What is CryptoLocker?
CryptoLocker is a malware type belonging to the crypto-virus family of ransomware. First discovered in 2013, it uses public key cryptography to encrypt files and demands a ransom in exchange for the decryption key. The keys are stored on its command and control (C2) server and are deleted if the ransom is not paid. This results in permanent data loss for victims, making CryptoLocker the most dangerous ransomware strain of its time.
Although the original strain was neutralized in 2014, several variants have been cloned and are used to this day, continuing the legacy and infamy of the CryptoLocker ransomware. Even though CryptoLocker no longer exists, its attack strategies live on through its variants, making it necessary to understand the anatomy of CryptoLocker to defend against related ransomware attacks.
Is CryptoLocker a virus?
Though referred to by cybercriminals as the CryptoLocker virus, CryptoLocker is not a virus that can self-propagate. It is incapable of making copies of itself, unlike most viruses, but it is still able to spread across a network. This is made possible with the help of the Gameover Zeus botnet, a vast network of malware-infected systems. The botnet typically uses the Zeus Trojan to compromise a computer and then propagates by exploiting security gaps in a peer-to-peer network. By leveraging the Zeus Trojan, CryptoLocker is able to infect the victim's system and spread the ransomware to devices on the peer network. This is why CryptoLocker has predominantly impacted files on shared network drives and file shares.
How does CryptoLocker work?
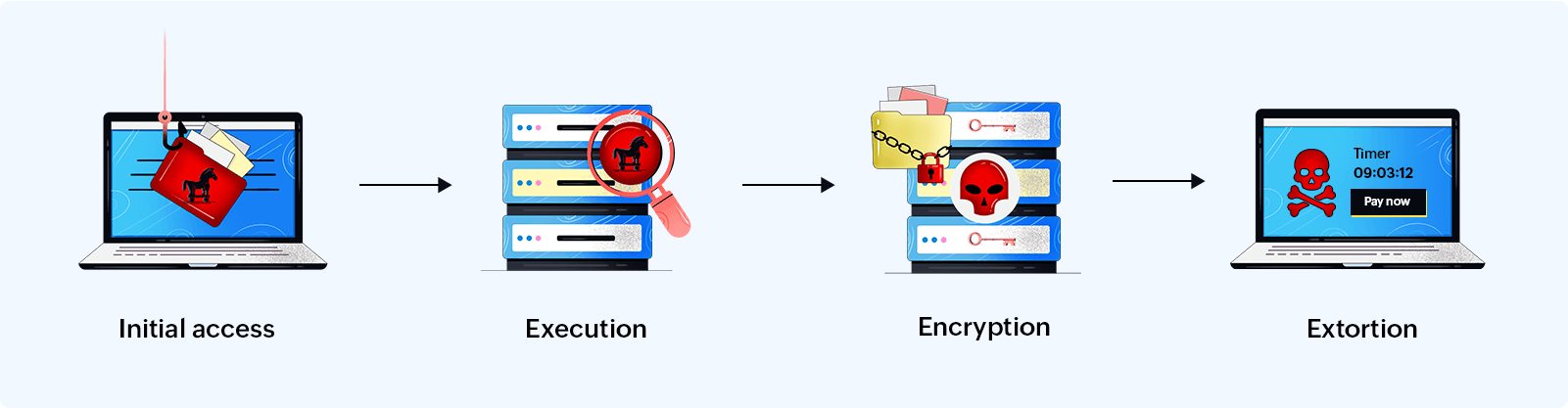
Figure 1: CryptoLocker attack stages
Stage 1: Initial access
- CryptoLocker gains access to a network through phishing emails, where users click malicious email attachments or links.
- Since CryptoLocker is distributed via the Zeus Trojan, the malware is automatically installed on compromised devices.
- It may also be installed through unsecured file-sharing sites, where malicious files with double extensions are disguised as harmless downloadable files.
Stage 2: Execution
Once CryptoLocker enters a device, it scans the network for network drivers, shared folders, and cloud storage associated with the device. It also spreads the infection with the help of the Trojan, affecting all devices in the network. It then identifies files and folders stored in the drivers and shared folders and encrypts them.
Stage 3: Encryption
CryptoLocker utilizes asymmetric encryption to encrypt files. Asymmetric encryption involves a public key for encrypting plaintext and a private key for decrypting the encrypted text. Typically, during data transfers, the sender possesses the public key to encrypt the data, while the corresponding receiver holds the private key to decrypt it. However, in a CryptoLocker attack, the attacker encrypts the files using the public key and stores the private key in the C2 server, preventing the victim from decrypting the files. After encryption, the files are renamed using extensions such as .cryptolocker or .encrypted.
Stage 4: Extortion
CryptoLocker demands a ransom amount to release the decryption key. The ransom payment is usually made in Bitcoin or with prepaid cash vouchers. Victims are given a countdown in the ransom note, indicating the time remaining for the ransom payment. If payment is not made by the specified deadline, CryptoLocker permanently deletes the decryption key.
How was CryptoLocker stopped?
In June 2014, the United States government launched a multinational operation to disrupt the Gameover Zeus botnet and neutralize CryptoLocker. As a result, the botnet was taken down, the CryptoLocker C2 servers were seized, and the private keys were made publicly available to the victims.
CryptoLocker variants
The attack methodology of CryptoLocker led to the development of several clones that continue to operate in a similar manner to the original version. CryptoLocker 2.0 is considered as the look-alike of CryptoLocker ransomware, which uses the base code of its predecessor. These CryptoLocker replicas continue to exist today, making CryptoLocker one of the most notable ransomware strains.
CryptoLocker 2.0: How is it different?
CryptoLocker 2.0 differs from the original version in the following ways:
| Variation | CryptoLocker | CryptoLocker 2.0 |
| Programming language | Visual C++ | C# |
| Encryption method | RSA-2048 | RSA-1024 |
| Target file types | Text files | All files, including images, music, and video. |
| C2 communication encryption method | RSA encryption for file transmission to C2 server. | AES encryption for file transmission to C2 server. |
| Ransom payment deadlines | Displays a countdown to pay the ransom, after which the decryption key will be deleted. | Specifies a deadline for ransom payment, after which the ransom demand will be increased. |
| Ransom payment method | Bitcoins, pre-paid cash vouchers | Bitcoins |
CryptoLocker detection techniques
The following techniques can be used to detect CryptoLocker ransomware attacks:
- Email filtering: Phishing emails are common vectors of ransomware that carry malicious URLs, attachments, and executables. Email filtering tools flag emails with suspicious content and block them from the user's inbox.
- Static file analysis: This technique enables the identification of malicious executables and attachments by scanning the file contents for common ransomware IoCs and signatures.
- Anomaly detection: User and entity behavior monitoring tools enable the detection of anomalous activities, like unauthorized access and logons, privilege escalations, and lateral movement within the network.
CryptoLocker removal procedure
Here are the various stages involved in the CryptoLocker removal process:
- Report: Report the incident and communicate the severity of the attack to regulatory authorities, stakeholders, and the public.
- Identify: Determine the infected systems and isolate them from unaffected critical systems.
- Contain: Disconnect all network connections, like Ethernet, Wi-Fi, and Bluetooth, to prevent communications with the C2 server.
- Eradicate: Analyze all storage drives, file systems, and folders to eliminate malicious executables.
- Recover: Determine the nature of the files and data contained in the impacted systems and check data backups to restore the files.
CryptoLocker prevention best practices
Want to steer clear from a CryptoLocker attack? Use these best practices to stay secure:
- Conduct employee awareness programs and train users to identify phishing emails, anomalous processes, and malicious executables.
- Adhere to the principle of least privilege and monitor suspicious privilege escalations and lateral movement.
- Enforce a Zero Trust policy and regularly patch and update endpoints and network devices and continuously audit them for vulnerabilities.
- Implement MFA for all user accounts and enforce strong password policies.
- Monitor changes to sensitive files and folders with a file integrity monitoring solution.
- Back up files containing sensitive data and protect both the original files and their backups using data encryption techniques.
- Implement a SIEM solution to gain comprehensive visibility across the entire network.
Related solutions
ManageEngine Log360 is a comprehensive SIEM solution with advanced ransomware detection and mitigation capabilities. Log360 stands out as one of the best ransomware protection solutions with these powerful features:
- 360-degree network visibility: Log360 provides complete visibility into the network through out-of-the-box audit reports and interactive dashboards on a single console.
- Ransomware detection: Predefined correlation rules and alert profiles for ransomware detection help identify potential ransomware activities in real time.
- User and entity behavior analytics: With its ML-based behavior monitoring capabilities, Log360 detects anomalous activities in the network to identify potential signs of a ransomware attack.
- File monitoring: Log360's file integrity monitoring feature helps monitor unauthorized file accesses, creations, deletions, and modifications to protect sensitive data from ransomware.
- Cloud app security: Log360's CASB capabilities help block suspicious websites and ban malicious applications to secure sensitive cloud data from ransomware threats.
- Ransomware incident response: The ransomware detection alert profiles include built-in incident response workflows that, when enabled, prevent the propagation of ransomware attacks.
To explore more, sign up for a personalized demo of Log360. Or, you can discover its powerful capabilities with a fully functional, 30-day, free trial.



