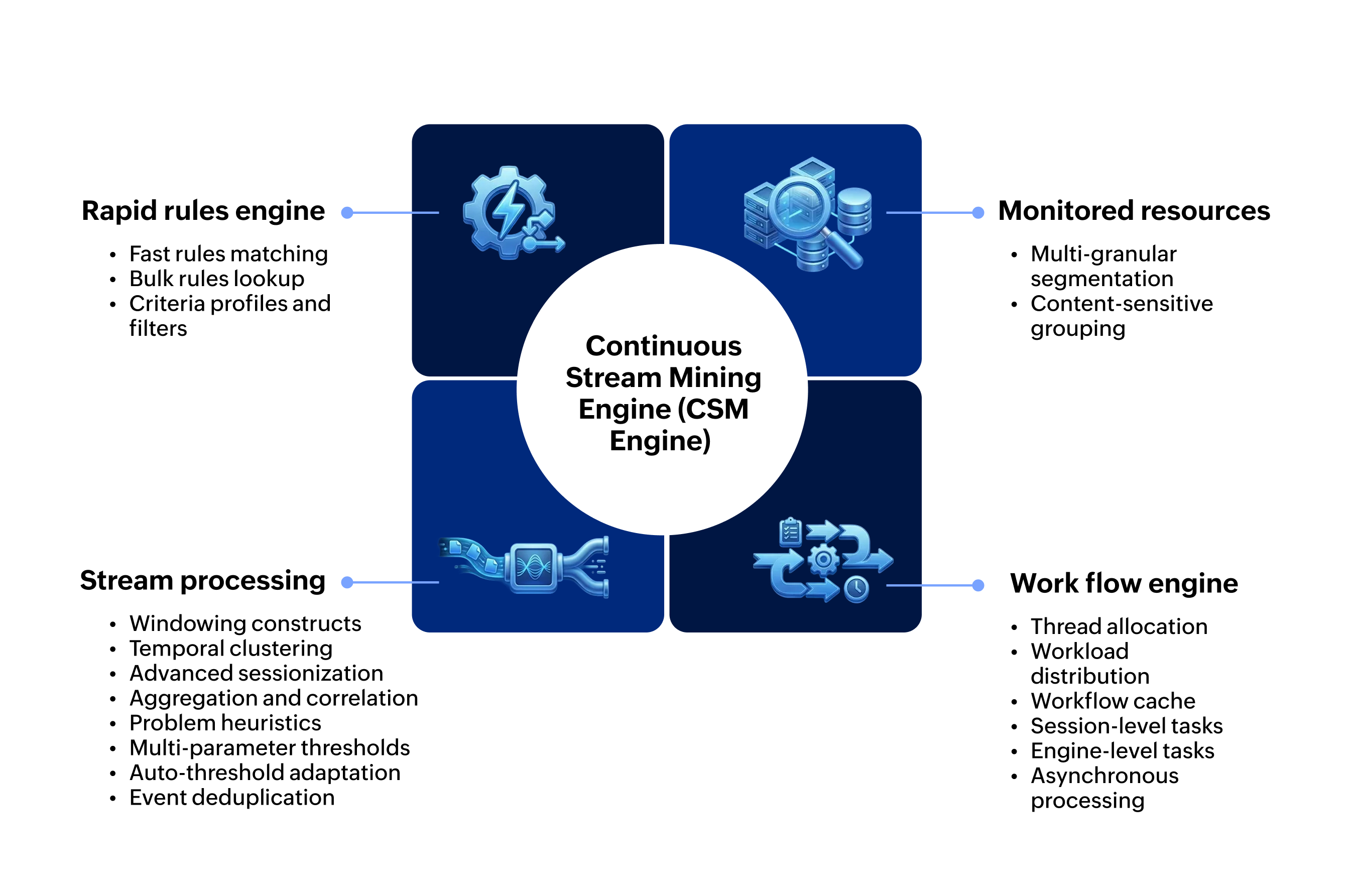
Continuous Stream Miner™ (CSM) / Continuous Stream Mining Engine (CSM Engine) is a Java based Complex Event Processing (CEP) Engine for real-time complex pattern matching & event correlation across multiple events, based on some effective strategies involving fast bulk-lookup rules matching, multi-granular context-sensitive resource modeling, temporal clustering & advanced sessionization, automatic threshold adaptation, de-noising & de-duplication, and heuristics based event stream classification. Primarily it employs a Rapid Rules Engine, a variety of data structures for indexing & caching, partitioning & windowing constructs, contracts/interfaces and generic base implementations for data aggregation and event correlation. It offers a configurable and extensively customizable, API rich framework for building high performance Event Stream Processing (ESP) applications.
NetFlow Analyzer’s Security Analytics converts raw flow data into clear threat insights using rule based detection, behavioral analysis, and MITRE ATT&CK mapping. It builds behavioral baselines for every asset, identifies sudden deviations, and highlights high risk events with full context on severity, source, destination, and traffic patterns. Security Analytics uses continuous stream mining technology to correlate events instantly, enrich context, and process large volumes of flow data with high speed and precision. The module reduces noise through adaptive learning, maintains continuous asset tracking using hostnames and MAC addresses, and detects both external and internal threats in real time, including unusual communication patterns, data exfiltration attempts, and lateral movement.