LockBit is a notorious ransomware-as-a-service (RaaS) provider, infamous for its self-propagating strains and double extortion tactics. Allegedly operated by a Russian-based advanced persistent threat group, LockBit primarily targets small to medium-sized businesses across the healthcare, finance, education, and manufacturing sectors. This RaaS provider is popular among affiliates due to its unique and constantly evolving attack methods, which often result in substantial damage and ransom payments. The FBI has reported approximately 1,700 LockBit attacks in the United States since 2020.
Evolution of LockBit
LockBit ransomware is infamous for its regular upgrades, making it one of the most complex ransomware strains. Let's look back at how LockBit has evolved over the years.
ABCD ransomware
ABCD, the precursor of LockBit ransomware, launched in September 2019. Afterward, the group established itself as a RaaS provider. This ransomware was also considered a subclass of the crypto-virus, as it demanded a ransom in the form of cryptocurrency. The encrypted files had the .abcd extension, and the compromised devices displayed the ransom note with instructions to restore the files.
LockBit
In January 2020, the RaaS provider proclaimed its identity with the extension .lockbit for encrypted files. This version was very similar to its predecessor. However, this is when the ransomware became infamous for its self-propagation—an ability to spread an infected script across devices without any human intervention.
LockBit 2.0
LockBit 2.0, also known as LockBit Red, was launched in June 2021. This variant maximized the effect of a LockBit attack with its new tool called StealBit. StealBit is a built-in data theft tool, used for double extortion that can help compel victims to pay higher ransoms. Furthermore, some of the LockBit affiliates were involved in triple extortion by launching a DDoS attack in addition to the ransomware attack. The group also updated its ransom note with an advertisement inviting insiders from organizations into an attack agreement and offering a percentage of the ransom collected.
LockBit Linux-ESXi Locker version 1.0
This version of LockBit was deployed in October 2021 to target Linux hosts and encrypt files on ESXi servers, which host multiple VMs. This version was considered complex as it employed both the AES and elliptical curve cryptography (ECC) for data encryption. AES involves multiple stages of encryption to conceal information, and ECC is a type of public key encryption technique that is faster than other encryption techniques. AES and ECC together hardened the encryption of stolen data for LockBit actors.
LockBit 3.0
Released in March 2022, LockBit 3.0, also known as LockBit Black, was an upgraded version of LockBit 2.0 with advancements in double extortion techniques. This variant was known to exploit Windows Defender to establish a chain of malware infections on multiple devices using Cobalt Strike—a commercial penetration testing tool. By bypassing Windows Defender, this variant also established an avenue for sideloading that other threat actors could exfiltrate data from infected devices. LockBit 3.0 took enterprises by storm with its advanced means of data encryption and exfiltration.
LockBit Green
Assimilating the source code from Conti ransomware, the group released LockBit Green in January 2023. This variant of ransomware was ultimately designed to target cloud-based services. Security experts considered the source code of this variant to be a complete replica of the Conti encryptor except for the ransom note, which was modified to refer to LockBit.
LockBit on macOS
In April 2023, it was reported that the RaaS provider emerged with its new ransomware variant, which was exclusive for macOS. It involved advanced artifacts capable of encrypting files on devices running on Apple macOS.
How LockBit ransomware works?
- The LockBit ransomware gains initial access to the network via phishing emails, brute-force attacks on RDP accounts, or the exploitation of vulnerable applications.
- It then infiltrates deeper into the victim's network and prepares the environment to stage the attack using post-exploitation tools, which use Windows PowerShell or the SMB protocol for execution.
- It deploys the ransomware payload and infects the first host. This single infected host automatically spreads the infection to multiple devices by sharing an infected script with all the compromised devices using the SMB protocol.
- All the files on the infected devices get encrypted, and a ransom note appears on the victims' compromised devices.
- The files can be decrypted only with the help of LockBit's proprietary decryption tool.
LockBit attack stages
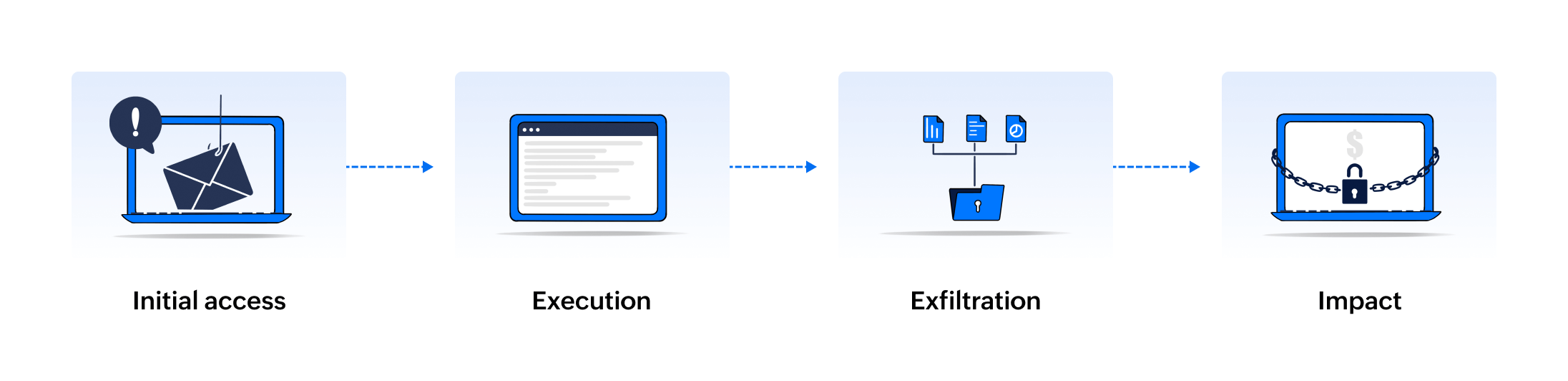
Figure 1: LockBit ransomware attack
Stage I: Initial access
Initial access is the first stage of the LockBit attack, where adversaries try to set foot into the victim's network. The different methods by which they gain access are as follows:
- Attackers phish victims using emails containing suspicious links and attachments to execute malicious codes on their devices.
- Masquerading as valid users, attackers connect to the internal enterprise network from external-facing remote services using compromised credentials.
- Threat actors lure users to a compromised or malicious website where an automatic script execution occurs.
Stage II: Execution
Execution is the stage where attackers run malicious scripts to infect a victim's compromised device. This is done by exploiting command interpreters like Windows Command Shell, PowerShell, Unix shells, and AppleScript to execute the scripts remotely.
Stage III: Exfiltration
Exfiltrationis the next stage of the LockBit attack. Here, threat actors steal sensitive data from a victim's network using the following techniques:
- Using built-in data theft tools like StealBit, which automatically transfers data via a command-and-control channel and eases the process of data exfiltration.
- By exploiting existing communications with cloud services to transmit data directly to cloud storage rather than using a command-and-control channel.
Stage IV: Impact
Impact is the last stage where adversaries disrupt operations in a victim's network causing distress to the business. The impacts include:
- Encryption of the exfiltrated data and demand of a hefty ransom in exchange for the decryption key.
- Disabling the recovery of corrupted systems, like backup, shadow copies, and automatic repair, to complement data encryption.
- Inhibition of critical services in systems that render them inoperable and unusable, thereby increasing the downtime.
- The display of a ransom note including payment instructions on the user's internal websites and desktop wallpapers to intimidate and threaten them.
Detection and mitigation techniques
- Stay vigilant against phishing emails using email filtering and spam blocking tools to prevent suspicious emails from reaching your inbox.
- Enable MFA across all endpoints and applications to combat account compromises.
- Monitor network traffic originating from unknown or unexpected devices and block connections to blacklisted IPs.
- Review remote logon activities from unintended user accounts to detect compromised accounts.
- Analyze user and entity behavioral patterns to identify anomalous activities in the network.
- Inspect command line executions to flag malicious script executions in command interpreters.
- Audit system processes to detect suspicious process executions and process terminations.
- Detect unauthorized accesses to sensitive files and track file creation, modification, and deletion activities in critical file servers, directories, and registries.
- Evaluate access controls in network shares and spot suspicious access or sharing of files.
- Track activities in the cloud and setup alerts to identify attempts to download or upload sensitive data.
Related solutions
ManageEngine Log360 is a comprehensive SIEM solution with advanced ransomware detection and mitigation capabilities. Log360 stands out as one of the best ransomware protection solutions, offering the following features:
- 360-degree network visibility: Log360 provides complete visibility into the network through out-of-the-box audit reports and interactive dashboards on a single console.
- Ransomware detection: Predefined correlation rules and alert profiles for ransomware detection help identify potential ransomware activities in real-time.
- User and entity behavior analytics: With its ML-based behavior monitoring capabilities, Log360 detects anomalous activities in the network to identify potential signs of a ransomware attack.
- File monitoring: Log360's file integrity monitoring feature helps monitor unauthorized file accesses, creations, deletions, and modifications to protect sensitive data from ransomware.
- Cloud app security: Log360's CASB capabilities helps blacklist suspicious websites and ban malicious applications to secure sensitive cloud data from ransomware threats.
- Ransomware incident response: The ransomware detection alert profiles include built-in incident response workflows that, when enabled, prevent the propagation of ransomware attacks.
To explore more, sign up for a personalized demo of Log360. Or, you can discover on your own with a fully functional, 30-day, free trial software download.



