Track critical file accesses instantly using the centralized access audit log.
Perform root cause analysis to locate the origin of security incidents.
Maintain audit trails and comply with IT regulations such as PCI DSS, HIPAA, SOX, etc.
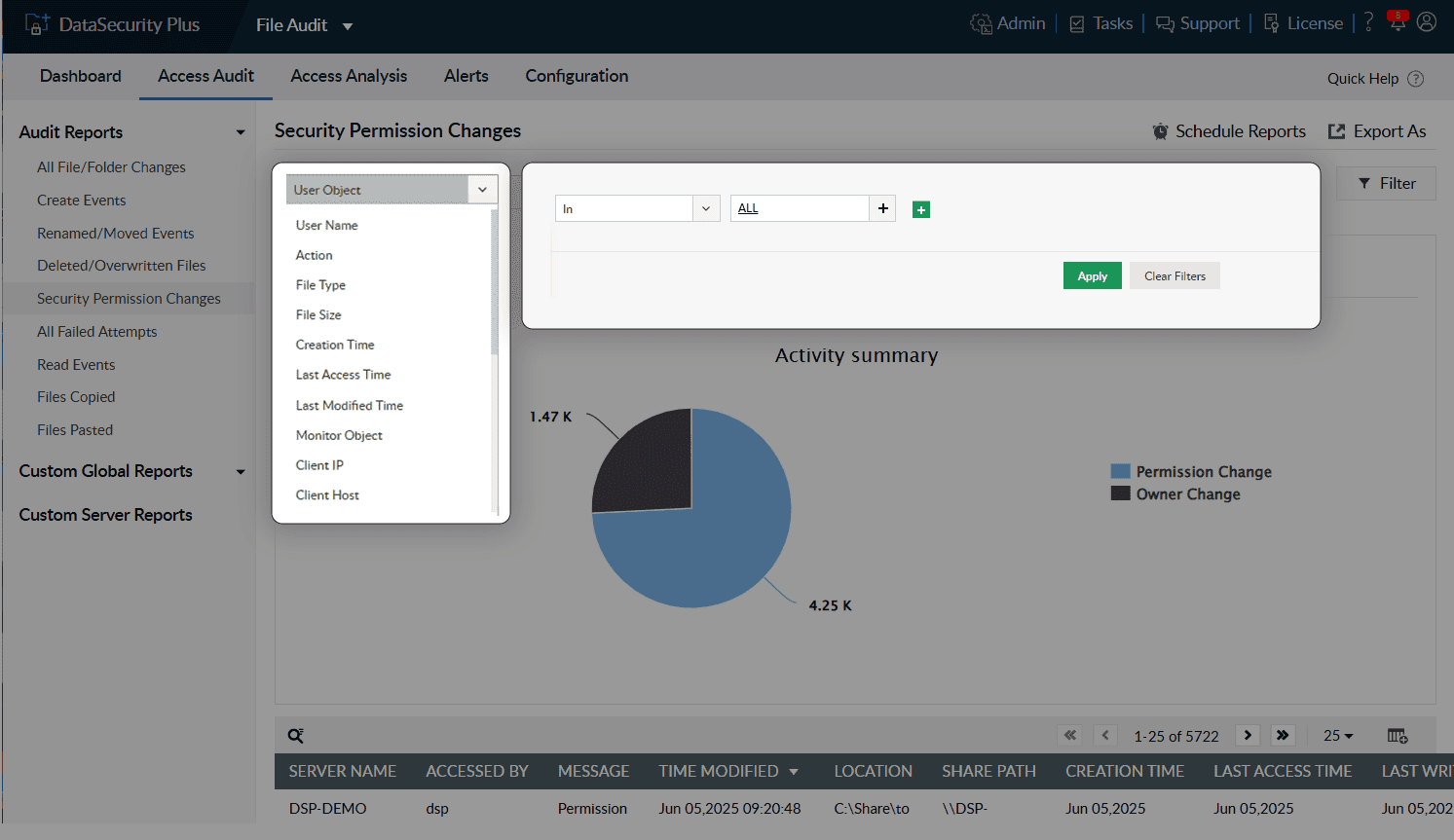
Track all file and folder events—read, create, modify, overwrite, move, rename, delete, and permission change events—happening in your file servers.
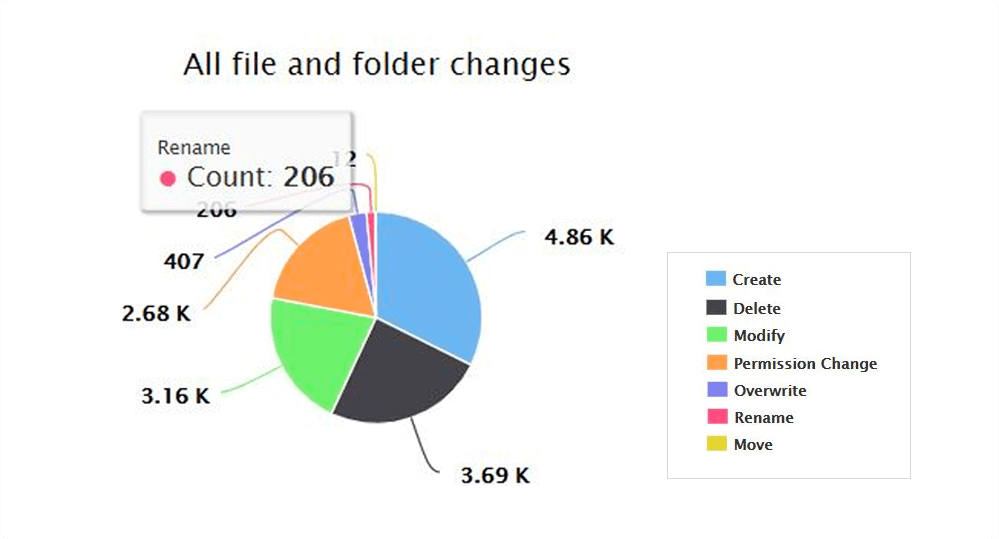
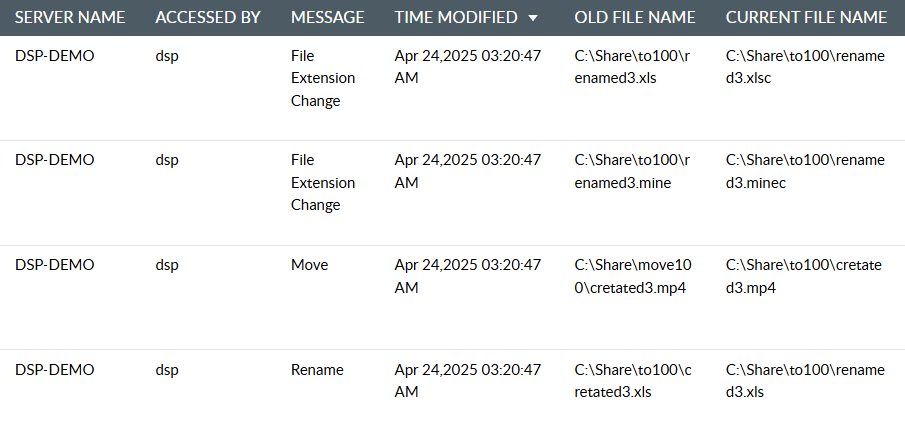
Easily locate renamed or moved files, and generate reports that show the old and new file paths. Track every unintentional file and folder access, and remediate as needed.
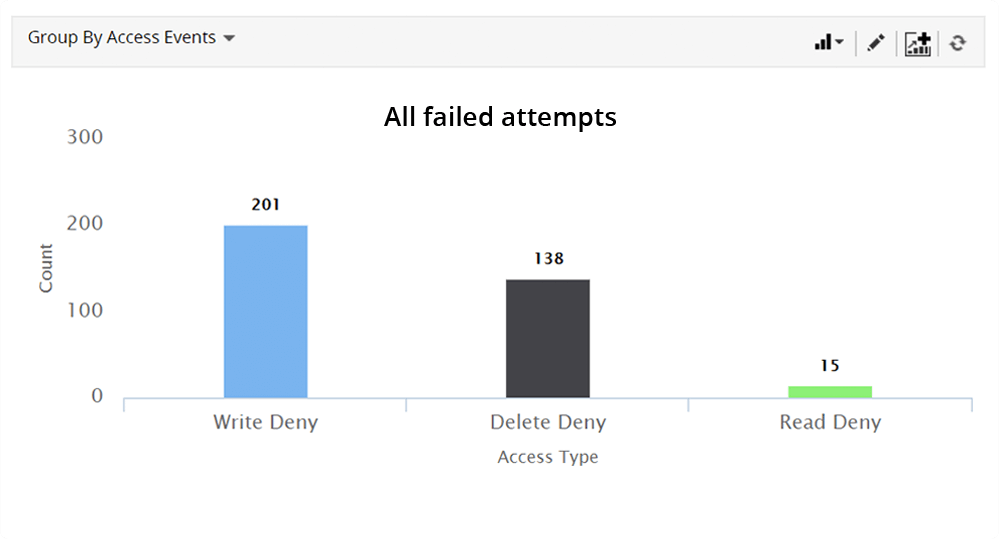
Track failed read, write, and delete attempts whether accidental or deliberate. These are often the first signs of an insider threat.



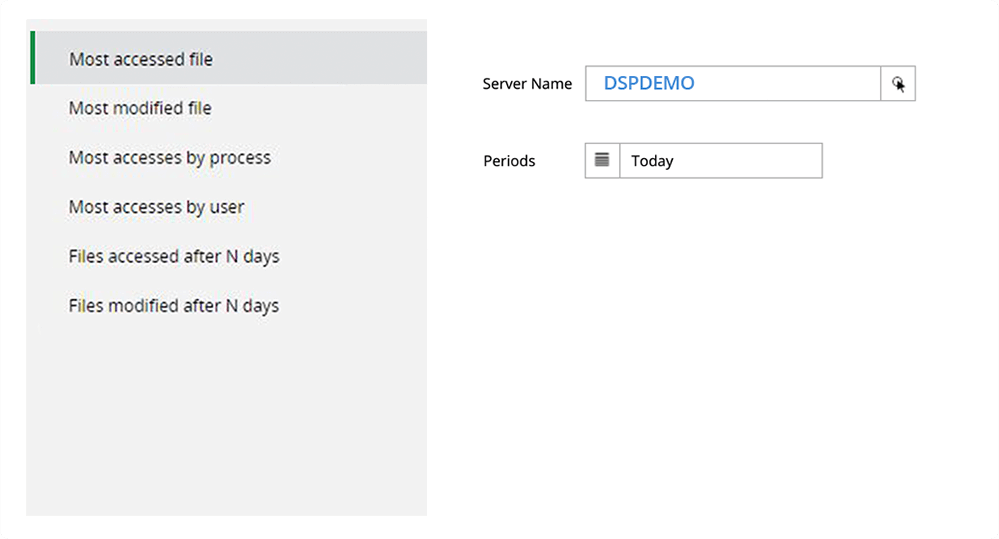
Identify standard and typical user changes to files on your servers. Track commonly accessed or modified files to ensure each user access is authorized.

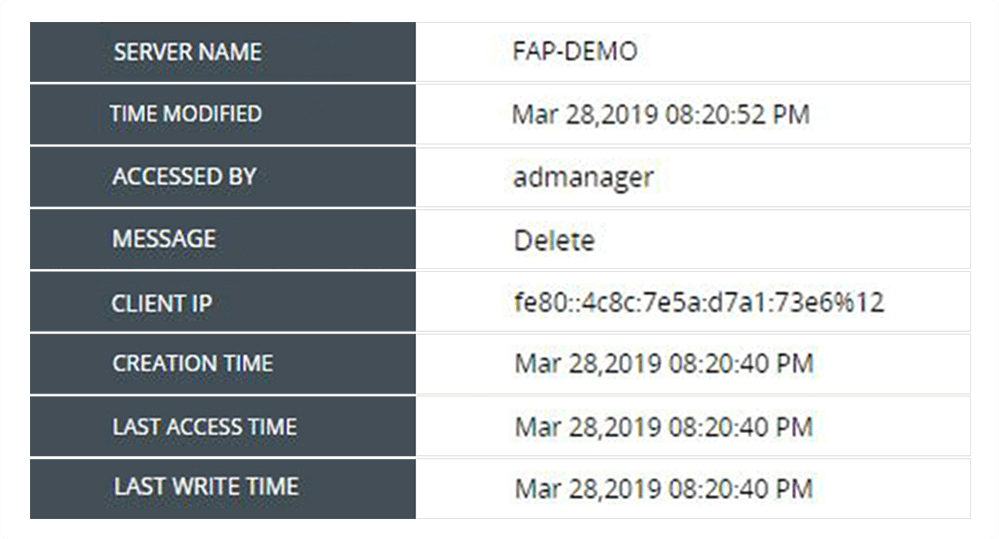
Perform forensic analysis effectively in the event of a security breach. Track the time of all accesses or modifications made to a file by a user.

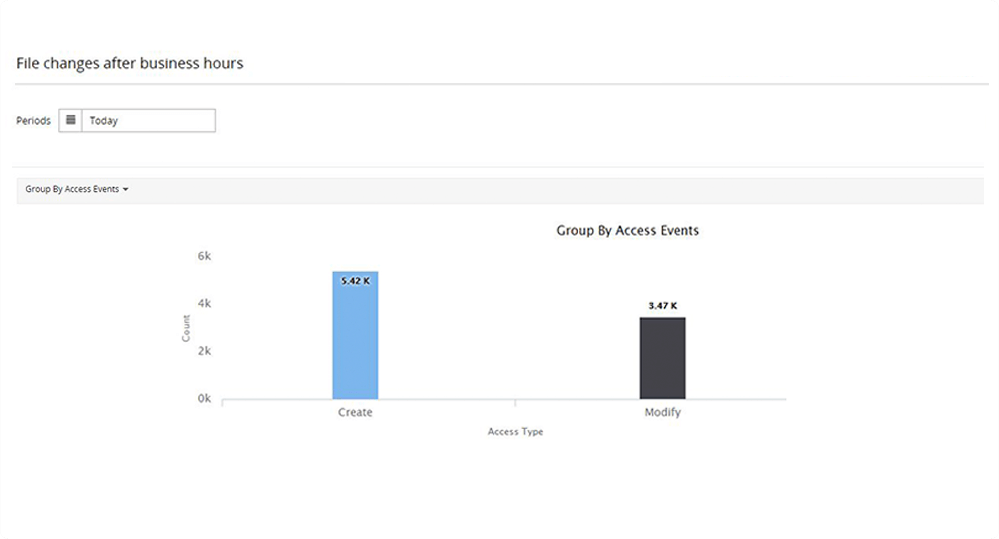
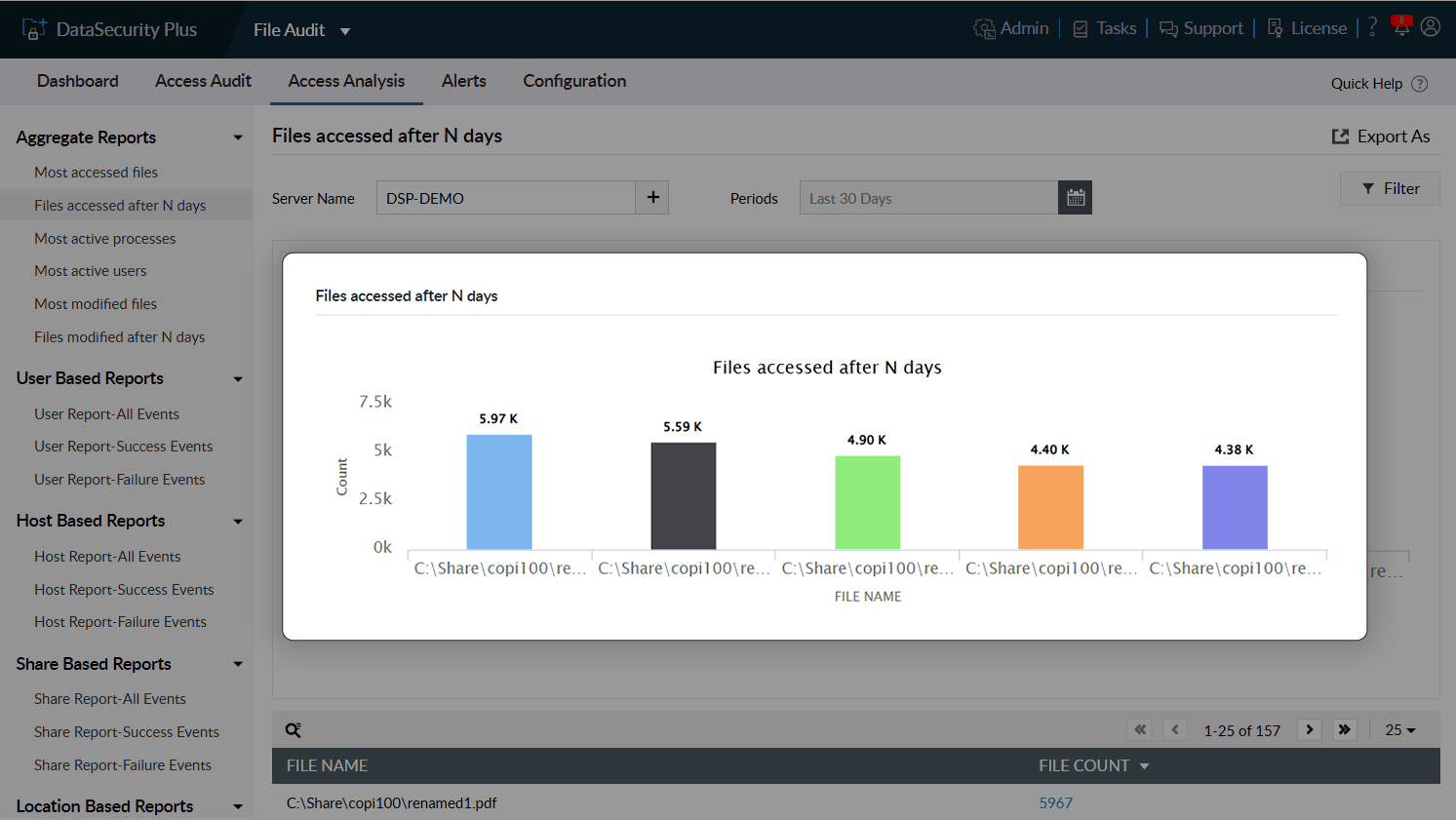
Spot out-of-the-ordinary events such as file accesses during non-business hours or files accessed after a long time. Verify whether the accesses were authorized.

Use file access auditing software to gain real-time visibility into every file modification across your file servers and NAS devices.
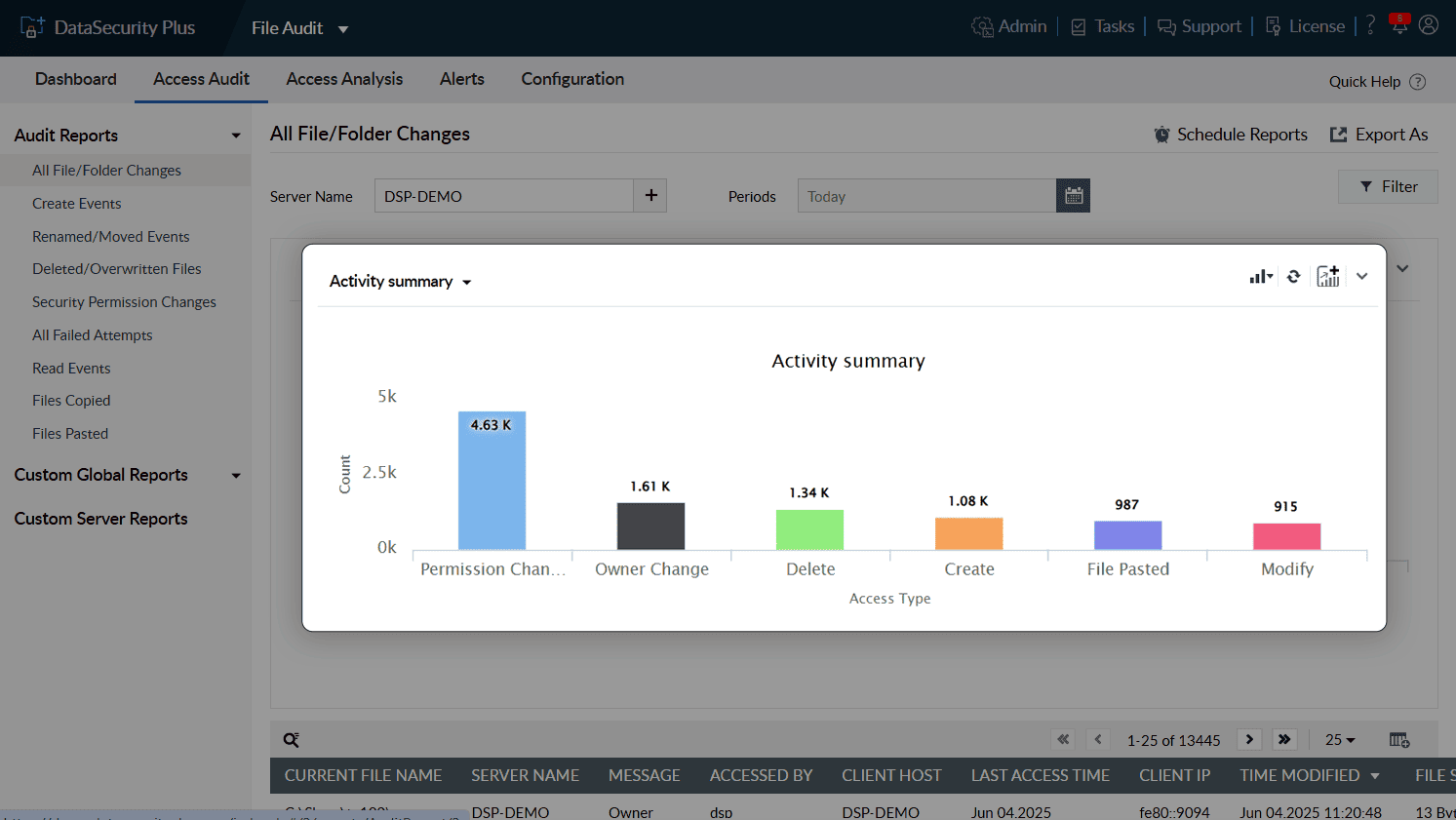
Receive detailed insights on file and folder accesses made by every user and process.
Monitor specific types of accesses in your file servers with easy-to-follow graphs and charts.

Filter reports to focus on a specific user or to see who accessed files and folders at odd hours.

Track users who access stale files or file shares and evaluate their actions.
Check last access times to flag unusual file and folder accesses after extended periods of inactivity.

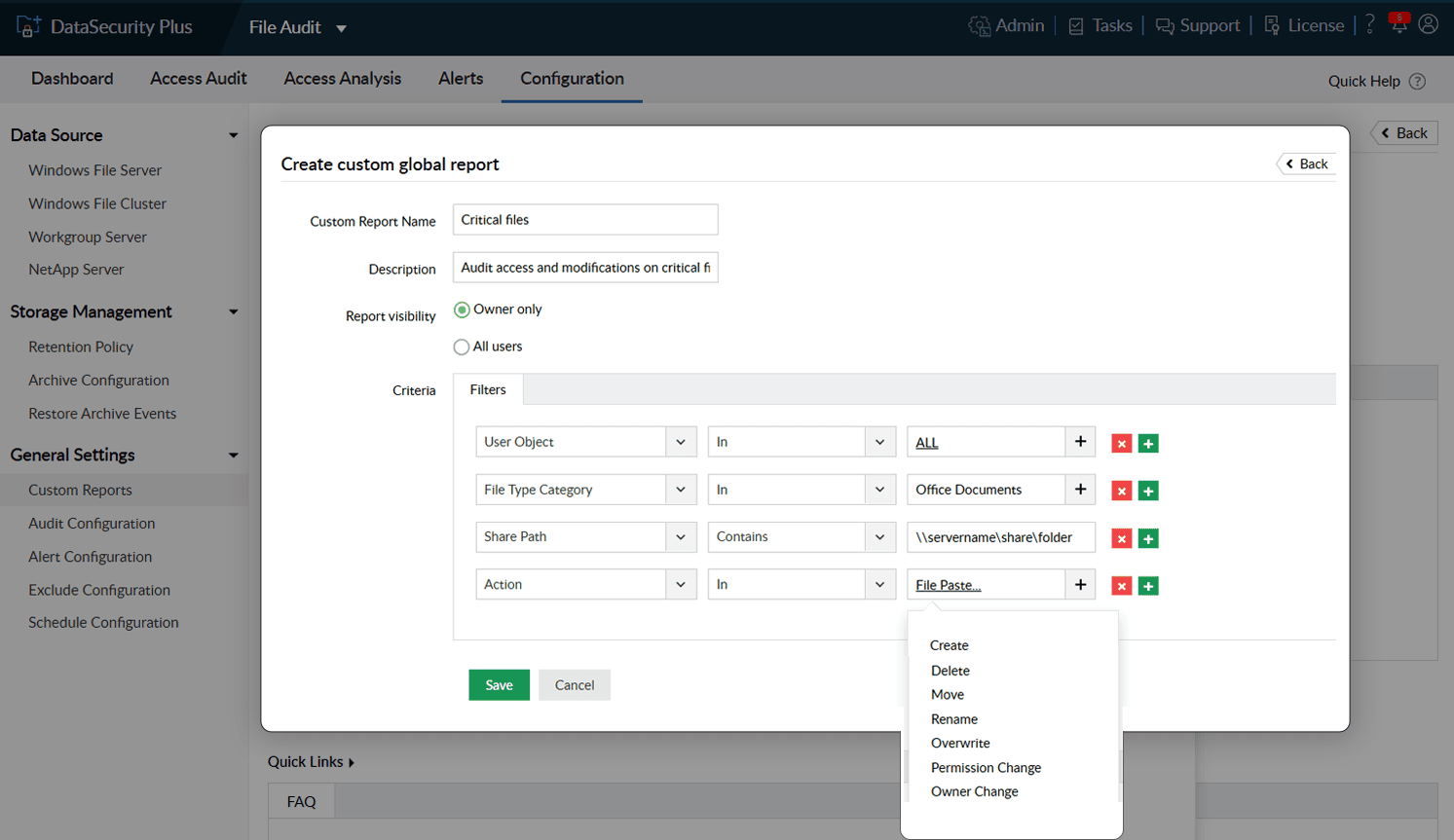
Customize reports based on your organization's needs. Receive insights on specific files, folders, or users.
