Map, Detect, Defend: The MITRE ATT&CK Way
Understand how real-world cyberattacks happen, helping security teams spot and stop threats faster
Modern cyberattacks are stealthy, persistent, and often slip past traditional defenses unnoticed. To strengthen security posture and improve threat visibility, MITRE developed the MITRE ATT&CK® framework, a globally recognized knowledge base that documents real-world attacker tactics, techniques, and behaviors.
ML-based Security Analytics in NetFlow Analyzer integrates MITRE ATT&CK, enabling security teams to gain immediate context around threats, align detection and response with real attacker behavior, and make faster, intelligence-driven decisions to strengthen defenses.
Understanding MITRE ATT&CK: Dissecting adversary methods
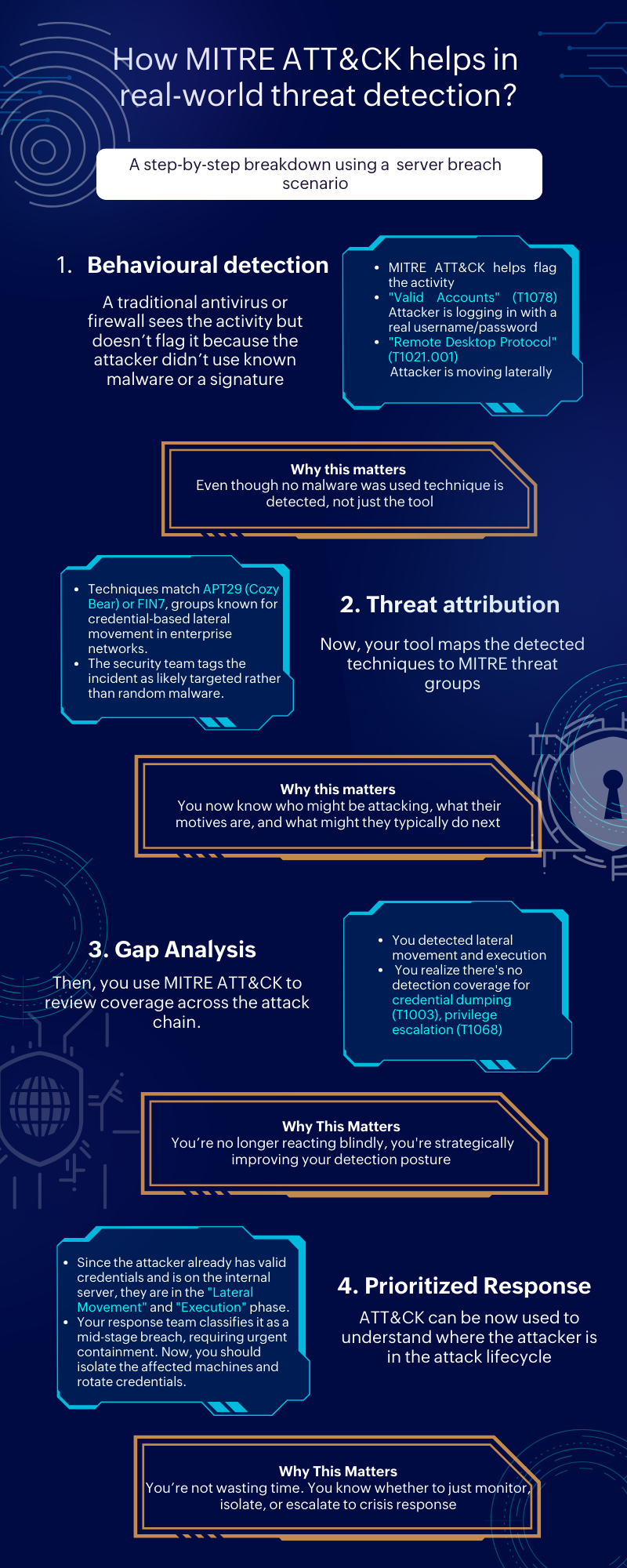
Think of MITRE ATT&CK as a blueprint of attacker behavior. It doesn’t just show what’s happening—it helps predict what’s coming next. It maps how adversaries move through systems, what techniques they use, and where your blind spots might be.
The framework supports,
- Behavioral detection of threats, even when traditional tools fail
- Attribution by linking activities to known threat groups
- Pinpoint and resolve gaps in threat detection
- Prioritized response based on where the attacker is in the kill chain
By understanding the “how” behind every attack, teams can build proactive defenses and respond with precision.
Why every security team needs to prioritize MITRE ATT&CK
- Offers a common framework for security teams, vendors, and researchers to describe and analyze threats consistently.
- Helps map security events and anomalies to known attack techniques, making threat detection more meaningful and actionable.
- Assists analysts in proactively searching for signs of compromise by thinking like an attacker.
- Helps responders understand how an attacker moved through the environment and what to investigate next.
- Used by security tools, SIEMs, SOARs, and NDRs to map security events to techniques and visualize attack paths.
How NetFlow Analyzer uses MITRE ATT&CK
Our platform seamlessly maps detected anomalies, events, and flows to corresponding MITRE ATT&CK techniques, helping you to,
- Visualize threats on an interactive ATT&CK matrix
- Drill down into technique details, involved assets, and affected users
- Identify when suspicious behavior aligns with known attack tactics
- Track coverage to know which techniques your environment can detect and which require attention
Example: A sudden spike in LDAP traffic mapped to T1018-Remote System Discovery may signal internal network discovery. You get a security event tagged with this MITRE technique, along with device context and recommended remediation.
