Manage web access through browsers and APIs by setting allowlists and blocklists to control employee access to specific web apps.
Protect your critical data by restricting unauthorized file transfers to and from various cloud applications.
Know which cloud apps are most used, which users have the most upload and download requests, and other useful metrics.
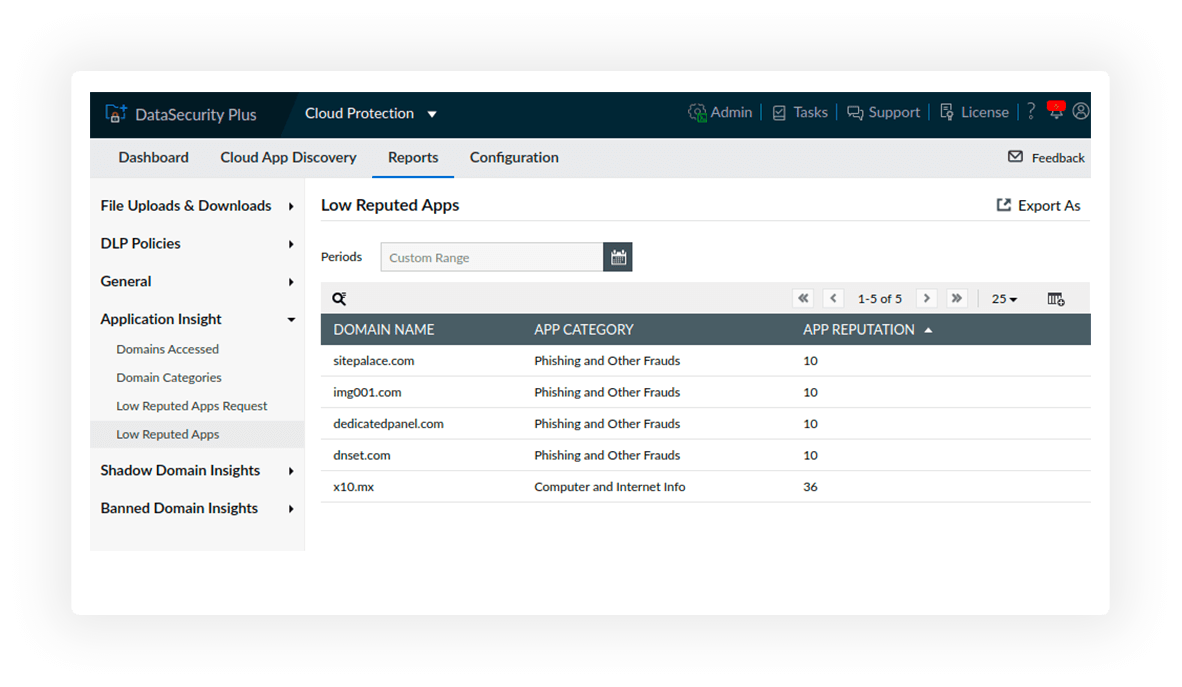
Use app reputation scores to identify low-reputed apps—ones that might contain malware, abusive extensions, and malicious and intrusive ads—and ban them.
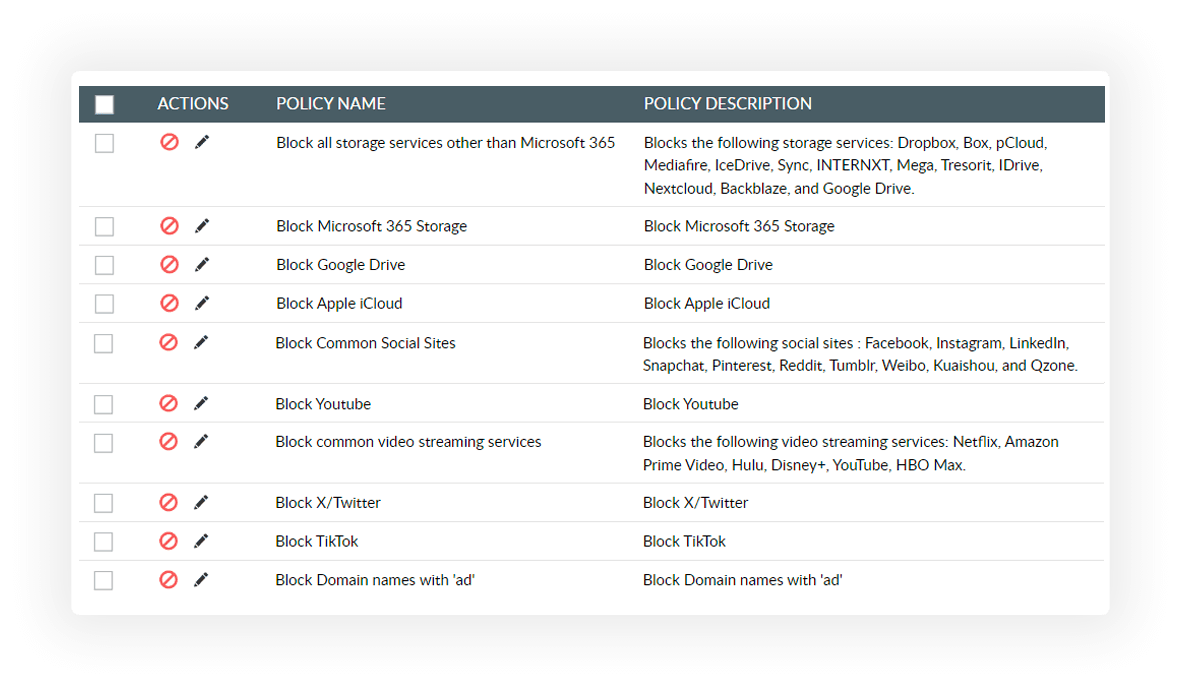
Block a range of cloud apps—including streaming, social media, gaming, storage, file-sharing, and spam—to reinforce security and boost productivity.
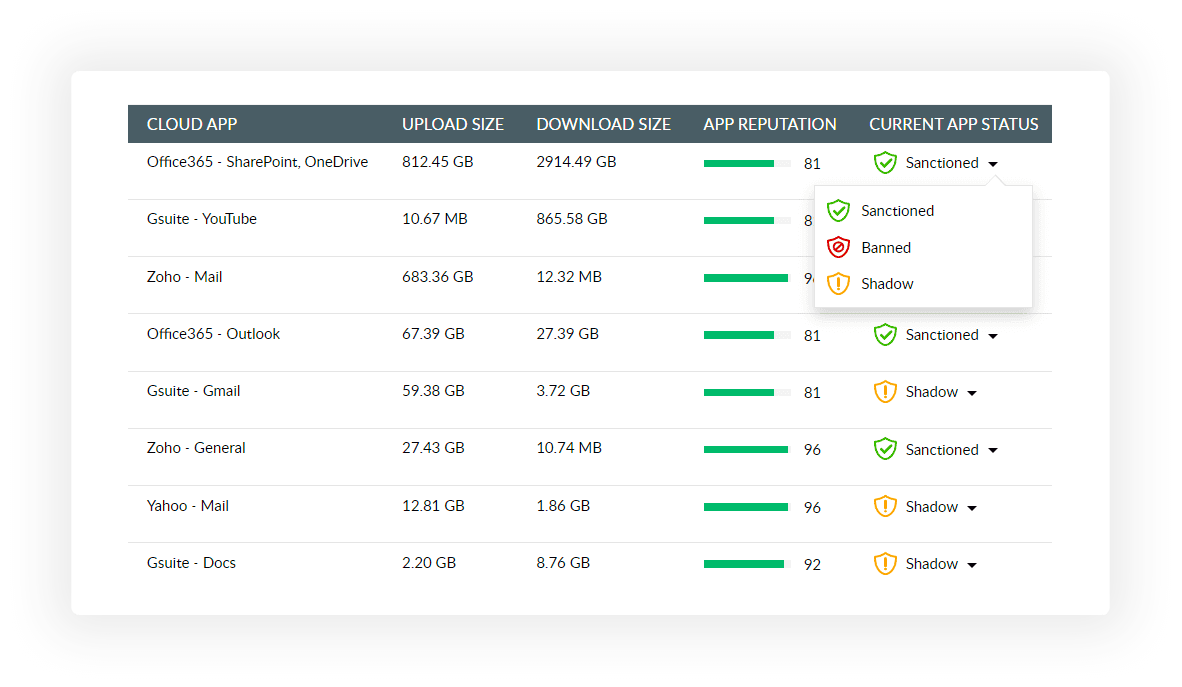
Discover cloud shadow apps in use, evaluate their risk and compliance levels, and decide to allow or ban them.
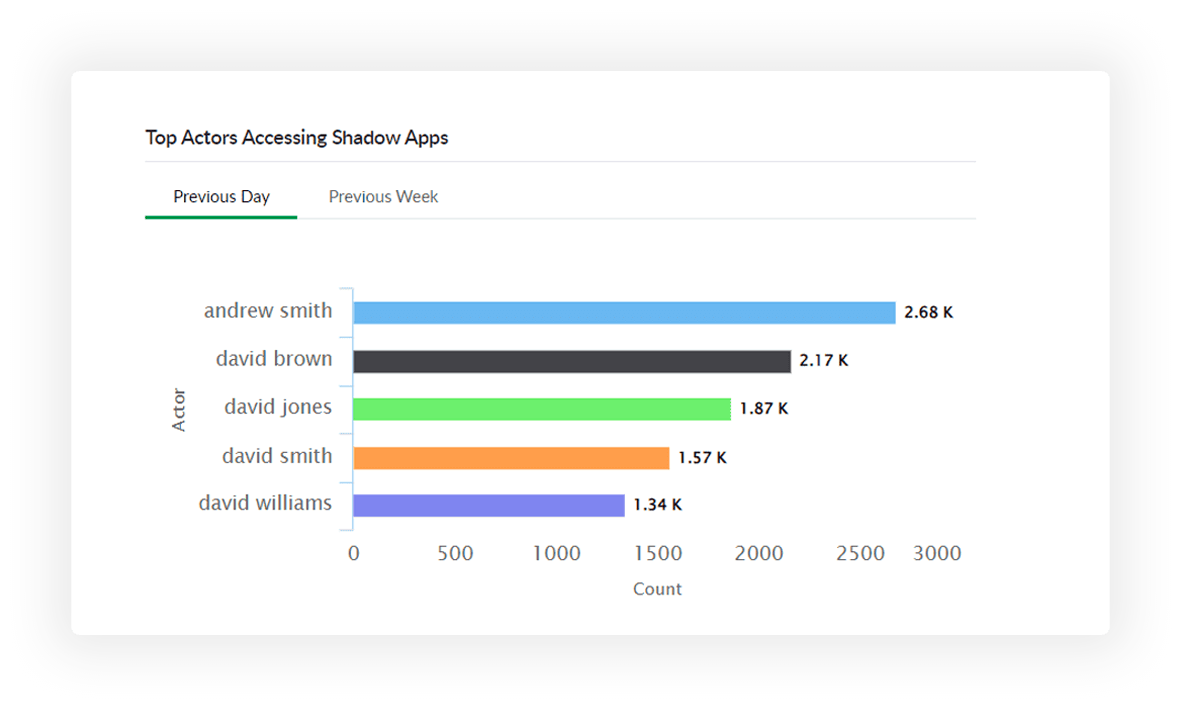

Find high-risk users who access unsafe, unauthorized, and shadow applications the most.
Allow file uploads to sanctioned cloud sharing platforms and block others to prevent data loss.
Restrict users from downloading malicious content from low-reputed cloud applications to protect against ransomware attacks, spam campaigns, credential theft, and more.
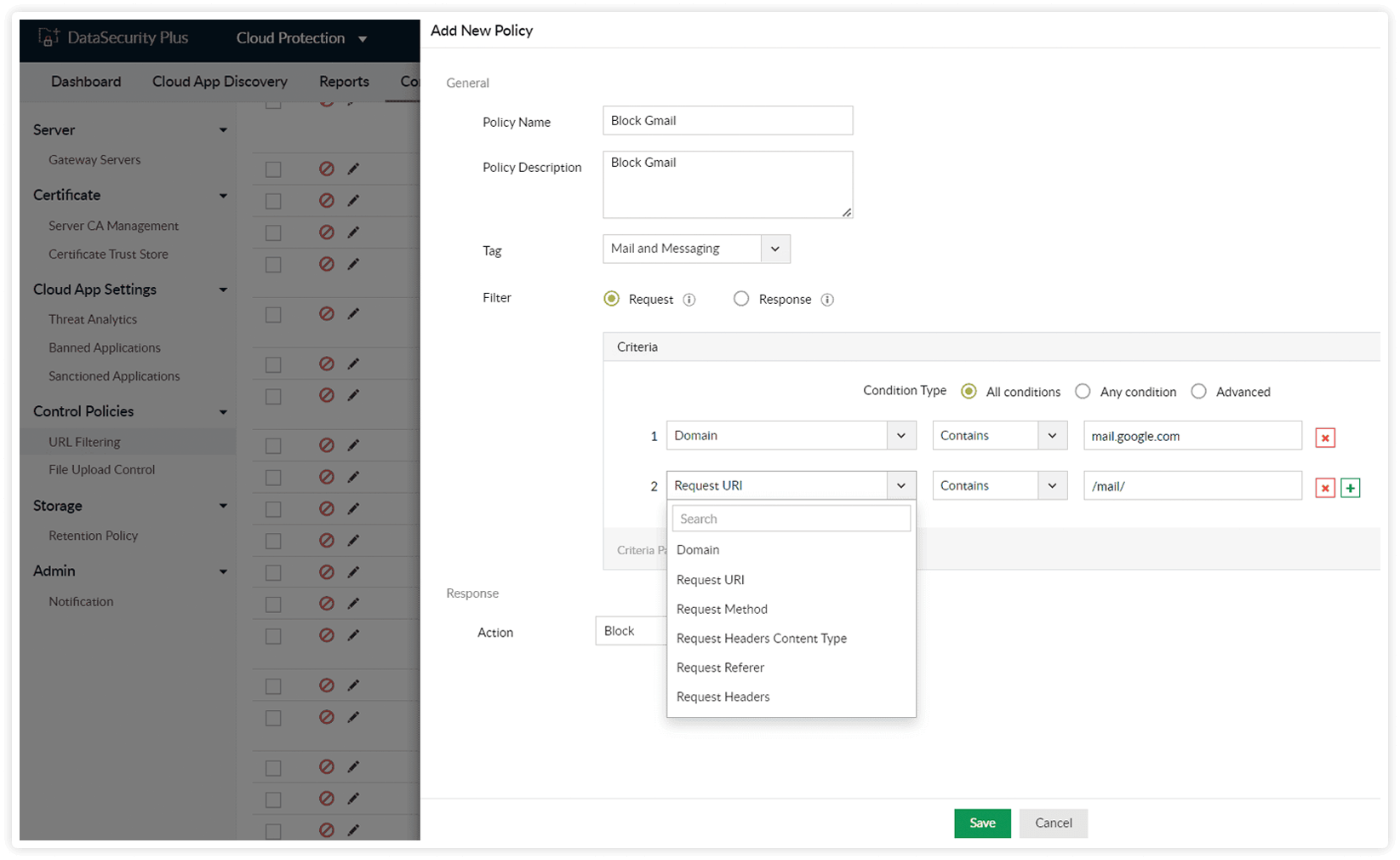
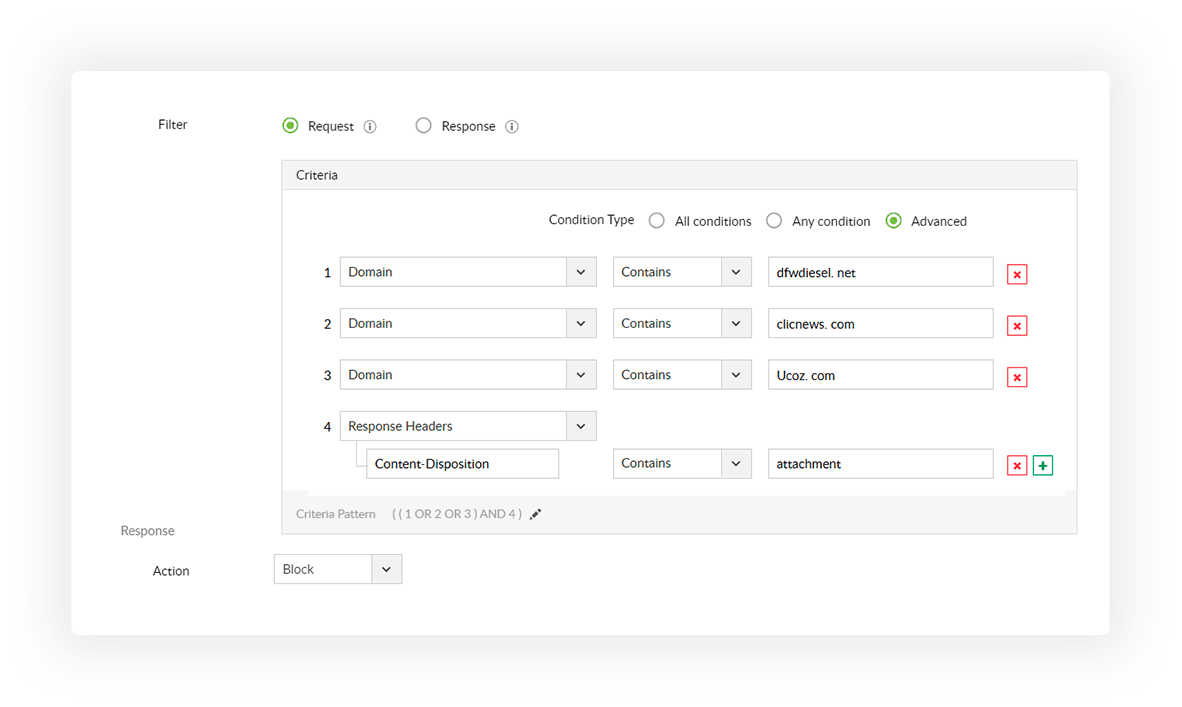
Leverage our built-in list of malicious domains or create custom filtering policies to protect your organization from online security threats.
Filter by request URI to block specific resources within a domain, filter by content type to block specific content types, and much more.

Get info on all cloud app access requests, categorize the list of banned and shadow apps, and identify who accessed them the most.
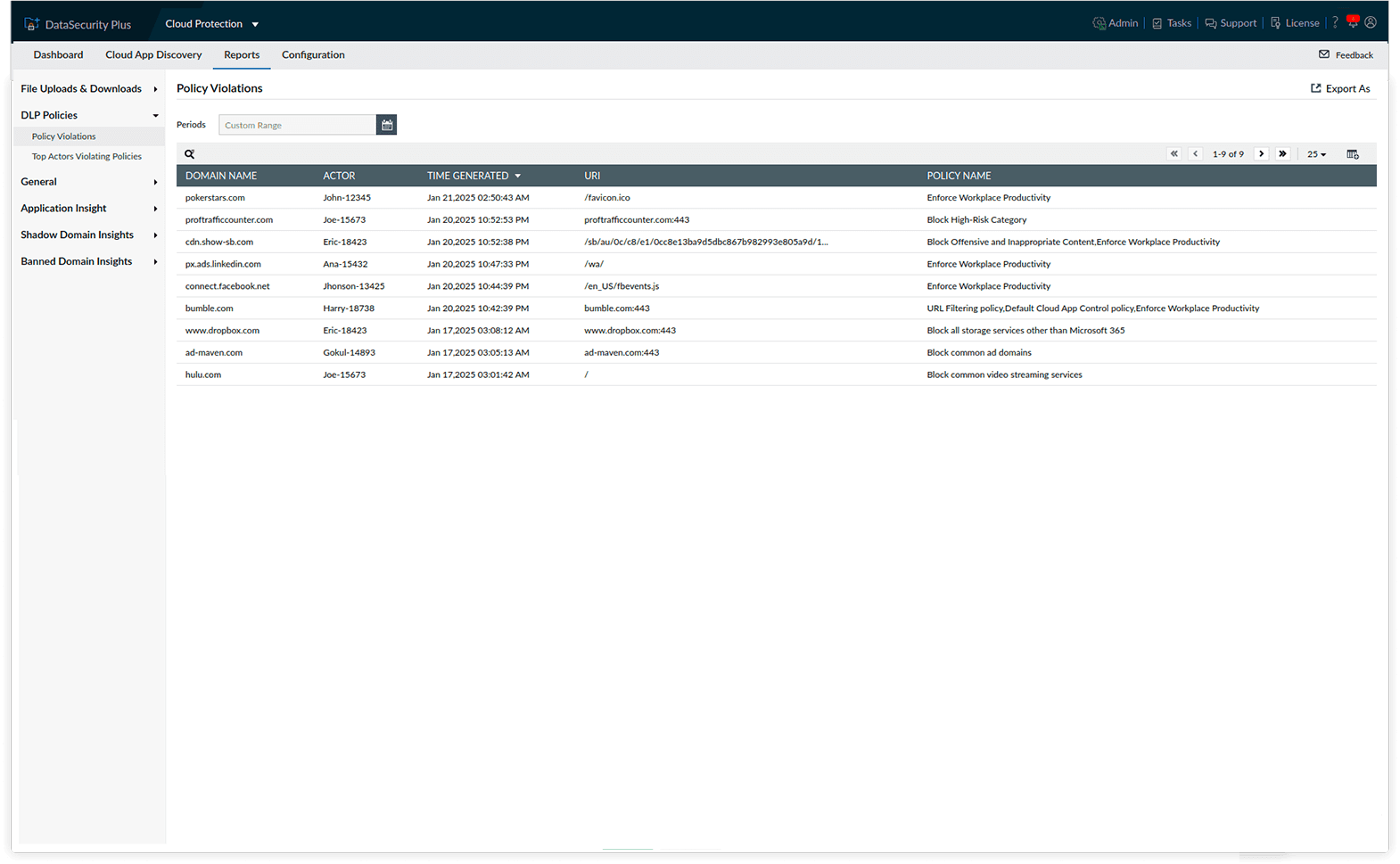
See who breached DLP policies, the domains accessed, and the time of the attempts—all from the policy violation reports.
Comply with CIPA using policies that block inappropriate, obscene, and direct communication tools, and monitor breach reports to take prompt actions.

View a snapshot view of cloud app usage, user behavior, shadow applications, and banned applications—all from a single window.
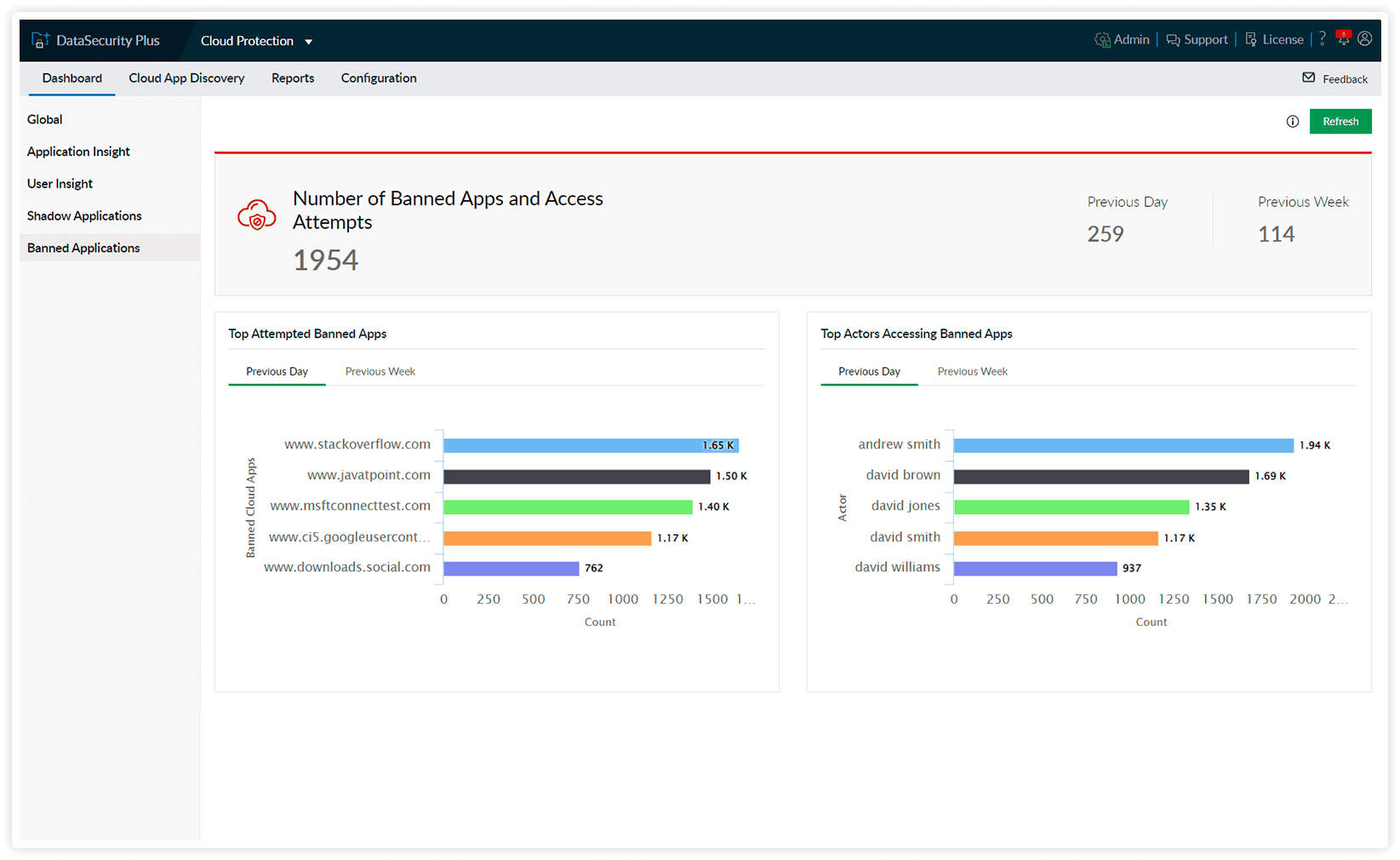
Get graphical representations of access attempts to banned applications and by who.
Use the daily graphs to check sudden spikes in access attempts and use the weekly graphs to analyze the trend of access attempts.

Detect data transfers to and from the web by monitoring upload and download activities.
Prevent data leaks via Outlook by monitoring file attachments for sensitive data.
