As businesses embrace the flexibility and innovation offered by cloud technologies, the use of multi-cloud and hybrid-cloud environments have become prevalent. A multi-cloud environment leverages multiple cloud providers to optimize resources, while a hybrid-cloud environment blends private and public clouds for seamless operations. However, these approaches introduce complex security challenges, such as fragmented controls, diverse compliance requirements, and a broader attack surface. In this page, we will focus on multi-cloud security, its importance, why organizations need a cloud access security broker (CASB), the different types of CASBs, and some tips to choose the right CASB solution for a multi-cloud strategy.
What is multi-cloud security?
Multi-cloud security refers to cloud security strategies, best practices, and technologies that organizations often use to protect sensitive data, applications, and workloads across multiple cloud service providers. The goal of such an approach is to ensure consistent security policies and practices, regardless of where resources are hosted. To put it simply, multi-cloud security focuses on managing security risks, maintaining compliance, and protecting sensitive information across all cloud platforms being utilized.
Why is multi-cloud security important?
The need for multi-cloud security can be understood by comprehending the challenges that organizations are bound to face following a multi-cloud adoption, some of which are listed below:
Complexity: Managing different security controls and protocols across various providers can be daunting, especially given the lack of standardized security guidelines across all cloud providers.
Gaps in visibility: Achieving centralized monitoring and gaining visibility into all cloud environments can be challenging, which complicates threat detection and response.
Compliance risks: Ensuring that all cloud environments meet regulatory and industry standards can be arduous, especially when dealing with different jurisdictions and compliance requirements.
Increased attack surface: Using more cloud platforms provides more potential entry points for attackers, increasing the chances of data breach.
Effective multi-cloud security addresses these challenges while enabling organizations to leverage the benefits of a multi-cloud strategy. A good way of ensuring multi-cloud security is by implementing a CASB-integrated SIEM solution. ManageEngine Log360 is a unified security information and event management (SIEM) solution with integrated DLP and CASB capabilities that can help you gain visibility into your AWS, Azure, Google Cloud Platform, and Salesforce cloud infrastructures. Moreover, with its CASB capabilities, Log360 helps organizations enhance security across cloud-based applications.
The need for CASBs
Storing sensitive data in a multi-cloud environment can be dangerous since it opens up more doors for cyberattackers to access the data. In addition, organizations are rapidly moving to cloud-based applications and allowing employees to work from anywhere, leading to increased use of shadow IT applications (the use of applications without prior approval from IT admins). IT teams that are struggling to meet their organization's security requirements need a comprehensive cybersecurity solution to secure their cloud infrastructure. A CASB is an on-premises or cloud-hosted security software or solution that acts as a gatekeeper and monitors the interaction between users and cloud applications. CASBs can help you monitor all the cloud apps accessed, and provide insights into whether the app request was for a sanctioned app or a shadow application, as well as the top shadow apps and the actors accessing them (as shown in Figure 1).
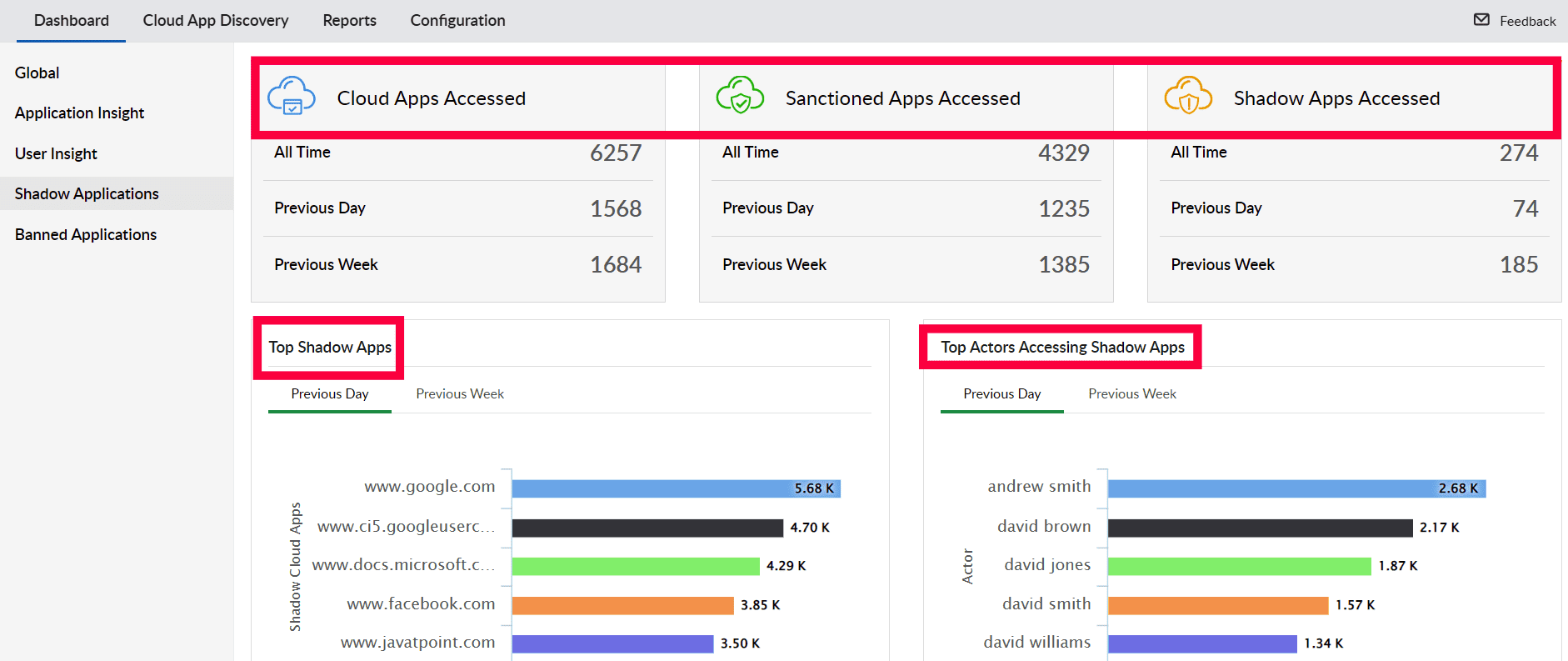
Figure 1: Log360 dashboard offering insights into shadow IT apps and users
With these insights, your IT team can then decide whether to approve or ban the shadow apps used by your employees.
CASBs allow organizations to extend the reach of their security policies to cloud infrastructure by acting as a gatekeeper. They give complete visibility into gaps in your cloud security and allow security professionals to oversee threats, minimize risk profiles, and gain insights on sanctioned and unsanctioned cloud use.
Log360 offers built-in policy profiles and allows users to create custom policy profiles based on their requirements. These custom profiles can then be added to a policy for activation and application across your cloud environment.
Types of CASBs and tips to evaluate the right CASB for your multi-cloud environment
Organizations looking to deploy a CASB solution should know that there are two deployment modes for CASBs: proxy-based and API-based. Both modes have their own merits and demerits, and organizations should look into use cases for both before deploying them in their multi-cloud environments.
Every organization has different multi-cloud security requirements, and choosing the right CASB solution can be tough. Here are three tips that can help you.Evaluate your organization's security goals
To choose the correct CASB solution for your multi-cloud environment, you first need to evaluate your organization's security needs, including which SaaS applications you want to secure. Build an inventory of all the SaaS offerings that the organization is using and determine the ones to secure. Next, identify your main security goal. Is it to control shadow IT or to encrypt data stored in third-party solutions to meet contractual demands?
Think about scalability
It is important to choose a CASB solution that will grow and change to suit your needs. With the proliferation of cloud usage, the threat landscape is growing along with it. This means that the CASB you choose should keep up with cloud compliance and ensure that cloud security policies are up-to-date.
Consider usage and system requirements
It is essential to think about the organization's cloud usage and system requirements while evaluating a CASB since each organization's usage differs. If your organization uses a mix of dozens or hundreds of small, more specific SaaS offerings, the proxy model is best suited for it. However, if it follows the hybrid approach, then the API model would be the one to go for.
Our CASB-integrated SIEM solution is highly scalable, and caters to important use cases such as shadow IT, malicious data exfiltration, and insider threats. To learn more, sign up for a personalized demo of Log360. But if you prefer a cloud-based solution, then sign up for Log360 Cloud, ManageEngine's cloud-based SIEM solution.
Frequently asked questions
- What is a multi-cloud?
-
A multi-cloud environment refers to the use of two or more cloud computing services from different cloud providers—such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud—to manage an organization’s applications, workloads, and data. For better understanding, consider this multi-cloud example: Organizations may use AWS for its ML applications while relying on Google Cloud for data storage and Microsoft Azure for its database services, allowing them to capitalize on the unique strengths of each provider.
- What is a hybrid cloud?
-
A hybrid cloud environment combines on-premises infrastructure or a private cloud with one or more public cloud platforms. This enables organizations to easily move workloads between private and public clouds, thereby maximizing cost, flexibility, and security.
For instance, a business may run sensitive workloads on its private cloud for security reasons while using the public cloud to handle spikes in demand or less critical workloads. This is an example of a hybrid cloud scenario.
- What's the difference between multi-cloud and hybrid-cloud?
-
While a multi-cloud environment focuses on distributing workloads across multiple public cloud providers—with workloads typically operating independently without any integration between clouds—to maximize efficiency and reduce dependency; a hybrid cloud offers a blend of control, flexibility, and scalability by integrating private and public clouds.
- What are the benefits of multi-cloud security?
-
Multi-cloud security provides several benefits to organizations, such as:
- Redundancy and resilience: By using multiple cloud providers, organizations can ensure higher availability and disaster recovery capabilities.
- Flexibility and scalability: Organizations can leverage the strengths of different CSPs to meet specific needs, scaling resources as required.
- Cost optimization: Multi-cloud strategies can help optimize costs by taking advantage of competitive pricing and avoiding vendor lock-in.



