What is a data breach?

A data breach represents one of the most significant cybersecurity threats faced by organizations today. It occurs when unauthorized parties gain access to sensitive or confidential information, potentially exposing both personal and corporate data.
Personal data at risk includes passwords, security questions, social security numbers, banking details, and healthcare records, while corporate data includes valuable assets like trade secrets, customer databases, transaction history, and financial statements.
What's the difference between a data breach and a cyberattack?
While many use the terms data breach and cyberattack interchangeably, it's crucial to understand the differences between them.
A cyberattack is an attempted intrusion on an organization's digital environment. This could be carried out on any part of its IT infrastructure, like networks, endpoints, or servers, affecting access to company resources and disrupting essential services. A cyberattack may or may not directly affect the organization's data.
A data breach, on the other hand, is a result of a cyberattack that is specifically carried out to steal and hijack sensitive company data. A data breach always involves the compromise of data confidentiality.
For instance, a DDoS attack that disrupts website operations isn't technically a data breach. However, if cybercriminals steal and encrypt company data before threatening to sell it to the highest bidder, it qualifies as a data breach. Similarly, physical theft of storage devices or paper files containing sensitive information also falls under the category of a data breach.
Analyzing the root cause: Why do data breaches happen?
Data breaches can be the result of a well-planned attack or be completely accidental. They stem from three primary sources:
Human error
Well-meaning employees can inadvertently cause data breaches through actions like sending confidential information to incorrect email recipients or mishandling sensitive documents. A general lack of cyber hygiene might lead to accidental data breaches.
Malicious insider threats
Disgruntled employees, recently terminated staff, or individuals susceptible to external bribes can purposefully compromise data security. These insider threats are particularly dangerous because they often have legitimate access to sensitive information and understand internal security measures and how to overcome them.
External cybercriminal activities
Cybercriminals frequently target organizations to steal valuable data. Their typical primary motivation is financial gain, either through direct theft of confidential information or the collection of personal data for identity theft. Stolen credentials are usually sold on the dark web—from $1 for a social security number to $2,000 for passport information.
Data breaches can also have other motives beyond financial gain:
Corporate espionage, where competitors steal trade secrets.
Nation-state actors targeting government systems for political intelligence.
Hacktivists seeking to damage an organization's reputation.
Destructive attacks aimed at data deletion or defacement. These cost organizations a whopping $5.68 million to mitigate, which is higher than ransomware or data exfiltration attacks, according to IBM's Cost of a Data Breach Report 2024.
Anatomy of an attack: How does a data breach happen?
Understanding the life cycle of a data breach can help organizations better prepare for and respond to these incidents. According to research, the average data breach takes 277 days to identify and contain, which is ample time for attackers to access and exploit sensitive data.
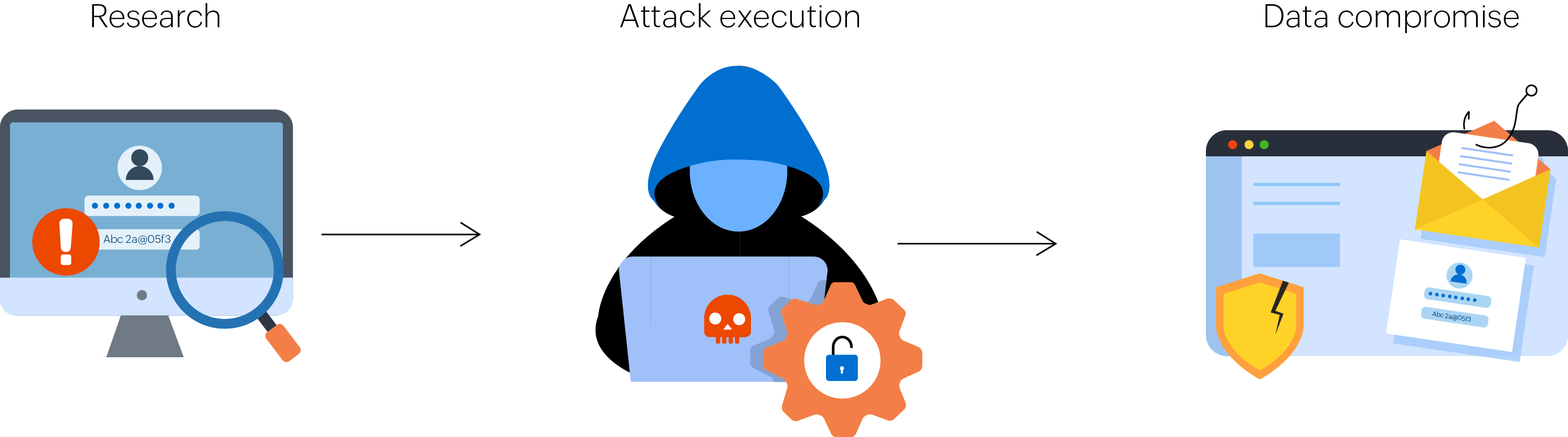
Research
Cybercriminals begin by identifying potential targets and analyzing their vulnerabilities. This includes examining both technical weaknesses in computer systems and potential human vulnerabilities, i.e., susceptible employees who lack safe cyber hygiene. Some attackers purchase previously stolen information or malware to facilitate their access.
Attack execution
Once vulnerabilities are identified, attackers launch their chosen method of breach. This might involve social engineering campaigns, direct exploitation of system vulnerabilities, or use of stolen credentials to gain unauthorized access.
Data compromise
After gaining access, attackers locate and take action on their targeted data. This could involve:
Data exfiltration for later use or sale.
Destruction of sensitive information.
Ransomware encryption with payment demands.
Different types of attacks that lead to a data breach
The effect of a data breach is threefold—it affects an organization's data, finances, and reputation. First, threat actors gain access to sensitive data, forcing the organization to pay the ransom demanded. The organization will also have to deal with any public fallout, leading to reputation loss and regulatory fines when the breach is disclosed.
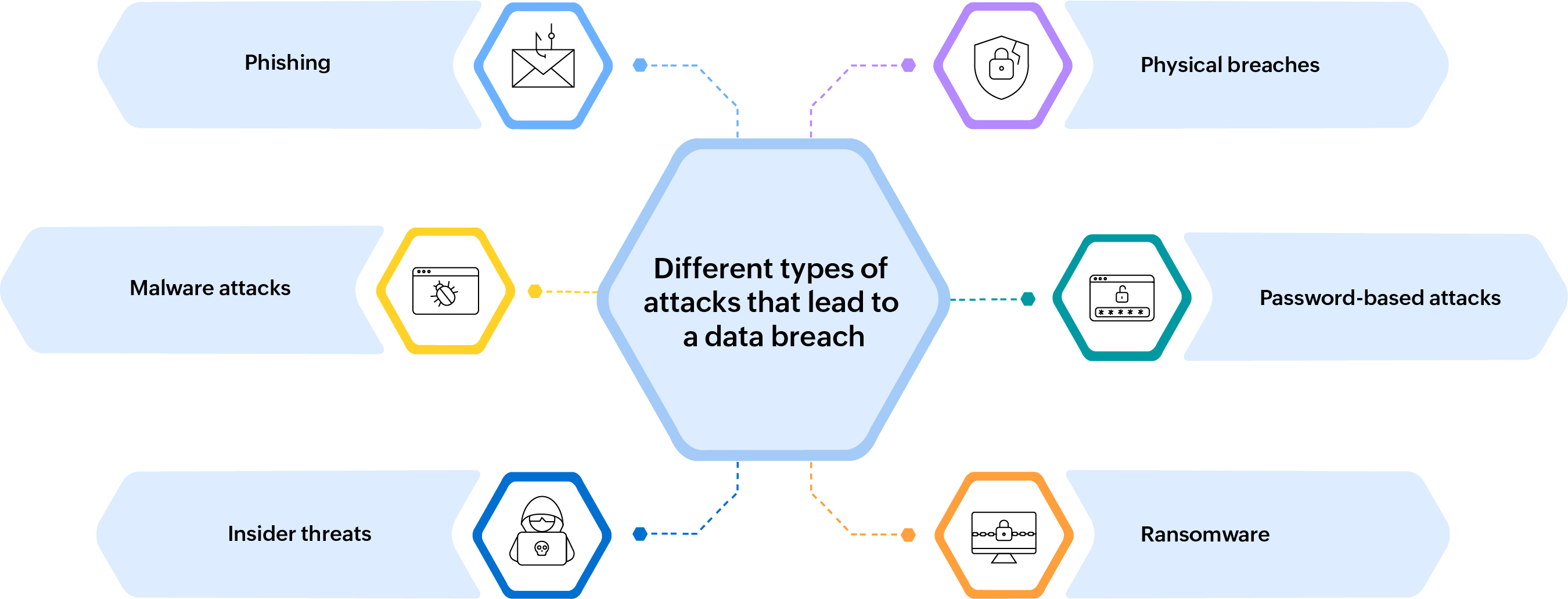
Based on the technique used and the extent to which the attack is carried out, a data breach can vary in severity. Here are a few methods threat actors prefer to use to induce mayhem in an organization:
Phishing
Phishing remains one of the most prevalent and effective vectors of data breaches. These attacks leverage sophisticated social engineering techniques to manipulate human psychology. Cybercriminals craft deceptive emails or messages that appear legitimate, often impersonating trusted organizations or colleagues.
The goal is to trick recipients into revealing sensitive information like login credentials, credit card details, etc., or to make them download malicious files unknowingly, which then creates access points for the threat actor to infiltrate the organization's network.
Modern phishing attacks have evolved beyond simple email scams to target specific individuals (spear-phishing) and high-level executives (whaling).
Malware attacks
Malware attacks utilize traditional viruses and other types of malicious software to breach an organization's data.
Malware comes in many forms. Ransomware encrypts valuable data and demands payment for its release. Spyware silently monitors user activity and steals sensitive information. Trojans disguise themselves as legitimate software while creating discreet back doors for attackers. Each type of malware serves specific purposes in the cybercriminal's arsenal, mandating a tailor-made detection and prevention plan for each malware type.
Insider threats
Insider threats present a unique challenge in data breach prevention because they originate from within the organization's trusted perimeter. These breaches can occur through two primary threat actors: malicious insiders who intentionally misuse their access privileges to steal or expose data, and negligent insiders who unintentionally cause breaches through careless handling of sensitive information. The existing privileges of these individuals often mean they can bypass many traditional security controls, making detection and prevention particularly challenging.
Physical breaches
While many organizations focus on digital security, physical breaches still remain a significant concern. These incidents can occur through:
Improper disposal of hardware or documents containing confidential information.
Lost or stolen laptops, smartphones, servers, or storage devices containing sensitive data.
Unauthorized physical access to workstations or network equipment.
Password-based attacks
Password guessing attacks have evolved from simple trial-and-error attempts to sophisticated operations. Modern attackers employ various techniques:
Brute-force attacks that systematically test all possible combinations.
Dictionary attacks using common words and variations.
Credential stuffing using previously leaked password databases.
Social engineering to obtain password information.
Rainbow table attacks against password hashes.
Ransomware
Ransomware, a vicious type of malware, has emerged as one of the most damaging vectors of data breaches. These attacks follow a distinct pattern:
Initial infection through various attack vectors.
Silent encryption of valuable data.
Presentation of ransom demands.
Threat of data destruction or public release.
Modern ransomware operators often employ double-extortion tactics. Here, the threat actors first steal the sensitive data before encrypting it, increasing the stakes on the organization to give in to their financial demands.
Repercussions: What happens after a data breach?
When an organization falls victim to a data breach, data privacy regulations mandate them to disclose the incident to affected individuals. These laws, specific to the regions where the organization operates and does business, are established by governments to ensure companies maintain necessary frameworks for preventing cyberattacks and protecting citizens. Such regulations hold organizations accountable for handling their customers' personal data with the highest degree of security and care.
The regulations assess both an organization's preparedness for cyberattacks and their response to incidents, with the power to impose substantial fines for inadequate security measures or improper handling of breaches. These financial penalties, combined with mandatory disclosure requirements, serve as powerful motivators for organizations to prioritize data protection. Here are a few data privacy regulations that support personal data privacy.
GDPR, European Union
The General Data Protection Regulation (GDPR) sets the global benchmark for data protection requirements. It mandates organizations to report breaches to supervisory authorities within 72 hours of discovery, setting one of the strictest timelines worldwide. The regulation's sharpest tooth is in its penalties: violations can incur fines up to €20 million or 4% of annual global turnover, whichever is higher.
CCPA/CPRA, United States
The California Consumer Privacy Act (CCPA) and the California Privacy Rights Act (CPRA) are popular data privacy laws in the US that requires organizations to notify affected residents "in the most expedient time possible" after breach discovery. The law empowers individuals with private right of action, allowing them to sue companies for data breaches resulting from negligence. Penalties are substantial: up to $7,500 per intentional violation and $2,500 per unintentional violation, alongside potential civil lawsuits for damages.
PIPEDA, Canada
The Personal Information Protection and Electronic Documents Act (PIPEDA) mandates that organizations must report data breaches to both the Privacy Commissioner and affected individuals as soon as is feasible. Organizations governed by PIPEDA are required to follow ten key principles to protect personal information, including but not limited to accountability, consent, limiting collection, and limiting use. The law imposes penalties up to CAD 100,000 per violation, ensuring organizations take breach notification seriously.
Data breach examples
As organizations scale up each year and adopt more technology into their stack, they inadvertently increase the number of potential entry points into their network. This incentivizes cybercriminals to carry out sophisticated attacks in hopes of exfiltrating sensitive data from the organization. Here are a few prominent cyberattacks that resulted in data breaches.
Yahoo! data breach
Between 2013 and 2014, Yahoo! was hit with the largest data breach in history. It affected approximately three billion user accounts, exposing sensitive data, including names, email addresses, passwords, and security questions and answers. The breach's disclosure in 2016 came amid the acquisition of Yahoo! by Verizon, resulting in $350 million being cut from the original offer.
One of the largest credit reporting agencies in the US, Equifax, was breached back in 2017, leading to the leak of sensitive information of over 140 million people, including social security numbers, birth dates, and credit card details. The incident cost Equifax nearly $500 million in damages and led to multiple regulatory investigations.
Marriott International, the hospitality multinational company, had the personal information of approximately 500 million guests exposed in a 2018 data breach, which was reportedly part of a Chinese intelligence operation. The company faced over $23 million in fines for failing to protect customer data.
Microsoft Exchange server breach
In 2021, hackers carried out a cyberattack on Microsoft Exchange servers, compromising email servers affecting 60,000 global organizations, deploying malware, and gaining control of critical systems.
In August 2023, Caesars Entertainment encountered a cybersecurity incident carried out by the hacker group Scattered Spider. Through social engineering tactics, the group was able to gain access to the Caesar loyalty program database containing personally identifiable information of millions of customers.
Data breach statistics
Recent statistics underscore the destructive nature of data breaches:
Over 10,626 confirmed data breaches were recorded in 2024. (2024 Data Breach Investigations Report, Verizon)
The average cost of a data breach in 2024 was $4.88 million, a 10% increase from the previous year. (Cost of a Data Breach Report 2024, IBM)
Nearly 16% of all recorded data breaches in 2024 were a result of compromised credentials, whereas phishing attacks accounted for another 15%. (Cost of a Data Breach Report 2024, IBM)
The median ransomware recovery cost doubled from $375K in 2023 to $750K in 2024. (The State of Ransomware 2024, Sophos)
34% of ransomware attacks began with email-based threats like malicious emails or phishing attacks. (The State of Ransomware 2024, Sophos)
The human element is responsible for 68% of breaches, emphasizing the need for security training and insider threat management. (2024 Data Breach Investigations Report, Verizon)
55% of organizations increased spending on incident response planning and testing after a breach. (Cost of a Data Breach Report 2024, IBM)
Data breach prevention and mitigation
Organizations must implement robust security measures to protect against data breaches, which have become increasingly sophisticated and costly to mitigate in today's digital landscape. It is paramount to have a comprehensive and nuanced cybersecurity approach to protect against unauthorized access to sensitive information.
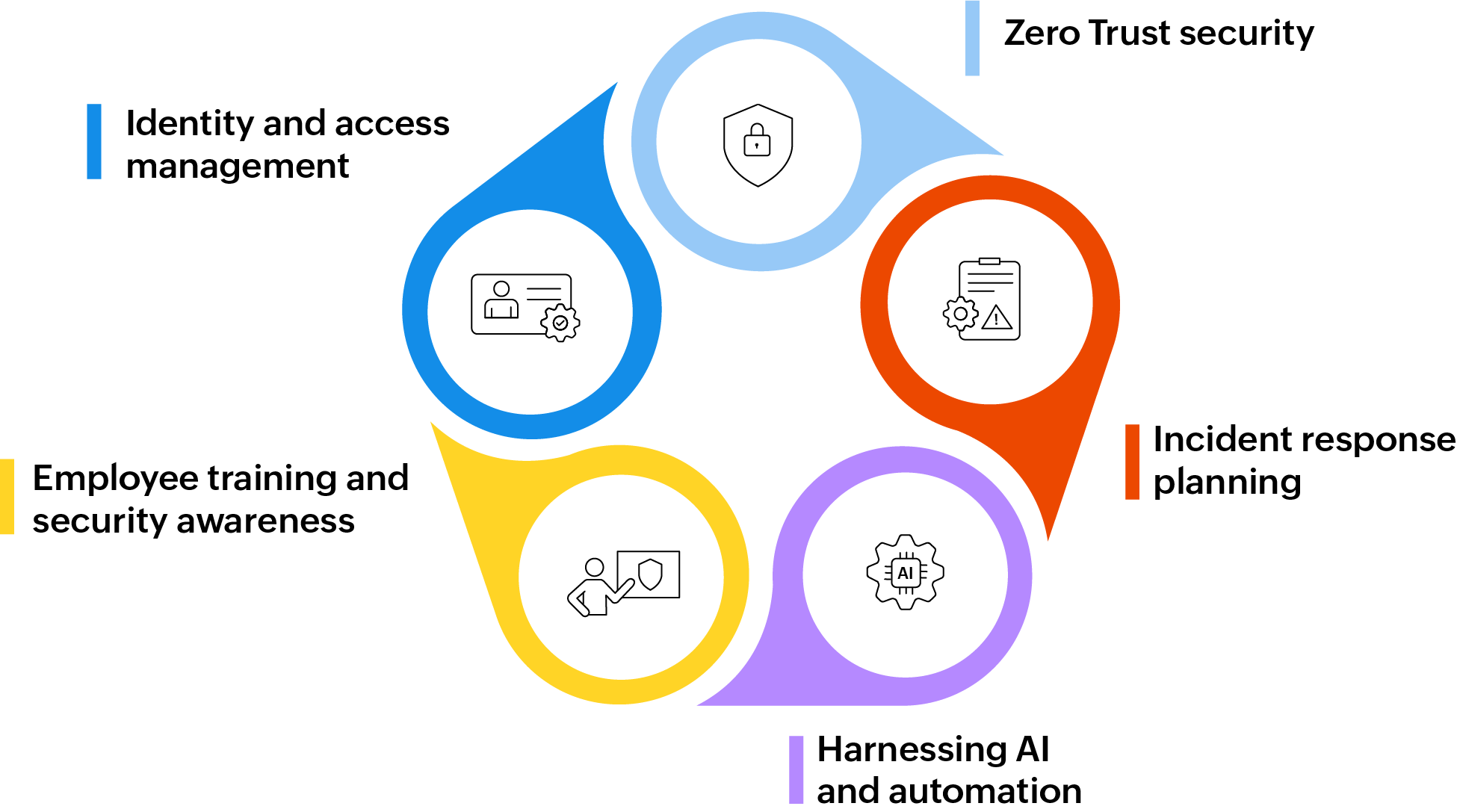
Incident response planning
An incident response plan (IRP) serves as the first line of defense against data breaches. Research reports reveal a compelling financial benefit: organizations with well-tested incident response plans and dedicated response teams face can reduce breach costs by $500,000 compared to organizations without them. An effective IRP provides a detailed blueprint for detecting, containing, and eliminating cyberthreats, ensuring swift and coordinated action when security incidents do occur.
Harnessing AI and automation
AI and automation technologies have revolutionized data breach prevention and detection. Organizations leveraging advanced AI systems experience 33% lower breach costs compared to those using basic security measures (Cost of a Data Breach Report 2024, IBM). This significant reduction stems from implementing sophisticated security technologies:
Security orchestration, automation, and response (SOAR) systems streamline security operations by automating threat detection and response protocols, enabling rapid reaction in the event of a data breach.
User and entity behavior analytics (UEBA) employs advanced algorithms to identify suspicious patterns in user behavior that might indicate a security threat.
Endpoint detection and response (EDR) provides around-the-clock monitoring and response capabilities for all endpoint devices, while extended detection and response (XDR) offers broader visibility across networks, cloud workloads, and applications.
Employee training and security awareness
Since social engineering and phishing attacks remain leading causes of data breaches, comprehensive employee training programs play a vital role in organizational security. Regular security awareness training should cover:
Recognition and reporting of suspicious emails and phishing attempts.
Proper handling of sensitive data and confidential information.
Security best practices for remote work and personal devices.
Local compliance requirements and data protection regulations.
Identity and access management
A robust identity and access management (IAM) framework forms a crucial component of data breach prevention. Modern IAM implementations should include:
Strong password policies that mandate complex combinations and regular password resets.
MFA for all user accounts.
SSO capabilities to streamline secure access.
Regular access reviews and privilege audits.
Automated user provisioning and deprovisioning.
Zero Trust security
The Zero Trust security model has proven to be extremely effective against data breaches in modern network environments. This comprehensive security framework operates on three fundamental principles:
1. Continuous authentication and validation
Every user, device, and application must continuously prove their identity and security status, regardless of their location or previous access history. This involves real-time monitoring of authentication attempts and behavior patterns.
2. Least privileged access control
Access rights are granted at the minimum level necessary for users to perform their duties. This principle significantly reduces the potential damage from compromised accounts by limiting their reach within the network. Organizations should regularly review access permissions and revoke unnecessary privileges.
3. Comprehensive security monitoring
Zero Trust architecture requires complete visibility into the organization's hybrid network ecosystem. This mandates real-time monitoring of all user activities, prompt vulnerability scanning, and penetration testing.
By implementing these security measures, organizations can significantly reduce their attack surface and bring down the risk of being the victim of a data breach while minimizing the potential impact if one occurs.
How can ManageEngine secure organizations against data breaches?
In today's threat landscape, the tactics used to gain unauthorized access to networks and sensitive information are constantly evolving. This is why it's important to choose an IT security partner who is with you at every step of this digital battle.
Ensure your data is safe with ManageEngine's suite of dedicated cybersecurity products:
Log360 enables security teams to monitor their networks in real time to detect signs of unusual activity. The UEBA module helps flag down compromised accounts and malicious insider activity. The UEBA module can also be integrated with PAM360 to monitor the activity of privileged users and track any anomalous behavior. SOC teams can calibrate a baseline of normal user activity to automatically detect and handle common security threats.
Identity360 and AD360 can help organizations protect against credential-based attacks and insider threats with adaptive MFA, ensuring account security. AD360 also comes equipped with an identity threat detection and response module to actively detect and eliminate any identity-based threats.
Endpoint Central, with its next-gen antivirus and anti-malware modules, can proactively look for potential threats on the network by employing advanced, AI-powered behavioral anomaly detection.
DataSecurity Plus helps organizations analyze and categorize data based on their vulnerability level, and securely locks down confidential information by isolating the affected device if ransomware is detected.
Device Control Plus offers teams holistic control of endpoint peripheral access, helping prevent insider threats by limiting the transfer of sensitive data.