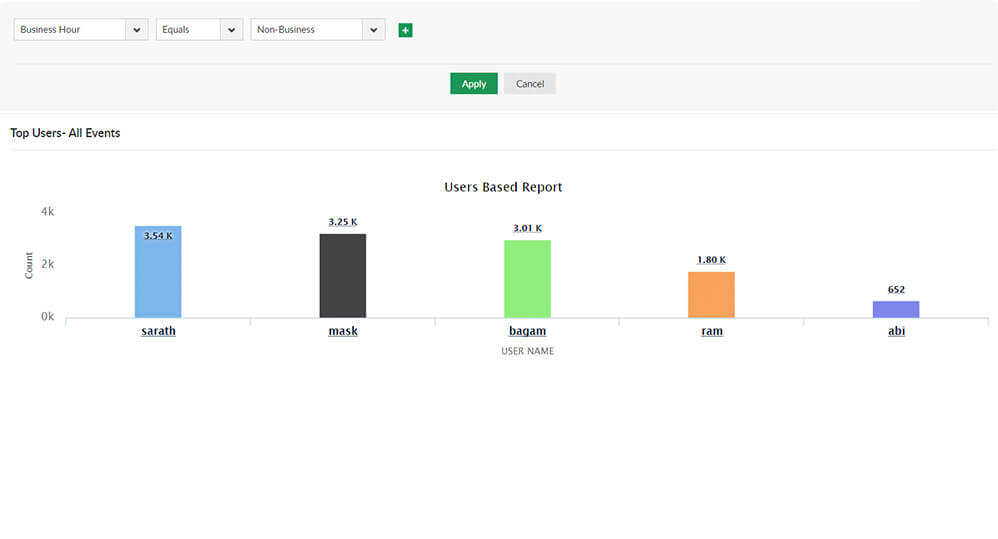
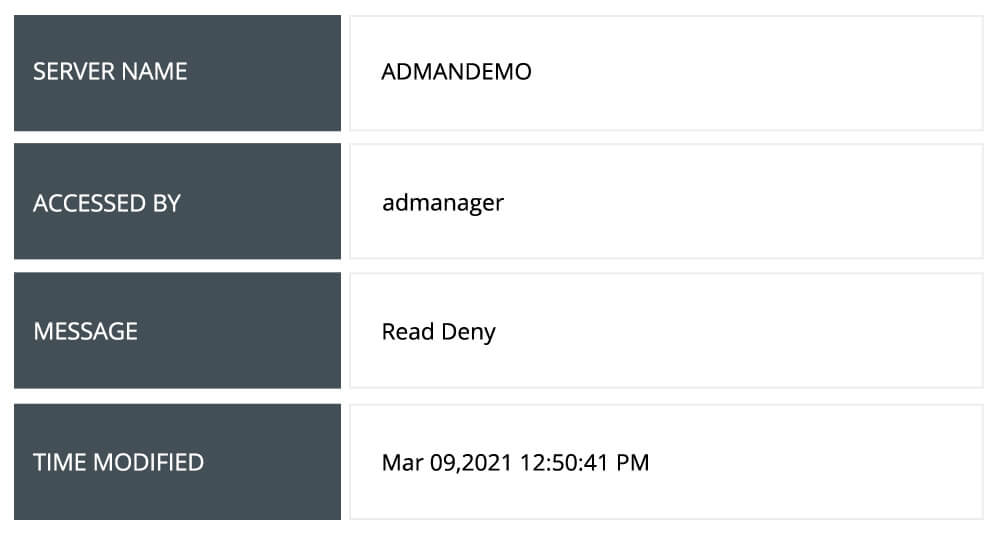
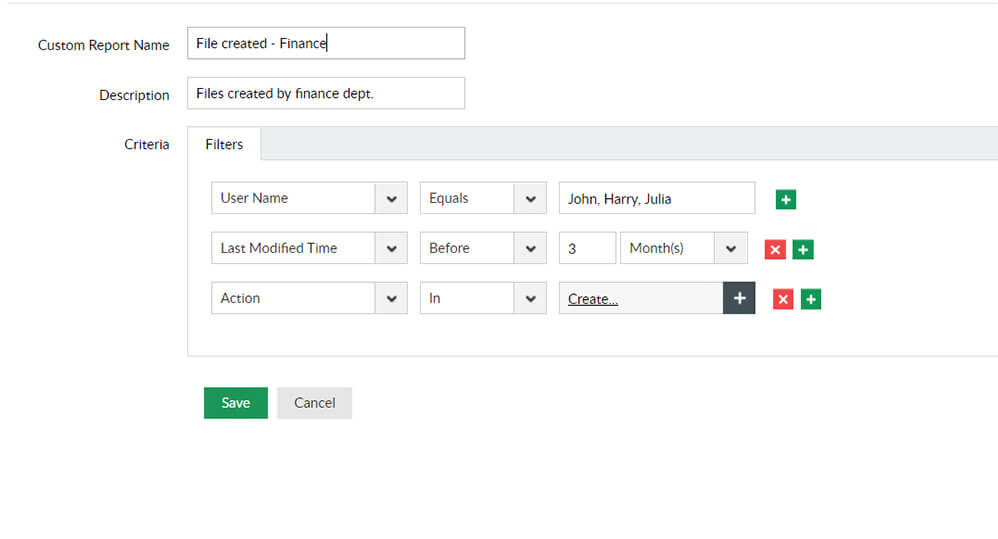
Identify standard and typical user changes to files on your servers. Track commonly accessed or modified files to ensure each user access is authorized.

Analyze failed file access attempts to gauge which users tried to access sensitive information and when to spot potential insider activity.

Generate custom reports with specific parameters to closely watch user accesses or important file and folder activities, and immediately spot impending security threats.

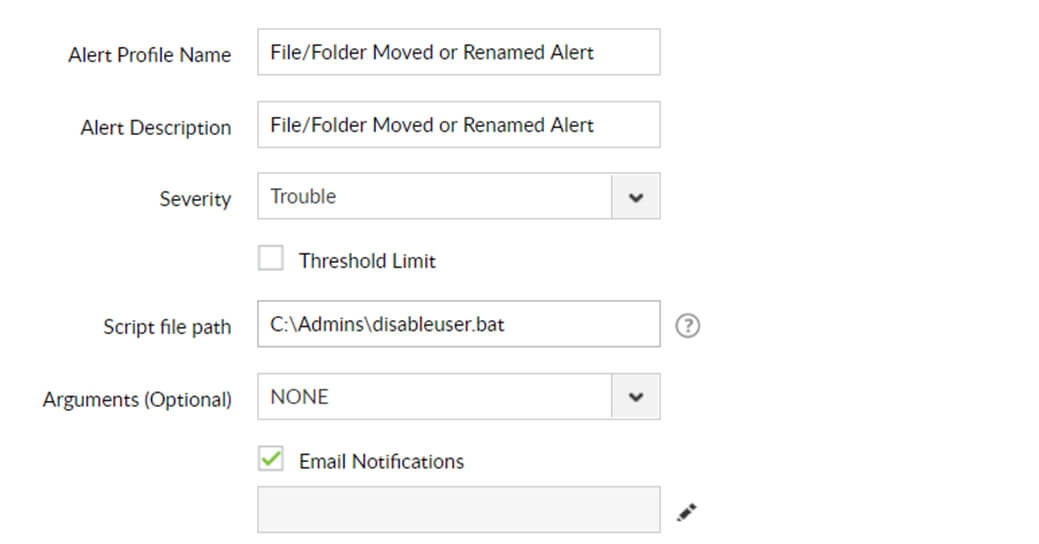
Use threshold and severity alert parameters to prioritize file events and receive instant notifications on events you designate as critical, troublesome, or requiring attention.
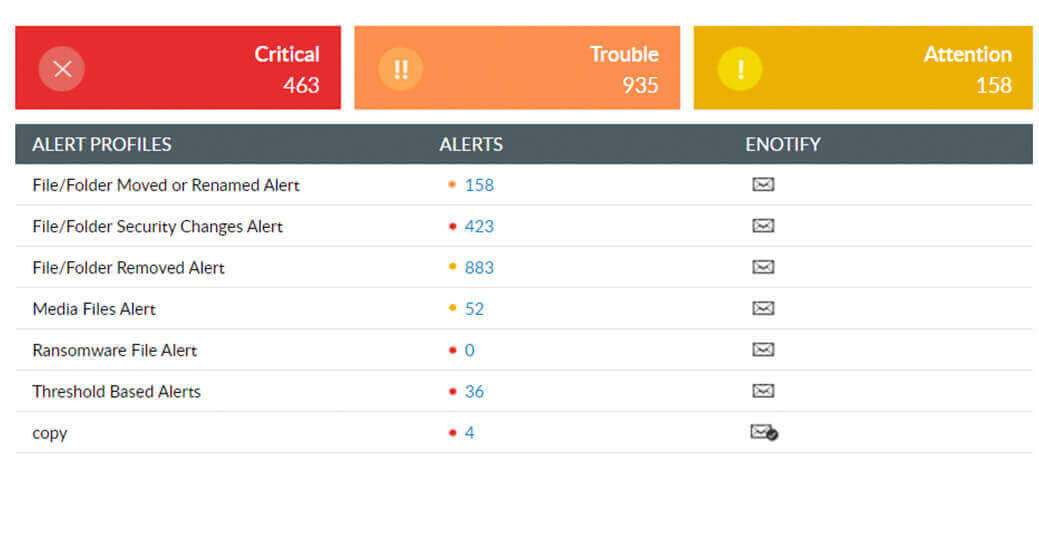
Set up customized script responses to quarantine ransomware-infected devices or shut down compromised user accounts to prevent full-scale ransomware invasions.
Use centralized audit data to perform root-cause analysis of security incidents and observe file access patterns.