Detect and shut down potential ransomware attacks instantly.
Quickly spot unauthorized file modifications, sudden spikes in permission changes, and more.
Meet HIPAA and PCI requirements with our file integrity monitoring software.
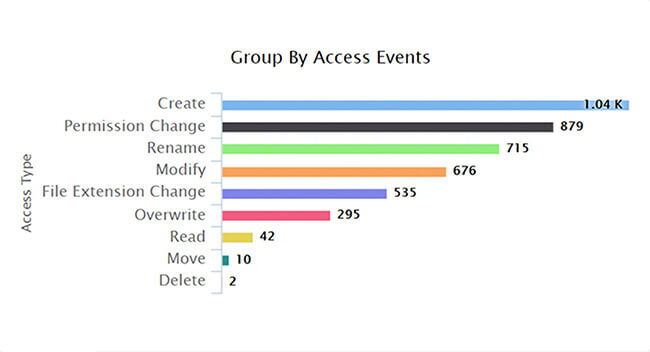
Monitor all changes made to your file servers including permission changes, file creation, move and modify events, and more in real time.
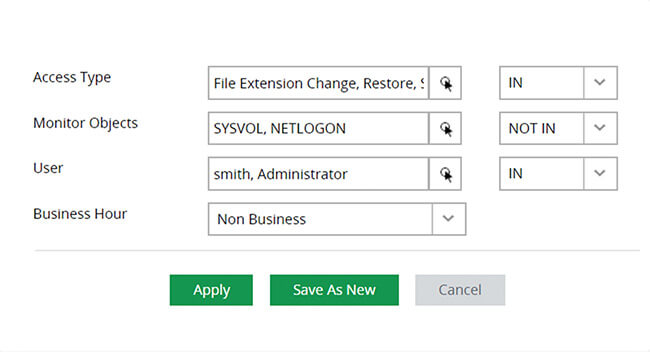
Pinpoint any unauthorized changes by selectively monitoring critical files, folders, suspicious users, and file changes after business hours.
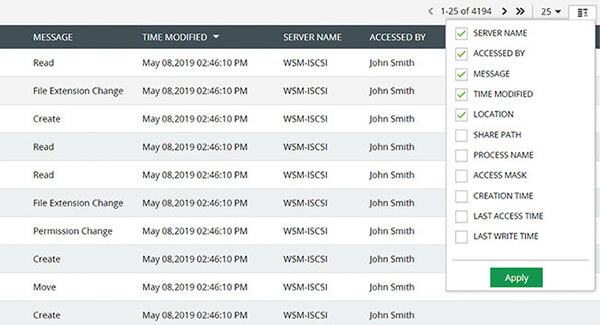
Use actionable, accurate data to quickly identify the source, host name, time, and location for all anomalous file events.



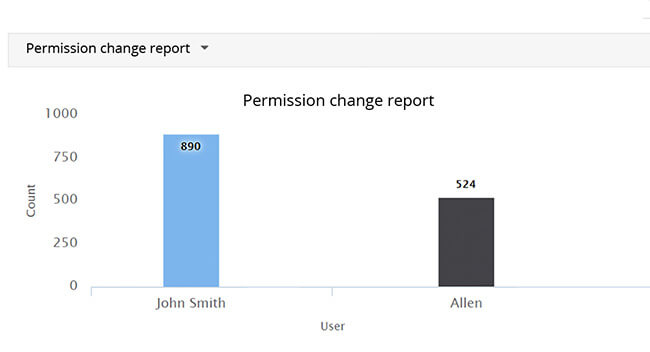
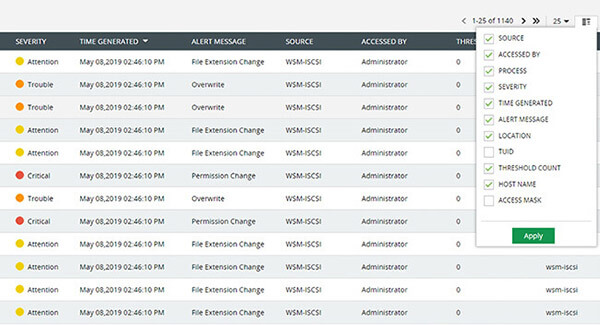
Prevent privilege abuse by detecting sudden spikes in access events, anomalous permission changes, and excessive delete or rename events.

Receive alerts when file servers record a suspiciously large number of events based on user, time, or action by establishing safe limits unique to your organization.

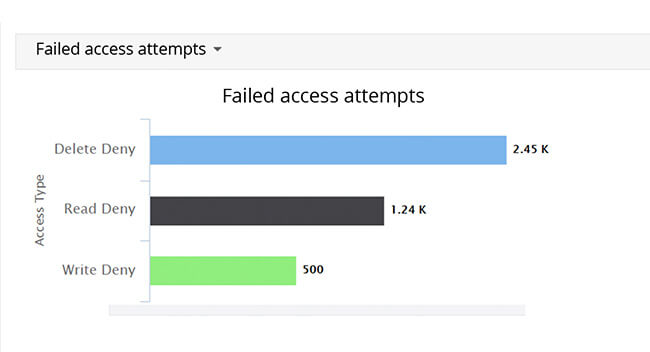
Monitor multiple failed access attempts made by suspicious users before they become critical security issues.

Speed up incident detection with default alerts for malware, access anomalies, and other threats. View the severity of specific events with detailed reports.
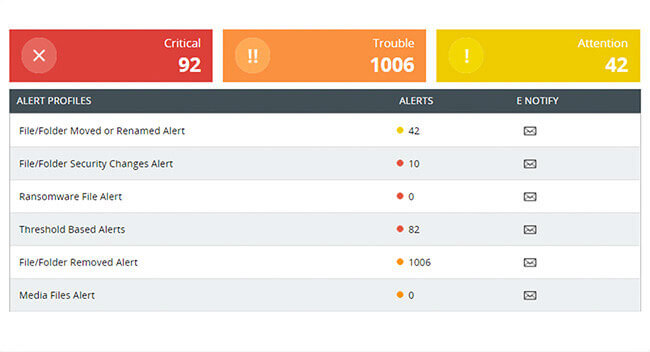
Generate real-time alerts for malicious events like unauthorized access, privilege escalation, and time-sensitive attacks like ransomware.
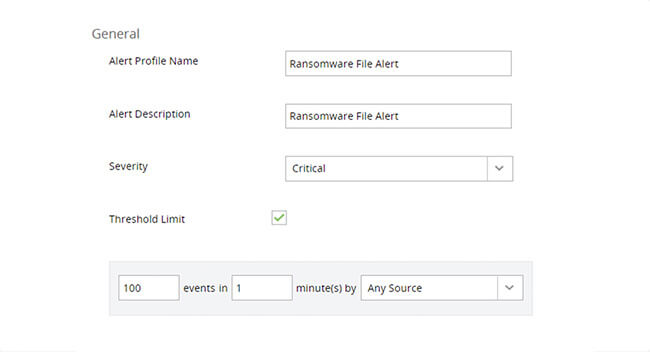
Disable compromised user accounts, shut down infected devices, or create your own response strategy to security incidents.
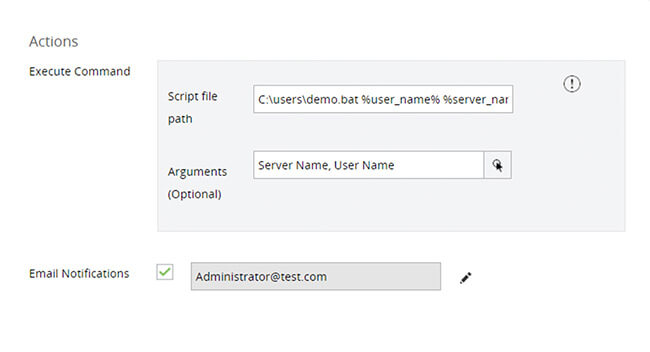



How DataSecurity Plus' file integrity monitoring solution helps achieve PCI DSS compliance
How to protect your organization from ransomware
10 best practices to prevent insider threats