The Conti ransomware strain first appeared in early 2020 and is believed to be operated by a Russia-based cybercrime group that uses the alias Wizard Spider. Conti operates as Ransomware as a Service (RaaS), where the malware developers sell or lease the malcode to affiliates. It is believed that the service provider team takes about 20-30% of the ransom while the affiliates keep the rest.
What makes Conti more dangerous than other ransomware attacks is the speed at which it encrypts and deploys across a system, and the extent of the invasion. As opposed to automated intrusions, Conti attacks are largely human-operated and follow the double extortion strategy. Double extortion is when the attackers not only steal, encrypt, and hold data hostage but also threaten to publish the data if the ransom is not paid. The group operating Conti has a data leak website (Conti.news) which is believed to have published stolen data from over 180 victims. The group apparently tries to find a buyer for the stolen data before publishing it on the website.
The most common attack vectors for Conti ransomware include phishing emails, weak authentication through Remote Desktop Protocol, and software or hardware vulnerabilities. The process often starts off via a phishing email that typically contains a malicious attachment and claims to come from a trusted source. Once the victim clicks the attachment, first-stage malware (i.e., TrickBot, BazarLoader, or Cobalt Strike) gets installed on to the target system, thereby giving remote access to the attackers. As soon as the attackers gain their initial access into the victim’s network, the kill chain starts.
It begins by encrypting files, changing the file extension of the encrypted files, and leaving behind a ransom note in multiple files and folders, usually with the filename readme.txt or conti_readme.txt. Conti uses sophisticated techniques in its code that encrypt files very quickly, such as multi-threading (32 concurrent CPU threads). This makes it difficult to identify and stop in time. Conti ransomware is also capable of moving laterally through the network. It uses the Server Message Block port to gain access to other computers on the same network. In this manner, it is able to penetrate into and spread throughout the victim’s network to a great extent. Following this, the double extortion mechanism kicks in.
Prior to the actual attack, the attackers are typically present in the victim’s network for days or weeks at a time. They do this to scan the victim’s network and gain information about servers, endpoints, backups, locations of sensitive data, the types of security solutions that are in place, etc. They use port scanners like Advanced Port Scanner and Angry IP Scanner to compile a list of IP addresses and machines to scan and learn about the victim's network, gather information, and attack the system. The attackers also often install a backdoor, which allows them to enter and exit the victim’s network as they wish; it also gives them time to install additional tools as needed for further destruction. This backdoor helps them transfer data to their command and control servers, which further enables them to monitor the victims’ reactions to the attack and their plans for recovery.
Conti is known to target medium-to-large-sized organizations, and the ransom amounts largely depend on the size of the organization and their ability to pay. Some of the most infamous Conti attacks include the ones against JVCKenwood, Ireland’s Health Service, Volkswagen Group, City of Tulsa, and the very recent attack on the Government of Costa Rica, where multiple government agencies were attacked and the country’s president was forced to declare a state of emergency.
Ireland’s Health Service Executive (HSE), which operates its public health care system, was hit by Conti ransomware on May 14, 2021. An analysis conducted by the consulting firm PriceWaterhouse Coopers (PWC) found that the initial intrusion actually happened almost eight weeks before in March 2021. According to the timeline released by PWC (as shown below), the initial intrusion happened when an employee inadvertently opened a phishing email containing a malicious Microsoft Excel attachment. Within no time, the attackers were able to establish a backdoor connection to the infected system (patient zero workstation), and they continued to operate in the network for almost eight weeks before launching the Conti ransomware attack on May 14,2021.
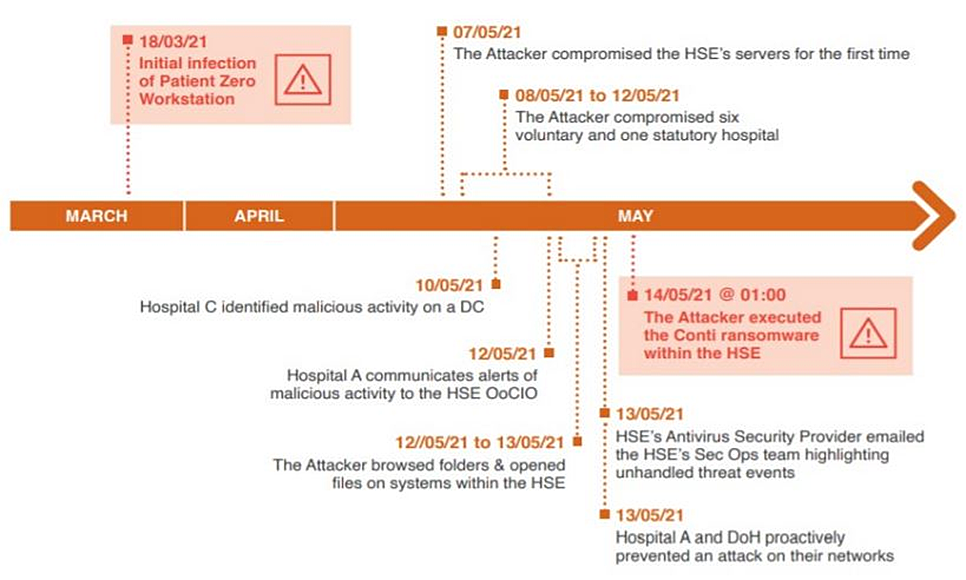
1. PWC’s eight-week timeline from the initial intrusion to the actual ransomware deployment.
Source: HSE/PWC
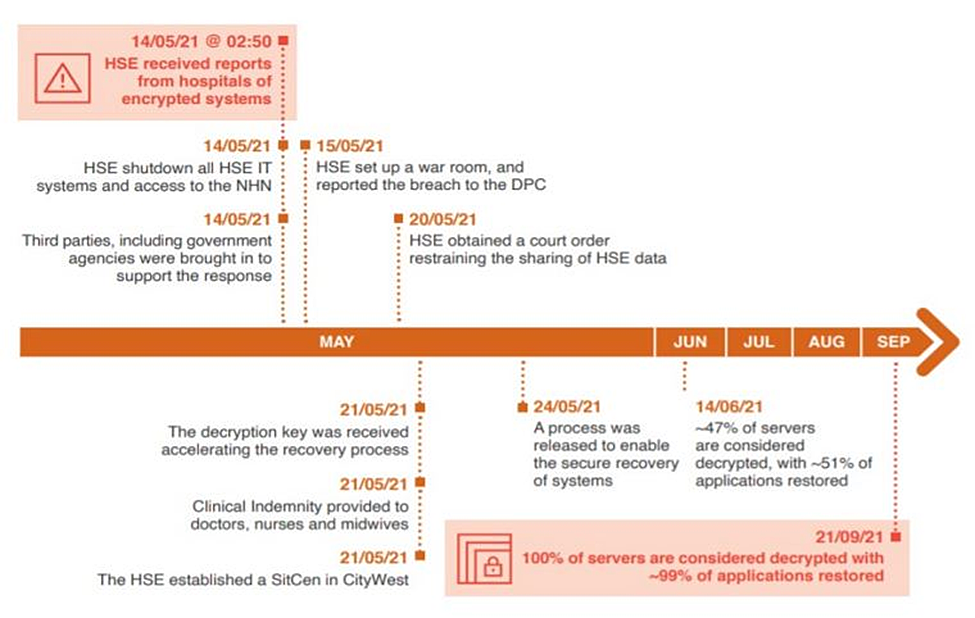
2. PWC’s post infection timeline from May to September 2021.
Source: HSE/PWC
The report also revealed that while there were several warnings of network intrusion, they all went undetected or misidentified by top management because no specific resources, i.e., cybersecurity experts, SOC analysts, or cybersecurity monitoring solutions were allocated, rendering the HSE unprepared to respond to such situations. Even though the HSE’s antivirus software detected the execution of code by Cobalt Strike and Mimikatz, two of the most common tools used by ransomware groups, the organization failed to block them as the antivirus was set to monitor mode, and thus, the alerts went ignored.
Nearly 80% of the HSE’s systems were encrypted and around 700GB of data was stolen during the attack. The services at various Irish hospitals were disrupted, impacting nearly 85,000 computers. This led to many radiology appointments being cancelled and COVID test reports getting delayed. The attack also affected multiple services related to pediatric, maternity, and outpatient departments.
The Conti group initially demanded a ransom of $20 million in exchange for the decryption key, which the HSE refused to pay. However, the group later provided the HSE with a free decryptor along with a warning that they would proceed to sell or publish the data if the ransom was not paid. The HSE, however, did not pay the ransom. It is believed that the HSE will have to spend nearly $100 million, or even more, to recover from this devastating cyber attack.
Conti was once again in the news recently for its cyberattack on the Government of Costa Rica in April-May 2022. The attack hit several government agencies in the country and also severely impacted its foreign trade. Following this, the newly elected president of the country, Rodrigo Chaves, declared a national emergency on May 8,2022. It is believed that the Conti group has leaked more than 95% of the nearly 700GB data that was stolen.
The US Department of State issued a notice on May 6,2022, announcing a reward of up to $10 million for information about the identification and location of anyone holding a key leadership position in the Conti group. As per the notice, the FBI estimates that Conti ransomware is responsible for more than 1,000 attacks and ransom payouts of more than $150 million as of January 2022, making it one of the costliest ransomware strains.
According to a tweet from Advanced Intel's Yelisey Boguslavskiy, the Conti group has apparently shutdown its operations officially.
It is believed that the gang members are rebranding and partnering up with smaller ransomware operations. According to a report by Advanced Intel, Conti has partnered with numerous well-known ransomware operations, including HelloKitty, AvosLocker, Hive, BlackCat, and BlackByte.
It is not the first time that a ransomware group has shut operations and disintegrated after a victorious and high profile attack, only to resurface again as a more dangerous and notorious variant. SIEM solution, ManageEngine Log360, helps prevent attacks by alerting if any unusual events or activities are diagnosed, and initiating an automatic remediation processes. To fully evaluate how Log360 can help the organizations defend against cyberattacks, sign up for a personalized demo.
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.