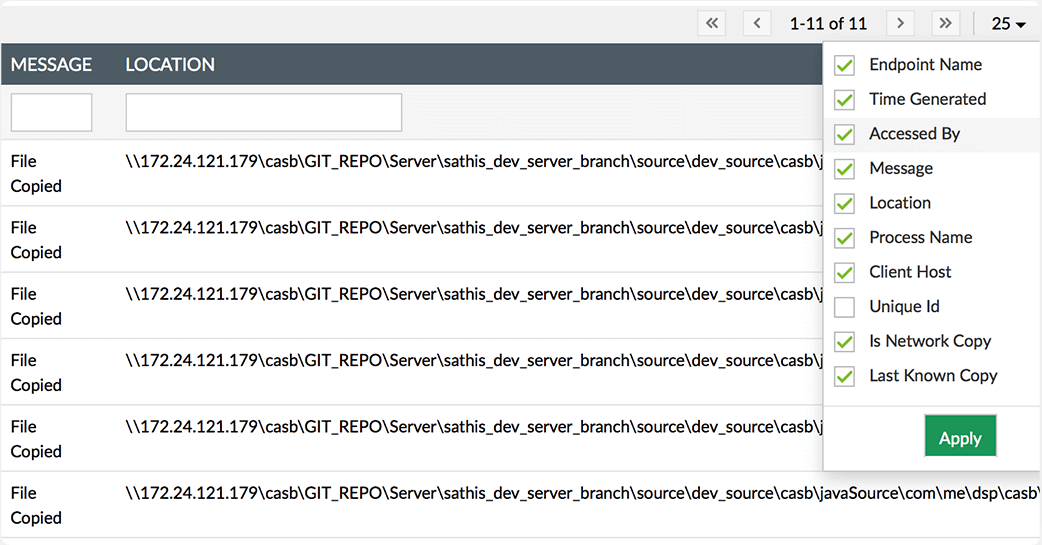
Monitor and correlate file copy and paste actions from a single report.
Audit files copied to removable storage media, including USBs.
Execute tailor-made scripts in response to malicious bulk file copy actions.
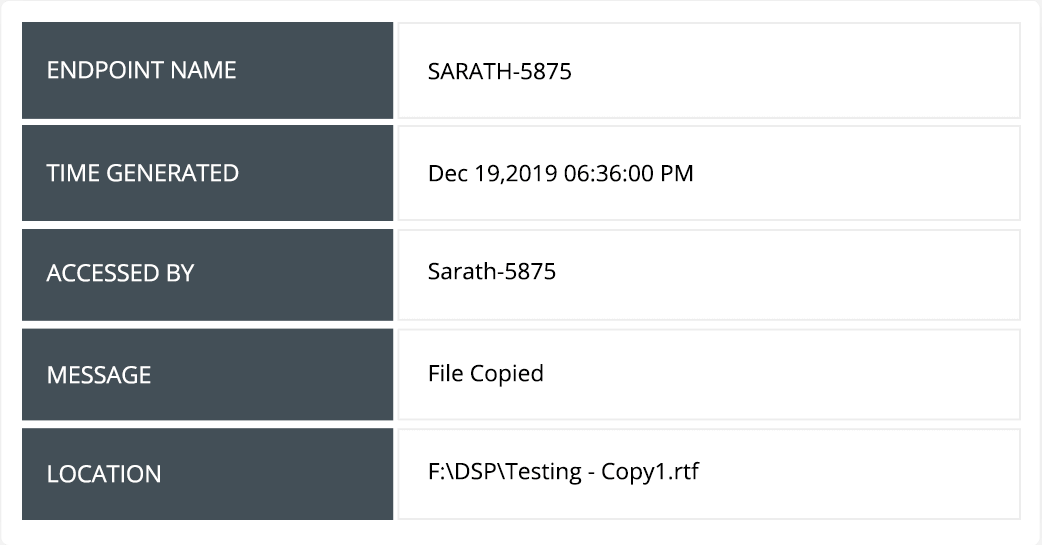
Track and report on significant details such as who copied what file/folder, when, and where it was pasted.
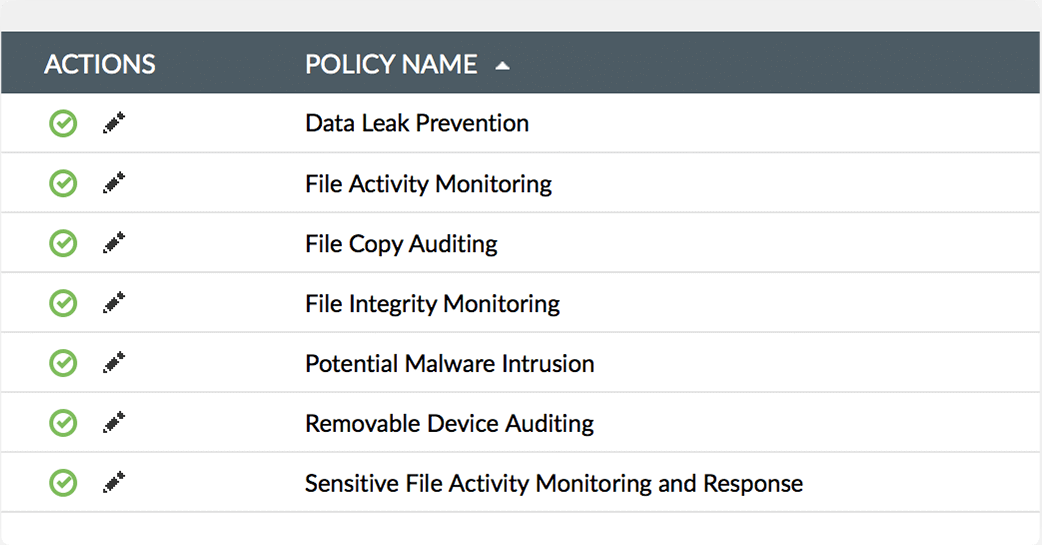
Set up predefined data leak prevention (DLP) policies to track and report when users copy files from workstations, network resources, removable devices, and more.
Use clipboard auditing to detect multiple ways users try to copy and moves files, including Ctrl+C, Ctrl+V, and right-click copy and paste.
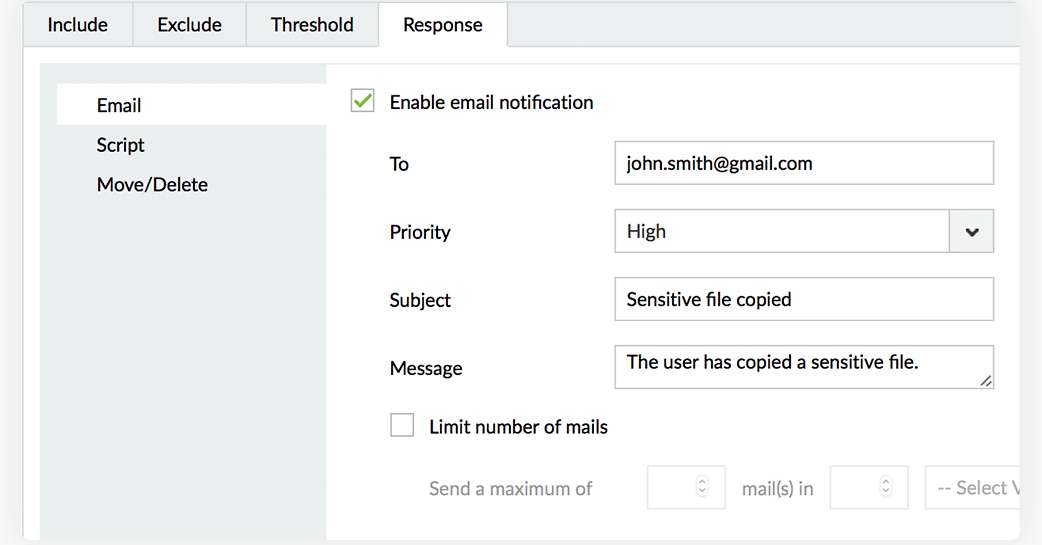
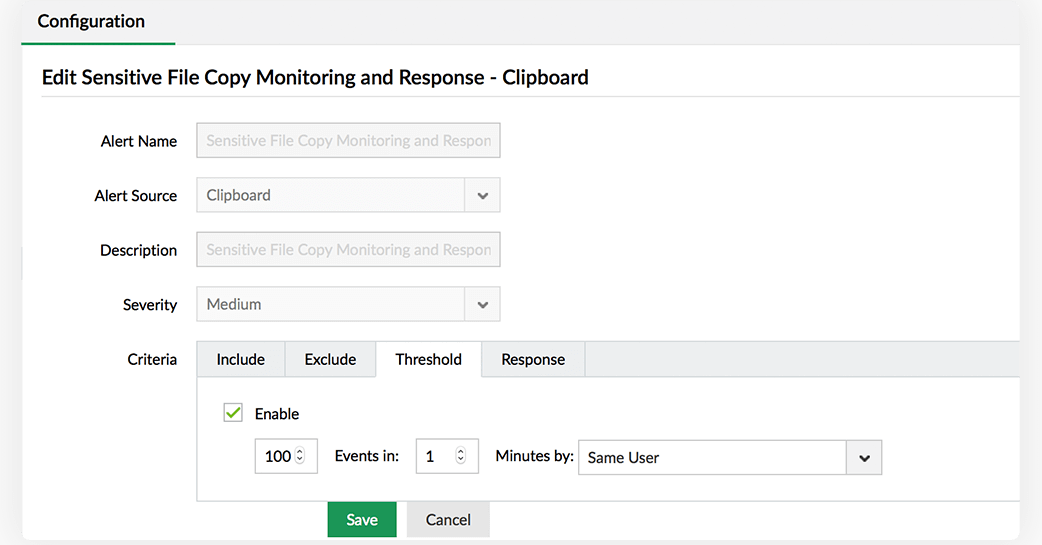
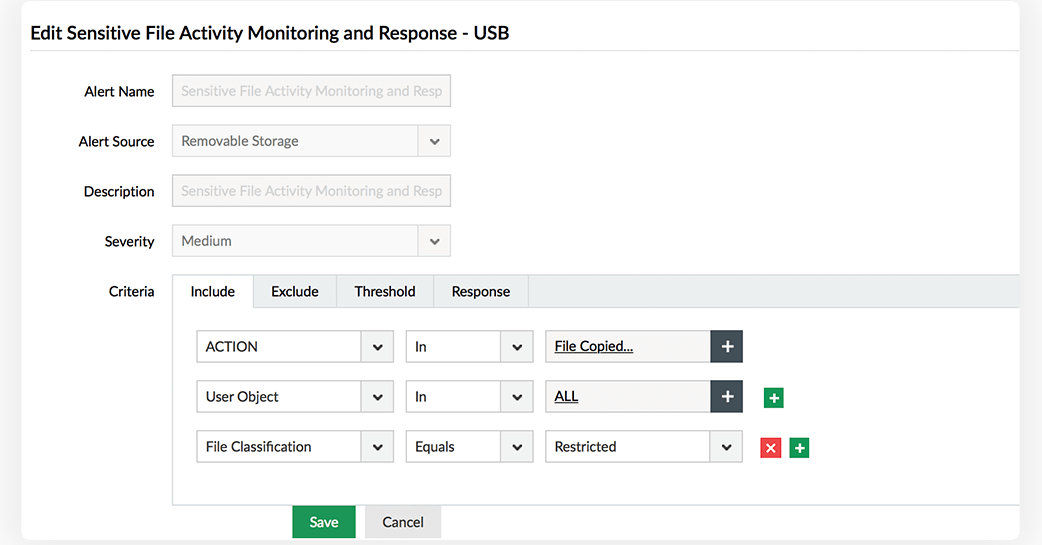
Receive instant notifications when your critical files or folders are moved to unsafe locations, and prevent potential data exposure.
Block USBs when malicious users attempt to copy files in bulk to their workstations or USBs discreetly.
Selectively monitor suspicious users, important files, and unsecured locations for unauthorized file movements in real time.
Look out for any malicious file copy actions within your storage environment and impose real-time restrictions to prevent data leaks.
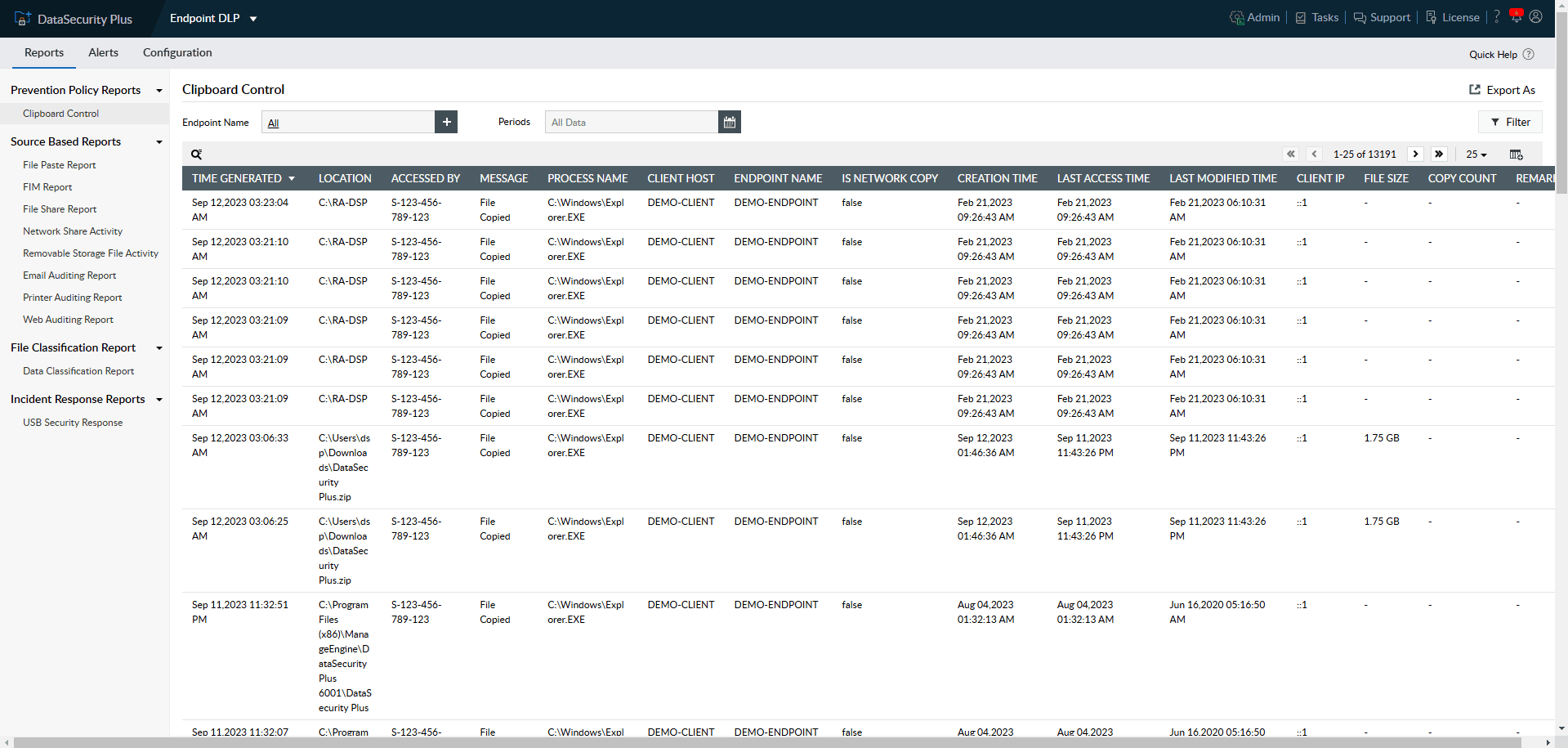
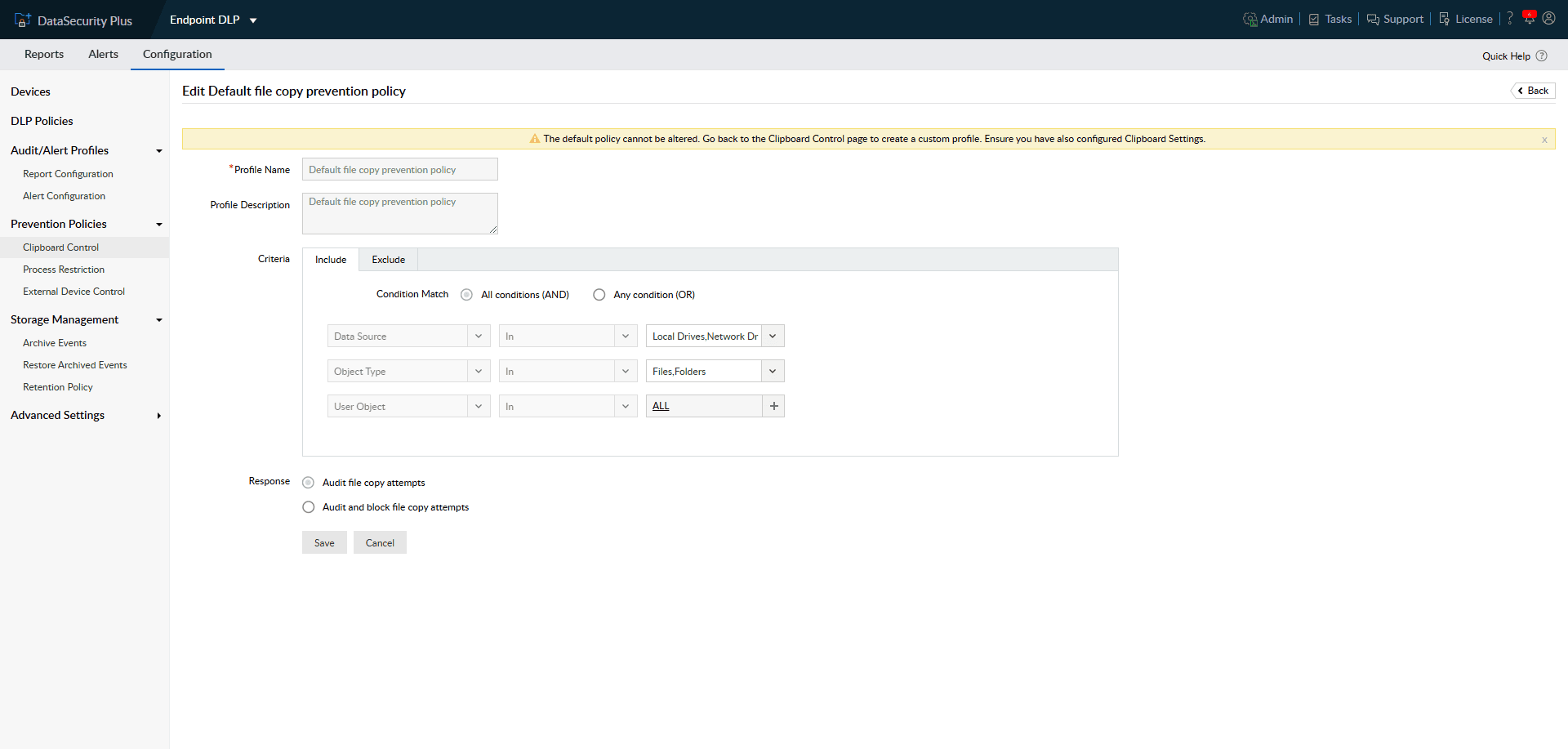
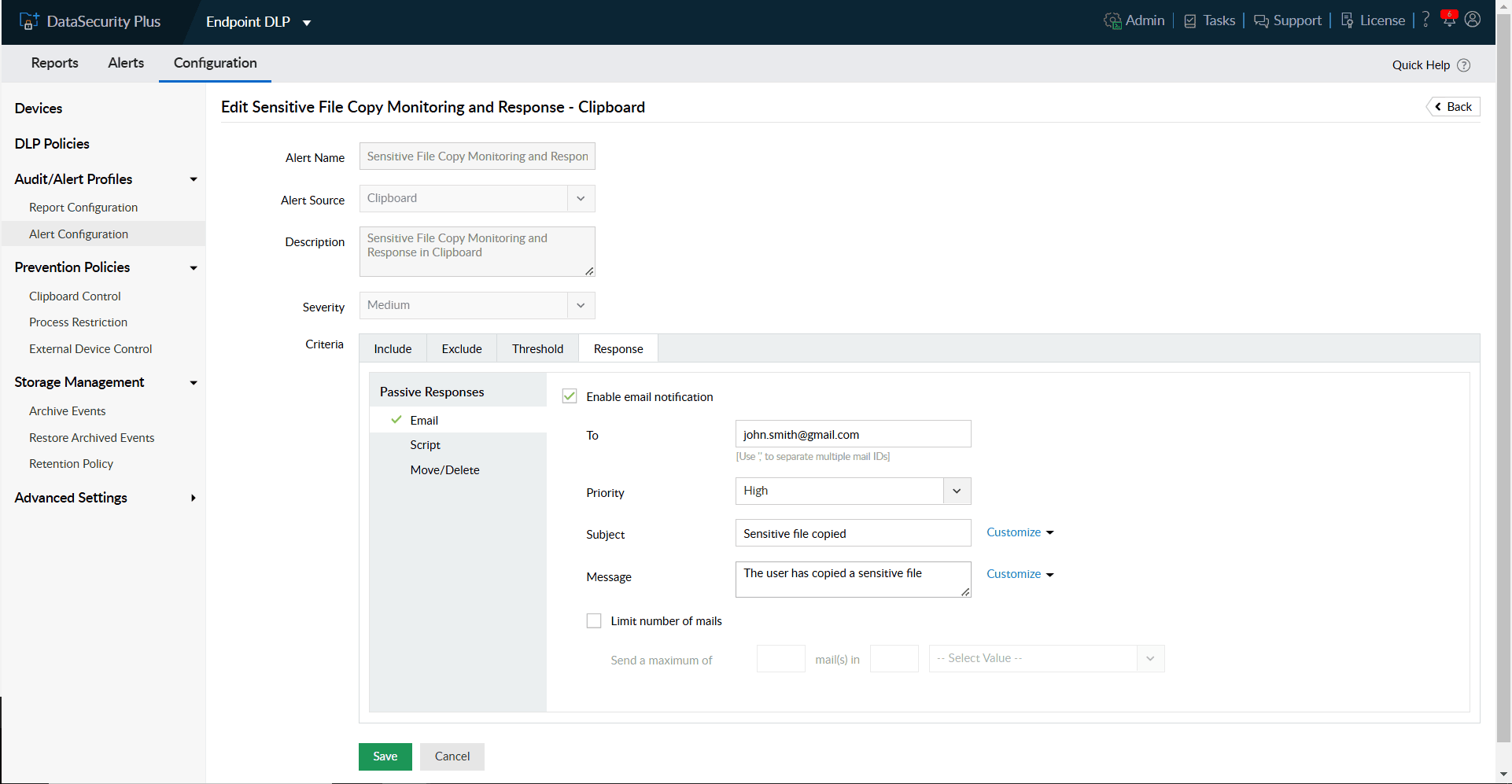
Generate instant audit records on data movements within your organization as legal evidence to comply with IT regulatory mandates.
Use built-in options to quickly identify the source, host name, time, and location for all anomalous file copies.
Generate instant reports on removable device usage and data transfer activities to and from USBs across your organization.

Use default policies to audit clipboard actions, and create custom policies to audit and block clipboard actions

Customize default DLP policies to include suspicious users, and exempt trusted users and groups.
Detect sudden anomalous spikes in files copied using customizable threshold values.
Use automated threat response mechanisms to execute scripts tailored to your organization's needs.

Leverage automatic and manual classification capabilities to sort risky files with sensitive data.