Receive immediate alerts when there is a sudden spike in file permission changes.
Track suspicious and unwarranted files activities with detailed reports.
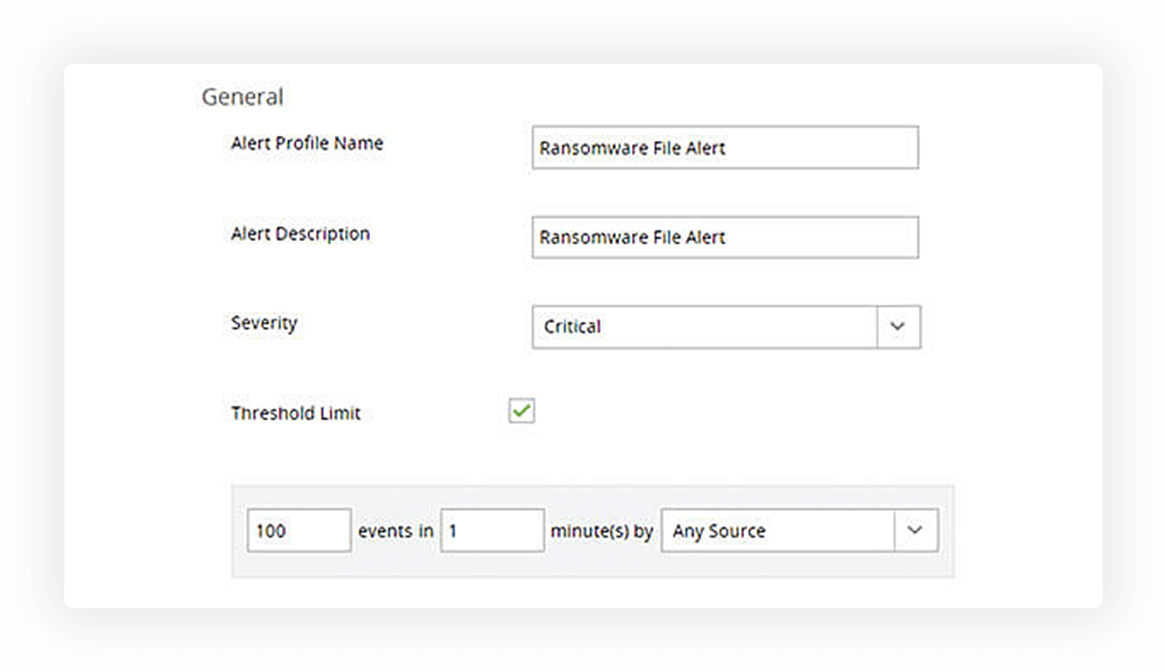
Detect and cut off potential ransomware attacks with preconfigured threat responses.
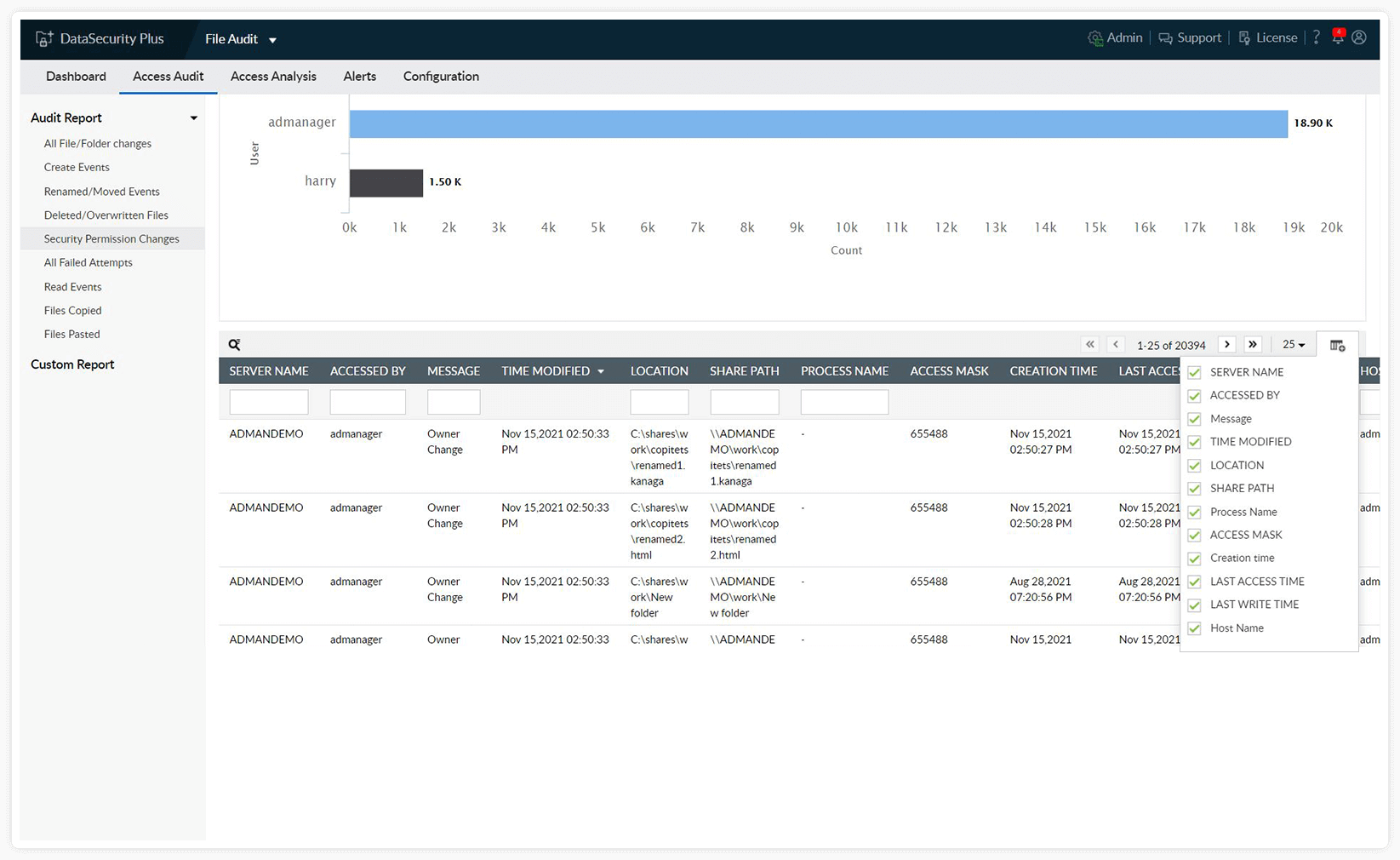
Track all file modifications and maintain a detailed audit trail to ensure data integrity and accountability. Gain firsthand information on who modified a file, when, and from where.
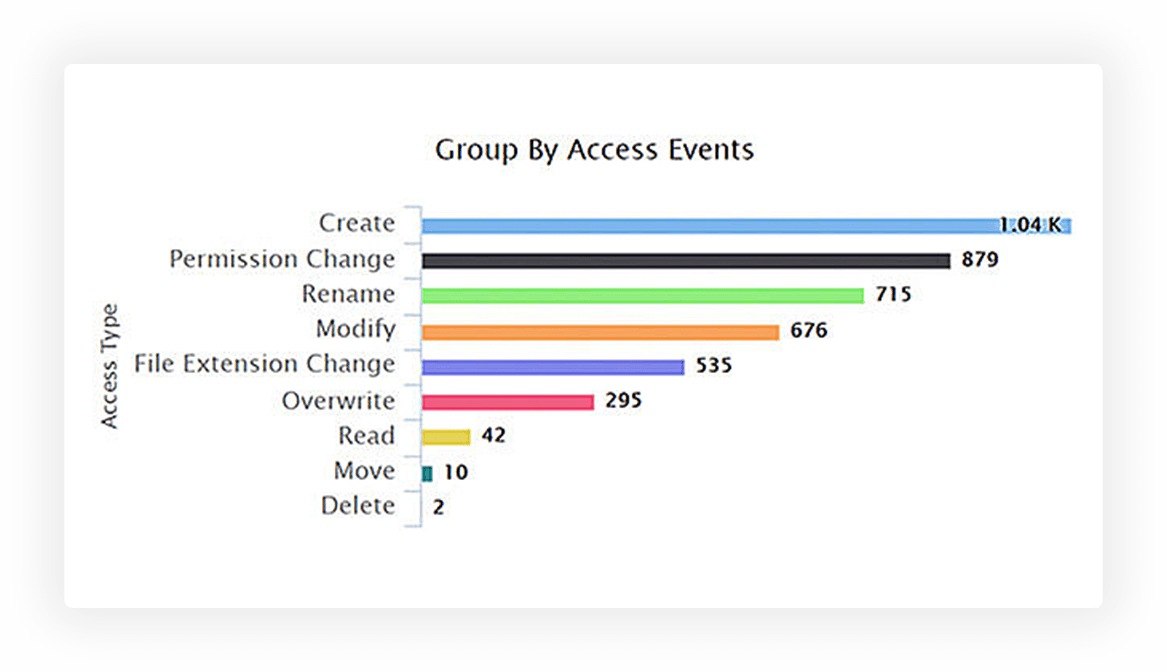
Detect ransomware attacks by spotting indicators like spikes in file rename and permission changes. Quarantine ransomware infections using threat responses.
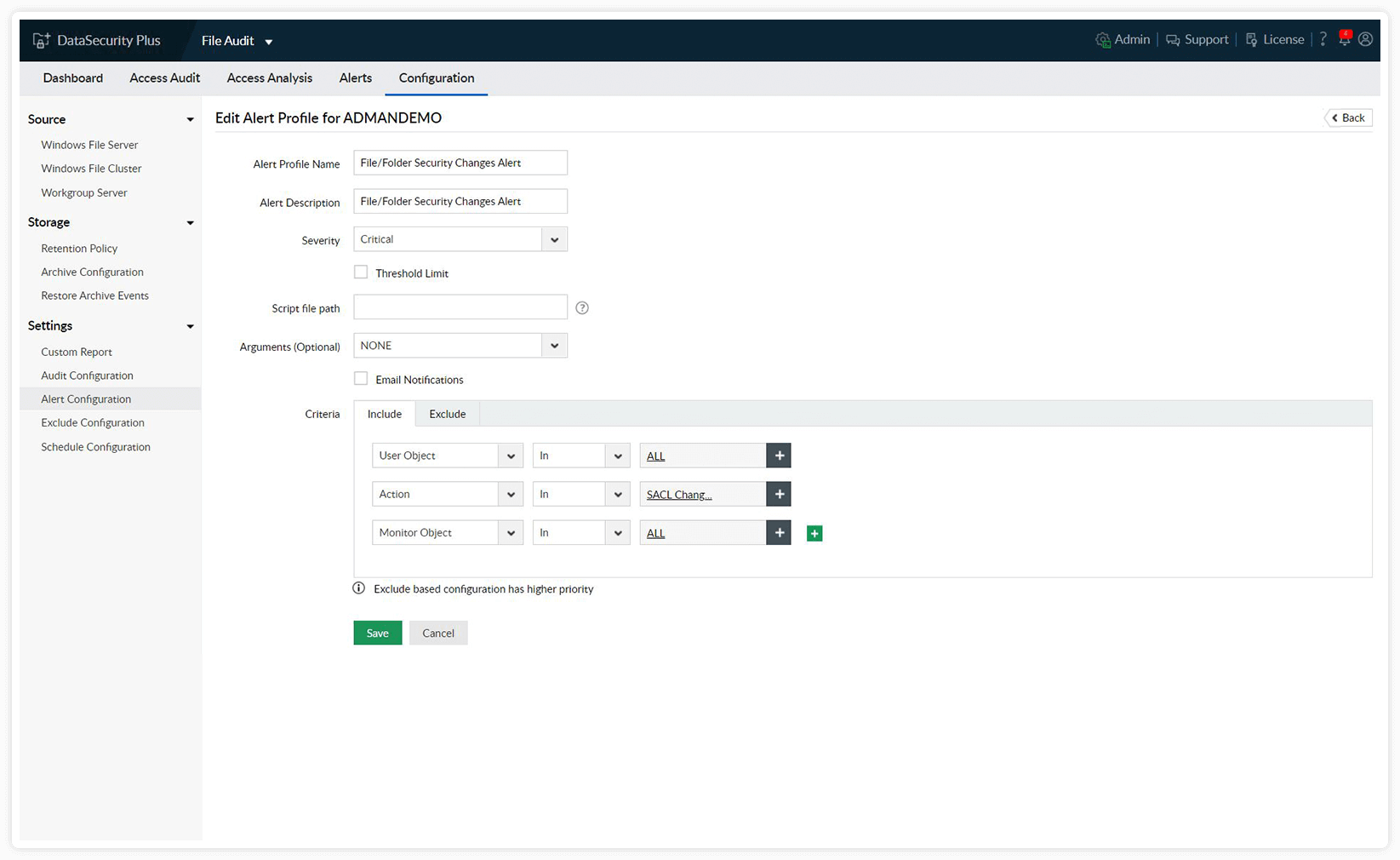
Monitor high-risk file activities including SACL, owner, and permission changes. Trigger instant alerts based on the intensity of the threat they pose to your organization.
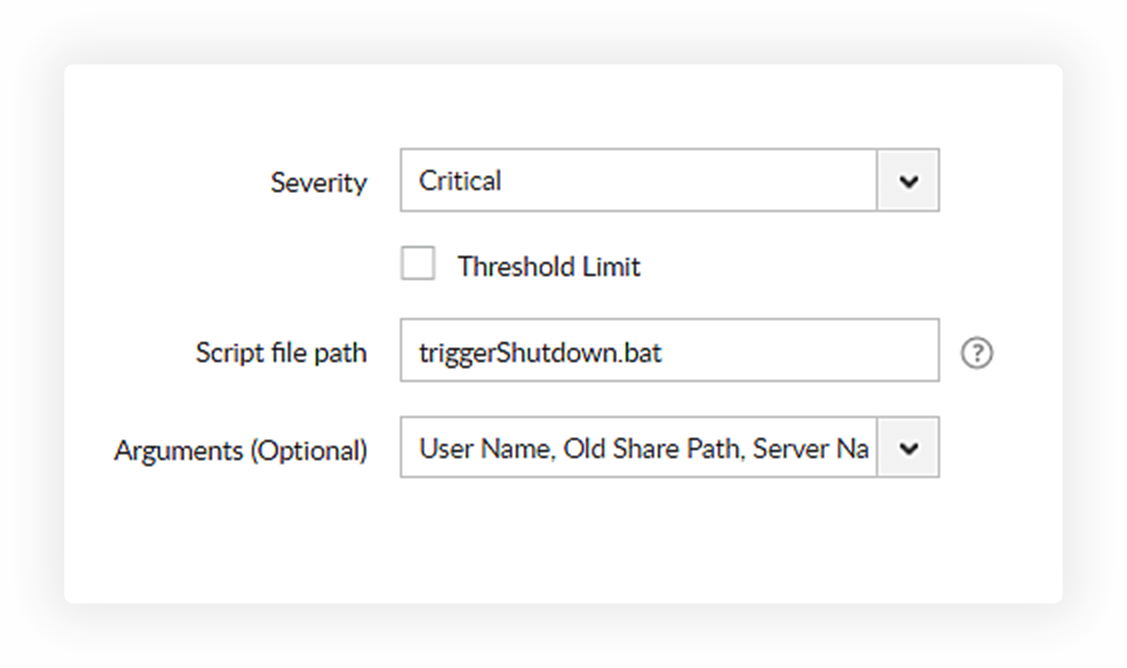
Use our default scripts or create your own to cut off ransomware infections, shut down infected devices, disconnect rogue users sessions, and more based on the security alert triggered.
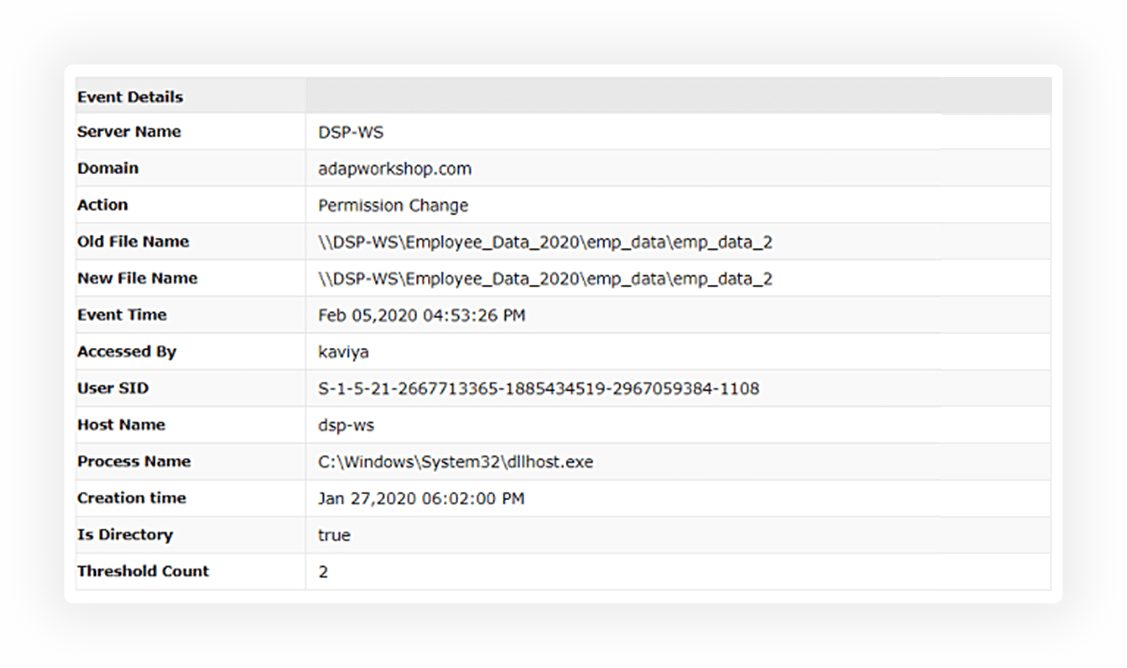
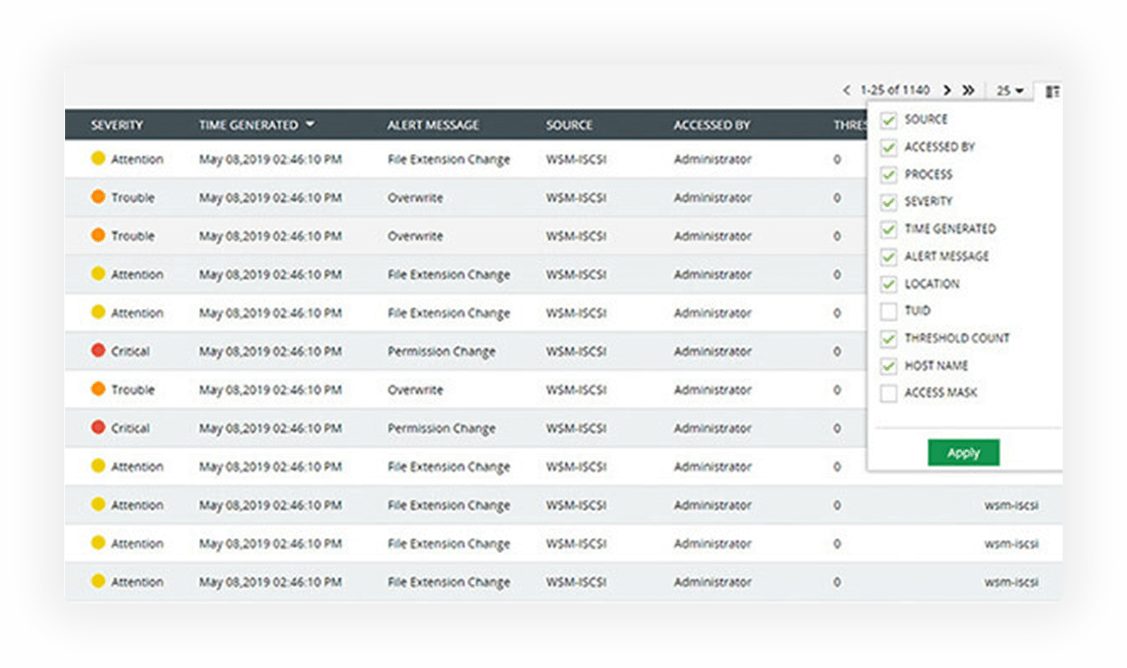
Find contextual and actionable details for every alert triggered including details on what triggered the alert, the process involved, when it was triggered, and much more.
Use our extensive audit-ready reports to meet the various requirements mandated by the GDPR, PCI DSS, HIPAA, and more. Store historical audit data to help with legal and forensic requirements.
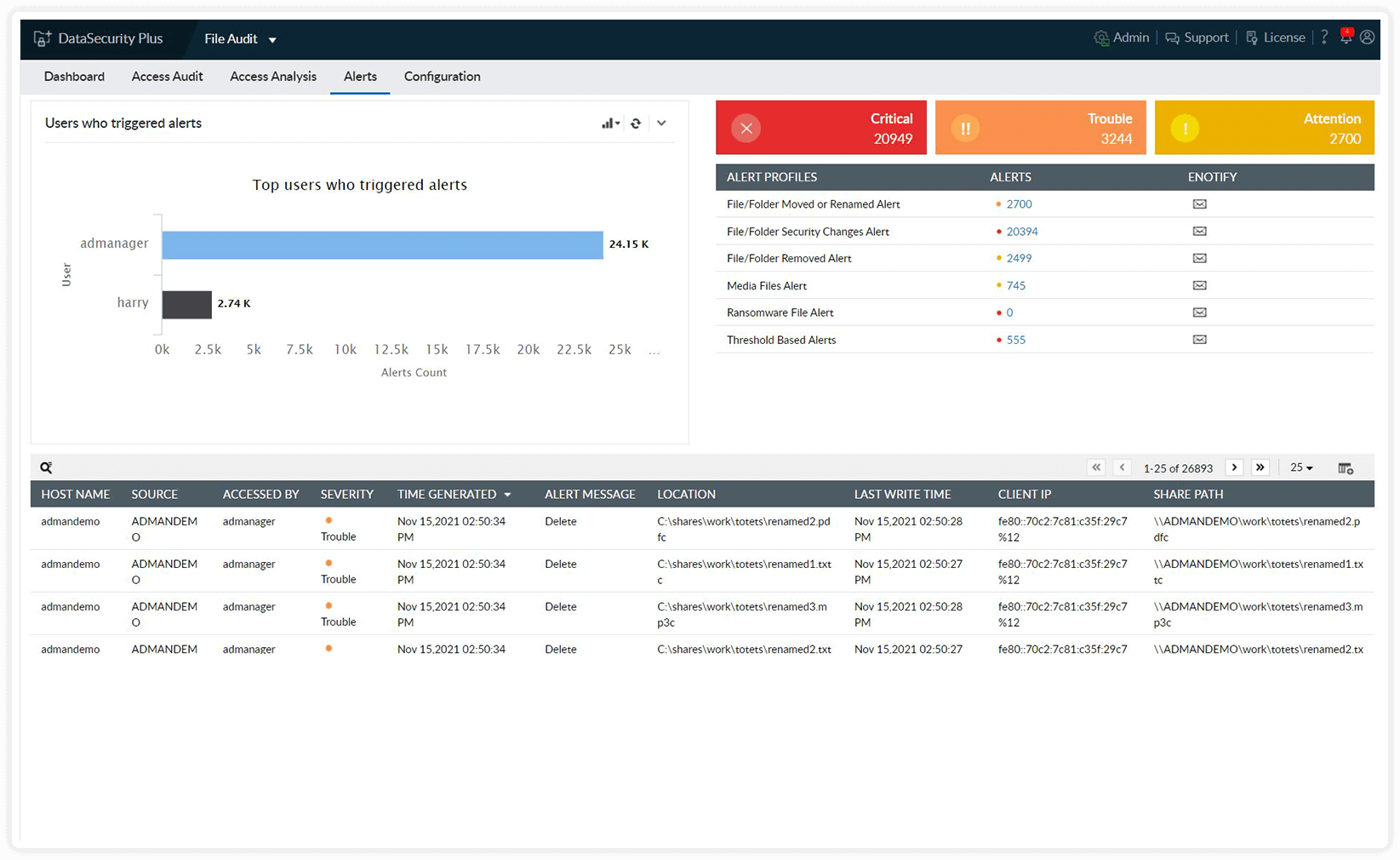
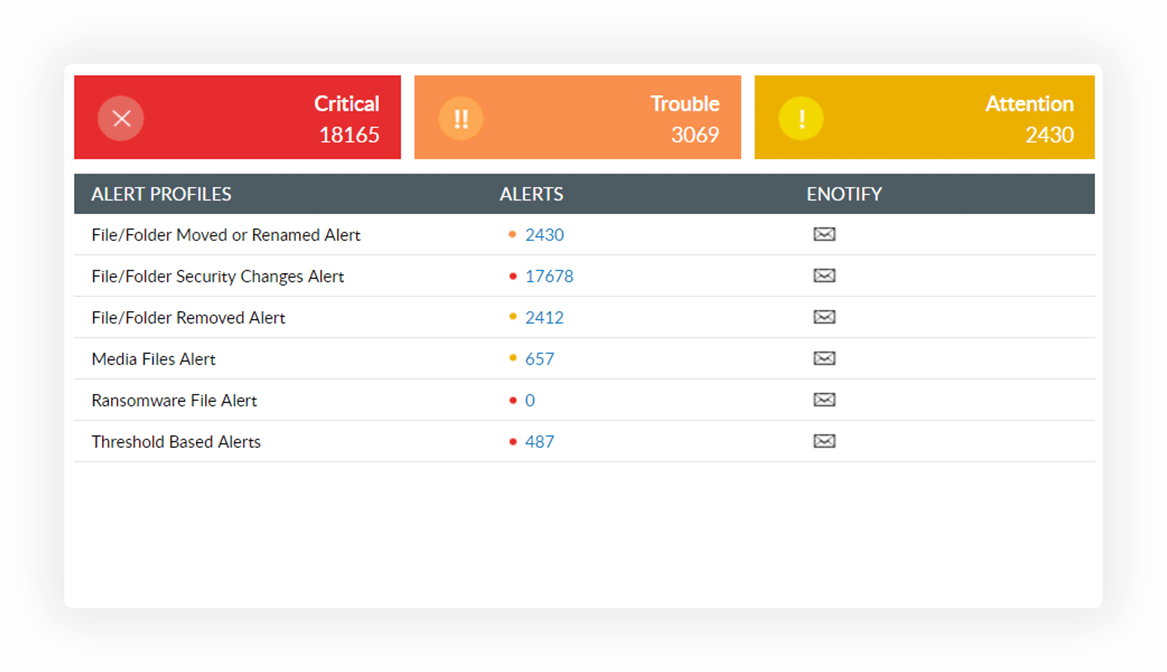
Speed up incident detection with default alerts for malware, access anomalies, or other significant events. View severity-specific event counts and get detailed reports for each.

Find breach sources by filtering reports according to your needs and analyzing each entry. Promptly locate infected files and respond accordingly.
Identify anomalous activities and non-compliance effortlessly. Ease analysis by searching for events triggered by specific users or sources.

Set alerts for specific events. Monitor critical files and folders, and get notifications when a user modifies them.
Receive alerts when file servers record a suspiciously large number of activities by establishing safe limits unique to your enterprise.
Automate responses to security incidents. Disable compromised user accounts, shut down infected devices, or create your own response strategies as per your enterprise's needs.

Scan for business-sensitive content and protect it from leakage via USBs and Outlook email.
