According to Zipdo Education Report 2024, 93% of educational institutions have already subscribed to cloud-based services, and about 86% of school districts have adopted cloud-based productivity tools to use cloud-based systems for collaboration. As more schools and universities move towards cloud adoption, there is an increasing need for data security measures within the cloud.
A cloud access security broker (CASB) provides educational institutions with the essential tools to guarantee secure cloud usage, protect sensitive data, and maintain compliance.
How will a CASB help address data security challenges in education?
Here are some data security challenges that educational institutions face, and how a CASB solution will help address them.
- Abundance of personal data: Schools and universities are data mines, as they contain personally identifiable information such as social security numbers, health records, scholarship and payment data of numerous students, parents, and faculty. CASB helps educational institutions secure this data by monitoring and detecting unusual download requests, thus preventing data exfiltration.
- Diversity of academic data: Sensitive information held by universities and research institutes can be leaked, leading to risks such as identity theft. Additionally, if this data from research institutes ends up in the hands of rival organizations, it could lead to intellectual property theft. CASB solutions help universities resolve many of these issues by enforcing access controls based on different criteria and constant monitoring.
- Increasing use of technology in the educational sector: Many organizations have heavily integrated technology into their lesson plans, such as the use of learning management systems (LMS) like Canvas and Moodle, collaborative tools such as Zoom and Workspace, and an increased dependence on cloud storage services such as OneDrive and Dropbox. Additionally, the use of personal laptops needs to be supported as students access applications from anywhere. Deploying a CASB solution will implement access and control regulations for approved applications like LMS, email, and chat, as well as find and keep an eye on cloud applications accessed by users.
- Complying with legal mandates: Complying with regulatory standards is another reason why organizations need to set up data security measures. Institutions risk heavy fines if they fail to comply with the mandates.Implementing CASB makes compliance simple because it guarantees that data is encrypted both in transit and at rest, as required by numerous compliance regulations.
- Maintaining trust and reputation: Every educational institution has an implicit pact with students to safeguard their personal information. It is this pact that provides them with the confidence to disclose their personal information.
Because CASB guarantees the visibility, control, and protection of sensitive data, it aids in addressing the primary data security concerns. By deploying a CASB-enabled SIEM solution, educational institutions can safely increase the use of cloud technology, safeguard student and personal information, assure compliance, and build trust and reputation.
How a CASB solution can improve data security in educational institutions
- Increased visibility: CASB can help you get complete visibility into the activities of the user within the cloud and can also help educational institutions combat issues related to shadow IT. To elucidate, if you are a K-12 school, you can monitor the internet activities, file downloads, or even the file sharing activities of students. This way, you can ensure that students are not exposed to unwanted content on the internet.
- Data loss prevention: CASB security solutions can inspect sensitive data being moved to and from the cloud, between cloud services, and within the cloud. Any university or institution concerned about securing their data should leverage a DLP-integrated CASB solution for improved cyberdefense. This will help identify and categorize different types of data and set up policies and real-time alerts in case of a breach.
- Real-time threat protection: According to Comparitech, ransomware attacks on educational institutions has cost the world economy $53 billion just from the downtime alone. CASB offers advanced threat detection and user behavior analytics to identify threats and send alerts to the instituiton's security admins. Especially for a new institution that is transitioning to the cloud they are more prone to social engineering attacks or other cyberthreats. Having a CASB solution can help admins get the right insights at the right time.
- Compliance monitoring and reporting: CASB will enforce security rules and provide thorough audit reports to assist educational institutions in meeting compliance regulations, including FERPA and GDPR. Some of these security rules include providing access controls to authorized people, monitoring data flow and user activity, and ensuring data encryption at rest and during transit.
A CASB solution can help educational institutions tackle different types of challenges. Some of these are:
Leveraging CASB in education: A few examples
Here are some hypothetical scenarios where a CASB solution will be useful for improving data security in an educational institution.
Stopping data exfiltration
Anthony, a senior research student, from Crescent University was working on a study that included confidential data about human subjects. Antony decided to move this data to his laptop by sending files via email as it was becoming late and he wanted to continue his analysis when he got home. He was unaware that his laptop lacked the necessary security to identify viruses and thwart attacks. Sadly for Antony, his system's data leaked, jeopardizing the 200 study participants' private information as well as the reputation of his university.
If a CASB-integrated SIEM solution had been in place, it would have quickly terminated the process and alerted the security team to the high priority risk. The SIEM solution could have correlated these unusual activities to identify the threat in advance, and even have initiated an automated shutdown. This, along with communication from the admin team, would have prevented issues. Following the event, Crescent University implemented extensive training for handling sensitive data and adopted a CASB solution. Here is an example of a report from such a solution.
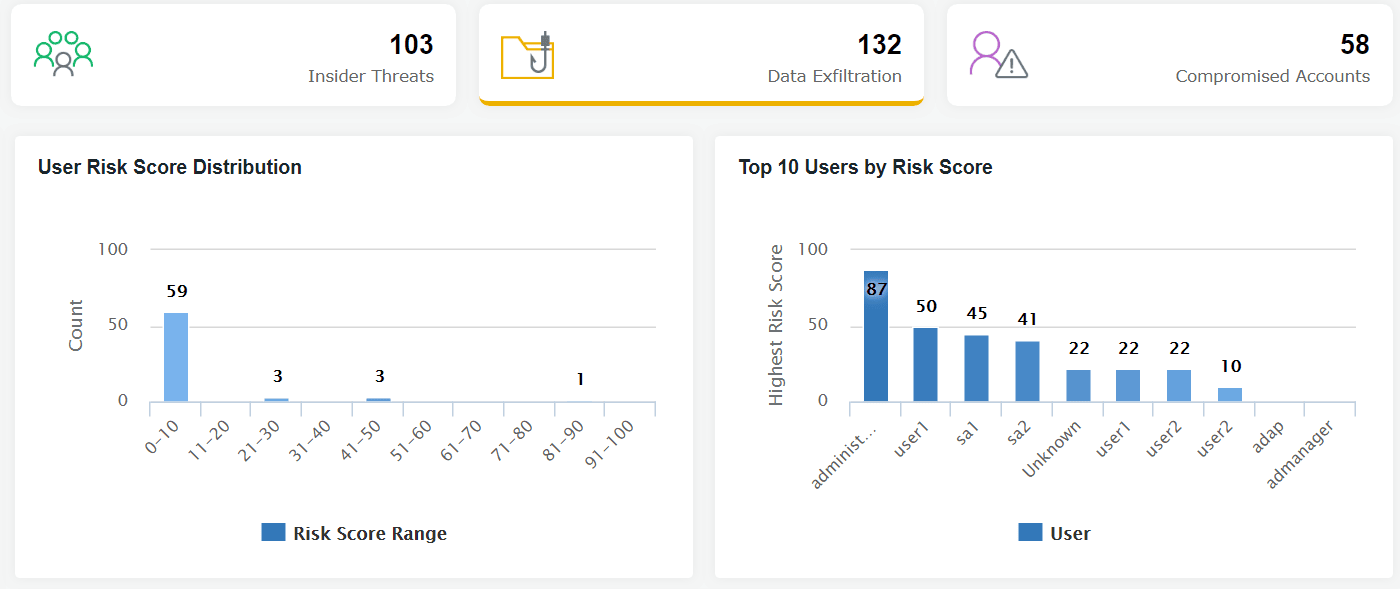
Figure 1: A graphical representation from Log360 UI which indicates top users by risk score due to data exfiltration.
Monitoring shadow IT
Emily was stoked at being elected as the event coordinator of her university's management conference. Since her appointment, she researched the different apps she could use to ensure the smooth flow of all the events. Then, she discovered Quick, a cloud-based event planning app. Excited by the features, she started collecting details including names, email IDs, and payment details for the conference from students, professors, and guests. However, the catch was that she did all this without the IT department's knowledge, on an app that was not approved by the university. The app, due to a lack of strong security controls, was attacked, and all the details she uploaded were leaked.
A CASB solution would have identified the unusual flow of data to an unapproved application and flagged it, then notified the admin team through the dashboard, where a complete list of all the shadow apps and associated users would be visible, including specifics about the data transfer, the type of data involved, and the external service used. An example of a dashboard from a CASB solution is shown below.
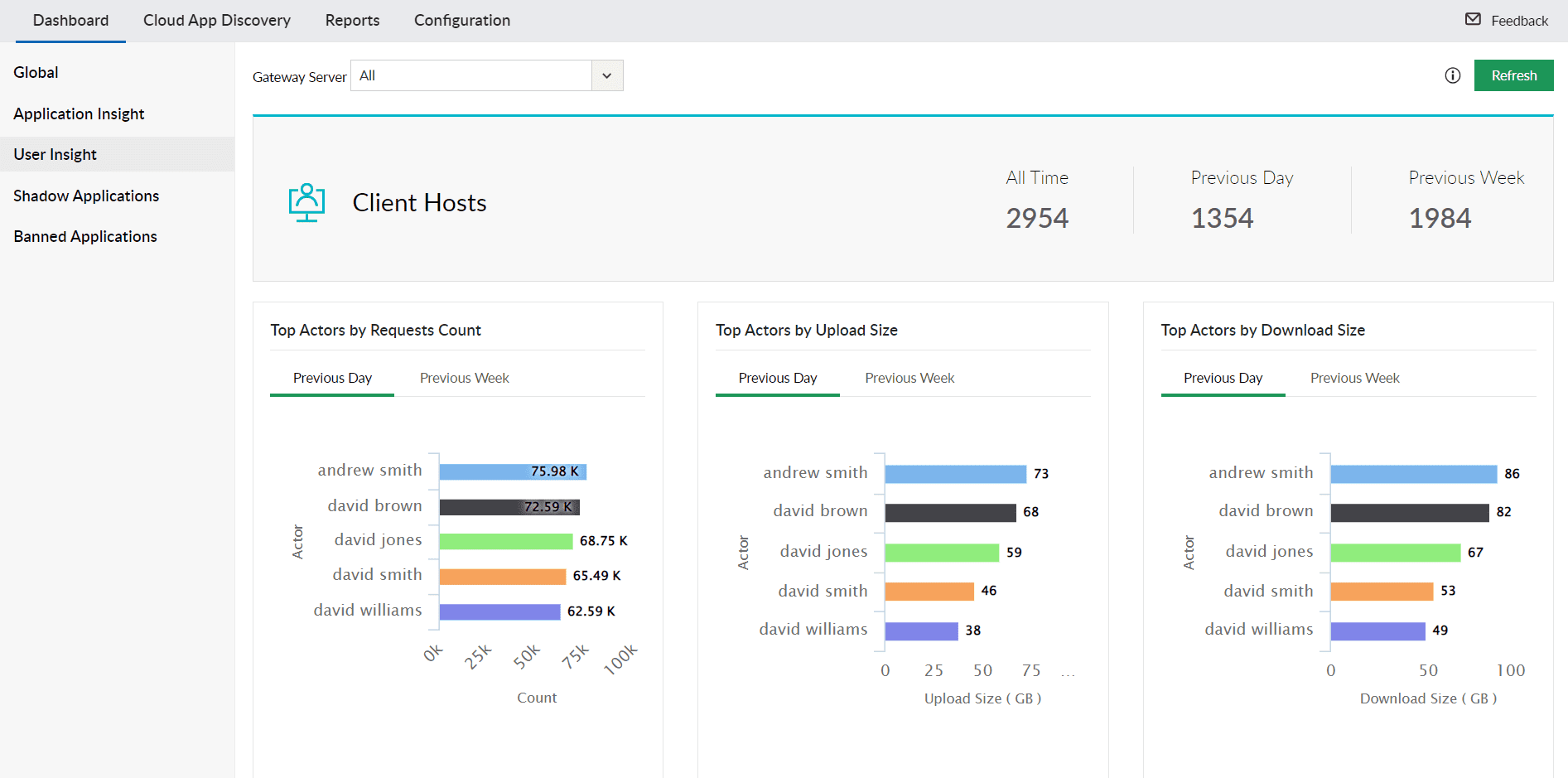
Figure 2: Log360 dashboard showing Top Actors by requests count, upload size, and download size.
Meeting compliance mandates
No matter what institution you are, compliance is mandatory. As an educational institution some of the mandates you may need to follow are FERPA, HIPAA, or GDPR. FERPA mandates strict controls over access to and sharing of student information. With a CASB, educational institutions can easily adhere to FERPA as the solution ensures that data is encrypted both at transit as well as at rest. Additionally, institutions also provide audit reports showing who accessed or modified student data. The same is the case with HIPAA (Institutions which are FERPA compliant don't need to be HIPAA-compliant). In case someone attempts to steal or modify data within the cloud, CASB immediately notifies the team, thus protecting the university from a HIPAA violation. Here is an example of FERPA compliance reports offered by our CASB-integrated SIEM solution, Log360.
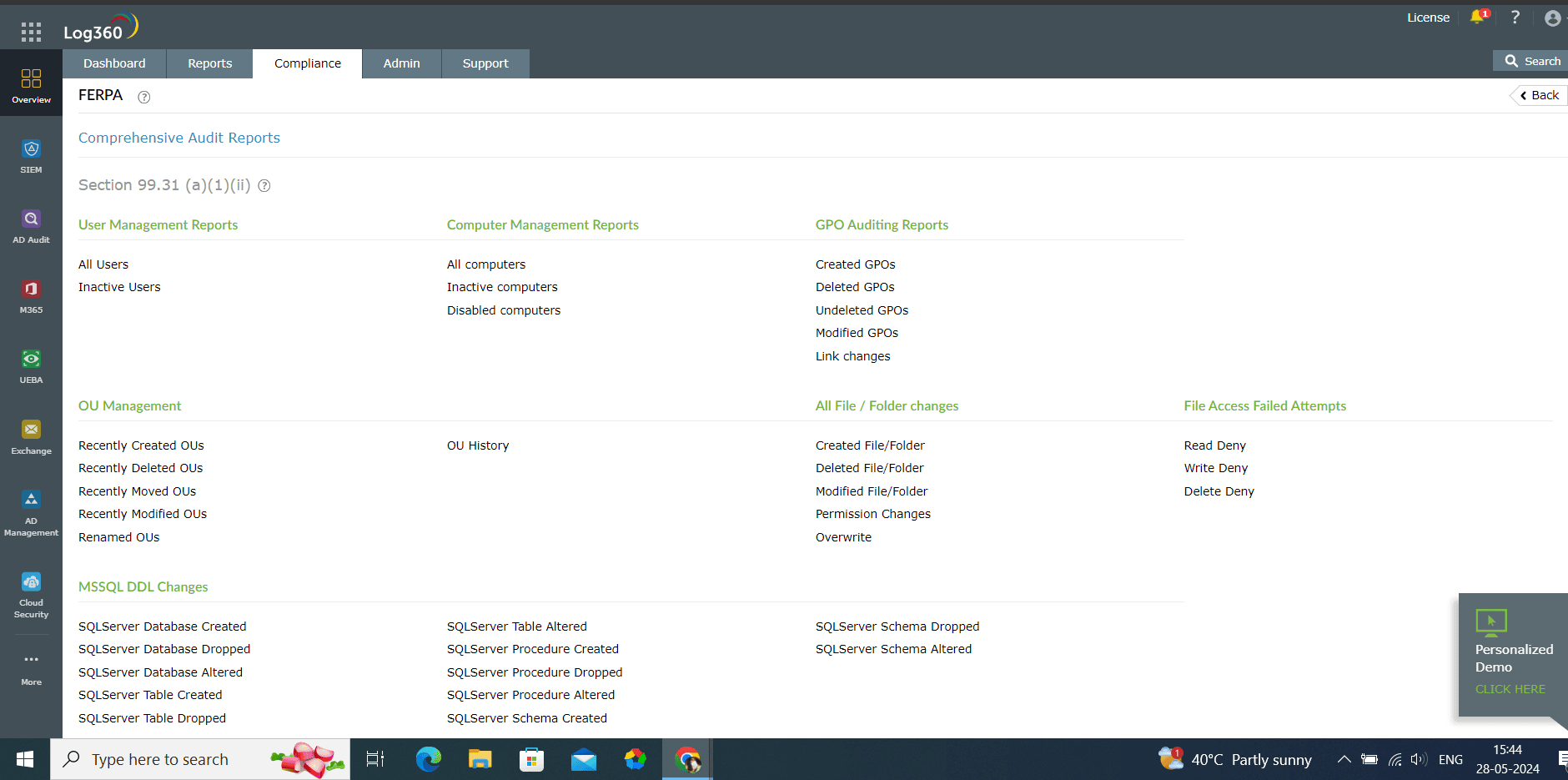
Figure 3: A screenshot from Log360 showing the different clauses under FERPA
Enabling the use of personal devices
Frankenstein University, like many other educational institutions, allows students to access their projects in cloud applications via personal devices. This meant that the university could not manage the devices or set policies at the endpoint level to govern how students accessed cloud applications and shared data. Security concerns arose among stakeholders, prompting the university to deploy a cost-effective CASB-integrated SIEM solution. This solution enabled them to discover and monitor cloud applications accessed from the institution's network and enforce access and control policies for sanctioned applications like LMS, email, and chat. As a result, Frankenstein University could block access to non-education-related applications on their internet network, allow conditional access to their sanctioned cloud applications based on parameters such as location, user groups, device type, and browser, and block uploads and downloads based on location, file type, and file size, ensuring a secure and manageable IT environment.
Why is a CASB-integrated SIEM solution better than a standalone solution?
SIEM solutions offer advanced threat detection by analyzing and consolidating logs from a security tool like firewall, or even from CASB event logs. They also allow for workflow creation in case of threat detection. CASB-integrated SIEM solutions automate incident response and play workflows, enabling IT teams to combat threats even during odd hours. SIEM solutions like Log360 simplify auditing by providing predefined reports for compliance requirements like FERPA, GDPR, or HIPAA. Some of the other advantages include preventing data leaks, providing visibility into Shadow IT, IAM and all other cloud applications. Read why a CASB should be part of your SIEM to learn more.



